|
XACML Architecture
__NOTOC__ The eXtensible Access Control Markup Language (XACML) is an XML-based standard markup language for specifying access control policies. The standard, published by OASIS, defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests according to the rules defined in policies. XACML is primarily an attribute-based access control system. In XACML, attributes – information about the subject accessing a resource, the resource to be addressed, and the environment – act as inputs for the decision of whether access is granted or not. XACML can also be used to implement role-based access control.See for example In XACML, access control decisions to be taken are expressed as Rules. Each Rule comprises a series of conditions which decide whether a given request is approved or not. If a Rule is applicable to a request but the conditions within the Rule fail to evalua ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Declarative Programming
In computer science, declarative programming is a programming paradigm—a style of building the structure and elements of computer programs—that expresses the logic of a computation without describing its control flow. Many languages that apply this style attempt to minimize or eliminate side effects by describing ''what'' the program must accomplish in terms of the problem domain, rather than describing ''how'' to accomplish it as a sequence of the programming language primitives (the ''how'' being left up to the language's implementation). This is in contrast with imperative programming, which implements algorithms in explicit steps. Declarative programming often considers programs as theories of a formal logic, and computations as deductions in that logic space. Declarative programming may greatly simplify writing parallel programs. Common declarative languages include those of database query languages (e.g., SQL, XQuery), regular expressions, logic programming ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proprietary Software
Proprietary software is computer software, software that grants its creator, publisher, or other rightsholder or rightsholder partner a legal monopoly by modern copyright and intellectual property law to exclude the recipient from freely sharing the software or modifying it, and—in some cases, as is the case with some patent-encumbered and EULA-bound software—from making use of the software on their own, thereby restricting their freedoms. Proprietary software is a subset of non-free software, a term defined in contrast to free and open-source software; non-commercial licenses such as CC BY-NC are not deemed proprietary, but are non-free. Proprietary software may either be closed-source software or source-available software. Types Origin Until the late 1960s, computers—especially large and expensive mainframe computers, machines in specially air-conditioned computer rooms—were usually leased to customers rather than Sales, sold. Service and all software available ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security Procedures
A computer is a machine that can be programmed to automatically carry out sequences of arithmetic or logical operations (''computation''). Modern digital electronic computers can perform generic sets of operations known as ''programs'', which enable computers to perform a wide range of tasks. The term computer system may refer to a nominally complete computer that includes the hardware, operating system, software, and peripheral equipment needed and used for full operation; or to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of industrial and consumer products use computers as control systems, including simple special-purpose devices like microwave ovens and remote controls, and factory devices like industrial robots. Computers are at the core of general-purpose devices such as personal computers and mobile devices such as smartphones. Computers power the Internet, which links billions of comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authorization
Authorization or authorisation (see American and British English spelling differences#-ise, -ize (-isation, -ization), spelling differences), in information security, computer security and identity management, IAM (Identity and Access Management), is the function of specifying rights/privileges for accessing resources, in most cases through an access policy, and then deciding whether a particular ''subject'' has privilege to access a particular ''resource''. Examples of ''subjects'' include human users, computer software and other Computer hardware, hardware on the computer. Examples of ''resources'' include individual files or an item's data, computer programs, computer Computer hardware, devices and functionality provided by computer applications. For example, user accounts for human resources staff are typically configured with authorization for accessing employee records. Authorization is closely related to access control, which is what enforces the authorization policy by d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Model-driven Security
Model-driven security (MDS) means applying model-driven approaches (and especially the concepts behind model-driven software development) to security. Development of the concept The general concept of Model-driven security in its earliest forms has been around since the late 1990s (mostly in university research), and was first commercialized around 2002. There is also a body of later scientific research in this area, which continues to this day. A more specific definition of Model-driven security specifically applies model-driven approaches to automatically generate technical security implementations from security requirements models. In particular, "Model driven security (MDS) is the tool supported process of modelling security requirements at a high level of abstraction, and using other information sources available about the system (produced by other stakeholders). These inputs, which are expressed in Domain Specific Languages (DSL), are then transformed into enforceable secur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PERMIS
PERMIS (PrivilEge and Role Management Infrastructure Standards) is a sophisticated policy-based authorization system that implements an enhanced version of the U.S. National Institute of Standards and Technology (NIST) standard Role-Based Access Control (RBAC) model. PERMIS supports the distributed assignment of both roles and attributes to users by multiple distributed attribute authorities, unlike the NIST model which assumes the centralised assignment of roles to users. PERMIS provides a cryptographically secure privilege management infrastructure ( PMI) using public key encryption technologies and X.509 Attribute certificates to maintain users' attributes. PERMIS does not provide any authentication mechanism, but leaves it up to the application to determine what to use. PERMIS's strength comes from its ability to be integrated into virtually any application and any authentication scheme like Shibboleth (Internet2), Kerberos, username/passwords, Grid proxy certificates and Pub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Discretionary Access Control
In computer security, discretionary access control (DAC) is a type of access control defined by the Trusted Computer System Evaluation Criteria (TCSEC) as a means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject (unless restrained by mandatory access control). Discretionary access control is commonly discussed in contrast to mandatory access control (MAC). Occasionally, a system as a whole is said to have "discretionary" or "purely discretionary" access control when that system lacks mandatory access control. On the other hand, systems can implement both MAC and DAC simultaneously, where DAC refers to one category of access controls that subjects can transfer among each other, and MAC refers to a second category of access controls that imposes constr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mandatory Access Control
In computer security, mandatory access control (MAC) refers to a type of access control by which a secured environment (e.g., an operating system or a database) constrains the ability of a ''subject'' or ''initiator'' to access or modify on an ''object'' or ''target''. In the case of operating systems, the subject is a process or thread, while objects are files, directories, TCP/ UDP ports, shared memory segments, or IO devices. Subjects and objects each have a set of security attributes. Whenever a subject attempts to access an object, the operating system kernel examines these security attributes, examines the authorization rules (aka ''policy'') in place, and decides whether to grant access. A database management system, in its access control mechanism, can also apply mandatory access control; in this case, the objects are tables, views, procedures, etc. In mandatory access control, the security policy is centrally controlled by a policy administrator and is guaranteed (in p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-pattern
An anti-pattern in software engineering, project management, and business processes is a common response to a recurring problem that is usually ineffective and risks being highly counterproductive. The term, coined in 1995 by computer programmer Andrew Koenig (programmer), Andrew Koenig, was inspired by the book ''Design Patterns'' (which highlights a number of design patterns in software development that its authors considered to be highly reliable and effective) and first published in his article in the ''Journal of Object-Oriented Programming''. A further paper in 1996 presented by Michael Ackroyd at the Object World West Conference also documented anti-patterns. It was, however, the 1998 book ''AntiPatterns'' that both popularized the idea and extended its scope beyond the field of software design to include software architecture and project management. Other authors have extended it further since to encompass environmental, organizational, and cultural anti-patterns. Definiti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
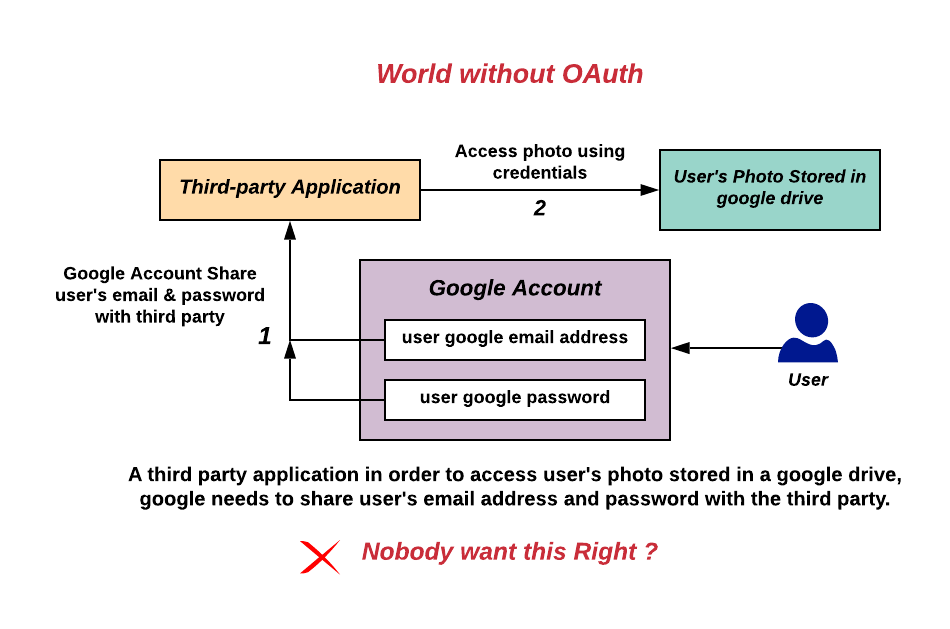
OAuth
OAuth (short for open authorization) is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Meta Platforms, Microsoft, and Twitter to permit users to share information about their accounts with third-party applications or websites. Generally, the OAuth protocol provides a way for resource owners to provide a client application with secure delegated access to server resources. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Assertion Markup Language
Security Assertion Markup Language (SAML, pronounced ''SAM-el'', ) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. SAML is an XML-based markup language for security assertions (statements that service providers use to make access-control decisions). SAML is also: * A set of XML-based protocol messages * A set of protocol message bindings * A set of profiles (utilizing all of the above) An important use case that SAML addresses is web-browser single sign-on (SSO). Single sign-on is relatively easy to accomplish within a security domain (using cookies, for example) but extending SSO across security domains is more difficult and resulted in the proliferation of non-interoperable proprietary technologies. The SAML Web Browser SSO profile was specified and standardized to promote interoperability.J. Hughes et al. ''Profiles for the OASIS Security Assertion Markup Langu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |