|
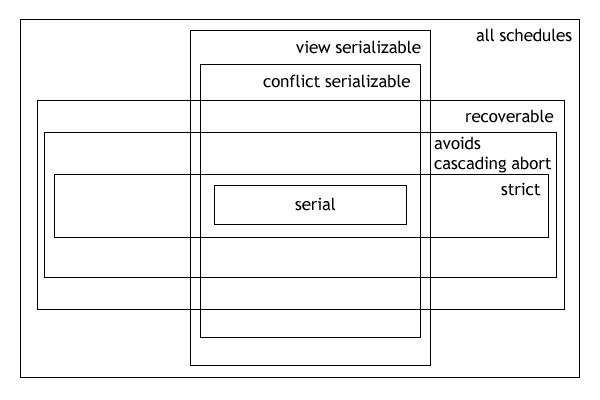
Database Transaction Schedule
In the fields of databases and transaction processing (transaction management), a schedule (or history) of a system is an abstract model to describe the order of Execution (computing), executions in a set of transactions running in the system. Often it is a ''list'' of operations (actions) ordered by time, performed by a set of Database transaction, transactions that are executed together in the system. If the order in time between certain operations is not determined by the system, then a ''partial order'' is used. Examples of such operations are requesting a read operation, reading, writing, aborting, Commit (data management), committing, requesting a Lock (computer science), lock, locking, etc. Often, only a subset of the transaction operation types are included in a schedule. Schedules are fundamental concepts in database concurrency control theory. In practice, most general purpose database systems employ conflict-serializable and strict recoverable schedules. Notation Gri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database
In computing, a database is an organized collection of data or a type of data store based on the use of a database management system (DBMS), the software that interacts with end users, applications, and the database itself to capture and analyze the data. The DBMS additionally encompasses the core facilities provided to administer the database. The sum total of the database, the DBMS and the associated applications can be referred to as a database system. Often the term "database" is also used loosely to refer to any of the DBMS, the database system or an application associated with the database. Before digital storage and retrieval of data have become widespread, index cards were used for data storage in a wide range of applications and environments: in the home to record and store recipes, shopping lists, contact information and other organizational data; in business to record presentation notes, project research and notes, and contact information; in schools as flash c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Maurice Herlihy
Maurice Peter Herlihy (born 4 January 1954) is an American computer scientist active in the field of multiprocessor synchronization. Herlihy has contributed to areas including theoretical foundations of wait-free synchronization, linearizable data structures, applications of combinatorial topology to distributed computing, as well as hardware and software transactional memory. He is the An Wang Professor of Computer Science at Brown University, where he has been a member of the faculty since 1994. Herlihy was elected a member of the National Academy of Engineering in 2013 for concurrent computing techniques for linearizability, non-blocking data structures, and transactional memory. Recognition * 2003 Dijkstra Prize * 2004 Gödel Prize * 2005 Fellow of the Association for Computing Machinery * 2012 Dijkstra Prize * 2013 W. Wallace McDowell Award * 2013 National Academy of Engineering The National Academy of Engineering (NAE) is an American Nonprofit organization, nonpro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Venn Diagram
A Venn diagram is a widely used diagram style that shows the logical relation between set (mathematics), sets, popularized by John Venn (1834–1923) in the 1880s. The diagrams are used to teach elementary set theory, and to illustrate simple set relationships in probability, logic, statistics, linguistics and computer science. A Venn diagram uses simple closed curves on a plane to represent sets. The curves are often circles or ellipses. Similar ideas had been proposed before Venn such as by Christian Weise in 1712 (''Nucleus Logicoe Wiesianoe'') and Leonhard Euler in 1768 (''Letters to a German Princess''). The idea was popularised by Venn in ''Symbolic Logic'', Chapter V "Diagrammatic Representation", published in 1881. Details A Venn diagram, also called a ''set diagram'' or ''logic diagram'', shows ''all'' possible logical relations between a finite collection of different sets. These diagrams depict element (mathematics), elements as points in the plane, and sets as r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Serializability
In the fields of databases and transaction processing (transaction management), a schedule (or history) of a system is an abstract model to describe the order of executions in a set of transactions running in the system. Often it is a ''list'' of operations (actions) ordered by time, performed by a set of transactions that are executed together in the system. If the order in time between certain operations is not determined by the system, then a ''partial order'' is used. Examples of such operations are requesting a read operation, reading, writing, aborting, committing, requesting a lock, locking, etc. Often, only a subset of the transaction operation types are included in a schedule. Schedules are fundamental concepts in database concurrency control theory. In practice, most general purpose database systems employ conflict-serializable and strict recoverable schedules. Notation Grid notation: * Columns: The different transactions in the schedule. * Rows: The time order of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NP-complete
In computational complexity theory, NP-complete problems are the hardest of the problems to which ''solutions'' can be verified ''quickly''. Somewhat more precisely, a problem is NP-complete when: # It is a decision problem, meaning that for any input to the problem, the output is either "yes" or "no". # When the answer is "yes", this can be demonstrated through the existence of a short (polynomial length) ''solution''. # The correctness of each solution can be verified quickly (namely, in polynomial time) and a brute-force search algorithm can find a solution by trying all possible solutions. # The problem can be used to simulate every other problem for which we can verify quickly that a solution is correct. Hence, if we could find solutions of some NP-complete problem quickly, we could quickly find the solutions of every other problem to which a given solution can be easily verified. The name "NP-complete" is short for "nondeterministic polynomial-time complete". In this name, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blind Write
In computing Computing is any goal-oriented activity requiring, benefiting from, or creating computer, computing machinery. It includes the study and experimentation of algorithmic processes, and the development of both computer hardware, hardware and softw ..., a blind write, also known as a write-only transaction, occurs when a transaction writes a value without reading it. In particular, a write wi(X) is said to be blind if it is not the last action of resource X and the following action on X is a write wj(X). Blind writes can cause anomalies if multiple different blind write transactions are executed at the same time. Any view serializable schedule that is not conflict serializable must contain a blind write. References Transaction processing {{Compu-prog-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Snapshot Isolation
In databases, and transaction processing (transaction management), snapshot isolation is a guarantee that all reads made in a transaction will see a consistent snapshot of the database (in practice it reads the last committed values that existed at the time it started), and the transaction itself will successfully commit only if no updates it has made conflict with any concurrent updates made since that snapshot. Snapshot isolation has been adopted by several major database management systems, such as InterBase, Firebird, Oracle, MySQL, PostgreSQL, SQL Anywhere, MongoDB and Microsoft SQL Server (2005 and later). The main reason for its adoption is that it allows better performance than serializability, yet still avoids most of the concurrency anomalies that serializability avoids (but not all). In practice snapshot isolation is implemented within multiversion concurrency control (MVCC), where generational values of each data item (versions) are maintained: MVCC is a common way to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Timestamp-based Concurrency Control
In computer science, a timestamp-based concurrency control algorithm is a optimistic concurrency control method. It is used in some databases to safely handle transactions using timestamps. Operation Assumptions * Every timestamp value is unique and accurately represents an instant in time. * A higher-valued timestamp occurs later in time than a lower-valued timestamp. Generating a timestamp A number of different approaches can generate timestamps * Using the value of the system's clock at the start of a transaction as the timestamp. * Using a thread-safe shared counter that is incremented at the start of a transaction as the timestamp. * A combination of the above two methods. Formal definition Each transaction (T_i) is an ordered list of actions (A_). Before the transaction performs its first action (A_), it is marked with the current timestamp, or any other strictly totally ordered sequence: TS(T_i) = NOW(). Every transaction is also given an initially empty set of transacti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Two-phase Locking
In databases and transaction processing, two-phase locking (2PL) is a pessimistic concurrency control method that guarantees conflict-serializability. Philip A. Bernstein, Vassos Hadzilacos, Nathan Goodman (1987) ''Concurrency Control and Recovery in Database Systems'' Addison Wesley Publishing Company, Gerhard Weikum, Gottfried Vossen (2001) ''Transactional Information Systems'' Elsevier, It is also the name of the resulting set of database transaction schedules (histories). The protocol uses locks, applied by a transaction to data, which may block (interpreted as signals to stop) other transactions from accessing the same data during the transaction's life. By the 2PL protocol, locks are applied and removed in two phases: # Expanding phase: locks are acquired and no locks are released. # Shrinking phase: locks are released and no locks are acquired. Two types of locks are used by the basic protocol: ''Shared'' and ''Exclusive'' locks. Refinements of the basic protocol may ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Precedence Graph
A precedence graph, also named conflict graph and serializability graph, is used in the context of concurrency control in databases. It is the directed graph representing precedence of transactions in the schedule, as reflected by precedence of conflicting operations in the transactions. A schedule is ''conflict-serializable'' if and only if its precedence graph of ''committed transactions'' is '' acyclic''. The precedence graph for a schedule S contains: * A node for each committed transaction in S * An arc from Ti to Tj if an action of Ti precedes and conflicts with one of Tj's actions. That is the actions belong to different transactions, at least one of the actions is a write operation, and the actions access the same object (read or write). Cycles of committed transactions can be prevented by aborting an ''undecided'' (neither committed, nor aborted) transaction on each cycle in the precedence graph of all the transactions, which can otherwise turn into a cycle of committed tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Write–write Conflict
In computer science, in the field of databases, write–write conflict, also known as overwriting uncommitted data is a computational anomaly associated with interleaved execution of transactions. Specifically, a write–write conflict occurs when "transaction requests to write an entity for which an unclosed transaction has already made a write request." Given a schedule S S = \begin T1 & T2 \\ W(A) & \\ & W(B) \\ W(B) & \\ Com. & \\ & W(A)\\ & Com. \end note that there is no read in this schedule. The writes are called '' blind writes''. We have a ''dirty write''. Any attempts to make this schedule serial would give off two different results (either T1's version of A and B is shown, or T2's version of A and B is shown), and would not be the same as the above schedule. This schedule would not be serializable. Strict 2PL overcomes this inconsistency by locking T1 out from B. Unfortunately, deadlocks are something Strict 2PL does not overcome all the time. See a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |