|
Zsh 5
The Z shell (Zsh) is a Unix shell that can be used as an interactive login shell and as a command interpreter for shell scripting. Zsh is an extended Bourne shell with many improvements, including some features of Bash, ksh, and tcsh. History Paul Falstad wrote the first version of Zsh in 1990 while a student at Princeton University. The name ''zsh'' derives from the name of Yale professor Zhong Shao (then a teaching assistant at Princeton University) – Paul Falstad regarded Shao's login-id, "zsh", as a good name for a shell. Zsh was at first intended to be a subset of csh for the Commodore Amiga, but expanded far beyond that. By the time of the release of version 1.0 in 1990 the aim was to be a cross between ksh and tcsh – a powerful "command and programming language" that is well-designed and logical (like ksh), but also built for humans (like tcsh), with all the neat features like spell checking, login/logout watching and termcap support that were "probably too weird ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
C (programming Language)
C (''pronounced like the letter c'') is a General-purpose language, general-purpose computer programming language. It was created in the 1970s by Dennis Ritchie, and remains very widely used and influential. By design, C's features cleanly reflect the capabilities of the targeted CPUs. It has found lasting use in operating systems, device drivers, protocol stacks, though decreasingly for application software. C is commonly used on computer architectures that range from the largest supercomputers to the smallest microcontrollers and embedded systems. A successor to the programming language B (programming language), B, C was originally developed at Bell Labs by Ritchie between 1972 and 1973 to construct utilities running on Unix. It was applied to re-implementing the kernel of the Unix operating system. During the 1980s, C gradually gained popularity. It has become one of the measuring programming language popularity, most widely used programming languages, with C compilers avail ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
UnxUtils
UnxUtils is a collection of ports of common GNU Unix-like utilities to native Win32, with executables only depending on the Microsoft C- runtime msvcrt.dll. The collection was last updated externally on April 15, 2003, by Karl M. Syring. The most recent release package available was an open-source project, UnxUtils at SourceForge, with the latest binary release in March, 2007 (though the files within are dated from the year 2000). The independent distribution included a main zip archive (UnxUtils.zip, 3,365,638 bytes) complemented by more recent updates (UnxUpdates.zip, 878,847 bytes, brought some binaries up to year 2003), but the SourceForge project has no UnxUpdates.zip package. An alternative source of Unix-like utilities for Windows is GnuWin32; it has later versions of many programs, but requires supporting files (e.g. DLLs) in many cases. The utilities included are: * agrep.exe *ansi2knr.exe *basename.exe * bc.exe *bison.exe *bunzip2.exe * bzip2.exe *bzip2recover.exe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Variable (computer Science)
In computer programming, a variable is an abstract storage location paired with an associated symbol, symbolic name, which contains some known or unknown quantity of information referred to as a ''value (computer science), value''; or in simpler terms, a variable is a named container for a particular set of bits or :simple:Data_type, type of data (like Integer (computer science), integer, Floating-point arithmetic, float, String (computer science), string etc...). A variable can eventually be associated with or identified by a memory address. The variable name is the usual way to Reference (computer science), reference the stored value, in addition to referring to the variable itself, depending on the context. This separation of name and content allows the name to be used independently of the exact information it represents. The identifier in computer source code can be Name binding, bound to a Value (computer science), value during Run time (program lifecycle phase), run time, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Find (Unix)
In Unix-like and some other operating systems, find is a command-line utility that locates files based on some user-specified criteria and either prints the pathname of each matched object or, if another action is requested, performs that action on each matched object. It initiates a search from a desired starting location and then recursively traverses the nodes (directories) of a hierarchical structure (typically a tree). find can traverse and search through different file systems of partitions belonging to one or more storage devices mounted under the starting directory. The possible search criteria include a pattern to match against the filename or a time range to match against the modification time or access time of the file. By default, find returns a list of all files below the current working directory, although users can limit the search to any desired maximum number of levels under the starting directory. The related locate programs use a database of indexed files ob ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Glob (programming)
In computer programming, glob () patterns specify sets of filenames with wildcard characters. For example, the Unix Bash shell command mv *.txt textfiles/ moves (mv) all files with names ending in .txt from the current directory to the directory textfiles. Here, * is a wildcard standing for "any string of characters except /" and *.txt is a glob pattern. The other common wildcard is the question mark (?), which stands for one character. For example, mv ?.txt shorttextfiles/ will move all files named with a single character followed by .txt from the current directory to directory shorttextfiles, while ??.txt would match all files whose name consists of 2 characters followed by .txt. In addition to matching filenames, globs are also used widely for matching arbitrary strings ( wildcard matching). In this capacity a common interface is fnmatch. Origin The glob command, short for ''global'', originates in the earliest versions of Bell Labs' Unix. The command interpreters of the ear ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Command History
Command history is a feature in many operating system shells, computer algebra programs, and other software that allows the user to recall, edit and rerun previous commands. Command line history was added to Unix in Bill Joy's C shell of 1978; Joy took inspiration from an earlier implementation in Interlisp. It quickly became popular because it made the C shell fast and easy to use. History has since become a standard feature in other shells, including ksh, Bash and Microsoft's cmd.exe. History addressed two important scenarios: # Executing the same command or a short sequence of commands over and over. An example might be a developer frequently compiling and running a program. # Correcting mistakes or rerunning a command with only a small modification. In Joy's original C shell, the user could refer to a previous command by typing an exclamation, !, followed by additional characters to specify a particular command, only certain words, or to edit it in some way before pa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Command-line Completion
Command-line completion (also tab completion) is a common feature of command-line interpreters, in which the program automatically fills in partially typed commands. Command line interpreters are programs that allow a user to interact with the underlying operating system by typing commands at a command prompt using a command line interface (CLI), in contrast to pointing and clicking a mouse in a Graphical User Interface (GUI). Command-line completion allows the user to type the first few characters of a command, program, or filename, and press a completion key (normally ) to fill in the rest of the item. The user then presses or to run the command or open the file. Command-line completion is useful in several ways, as illustrated by the animation accompanying this article. Commonly accessed commands, especially ones with long names, require fewer keystrokes to reach. Commands with long or difficult to spell filenames can be entered by typing the first few characters and pressin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zsh 5
The Z shell (Zsh) is a Unix shell that can be used as an interactive login shell and as a command interpreter for shell scripting. Zsh is an extended Bourne shell with many improvements, including some features of Bash, ksh, and tcsh. History Paul Falstad wrote the first version of Zsh in 1990 while a student at Princeton University. The name ''zsh'' derives from the name of Yale professor Zhong Shao (then a teaching assistant at Princeton University) – Paul Falstad regarded Shao's login-id, "zsh", as a good name for a shell. Zsh was at first intended to be a subset of csh for the Commodore Amiga, but expanded far beyond that. By the time of the release of version 1.0 in 1990 the aim was to be a cross between ksh and tcsh – a powerful "command and programming language" that is well-designed and logical (like ksh), but also built for humans (like tcsh), with all the neat features like spell checking, login/logout watching and termcap support that were "probably too weird ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
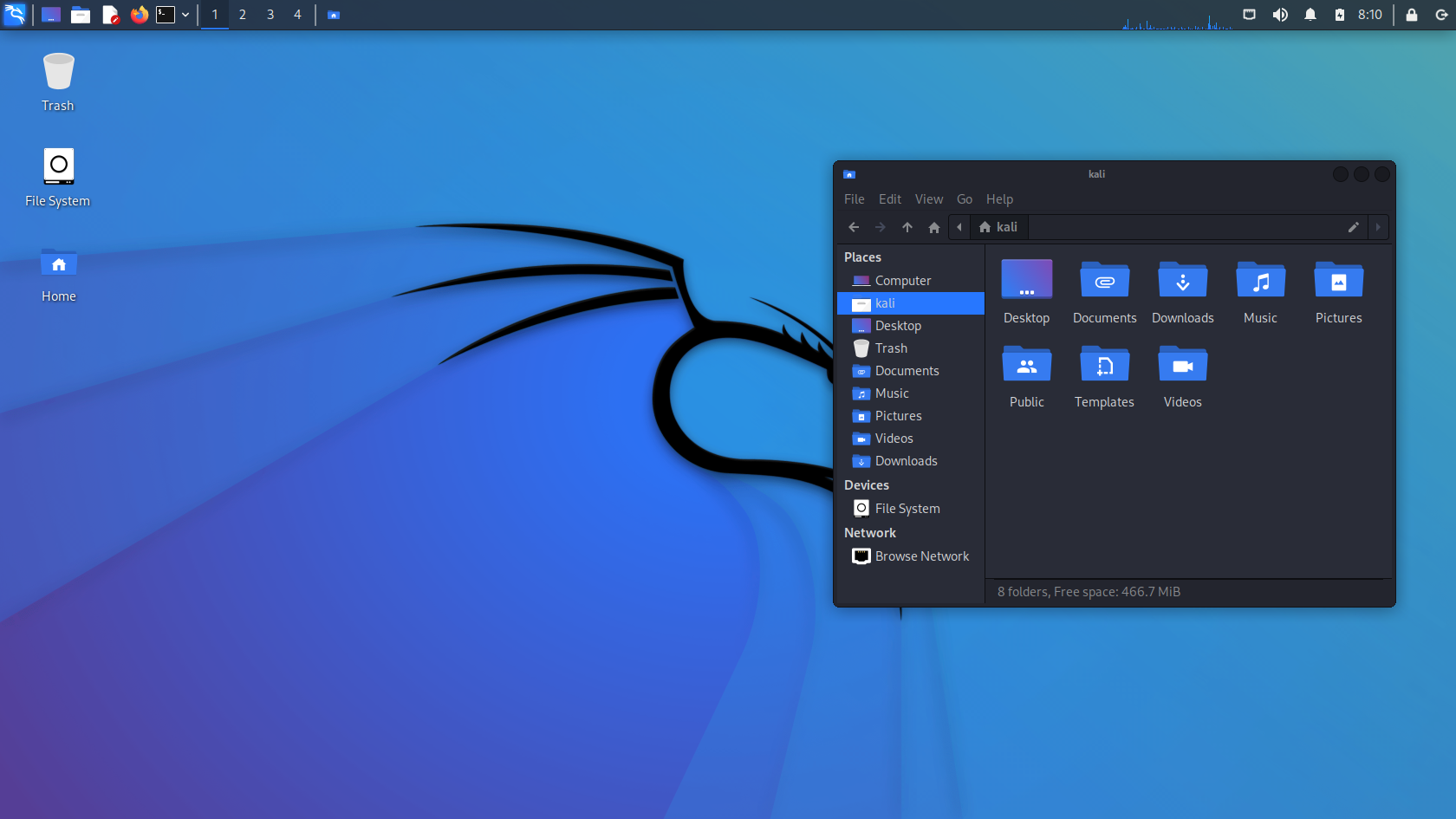
Kali Linux
Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is maintained and funded by Offensive Security. Kali Linux has around 600 penetration-testing programs (tools), including Armitage (a graphical cyber attack management tool), Nmap (a port scanner), Wireshark (a packet analyzer), metasploit (penetration testing framework), John the Ripper (a password cracker), sqlmap (automatic SQL injection and database takeover tool), Aircrack-ng (a software suite for penetration-testing wireless LANs), Burp suite and OWASP ZAP web application security scanners, etc. It was developed by Mati Aharoni and Devon Kearns of Offensive Security through the rewrite of BackTrack, their previous information security testing Linux distribution based on Knoppix. The name was inspired by the Hindu goddess Kali. Kali Linux is based on the Debian ''Testing'' branch. Most packages Kali uses are imported from the Debian repositories. Kali Linux's pop ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GPLv2
The GNU General Public License (GNU GPL or simply GPL) is a series of widely used free software licenses that guarantee end users the four freedoms to run, study, share, and modify the software. The license was the first copyleft for general use and was originally written by the founder of the Free Software Foundation (FSF), Richard Stallman, for the GNU Project. The license grants the recipients of a computer program the rights of the Free Software Definition. These GPL series are all copyleft licenses, which means that any derivative work must be distributed under the same or equivalent license terms. It is more restrictive than the Lesser General Public License and even further distinct from the more widely used permissive software licenses BSD, MIT, and Apache. Historically, the GPL license family has been one of the most popular software licenses in the free and open-source software domain. Prominent free software programs licensed under the GPL include the Linux kernel a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MacOS Catalina
macOS Catalina (version 10.15) is the sixteenth major release of macOS, Apple Inc.'s desktop operating system for Macintosh computers. It is the successor to macOS Mojave and was announced at WWDC 2019 on June 3, 2019 and released to the public on October 7, 2019. Catalina is the first version of macOS to support only 64-bit applications and the first to include Activation Lock. It is also the last version of macOS to have the major version number of 10; its successor, Big Sur, released on November 12, 2020, is version 11. In order to increase web compatibility, Safari, Chromium and Firefox have frozen the OS in the user agent running in subsequent releases of macOS at 10.15.7 Catalina. The operating system is named after Santa Catalina Island, which is located off the coast of southern California. System requirements macOS Catalina officially runs on all standard configuration Macs that supported Mojave. 2010–2012 Mac Pros, which could run Mojave only with a GPU upgra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |