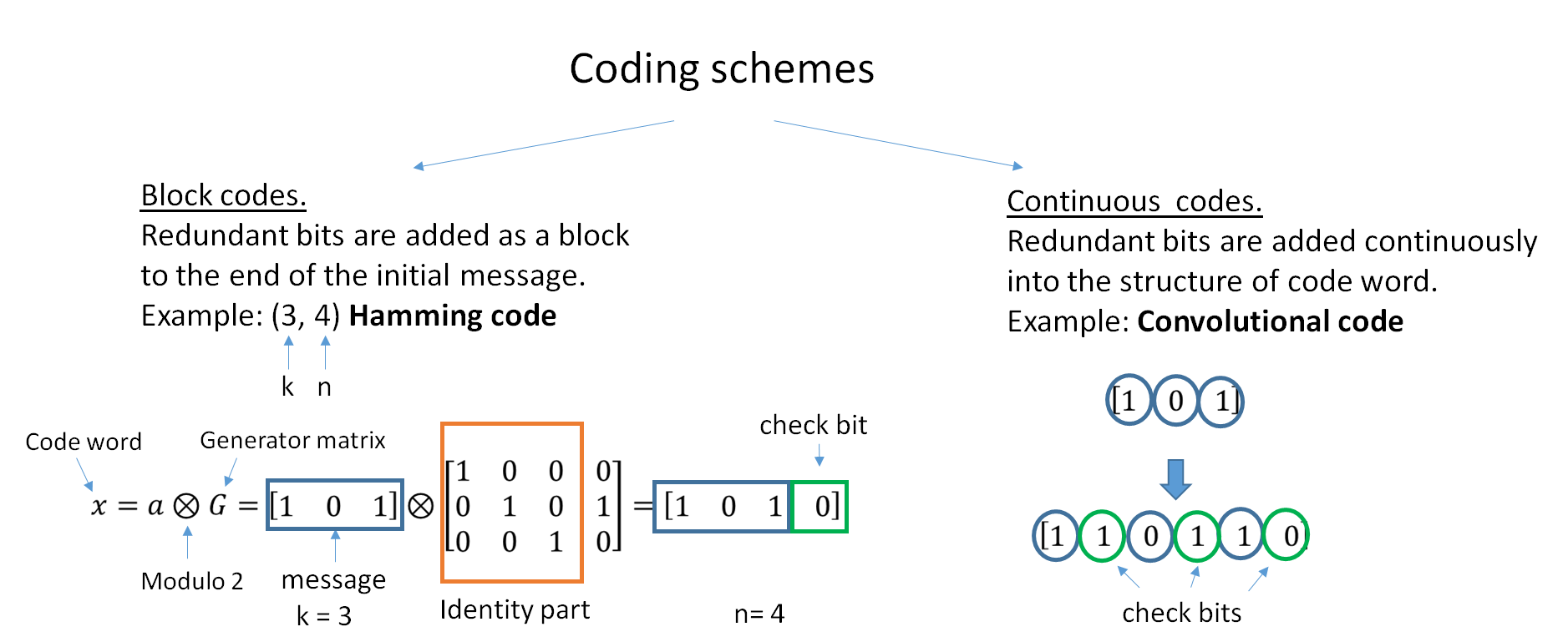
|
Error-correcting Code Memory
Error correction code memory (ECC memory) is a type of computer data storage that uses an error correction code (ECC) to detect and correct n-bit data corruption which occurs in memory. ECC memory is used in most computers where data corruption cannot be tolerated, like industrial control applications, critical databases, and infrastructural memory caches. Typically, ECC memory maintains a memory system immune to single-bit errors: the data that is read from each word is always the same as the data that had been written to it, even if one of the bits actually stored has been flipped to the wrong state. Most non-ECC memory cannot detect errors, although some non-ECC memory with parity support allows detection but not correction. Description Error correction codes protect against undetected data corruption and are used in computers where such corruption is unacceptable, examples being scientific and financial computing applications, or in database and file servers. ECC can als ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Micron PC2700 DDR ECC REG
The micrometre ( international spelling as used by the International Bureau of Weights and Measures; SI symbol: μm) or micrometer ( American spelling), also commonly known as a micron, is a unit of length in the International System of Units (SI) equalling (SI standard prefix "micro-" = ); that is, one millionth of a metre (or one thousandth of a millimetre, , or about ). The nearest smaller common SI unit is the nanometre, equivalent to one thousandth of a micrometre, one millionth of a millimetre or one billionth of a metre (). The micrometre is a common unit of measurement for wavelengths of infrared radiation as well as sizes of biological cells and bacteria, and for grading wool by the diameter of the fibres. The width of a single human hair ranges from approximately 20 to . The longest human chromosome, chromosome 1, is approximately in length. Examples Between 1 μm and 10 μm: * 1–10 μm – length of a typical bacterium * 3–8 μm – width of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Solar Particle Event
In solar physics, a solar particle event (SPE), also known as a solar energetic particle (SEP) event or solar radiation storm, is a solar phenomenon which occurs when particles emitted by the Sun, mostly protons, become accelerated either in the Sun's atmosphere during a solar flare or in interplanetary space by a coronal mass ejection shock. Other nuclei such as helium and HZE ions may also be accelerated during the event. These particles can penetrate the Earth's magnetic field and cause partial ionization of the ionosphere. Energetic protons are a significant radiation hazard to spacecraft and astronauts. Description SPEs occur when charged particles in the Sun's atmosphere are accelerated to extremely high velocities. These charged particles, referred to as solar energetic particles, can escape into interplanetary space where they follow the interplanetary magnetic field. When solar energetic particles interact with the Earth's magnetosphere, they are guided by the Ear ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Single-error Correction And Double-error Detection
In computer science and telecommunication, Hamming codes are a family of linear error-correcting codes. Hamming codes can detect one-bit and two-bit errors, or correct one-bit errors without detection of uncorrected errors. By contrast, the simple parity code cannot correct errors, and can detect only an odd number of bits in error. Hamming codes are perfect codes, that is, they achieve the highest possible rate for codes with their block length and minimum distance of three. Richard W. Hamming invented Hamming codes in 1950 as a way of automatically correcting errors introduced by punched card readers. In his original paper, Hamming elaborated his general idea, but specifically focused on the Hamming(7,4) code which adds three parity bits to four bits of data. In mathematical terms, Hamming codes are a class of binary linear code. For each integer there is a code-word with block length and message length . Hence the rate of Hamming codes is , which is the highest possibl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Error-correcting Code
In computing, telecommunication, information theory, and coding theory, an error correction code, sometimes error correcting code, (ECC) is used for controlling errors in data over unreliable or noisy communication channels. The central idea is the sender encodes the message with redundant information in the form of an ECC. The redundancy allows the receiver to detect a limited number of errors that may occur anywhere in the message, and often to correct these errors without retransmission. The American mathematician Richard Hamming pioneered this field in the 1940s and invented the first error-correcting code in 1950: the Hamming (7,4) code. ECC contrasts with error detection in that errors that are encountered can be corrected, not simply detected. The advantage is that a system using ECC does not require a reverse channel to request retransmission of data when an error occurs. The downside is that there is a fixed overhead that is added to the message, thereby requiring a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Error Detection And Correction
In information theory and coding theory with applications in computer science and telecommunication, error detection and correction (EDAC) or error control are techniques that enable reliable delivery of digital data over unreliable communication channels. Many communication channels are subject to channel noise, and thus errors may be introduced during transmission from the source to a receiver. Error detection techniques allow detecting such errors, while error correction enables reconstruction of the original data in many cases. Definitions ''Error detection'' is the detection of errors caused by noise or other impairments during transmission from the transmitter to the receiver. ''Error correction'' is the detection of errors and reconstruction of the original, error-free data. History In classical antiquity, copyists of the Hebrew Bible were paid for their work according to the number of stichs (lines of verse). As the prose books of the Bible were hardly ever ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RAM Parity
RAM parity checking is the storing of a redundant parity bit representing the parity (odd or even) of a small amount of computer data (typically one byte) stored in random-access memory, and the subsequent comparison of the stored and the computed parity to detect whether a data error has occurred. The parity bit was originally stored in additional individual memory chips; with the introduction of plug-in DIMM, SIMM, etc. modules, they became available in non-parity and parity (with an extra bit per byte, storing 9 bits for every 8 bits of actual data) versions. History Early computers sometimes required the use of parity RAM, and parity-checking could not be disabled. A parity error typically caused the machine to halt, with loss of unsaved data; this is usually a better option than saving corrupt data. ''Logic parity RAM'', also known as fake parity RAM, is non-parity RAM that can be used in computers that require parity RAM. Logic parity RAM recalculates an always-valid parit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ars Technica
''Ars Technica'' is a website covering news and opinions in technology, science, politics, and society, created by Ken Fisher and Jon Stokes in 1998. It publishes news, reviews, and guides on issues such as computer hardware and software, science, technology policy, and video games. ''Ars Technica'' was privately owned until May 2008, when it was sold to Condé Nast Digital, the online division of Condé Nast Publications. Condé Nast purchased the site, along with two others, for $25 million and added it to the company's ''Wired'' Digital group, which also includes '' Wired'' and, formerly, Reddit. The staff mostly works from home and has offices in Boston, Chicago, London, New York City, and San Francisco. The operations of ''Ars Technica'' are funded primarily by advertising, and it has offered a paid subscription service since 2001. History Ken Fisher, who serves as the website's current editor-in-chief, and Jon Stokes created ''Ars Technica'' in 1998. Its purpose w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IEEE
The Institute of Electrical and Electronics Engineers (IEEE) is a 501(c)(3) professional association for electronic engineering and electrical engineering (and associated disciplines) with its corporate office in New York City and its operations center in Piscataway, New Jersey. The mission of the IEEE is ''advancing technology for the benefit of humanity''. The IEEE was formed from the amalgamation of the American Institute of Electrical Engineers and the Institute of Radio Engineers in 1963. Due to its expansion of scope into so many related fields, it is simply referred to by the letters I-E-E-E (pronounced I-triple-E), except on legal business documents. , it is the world's largest association of technical professionals with more than 423,000 members in over 160 countries around the world. Its objectives are the educational and technical advancement of electrical and electronic engineering, telecommunications, computer engineering and similar disciplines. History Ori ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exploit (computer Security)
An exploit (from the English verb ''to exploit'', meaning "to use something to one’s own advantage") is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic (usually computerized). Such behavior frequently includes things like gaining control of a computer system, allowing privilege escalation, or a denial-of-service (DoS or related DDoS) attack. In lay terms, some exploit is akin to a 'hack'. Classification There are several methods of classifying exploits. The most common is by how the exploit communicates to the vulnerable software. A ''remote exploit'' works over a network and exploits the security vulnerability without any prior access to the vulnerable system. A ''local exploit'' requires prior access to the vulnerable system and usually increases the privileges of the person running the exploit past t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privilege Escalation
Privilege escalation is the act of exploiting a bug, a design flaw, or a configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user. The result is that an application with more privileges than intended by the application developer or system administrator can perform unauthorized actions. Background Most computer systems are designed for use with multiple user accounts, each of which has abilities known as privileges. Common privileges include viewing and editing files or modifying system files. Privilege escalation means users receive privileges they are not entitled to. These privileges can be used to delete files, view private information, or install unwanted programs such as viruses. It usually occurs when a system has a bug that allows security to be bypassed or, alternatively, has flawed design assumptions about how it will be used. Privilege escalation occurs in tw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Row Hammer
Row hammer (also written as rowhammer) is a security exploit that takes advantage of an unintended and undesirable side effect in dynamic random-access memory (DRAM) in which memory cells interact electrically between themselves by leaking their charges, possibly changing the contents of nearby memory rows that were not addressed in the original memory access. This circumvention of the isolation between DRAM memory cells results from the high cell density in modern DRAM, and can be triggered by specially crafted memory access patterns that rapidly activate the same memory rows numerous times. The row hammer effect has been used in some privilege escalation computer security exploits, and network-based attacks are also theoretically possible. Different hardware-based techniques exist to prevent the row hammer effect from occurring, including required support in some processors and types of DRAM memory modules. Background In dynamic RAM (DRAM), each bit of stored da ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DRAM
Dynamic random-access memory (dynamic RAM or DRAM) is a type of random-access semiconductor memory that stores each bit of data in a memory cell, usually consisting of a tiny capacitor and a transistor, both typically based on metal-oxide-semiconductor (MOS) technology. While most DRAM memory cell designs use a capacitor and transistor, some only use two transistors. In the designs where a capacitor is used, the capacitor can either be charged or discharged; these two states are taken to represent the two values of a bit, conventionally called 0 and 1. The electric charge on the capacitors gradually leaks away; without intervention the data on the capacitor would soon be lost. To prevent this, DRAM requires an external '' memory refresh'' circuit which periodically rewrites the data in the capacitors, restoring them to their original charge. This refresh process is the defining characteristic of dynamic random-access memory, in contrast to static random-access memory (S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.gif)