|
Cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown. In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation. Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the mathematically advanced ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Colossus Computer
Colossus was a set of computers developed by British cryptanalysis, codebreakers in the years 1943–1945 to help in the cryptanalysis of the Lorenz cipher. Colossus used vacuum tube, thermionic valves (vacuum tubes) to perform Boolean algebra (logic), Boolean and counting operations. Colossus is thus regarded as the world's first computer programming, programmable, electronics, electronic, digital electronics, digital computer, although it was programmed by switches and plugs and not by a stored-program computer, stored program. Colossus was designed by General Post Office (GPO) research telephone engineer Tommy Flowers based on plans developed by mathematician Max Newman at the Government Code and Cypher School at Bletchley Park. Alan Turing's use of probability in cryptanalysis (see Banburismus) contributed to its design. It has sometimes been erroneously stated that Turing designed Colossus to aid the cryptanalysis of the Enigma. (Turing's machine that helped decode Enigma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attack Model
In cryptanalysis, attack models or attack types are a classification of cryptographic attacks specifying the kind of access a Cryptanalysis, cryptanalyst has to a system under attack when attempting to "break" an Encryption, encrypted message (also known as ''ciphertext'') generated by the system. The greater the access the cryptanalyst has to the system, the more useful information they can get to utilize for breaking the cypher. In cryptography, a sending party uses a cipher to encryption, encrypt (transform) a secret ''plaintext'' into a ''ciphertext'', which is sent over an insecure communication channel to the receiving party. The receiving party uses an inverse cipher to decryption, decrypt the ciphertext to obtain the plaintext. A secret knowledge is required to apply the inverse cipher to the ciphertext. This secret knowledge is usually a short number or string called a ''cryptographic key, key''. In a cryptographic attack a third party cryptanalyst analyzes the ciphertex ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Side-channel Attacks
In computer security, a side-channel attack is a type of security exploit that leverages information inadvertently leaked by a system—such as timing, power consumption, or electromagnetic or acoustic emissions—to gain unauthorized access to sensitive information. These attacks differ from those targeting flaws in the design of cryptography, cryptographic computer protocol, protocols or algorithm, algorithms. (Cryptanalysis may identify vulnerabilities relevant to both types of attacks). Some side-channel attacks require technical knowledge of the internal operation of the system, others such as differential power analysis are effective as Black-box testing, black-box attacks. The rise of Web 2.0 applications and software-as-a-service has also significantly raised the possibility of side-channel attacks on the web, even when transmissions between a web browser and server are encrypted (e.g. through HTTPS or WiFi encryption), according to researchers from Microsoft Research and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
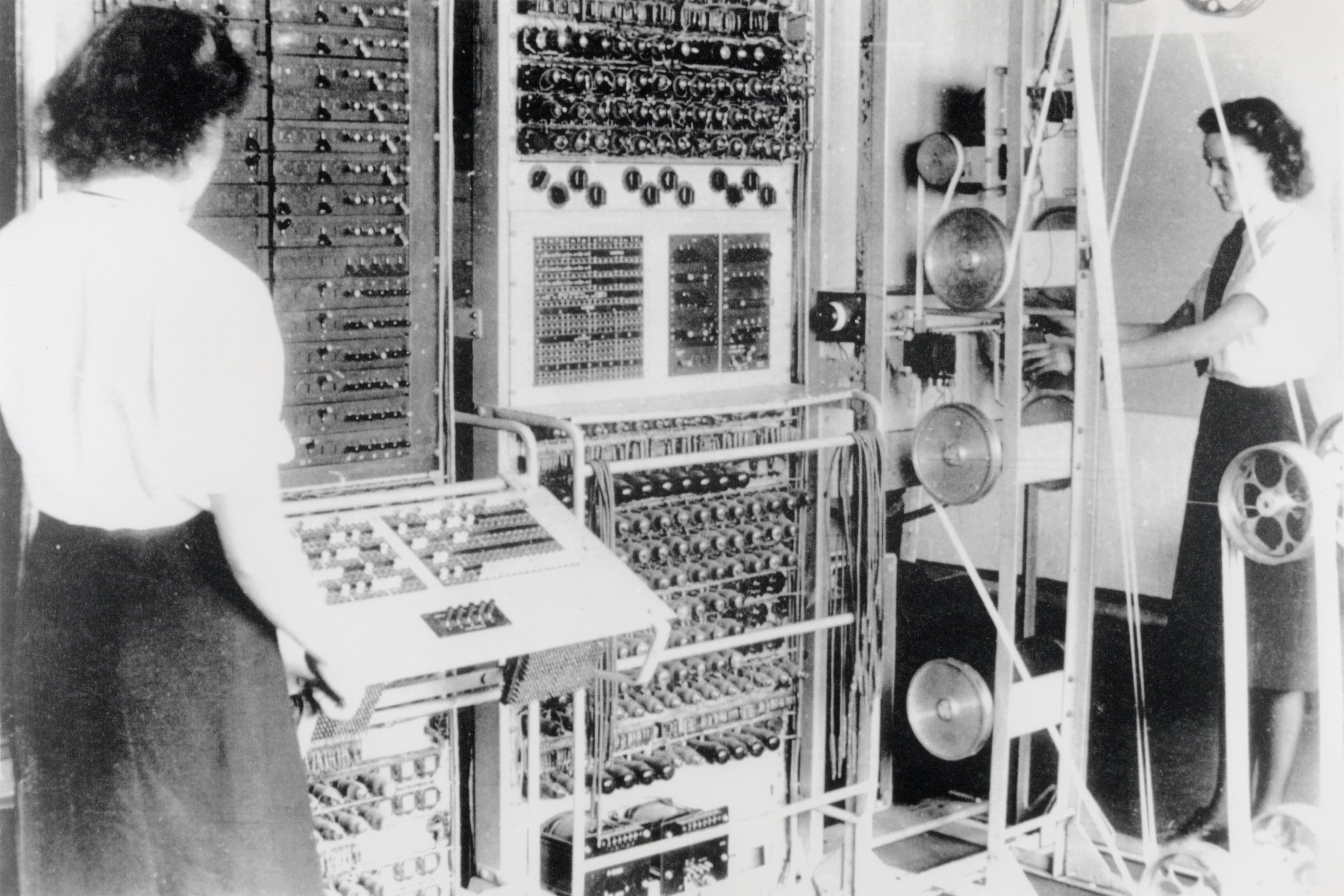
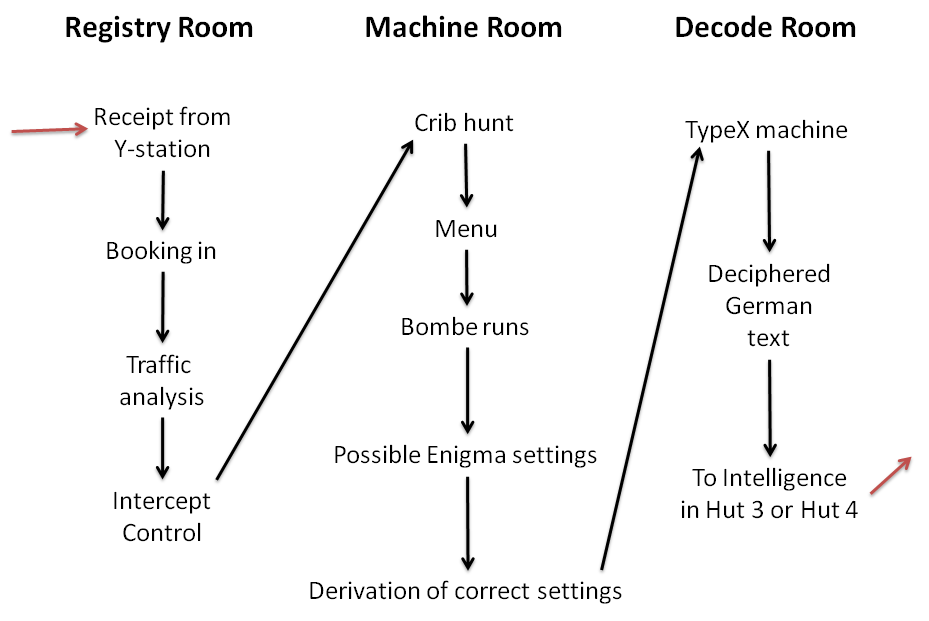
Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the Second World War. During World War II, the estate housed the Government Code and Cypher School (GC&CS), which regularly penetrated the secret communications of the Axis Powers most importantly the German Enigma machine, Enigma and Lorenz cipher, Lorenz ciphers. The GC&CS team of codebreakers included John Tiltman, Dilwyn Knox, Alan Turing, Harry Golombek, Gordon Welchman, Conel Hugh O'Donel Alexander, Hugh Alexander, Donald Michie, W. T. Tutte, Bill Tutte and Stuart Milner-Barry. The team at Bletchley Park devised automatic machinery to help with decryption, culminating in the development of Colossus computer, Colossus, the world's first programmable digital electronic computer. Codebreaking operations at Bletchley Park ended in 1946 and al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reverse Engineering
Reverse engineering (also known as backwards engineering or back engineering) is a process or method through which one attempts to understand through deductive reasoning how a previously made device, process, system, or piece of software accomplishes a task with very little (if any) insight into exactly how it does so. Depending on the system under consideration and the technologies employed, the knowledge gained during reverse engineering can help with repurposing obsolete objects, doing security analysis, or learning how something works. Although the process is specific to the object on which it is being performed, all reverse engineering processes consist of three basic steps: information extraction, modeling, and review. Information extraction is the practice of gathering all relevant information for performing the operation. Modeling is the practice of combining the gathered information into an abstract model, which can be used as a guide for designing the new object or syst ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bombe
The bombe () was an Electromechanics, electro-mechanical device used by British cryptologists to help decipher German Enigma machine, Enigma-machine-encrypted secret messages during World War II. The United States Navy, US Navy and United States Army, US Army later produced their own machines to the same functional specification, albeit engineered differently both from each other and from Polish and British bombes. The British bombe was developed from a device known as the "Bomba (cryptography), bomba" (), which had been designed in Poland at the Biuro Szyfrów (Cipher Bureau) by cryptologist Marian Rejewski, who had been breaking German Enigma machine, Enigma messages for the previous seven years, using it and earlier machines. The initial design of the British bombe was produced in 1939 at the UK Government Code and Cypher School (GC&CS) at Bletchley Park by Alan Turing, with an important refinement devised in 1940 by Gordon Welchman. The engineering design and construction ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Algorithm
In mathematics and computer science, an algorithm () is a finite sequence of Rigour#Mathematics, mathematically rigorous instructions, typically used to solve a class of specific Computational problem, problems or to perform a computation. Algorithms are used as specifications for performing calculations and data processing. More advanced algorithms can use Conditional (computer programming), conditionals to divert the code execution through various routes (referred to as automated decision-making) and deduce valid inferences (referred to as automated reasoning). In contrast, a Heuristic (computer science), heuristic is an approach to solving problems without well-defined correct or optimal results.David A. Grossman, Ophir Frieder, ''Information Retrieval: Algorithms and Heuristics'', 2nd edition, 2004, For example, although social media recommender systems are commonly called "algorithms", they actually rely on heuristics as there is no truly "correct" recommendation. As an e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Decryption
In cryptography, encryption (more specifically, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher to decrypt it. This process prevents the loss of sensitive information via hacking. Decryption, the inverse of encryption, is the process of turning ciphertext into readable plaintext. Ciphertext is not to be confused with codetext because the latter is a result of a code, not a cipher. Conceptual underpinnings Let m\! be the plaintext message that Alice wants to secretly transmit to Bob and let E_k\! be the encryption cipher, where _k\! is a secret key, cryptographic key. Alice must first transform the plaintext into ciphertext, c\!, in order to securely send the message to Bob, as follows: : c = E_k(m). \! In a symmetric-key system, Bob knows Alice's encryption key. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |