|
WARRIOR PRIDE
WARRIOR PRIDE is the GCHQ and NSA code name for a pair of spyware kits that can be installed on the iPhone and Android-based smartphones. Information about these kits was published by the press on 27 January 2014 from the documents leaked by Edward Snowden. Kits The iPhone kit was developed first; its code was ported from an undisclosed code base. The Android port was completed later (Q3 2010) and it was done in collaboration with Communications Security Establishment Canada. Although using different code, the modules of the kit have the same names on both platforms (all seemingly derived from The Smurfs cartoons), and correspond to their functionality as follows: * DREAMY SMURF – handles power management, which according to '' The Guardian'' includes "an ability to stealthily activate a phone that is apparently turned off" * NOSEY SMURF – "hot mic", turning on the microphone to listen in on conversations * TRACKER SMURF – high-precision geolocation * PORUS – " ke ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GCHQ
Government Communications Headquarters, commonly known as GCHQ, is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the United Kingdom. Primarily based at "The Doughnut" in the suburbs of Cheltenham, GCHQ is the responsibility of the country's Secretary of State for Foreign and Commonwealth Affairs (Foreign Secretary), but it is not a part of the Foreign Office and its Director ranks as a Permanent Secretary. GCHQ was originally established after the First World War as the Government Code and Cypher School (GC&CS) and was known under that name until 1946. During the Second World War it was located at Bletchley Park, where it was responsible for breaking the German Enigma codes. There are two main components of the GCHQ, the Composite Signals Organisation (CSO), which is responsible for gathering information, and the National Cyber Security Centre (NCSC), whi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-tamper Software
Anti-tamper software is software which makes it harder for an attacker to modify it. The measures involved can be passive such as obfuscation to make reverse engineering difficult or active tamper-detection techniques which aim to make a program malfunction or not operate at all if modified. It is essentially tamper resistance implemented in the software domain. It shares certain aspects but also differs from related technologies like copy protection and trusted hardware, though it is often used in combination with them. Anti-tampering technology typically makes the software somewhat larger and also has a performance impact. There are no provably secure software anti-tampering methods; thus, the field is an arms race between attackers and software anti-tampering technologies. Tampering can be malicious, to gain control over some aspect of the software with an unauthorized modification that alters the computer program code and behaviour. Examples include installing rootkits and ba ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency Operations
National may refer to: Common uses * Nation or country ** Nationality – a ''national'' is a person who is subject to a nation, regardless of whether the person has full rights as a citizen Places in the United States * National, Maryland, census-designated place * National, Nevada, ghost town * National, Utah, ghost town * National, West Virginia, unincorporated community Commerce * National (brand), a brand name of electronic goods from Panasonic * National Benzole (or simply known as National), former petrol station chain in the UK, merged with BP * National Car Rental, an American rental car company * National Energy Systems, a former name of Eco Marine Power * National Entertainment Commission, a former name of the Media Rating Council * National Motor Vehicle Company, Indianapolis, Indiana, USA 1900-1924 * National Supermarkets, a defunct American grocery store chain * National String Instrument Corporation, a guitar company formed to manufacture the first r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GCHQ Operations
Government Communications Headquarters, commonly known as GCHQ, is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the United Kingdom. Primarily based at "The Doughnut" in the suburbs of Cheltenham, GCHQ is the responsibility of the country's Secretary of State for Foreign and Commonwealth Affairs (Foreign Secretary), but it is not a part of the Foreign Office and its Director ranks as a Permanent Secretary. GCHQ was originally established after the First World War as the Government Code and Cypher School (GC&CS) and was known under that name until 1946. During the Second World War it was located at Bletchley Park, where it was responsible for breaking the German Enigma codes. There are two main components of the GCHQ, the Composite Signals Organisation (CSO), which is responsible for gathering information, and the National Cyber Security Centre (NCSC), whic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trojan Horses
The Trojan Horse was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's ''Iliad'', with the poem ending before the war is concluded, and it is only briefly mentioned in the ''Odyssey''. But in the ''Aeneid'' by Virgil, after a fruitless 10-year siege, the Greeks constructed a huge wooden horse at the behest of Odysseus, and hid a select force of men inside, including Odysseus himself. The Greeks pretended to sail away, and the Trojans pulled the horse into their city as a victory trophy. That night, the Greek force crept out of the horse and opened the gates for the rest of the Greek army, which had sailed back under cover of darkness. The Greeks entered and destroyed the city, ending the war. Metaphorically, a "Trojan horse" has come to mean any trick or stratagem that causes a target to invite a foe into a securely protected bastion or place. A malicious computer pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tailored Access Operations
The Office of Tailored Access Operations (TAO), now Computer Network Operations, and structured as S32, is a cyber-warfare intelligence-gathering unit of the National Security Agency (NSA). It has been active since at least 1998, possibly 1997, but was not named or structured as TAO until "the last days of 2000," according to General Michael Hayden. TAO identifies, monitors, infiltrates, and gathers intelligence on computer systems being used by entities foreign to the United States. History TAO is reportedly "the largest and arguably the most important component of the NSA's huge Signals Intelligence Directorate (SID), consisting of more than 1,000 military and civilian computer hackers, intelligence analysts, targeting specialists, computer hardware and software designers, and electrical engineers". Snowden leak A document leaked by former NSA contractor Edward Snowden describing the unit's work says TAO has software templates allowing it to break into commonly used hardw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Regin (malware)
Regin (also known as Prax or QWERTY) is a sophisticated malware and hacking toolkit used by United States' National Security Agency (NSA) and its British counterpart, the Government Communications Headquarters (GCHQ). It was first publicly revealed by Kaspersky Lab, Symantec, and The Intercept in November 2014. The malware targets specific users of Microsoft Windows-based computers and has been linked to the US intelligence-gathering agency NSA and its British counterpart, the GCHQ. ''The Intercept'' provided samples of Regin for download, including malware discovered at a Belgian telecommunications provider, Belgacom. Kaspersky Lab says it first became aware of Regin in spring 2012, but some of the earliest samples date from 2003. (The name Regin is first found on the VirusTotal website on 9 March 2011.) Among computers infected worldwide by Regin, 28 percent were in Russia, 24 percent in Saudi Arabia, 9 percent each in Mexico and Ireland, and 5 percent in each of India, Afghan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NSA ANT Catalog
The ANT catalog (or TAO catalog) is a classified product catalog by the U.S. National Security Agency (NSA) of which the version written in 2008–2009 was published by German news magazine ''Der Spiegel'' in December 2013. Forty-nine catalog pages with pictures, diagrams and descriptions of espionage devices and spying software were published. The items are available to the Tailored Access Operations unit and are mostly targeted at products from US companies such as Apple, Cisco and Dell. The source is believed to be someone different than Edward Snowden, who is largely responsible for the global surveillance disclosures since 2013. Companies whose products could be compromised have denied any collaboration with the NSA in developing these capabilities. In 2014, a project was started to implement the capabilities from the ANT catalog as open-source hardware and software. Background The Tailored Access Operations unit has existed since the late 90s. Its mission is to collec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Google Maps
Google Maps is a web mapping platform and consumer application offered by Google. It offers satellite imagery, aerial photography, street maps, 360° interactive panoramic views of streets ( Street View), real-time traffic conditions, and route planning for traveling by foot, car, bike, air (in beta) and public transportation. , Google Maps was being used by over 1 billion people every month around the world. Google Maps began as a C++ desktop program developed by brothers Lars and Jens Rasmussen at Where 2 Technologies. In October 2004, the company was acquired by Google, which converted it into a web application. After additional acquisitions of a geospatial data visualization company and a real-time traffic analyzer, Google Maps was launched in February 2005. The service's front end utilizes JavaScript, XML, and Ajax. Google Maps offers an API that allows maps to be embedded on third-party websites, and offers a locator for businesses and other organizations in numero ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
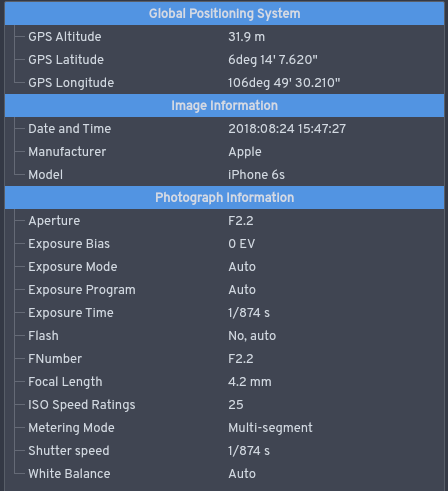
Exif
Exchangeable image file format (officially Exif, according to JEIDA/JEITA/CIPA specifications) is a standard that specifies formats for images, sound, and ancillary tags used by digital cameras (including smartphones), scanners and other systems handling image and sound files recorded by digital cameras. The specification uses the following existing encoding formats with the addition of specific metadata tags: JPEG lossy coding for compressed image files, TIFF Rev. 6.0 (RGB or YCbCr) for uncompressed image files, and RIFF WAV for audio files (linear PCM or ITU-T G.711 μ-law PCM for uncompressed audio data, and IMA-ADPCM for compressed audio data). It does not support JPEG 2000 or GIF encoded images. This standard consists of the Exif image file specification and the Exif audio file specification. Background Exif is supported by almost all camera manufacturers. The metadata tags defined in the Exif standard cover a broad spectrum: * Camera settings: This includes static ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Muslim
Muslims ( ar, المسلمون, , ) are people who adhere to Islam, a monotheistic religion belonging to the Abrahamic tradition. They consider the Quran, the foundational religious text of Islam, to be the verbatim word of the God of Abraham (or '' Allah'') as it was revealed to Muhammad, the main Islamic prophet. The majority of Muslims also follow the teachings and practices of Muhammad ('' sunnah'') as recorded in traditional accounts (''hadith''). With an estimated population of almost 1.9 billion followers as of 2020 year estimation, Muslims comprise more than 24.9% of the world's total population. In descending order, the percentage of people who identify as Muslims on each continental landmass stands at: 45% of Africa, 25% of Asia and Oceania (collectively), 6% of Europe, and 1% of the Americas. Additionally, in subdivided geographical regions, the figure stands at: 91% of the Middle East–North Africa, 90% of Central Asia, 65% of the Caucasus, 42% of Southeast As ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multimedia Messaging Service
Multimedia Messaging Service (MMS) is a standard way to send messages that include multimedia content to and from a mobile phone over a cellular network. Users and providers may refer to such a message as a PXT, a picture message, or a multimedia message. The MMS standard extends the core SMS (Short Message Service) capability, allowing the exchange of text messages greater than 160 characters in length. Unlike text-only SMS, MMS can deliver a variety of media, including up to forty seconds of video, one image, a slide show, slideshow of multiple images, or audio. The most common use involves sending photographs from Camera phone, camera-equipped handsets. Media companies have utilized MMS on a commercial basis as a method of delivering news and entertainment content, and retailers have deployed it as a tool for delivering scannable coupon codes, product images, videos, and other information. The 3GPP and Wireless Application Protocol, WAP groups fostered the development of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |





.jpg)