|
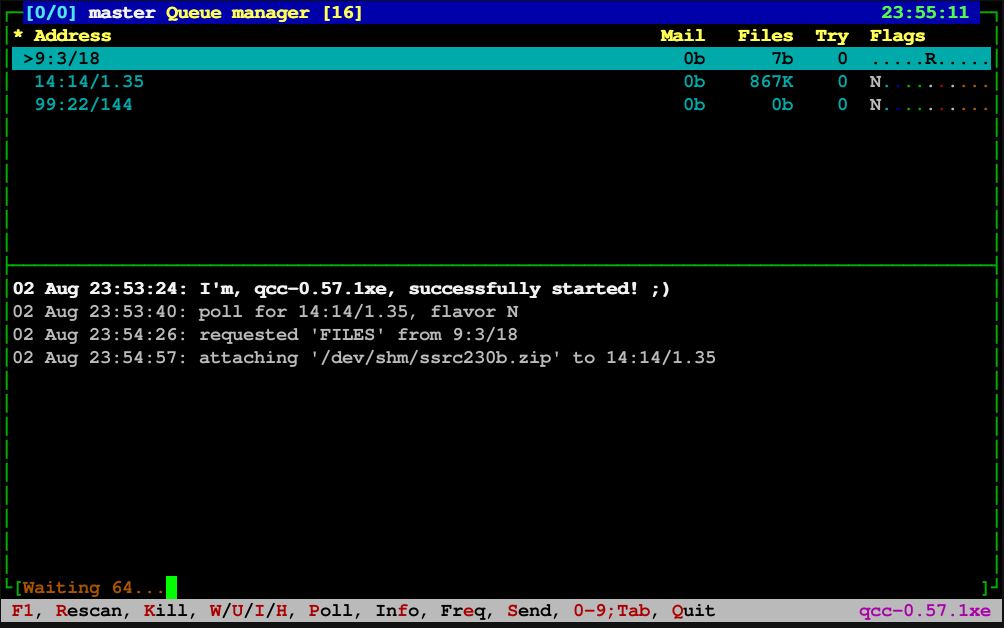
YMODEM
YMODEM is a file transfer protocol used between microcomputers connected together using modems. It was primarily used to transfer files to and from bulletin board systems. YMODEM was developed by Chuck Forsberg as an expansion of XMODEM and was first implemented in his CP/M YAM program. Initially also known as YAM, it was formally given the name "YMODEM" in 1985 by Ward Christensen, author of the original XMODEM. YMODEM extended XMODEM in three ways, combining features found in other extended XMODEM varieties. Like XMODEM-CRC, YMODEM replaced the 8-bit checksum with a 16-bit cyclic redundancy check (CRC), but made it the default form of correction instead of optional. From TeLink it added the "block 0" header that sent the filename and size, which allowed batch transfers (multiple files in a single session) and eliminated the need to add padding at the end of the file. Finally, YMODEM allowed the block size to be increased from the original 128 bytes of data to 1024, as in XMOD ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
XMODEM
XMODEM is a simple file transfer protocol developed as a quick hack by Ward Christensen for use in his 1977 MODEM.ASM terminal program. It allowed users to transmit files between their computers when both sides used MODEM. Keith Petersen made a minor update to always turn on "quiet mode", and called the result XMODEM. XMODEM, like most file transfer protocols, breaks up the original data into a series of " packets" that are sent to the receiver, along with additional information allowing the receiver to determine whether that packet was correctly received. If an error is detected, the receiver requests that the packet be re-sent. A string of bad packets causes the transfer to abort. XMODEM became extremely popular in the early bulletin board system (BBS) market, largely because it was simple to implement. It was also fairly inefficient, and as modem speeds increased, this problem led to the development of a number of modified versions of XMODEM to improve performance or address ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protocol For File Transfer
This article lists communication protocols that are designed for file transfer over a telecommunications network. Protocols for shared file systems—such as 9P and the Network File System—are beyond the scope of this article, as are file synchronization protocols. Protocols for packet-switched networks A packet-switched network transmits data that is divided into units called '' packets''. A packet comprises a header (which describes the packet) and a payload (the data). The Internet is a packet-switched network, and most of the protocols in this list are designed for its protocol stack, the IP protocol suite. They use one of two transport layer protocols: the Transmission Control Protocol (TCP) or the User Datagram Protocol (UDP). In the tables below, the "Transport" column indicates which protocol(s) the transfer protocol uses at the transport layer. Some protocols designed to transmit data over UDP also use a TCP port for oversight. The " Server port" column indica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chuck Forsberg
Charles Alton "Chuck" Forsberg (May 6, 1944 – September 24, 2015) developed two data transmission protocols popular in the 1990s, for uploading and downloading files from dial-up bulletin board systems. He received a Dvorak Award for Excellence in Telecommunications in 1992 for developing ZMODEM. He was also the project engineer on the Tektronix 4010-series graphics terminals. The widely adopted ZMODEM uses a sliding window protocol. Rather than wait for positive acknowledgment after each block is sent, it sends blocks in rapid succession and resends unacknowledged blocks later. By avoiding delays due to latency, the bandwidth usable for transmission more closely approached the bandwidth of the underlying link. ZMODEM could also resume interrupted transfers without retransmitting the already-received blocks. In addition to developing the protocol, Forsberg developed software for sending and receiving files using ZMODEM. Forsberg then wrote a version, Zmodem G, which was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File Transfer
File transfer is the transmission of a computer file through a communication channel from one computer system to another. Typically, file transfer is mediated by a communications protocol. In the history of computing, numerous file transfer protocols have been designed for different contexts. Protocols A file transfer protocol is a convention that describes how to transfer files between two computing endpoints. As well as the stream of bits from a file stored as a single unit in a file system, some may also send relevant metadata such as the filename, file size and timestamp – and even file-system permissions and file attributes. Some examples: * FTP is an older cross-platform file transfer protocol * SSH File Transfer Protocol In computing, the SSH File Transfer Protocol, also known as Secure File Transfer Protocol (SFTP), is a network protocol that provides file access, file transfer, and file management over any reliable data stream. It was designed by the In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bulletin Board System
A bulletin board system (BBS), also called a computer bulletin board service (CBBS), is a computer server running list of BBS software, software that allows users to connect to the system using a terminal program. Once logged in, the user performs functions such as uploading and downloading software and data, reading news and bulletins, and exchanging messages with other users through public Internet forum, message boards and sometimes via direct synchronous conferencing, chatting. In the early 1980s, message networks such as FidoNet were developed to provide services such as M+NetMail, NetMail, which is similar to internet-based email. Many BBSes also offered BBS door, online games in which users could compete with each other. BBSes with multiple phone lines often provided chat rooms, allowing users to interact with each other. Bulletin board systems were in many ways a precursor to the modern form of the World Wide Web, social networking service, social networks, and other aspe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FidoNet
__ / \ /, oo \ (_, /_) _`@/_ \ _ , , \ \\ , (*) , \ )) ______ , __U__, / \// / FIDO \ _//, , _\ / (________) (_/(_, (____/ (c) John Madill FidoNet logo by John Madill FidoNet is a worldwide computer network that is used for communication between bulletin board systems (BBSes). It uses a store-and-forward system to exchange private (email) and public (forum) messages between the BBSes in the network, as well as other files and protocols in some cases. The FidoNet system was based on several small interacting programs, only one of which needed to be Porting, ported to support other BBS software. FidoNet was one of the few networks that was supported by almost all BBS software, as well as a number of non-BBS online services. This modular construction also allowed FidoNet to easily upgrade to new data c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
16550 UART
The 16550 UART (universal asynchronous receiver-transmitter) is an integrated circuit designed for implementing the interface for serial communications. The corrected -A version was released in 1987 by National Semiconductor. It is frequently used to implement the serial port for IBM PC compatible personal computers, where it is often connected to an RS-232 interface for modems, serial mice, printers, and similar peripherals. It was the first serial chip used in the IBM PS/2 line, which were introduced in 1987. The part was originally made by National Semiconductor. Similarly numbered devices, with varying levels of compatibility with the original National Semiconductor part, are made by other manufacturers. A UART function that is register-compatible with the 16550 is usually a feature of multifunction I/O cards for IBM PC-compatible computers and may be integrated on the motherboard of other compatible computers. Replacement of the factory-installed 8250 UART was a common u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microcom Networking Protocol
The Microcom Networking Protocols, almost always shortened to MNP, is a family of error-correcting protocols commonly used on early high-speed (2400 bit/s and higher) modems. Originally developed for use on Microcom's own family of modems, the protocol was later openly licensed and used by most of the modem industry, notably the "big three", Telebit, USRobotics and Hayes. MNP was later supplanted by V.42bis, which was used almost universally starting with the first V.32bis modems in the early 1990s. Overview Although XMODEM was introduced 1977, as late as 1985, ''The New York Times'' described XMODEM first, then discussed MNP as a leading contender, and that 9600 baud modems "are beginning to make their appearance." By 1988, the ''Times'' was talking about 9600 and 19.2K, and that "At least 100 other brands of modems follow" MNP (compared to Hayes's use of LAP-B). Error correction basics Modems are, by their nature, error-prone devices. Noise on the telephone line, a common oc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Latency (engineering)
Latency, from a general point of view, is a time delay between the Causality, cause and the effect of some physical change in the system being observed. Lag (video games), Lag, as it is known in Gaming culture, gaming circles, refers to the latency between the input to a simulation and the visual or auditory response, often occurring because of network delay in online games. The original meaning of “latency”, as used widely in psychology, medicine and most other disciplines, derives from “latent”, a word of Latin origin meaning “hidden”. Its different and relatively recent meaning (this topic) of “lateness” or “delay” appears to derive from its superficial similarity to the word “late”, from the old English “laet”. Latency is physically a consequence of the limited velocity at which any Event (relativity), physical interaction can propagate. The magnitude of this velocity is always less than or equal to the speed of light. Therefore, every physical s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Flow Control (data)
In data communications, flow control is the process of managing the rate of data transmission between two nodes to prevent a fast sender from overwhelming a slow receiver. Flow control should be distinguished from congestion control, which is used for controlling the flow of data when congestion has actually occurred. Flow control mechanisms can be classified by whether or not the receiving node sends feedback to the sending node. Flow control is important because it is possible for a sending computer to transmit information at a faster rate than the destination computer can receive and process it. This can happen if the receiving computers have a heavy traffic load in comparison to the sending computer, or if the receiving computer has less processing power than the sending computer. Stop-and-wait Stop-and-wait flow control is the simplest form of flow control. In this method the message is broken into multiple frames, and the receiver indicates its readiness to receive a fra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |