|
Biometric Word List
The PGP Word List ("Pretty Good Privacy word list", also called a biometric word list for reasons explained below) is a list of words for conveying data bytes in a clear unambiguous way via a voice channel. They are analogous in purpose to the NATO phonetic alphabet used by pilots, except a longer list of words is used, each word corresponding to one of the 256 distinct numeric byte values. History and structure The PGP Word List was designed in 1995 by Patrick Juola, a computational linguist, and Philip Zimmermann, creator of PGP. The words were carefully chosen for their phonetic distinctiveness, using genetic algorithms to select lists of words that had optimum separations in phoneme space. The candidate word lists were randomly drawn from Grady Ward's Moby Pronunciator list as raw material for the search, successively refined by the genetic algorithms. The automated search converged to an optimized solution in about 40 hours on a DEC Alpha, a particularly fast machine in th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pretty Good Privacy
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991. PGP and similar software follow the OpenPGP, an open standard of PGP encryption software, standard (RFC 4880) for encrypting and decrypting data. Design PGP encryption uses a serial combination of hashing, data compression, symmetric-key cryptography, and finally public-key cryptography; each step uses one of several supported algorithms. Each public key is bound to a username or an e-mail address. The first version of this system was generally known as a web of trust to contrast with the X.509 system, which uses a hierarchical approach based on certificate authority and which was added to PGP implementations later. Current versions of P ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Jon Callas
Jon Callas is an American computer security expert, software engineer, user experience designer, and technologist who is the co-founder and former CTO of the global encrypted communications service Silent Circle.http://www.linkedin.com/in/joncallas He has held major positions at Digital Equipment Corporation, Apple, PGP, and Entrust, and is considered "one of the most respected and well-known names in the mobile security industry." Callas is credited with creating several Internet Engineering Task Force (IETF) standards, including OpenPGP, DKIM, and ZRTP, which he wrote. Prior to his work at Entrust, he was Chief Technical Officer and co-founder of PGP Corporation and the former Chief Technical Officer of Entrust. On his website, Callas describes himself as "an entrepreneur and innovator in information and business security, including cryptography, operating system security, public key infrastructure, and intellectual property rights," as well as "an innovator in human-computer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Seed Phrase
A cryptocurrency wallet is a device, physical medium, program or a service which stores the public and/or private keys for cryptocurrency transactions. In addition to this basic function of storing the keys, a cryptocurrency wallet more often also offers the functionality of encrypting and/or signing information. Signing can for example result in executing a smart contract, a cryptocurrency transaction (see "bitcoin transaction" image), identification or legally signing a 'document' (see "application form" image). Technology Private and public key generation A cryptocurrency wallet works by a theoretical or random number being generated and used with a length that depends on the algorithm size of the cryptocurrency's technology requirements. The number is then converted to a private key using the specific requirements of the cryptocurrency cryptography algorithm requirement. A public key is then generated from the private key using whichever cryptographic algorithm requi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptocurrency Wallet
A cryptocurrency wallet is a device, physical medium, program or a service which stores the public and/or private keys for cryptocurrency transactions. In addition to this basic function of storing the keys, a cryptocurrency wallet more often also offers the functionality of encrypting and/or signing information. Signing can for example result in executing a smart contract, a cryptocurrency transaction (see "bitcoin transaction" image), identification or legally signing a 'document' (see "application form" image). Technology Private and public key generation A cryptocurrency wallet works by a theoretical or random number being generated and used with a length that depends on the algorithm size of the cryptocurrency's technology requirements. The number is then converted to a private key using the specific requirements of the cryptocurrency cryptography algorithm requirement. A public key is then generated from the private key using whichever cryptographic algorithm requ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
What3words
what3words is a proprietary geocode system designed to identify any location with a resolution of about . It is owned by What3words Limited, based in London, England. The system encodes geographic coordinates into three permanently fixed dictionary words. For example, the front door of 10 Downing Street in London is identified by . What3words differs from most location encoding systems in that it uses words rather than strings of numbers or letters, and the pattern of this mapping is not obvious; the algorithm mapping locations to words is protected by copyright. The company has a website, apps for iOS and Android, and an API for bidirectional conversion between what3words addresses and latitude/longitude coordinates. History Founded by Chris Sheldrick, Jack Waley-Cohen, Mohan Ganesalingam and Michael Dent, what3words was launched in July 2013. Sheldrick and Ganesalingam conceived the idea when Sheldrick, working as an event organizer, struggled to get bands and equipment to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Automated Password Generator
A random password generator is software program or hardware device that takes input from a random or pseudo-random number generator and automatically generates a password. Random passwords can be generated manually, using simple sources of randomness such as dice or coins, or they can be generated using a computer. While there are many examples of "random" password generator programs available on the Internet, generating randomness can be tricky and many programs do not generate random characters in a way that ensures strong security. A common recommendation is to use open source security tools where possible since they allow independent checks on the quality of the methods used. Note that simply generating a password at random does not ensure the password is a strong password, because it is possible, although highly unlikely, to generate an easily guessed or cracked password. In fact, there is no need at all for a password to have been produced by a perfectly random process: it j ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Frontier Foundation
The Electronic Frontier Foundation (EFF) is an international non-profit digital rights group based in San Francisco, California. The foundation was formed on 10 July 1990 by John Gilmore, John Perry Barlow and Mitch Kapor to promote Internet civil liberties. The EFF provides funds for legal defense in court, presents '' amicus curiae'' briefs, defends individuals and new technologies from what it considers abusive legal threats, works to expose government malfeasance, provides guidance to the government and courts, organizes political action and mass mailings, supports some new technologies which it believes preserve personal freedoms and online civil liberties, maintains a database and web sites of related news and information, monitors and challenges potential legislation that it believes would infringe on personal liberties and fair use and solicits a list of what it considers abusive patents with intentions to defeat those that it considers without merit. History Fou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Diceware
Diceware is a method for creating passphrases, passwords, and other cryptographic variables using ordinary dice as a hardware random number generator. For each word in the passphrase, five rolls of a six-sided die are required. The numbers from 1 to 6 that come up in the rolls are assembled as a five-digit number, e.g. ''43146''. That number is then used to look up a word in a cryptographic word list. In the original such list ''43146'' corresponds to ''munch''. By generating several words in sequence, a lengthy passphrase can thus be constructed randomly. A Diceware word list is any list of 6^5 = 7\,776 unique words, preferably ones the user will find easy to spell and to remember. The contents of the word list do not have to be protected or concealed in any way, as the security of a Diceware passphrase is in the number of words selected, and the number of words each selected word could be taken from. Lists have been compiled for several languages, including Basque, Bulgarian, C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
S/KEY
S/KEY is a one-time password system developed for authentication to Unix-like operating systems, especially from dumb terminals or untrusted public computers on which one does not want to type a long-term password. A user's real password is combined in an offline device with a short set of characters and a decrementing counter to form a single-use password. Because each password is only used once, they are useless to password sniffers. Because the short set of characters does not change until the counter reaches zero, it is possible to prepare a list of single-use passwords, in order, that can be carried by the user. Alternatively, the user can present the password, characters, and desired counter value to a local calculator to generate the appropriate one-time password that can then be transmitted over the network in the clear. The latter form is more common and practically amounts to challenge–response authentication. S/KEY is supported in Linux (via pluggable authentication mo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Endianness
In computing, endianness, also known as byte sex, is the order or sequence of bytes of a word of digital data in computer memory. Endianness is primarily expressed as big-endian (BE) or little-endian (LE). A big-endian system stores the most significant byte of a word at the smallest memory address and the least significant byte at the largest. A little-endian system, in contrast, stores the least-significant byte at the smallest address. Bi-endianness is a feature supported by numerous computer architectures that feature switchable endianness in data fetches and stores or for instruction fetches. Other orderings are generically called middle-endian or mixed-endian. Endianness may also be used to describe the order in which the bits are transmitted over a communication channel, e.g., big-endian in a communications channel transmits the most significant bits first. Bit-endianness is seldom used in other contexts. Etymology Danny Cohen introduced the terms ''big-endian'' a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Byte Order
In computing, endianness, also known as byte sex, is the order or sequence of bytes of a word of digital data in computer memory. Endianness is primarily expressed as big-endian (BE) or little-endian (LE). A big-endian system stores the most significant byte of a word at the smallest memory address and the least significant byte at the largest. A little-endian system, in contrast, stores the least-significant byte at the smallest address. Bi-endianness is a feature supported by numerous computer architectures that feature switchable endianness in data fetches and stores or for instruction fetches. Other orderings are generically called middle-endian or mixed-endian. Endianness may also be used to describe the order in which the bits are transmitted over a communication channel, e.g., big-endian in a communications channel transmits the most significant bits first. Bit-endianness is seldom used in other contexts. Etymology Danny Cohen introduced the terms ''big-endian'' a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
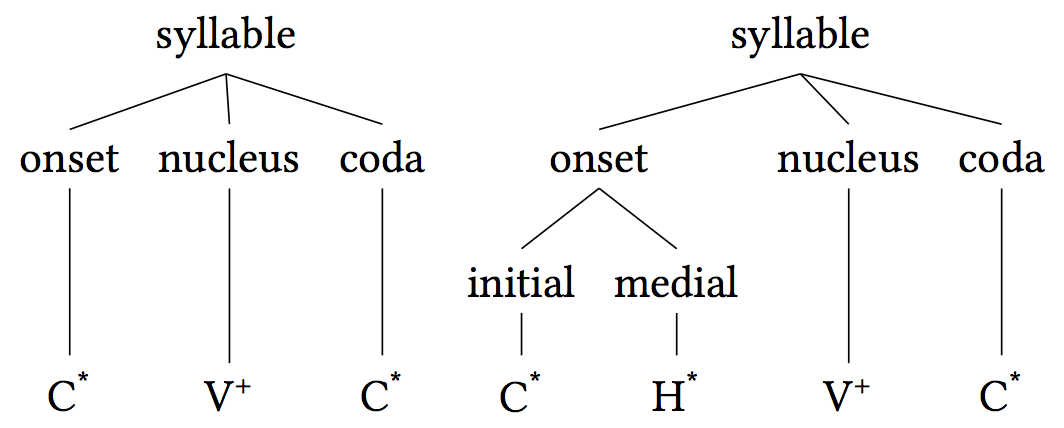
Syllables
A syllable is a unit of organization for a sequence of speech sounds typically made up of a syllable nucleus (most often a vowel) with optional initial and final margins (typically, consonants). Syllables are often considered the phonological "building blocks" of words. They can influence the rhythm of a language, its prosody, its poetic metre and its stress patterns. Speech can usually be divided up into a whole number of syllables: for example, the word ''ignite'' is made of two syllables: ''ig'' and ''nite''. Syllabic writing began several hundred years before the first letters. The earliest recorded syllables are on tablets written around 2800 BC in the Sumerian city of Ur. This shift from pictograms to syllables has been called "the most important advance in the history of writing". A word that consists of a single syllable (like English ''dog'') is called a monosyllable (and is said to be ''monosyllabic''). Similar terms include disyllable (and ''disyllabic''; also ''bis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |