Seed Phrase on:
[Wikipedia]
[Google]
[Amazon]
 A cryptocurrency wallet is a device, physical medium, program or a service which stores the public and/or private keys for
A cryptocurrency wallet is a device, physical medium, program or a service which stores the public and/or private keys for
 A simple cryptocurrency wallet contains pairs of public and private cryptographic keys. The keys can be used to track ownership, receive or spend
A simple cryptocurrency wallet contains pairs of public and private cryptographic keys. The keys can be used to track ownership, receive or spend
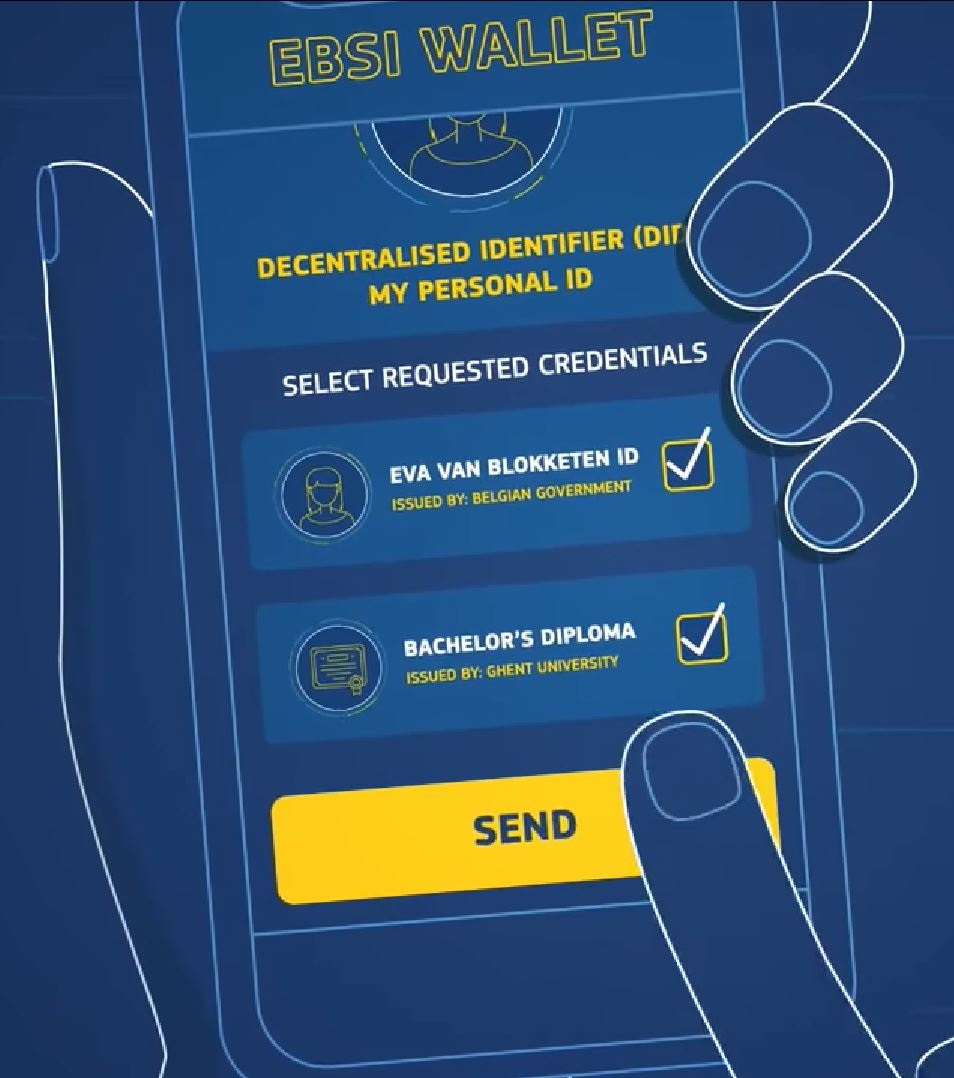 Some wallets are specifically designed to be compatible with a framework. The European Union is creating an eIDAS compatible European Self-Sovereign Identity Framework (ESSIF) which runs on the European Blockchain Services Infrastructure (EBSI). The EBSI wallet is designed to (securely) provide information, an eID and to sign 'transactions'.
Some wallets are specifically designed to be compatible with a framework. The European Union is creating an eIDAS compatible European Self-Sovereign Identity Framework (ESSIF) which runs on the European Blockchain Services Infrastructure (EBSI). The EBSI wallet is designed to (securely) provide information, an eID and to sign 'transactions'.
 A sequential deterministic wallet utilizes a simple method of generating addresses from a known starting string or "seed". This would utilize a
A sequential deterministic wallet utilizes a simple method of generating addresses from a known starting string or "seed". This would utilize a
Air-gap jumpers on cyber.bgu.ac.il
/ref> When using a software wallet for receiving cryptocurrency, access to the receiving wallet is not needed—the sending party only need know the destination address, thus anyone can send cryptocurrency to an address. Only the one who has the private key of the corresponding (public key) address otherwise has access.
 A cryptocurrency wallet is a device, physical medium, program or a service which stores the public and/or private keys for
A cryptocurrency wallet is a device, physical medium, program or a service which stores the public and/or private keys for cryptocurrency
A cryptocurrency, crypto-currency, or crypto is a digital currency designed to work as a medium of exchange through a computer network that is not reliant on any central authority, such as a government or bank, to uphold or maintain it. It i ...
transactions. In addition to this basic function of storing the keys, a cryptocurrency wallet more often also offers the functionality of encrypting
In cryptography, encryption is the process of Code, encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can ...
and/or signing information. Signing can for example result in executing a smart contract, a cryptocurrency transaction (see "bitcoin transaction" image), identification or legally signing a 'document' (see "application form" image).
Technology
Private and public key generation
A cryptocurrency wallet works by a theoretical or random number being generated and used with a length that depends on the algorithm size of the cryptocurrency's technology requirements. The number is then converted to a private key using the specific requirements of the cryptocurrency cryptography algorithm requirement. A public key is then generated from the private key using whichever cryptographic algorithm requirements are required. The private key is utilised by the owner to access and send cryptocurrency and is private to the owner, whereas the public key is to be shared to any third party to receive cryptocurrency. Up to this stage no computer or electronic device is required and all key pairs can be mathematically derived and written down by hand. The private key and public key pair (known as an address) are not known by the blockchain or anyone else. The blockchain will only record the transaction of the public address when cryptocurrency is sent to it, thus recording in the blockchain ledger the transaction of the public address.Duplicate private keys
Collision (two or more wallets having the same private key) is theoretically possible, since keys can be generated without being used for transactions, and are therefore offline until recorded in the blockchain ledger. However, this possibility is negated because the theoretical probability of two or more private keys being the same is extremely low. The number of possible wallets and thus private keys is extremely high, so duplicating or hacking a certain key would be inconceivable.Seed phrases
In modern convention a seed phrase is now utilised which is a random 12 to 24 (or even greater) list of dictionary words which is an unencrypted form of the private key. (Words are easier tomemorize
Memorization is the process of committing something to memory. It is a mental process undertaken in order to store in memory for later recall visual, auditory, or tactical information.
The scientific study of memory is part of cognitive neurosc ...
than numerals.) When online, exchange and hardware wallets are generated using random numbers, and a seed phrase is asked to be recorded by the user, hence when access to the wallet becomes misplaced, damaged or compromised, the seed phrase can be used to re-access the wallet and associated keys and cryptocurrency in toto.
Wallets
A number of technologies known as wallets exist that store the key value pair of private and public key known as wallets. A wallet hosts the details of the key pair making transacting cryptocurrency possible. Multiple methods exist for storing keys or seeds in a wallet.Crypto wallets vis-à-vis dapp browsers
Dapp
A decentralised application (DApp, dApp, Dapp, or dapp) is an application that can operate autonomously, typically through the use of smart contracts, that run on a decentralized computing, blockchain or other distributed ledger system. Like ...
browsers are specialized software that supports decentralized applications. Dapp browsers are considered to be the browsers of Web3
Web3 (also known as Web 3.0) is an idea for a new iteration of the World Wide Web which incorporates concepts such as decentralization, blockchain technologies, and token-based economics. Some technologists and journalists have contrasted it w ...
and are the gateway to access the decentralized applications which are working based on blockchain technology. That means all dapp browsers must have a unique code system to unify all the different codes of the dapps.
While crypto wallets are focused on the exchange, purchase, sale of digital assets and support narrowly targeted applications, the browsers support different kinds of applications of various formats, including exchange, games, NFTs marketplaces, etc.
Technical specifications of different browsers may or may not include features such as:
*Full support for all modern Web2.0 technologies;
*Built-in Ethereum mainnet/testnet RPC, fully compatible with Web3.0;
*Built-in Ethereum wallet (using smart contracts);
* Dapp naming support
Characteristics
In addition to the basic function of storing the keys, a cryptocurrency wallet may also have one or more of the following characteristics.Simple cryptocurrency wallet
 A simple cryptocurrency wallet contains pairs of public and private cryptographic keys. The keys can be used to track ownership, receive or spend
A simple cryptocurrency wallet contains pairs of public and private cryptographic keys. The keys can be used to track ownership, receive or spend cryptocurrencies
A cryptocurrency, crypto-currency, or crypto is a digital currency designed to work as a medium of exchange through a computer network that is not reliant on any central authority, such as a government or bank
A bank is a financial i ...
. A public key allows others to make payments to the address derived from it, whereas a private key enables the spending of cryptocurrency from that address.
The cryptocurrency itself is not in the wallet. In the case of bitcoin
Bitcoin ( abbreviation: BTC; sign: ₿) is a decentralized digital currency that can be transferred on the peer-to-peer bitcoin network. Bitcoin transactions are verified by network nodes through cryptography and recorded in a public distr ...
and cryptocurrencies derived from it, the cryptocurrency is decentrally stored and maintained in a publicly available distributed ledger
A distributed ledger (also called a shared ledger or distributed ledger technology or DLT) is the consensus of replicated, shared, and synchronized digital data that is geographically spread (distributed) across many sites, countries, or institutio ...
called the ''blockchain
A blockchain is a type of distributed ledger technology (DLT) that consists of growing lists of records, called ''blocks'', that are securely linked together using cryptography. Each block contains a cryptographic hash of the previous block, a ...
''.
eID wallet
 Some wallets are specifically designed to be compatible with a framework. The European Union is creating an eIDAS compatible European Self-Sovereign Identity Framework (ESSIF) which runs on the European Blockchain Services Infrastructure (EBSI). The EBSI wallet is designed to (securely) provide information, an eID and to sign 'transactions'.
Some wallets are specifically designed to be compatible with a framework. The European Union is creating an eIDAS compatible European Self-Sovereign Identity Framework (ESSIF) which runs on the European Blockchain Services Infrastructure (EBSI). The EBSI wallet is designed to (securely) provide information, an eID and to sign 'transactions'.
Multisignature wallet
In contrast to simple cryptocurrency wallets requiring just one party to sign a transaction,multisignature
A cryptocurrency wallet is a device, physical medium, program or a service which stores the public and/or private keys for cryptocurrency transactions. In addition to this basic function of storing the keys, a cryptocurrency wallet more often a ...
wallets require multiple parties to sign a transaction. Multisignature wallets are designed for increased security. Usually, a multisignature algorithm produces a joint signature that is more compact than a collection of distinct signatures from all users.
Smart contract
In the cryptocurrency space, smart contracts are digitally signed in the same way a cryptocurrency transaction is signed. The signing keys are held in a cryptocurrency wallet.Key derivation
Sequential deterministic wallet
 A sequential deterministic wallet utilizes a simple method of generating addresses from a known starting string or "seed". This would utilize a
A sequential deterministic wallet utilizes a simple method of generating addresses from a known starting string or "seed". This would utilize a cryptographic hash function
A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with fixed size of n bits) that has special properties desirable for cryptography:
* the probability of a particular n-bit output re ...
, e.g. SHA-256
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published in 2001. They are built using the Merkle–Damgård construction, from a one-way compression ...
(seed + n), where n is an ASCII
ASCII ( ), abbreviated from American Standard Code for Information Interchange, is a character encoding standard for electronic communication. ASCII codes represent text in computers, telecommunications equipment, and other devices. Because of ...
-coded number that starts from 1 and increments as additional keys are needed.
Hierarchical deterministic wallet
The hierarchical deterministic (HD) wallet was publicly described in BIP32. As a deterministic wallet, it also derives keys from a single master root seed, but instead of having a single "chain" of keypairs, an HD wallet supports multiple key pair chains. This allows a single key string to be used to generate an entiretree
In botany, a tree is a perennial plant with an elongated stem, or trunk, usually supporting branches and leaves. In some usages, the definition of a tree may be narrower, including only woody plants with secondary growth, plants that are ...
of key pairs with a stratified structure. The single master string serves as the root
In vascular plants, the roots are the organs of a plant that are modified to provide anchorage for the plant and take in water and nutrients into the plant body, which allows plants to grow taller and faster. They are most often below the sur ...
of the tree, and the hierarchy scheme allows the private keys generated from a master private key to be themselves master private keys, which can in turn be treated as deterministic wallets in their own right.
BIP39 proposed the use of a set of human-readable words to derive the master private key of a wallet. This mnemonic
A mnemonic ( ) device, or memory device, is any learning technique that aids information retention or retrieval (remembering) in the human memory for better understanding.
Mnemonics make use of elaborative encoding, retrieval cues, and imag ...
phrase allows for easier wallet backup and recovery, due to all the keys of a wallet being derivable from a single plaintext string.
Armory deterministic wallet
Bitcoin Armory, anopen source
Open source is source code that is made freely available for possible modification and redistribution. Products include permission to use the source code, design documents, or content of the product. The open-source model is a decentralized sof ...
, Python
Python may refer to:
Snakes
* Pythonidae, a family of nonvenomous snakes found in Africa, Asia, and Australia
** ''Python'' (genus), a genus of Pythonidae found in Africa and Asia
* Python (mythology), a mythical serpent
Computing
* Python (pro ...
-based, wallet-management application for the Bitcoin network, utilized its own implementation the hierarchical deterministic scheme and served as inspiration for the BIP32 standard.
Non-deterministic wallet
In a non-deterministic wallet, each key is randomly generated on its own accord, and they are not seeded from a common key. Therefore, any backups of the wallet must store each and every single private key used as an address, as well as a buffer of 100 or so future keys that may have already been given out as addresses but not received payments yet.Concerns
Wallet access permissions
When choosing a wallet, the owner must keep in mind who is supposed to have access to (a copy of) the private keys and thus potentially has signing capabilities. In case of cryptocurrency the user needs to trust the provider to keep the cryptocurrency safe, just like with abank
A bank is a financial institution that accepts deposits from the public and creates a demand deposit while simultaneously making loans. Lending activities can be directly performed by the bank or indirectly through capital markets.
Because ...
. Trust was misplaced in the case of the Mt. Gox
Mt. Gox was a bitcoin exchange based in Shibuya, Tokyo, Japan. Launched in 2010, it was handling over 70% of all bitcoin (BTC) transactions worldwide by early 2014, when it abruptly ceased operations amid revelations of its involvement in the ...
exchange, which 'lost' most of their clients' bitcoins. Downloading a cryptocurrency wallet from a wallet provider to a computer or phone does not automatically mean that the owner is the only one who has a copy of the private keys. For example, with Coinbase
Coinbase Global, Inc., branded Coinbase, is an American publicly traded company that operates a cryptocurrency exchange platform. Coinbase is a distributed company; all employees operate via remote work and the company lacks a physical headq ...
, it is possible to install a wallet on a phone and to also have access to the same wallet through their website.
Vulnerabilities
A wallet can also have known or unknownvulnerabilities
Vulnerability refers to "the quality or state of being exposed to the possibility of being attacked or harmed, either physically or emotionally."
A window of vulnerability (WOV) is a time frame within which defensive measures are diminished, com ...
. A supply chain attack
A supply chain attack is a cyber-attack that seeks to damage an organization by targeting less secure elements in the supply chain. A supply chain attack can occur in any industry, from the financial sector, oil industry, to a government sector. ...
or side-channel attack
In computer security, a side-channel attack is any attack based on extra information that can be gathered because of the fundamental way a computer protocol or algorithm is implemented, rather than flaws in the design of the protocol or algorit ...
are ways of a vulnerability introduction. In extreme cases even a computer which is not connected to any network can be hacked./ref> When using a software wallet for receiving cryptocurrency, access to the receiving wallet is not needed—the sending party only need know the destination address, thus anyone can send cryptocurrency to an address. Only the one who has the private key of the corresponding (public key) address otherwise has access.
See also
*Cryptocurrency
A cryptocurrency, crypto-currency, or crypto is a digital currency designed to work as a medium of exchange through a computer network that is not reliant on any central authority, such as a government or bank, to uphold or maintain it. It i ...
*Cryptocurrency and security
Cryptocurrency and crime describes notable examples of cybercrime related to theft (or the otherwise illegal acquisition) of cryptocurrencies and some of the methods or security vulnerabilities commonly exploited. Cryptojacking is a form of cyb ...
* Private and Public key cryptography
* Mobile payment
A mobile payment, also referred to as mobile money, mobile money transfer and mobile wallet, is any of various payment processing services operated under financial regulations and performed from or via a mobile device, as the cardinal class of d ...
References
{{Cryptocurrencies, state=collapsed BitcoinWallet
A wallet is a flat case or pouch often used to carry small personal items such as paper currency, credit cards; identification documents such as driver's license, identification card, club card; photographs, transit pass, business cards and oth ...