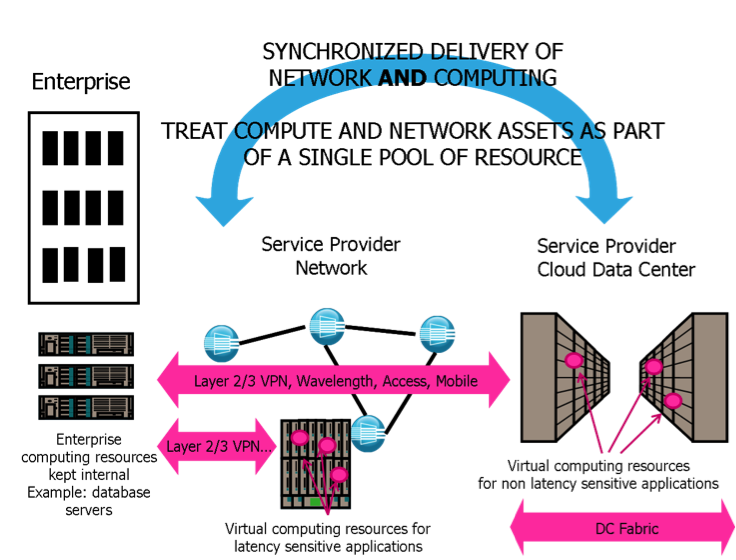
|
Carrier Cloud
In cloud computing a carrier cloud is a class of cloud that integrates wide area networks (WAN) and other attributes of communications service providers’ carrier grade networks to enable the deployment of highly complex applications in the cloud. In contrast, classic cloud computing focuses on the data center, and does not address the network connecting data centers and cloud users. This may result in unpredictable response times and security issues when business critical data are transferred over the Internet. History The advent of virtualization technology and cost effective computing hardware as well as ubiquitous Internet connectivity enabled a first wave of cloud services starting in the first years of the 21st century. But many businesses and other organizations hesitated to move more demanding applications from on-premises dedicated hardware into private or public clouds. As a response, communications service providers started in the 2010/2011 time frame to develop ca ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cloud Computing
Cloud computing is the on-demand availability of computer system resources, especially data storage ( cloud storage) and computing power, without direct active management by the user. Large clouds often have functions distributed over multiple locations, each of which is a data center. Cloud computing relies on sharing of resources to achieve coherence and typically uses a "pay as you go" model, which can help in reducing capital expenses but may also lead to unexpected operating expenses for users. Value proposition Advocates of public and hybrid clouds claim that cloud computing allows companies to avoid or minimize up-front IT infrastructure costs. Proponents also claim that cloud computing allows enterprises to get their applications up and running faster, with improved manageability and less maintenance, and that it enables IT teams to more rapidly adjust resources to meet fluctuating and unpredictable demand, providing burst computing capability: high computing p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OSI Model
The Open Systems Interconnection model (OSI model) is a conceptual model that 'provides a common basis for the coordination of SOstandards development for the purpose of systems interconnection'. In the OSI reference model, the communications between a computing system are split into seven different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application. The model partitions the flow of data in a communication system into seven abstraction layers to describe networked communication from the physical implementation of transmitting bits across a communications medium to the highest-level representation of data of a distributed application. Each intermediate layer serves a class of functionality to the layer above it and is served by the layer below it. Classes of functionality are realized in all software development through all and any standardized communication protocols. Each layer in the OSI model has its own well-defined functi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Graphical User Interface
The GUI ( "UI" by itself is still usually pronounced . or ), graphical user interface, is a form of user interface that allows users to interact with electronic devices through graphical icons and audio indicator such as primary notation, instead of text-based UIs, typed command labels or text navigation. GUIs were introduced in reaction to the perceived steep learning curve of CLIs ( command-line interfaces), which require commands to be typed on a computer keyboard. The actions in a GUI are usually performed through direct manipulation of the graphical elements. Beyond computers, GUIs are used in many handheld mobile devices such as MP3 players, portable media players, gaming devices, smartphones and smaller household, office and industrial controls. The term ''GUI'' tends not to be applied to other lower-display resolution types of interfaces, such as video games (where HUD (''head-up display'') is preferred), or not including flat screens like volumetric displays because ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Health Insurance Portability And Accountability Act
The Health Insurance Portability and Accountability Act of 1996 (HIPAA or the Kennedy– Kassebaum Act) is a United States Act of Congress enacted by the 104th United States Congress and signed into law by President Bill Clinton on August 21, 1996. It modernized the flow of healthcare information, stipulates how personally identifiable information maintained by the healthcare and healthcare insurance industries should be protected from fraud and theft, and addressed some limitations on healthcare insurance coverage. It generally prohibits healthcare providers and healthcare businesses, called ''covered entities'', from disclosing protected information to anyone other than a patient and the patient's authorized representatives without their consent. With limited exceptions, it does not restrict patients from receiving information about themselves. It does not prohibit patients from voluntarily sharing their health information however they choose, nor does it require confidential ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Protection Directive
The Data Protection Directive, officially Directive 95/46/EC, enacted in October 1995, is a European Union directive which regulates the processing of personal data within the European Union (EU) and the free movement of such data. The Data Protection Directive is an important component of EU privacy and human rights law. The principles set out in the Data Protection Directive are aimed at the protection of fundamental rights and freedoms in the processing of personal data. The General Data Protection Regulation, adopted in April 2016, superseded the Data Protection Directive and became enforceable on 25 May 2018. Context The right to privacy is a highly developed area of law in Europe. All the member states of the Council of Europe (CoE) are also signatories of the European Convention on Human Rights (ECHR). Article 8 of the ECHR provides a right to respect for one's "private and family life, his home and his correspondence", subject to certain restrictions. The European Cour ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ALTO Protocol
The musical term alto, meaning "high" in Italian (Latin: ''altus''), historically refers to the contrapuntal part higher than the tenor and its associated vocal range. In 4-part voice leading alto is the second-highest part, sung in choruses by either low women's or high men's voices. In vocal classification these are usually called contralto and male alto or countertenor. Such confusion of "high" and "low" persists in instrumental terminology. Alto flute and alto trombone are respectively lower and higher than the standard instruments of the family (the standard instrument of the trombone family being the tenor trombone), though both play in ranges within the alto clef. Alto recorder, however, is an octave higher, and is defined by its relationship to tenor and soprano recorders; alto clarinet is a fifth lower than B-flat clarinet, already an 'alto' instrument. There is even a contra-alto clarinet, (an octave lower than the alto clarinet), with a range B♭0 – D4. Etymology ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Low Latency
Latency, from a general point of view, is a time delay between the cause and the effect of some physical change in the system being observed. Lag, as it is known in gaming circles, refers to the latency between the input to a simulation and the visual or auditory response, often occurring because of network delay in online games. Latency is physically a consequence of the limited velocity at which any physical interaction can propagate. The magnitude of this velocity is always less than or equal to the speed of light. Therefore, every physical system with any physical separation (distance) between cause and effect will experience some sort of latency, regardless of the nature of the stimulation at which it has been exposed to. The precise definition of latency depends on the system being observed or the nature of the simulation. In communications, the lower limit of latency is determined by the medium being used to transfer information. In reliable two-way communication syst ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Layer
In the seven-layer OSI model of computer networking, the network layer is layer 3. The network layer is responsible for packet forwarding including routing through intermediate routers. Functions The network layer provides the means of transferring variable-length network packets from a source to a destination host via one or more networks. Within the service layering semantics of the OSI network architecture, the network layer responds to service requests from the transport layer and issues service requests to the data link layer. Functions of the network layer include: ; Connectionless communication : For example, IP is connectionless, in that a data packet can travel from a sender to a recipient without the recipient having to send an acknowledgement. Connection-oriented protocols exist at other, higher layers of the OSI model. ; Host addressing :Every host in the network must have a unique address that determines where it is. This address is normally assigned from a hierar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Link Layer
The data link layer, or layer 2, is the second layer of the seven-layer OSI model of computer networking. This layer is the protocol layer that transfers data between nodes on a network segment across the physical layer. The data link layer provides the functional and procedural means to transfer data between network entities and may also provide the means to detect and possibly correct errors that can occur in the physical layer. The data link layer is concerned with local delivery of frames between nodes on the same level of the network. Data-link frames, as these protocol data units are called, do not cross the boundaries of a local area network. Inter-network routing and global addressing are higher-layer functions, allowing data-link protocols to focus on local delivery, addressing, and media arbitration. In this way, the data link layer is analogous to a neighborhood traffic cop; it endeavors to arbitrate between parties contending for access to a medium, without con ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wavelength Division Multiplexing
In fiber-optic communications, wavelength-division multiplexing (WDM) is a technology which multiplexes a number of optical carrier signals onto a single optical fiber by using different wavelengths (i.e., colors) of laser light. This technique enables bidirectional communications over a single strand of fiber, also called wavelength-division duplexing, as well as multiplication of capacity. The term WDM is commonly applied to an optical carrier, which is typically described by its wavelength, whereas frequency-division multiplexing typically applies to a radio carrier which is more often described by frequency. This is purely conventional because wavelength and frequency communicate the same information. Specifically, frequency (in Hertz, which is cycles per second) multiplied by wavelength (the physical length of one cycle) equals the velocity of the carrier wave. In a vacuum, this is the speed of light, usually denoted by the lowercase letter, c. In glass fiber, it is subst ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Private Network
A virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. The benefits of a VPN include increases in functionality, security, and management of the private network. It provides access to resources that are inaccessible on the public network and is typically used for remote workers. Encryption is common, although not an inherent part of a VPN connection. A VPN is created by establishing a virtual point-to-point connection through the use of dedicated circuits or with tunneling protocols over existing networks. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN). From a user perspective, the resources available within the private network can be accessed remotely. Types Virtual private networks may be classified into several categories: ;Remote acce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |