|
Winston Smith Project
The Winston Smith Project ( it, Progetto Winston Smith, or PWS) is an informational and operational project for the defence of human rights on the Internet and in the digital era. The project was started in 1999 as an anonymous association and it is characterised by the absence of a physical reference identity. It is named after the main character in George Orwell's novel "Nineteen Eighty-Four". The reference to Orwell's dystopia is embodied in the motto of PWS: "Unplug the Big Brother" which is aligned with its more generalist motto "Paranoia is a virtue". PWS aims to make users aware of the risks of violation of privacy on the Internet and threats to freedom of speech. PWS is engaged in spreading the informational tools and counter-censorship technologies that allow users to maintain confidentiality in their communications, anonymity in the network and freedom of expression. PWS has generated and maintains the ''e-privacy'', ''Big Brother Awards Italy'', ''Privacy Box'' and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Human Rights
Human rights are Morality, moral principles or Social norm, normsJames Nickel, with assistance from Thomas Pogge, M.B.E. Smith, and Leif Wenar, 13 December 2013, Stanford Encyclopedia of PhilosophyHuman Rights Retrieved 14 August 2014 for certain standards of human behaviour and are regularly protected in Municipal law, municipal and international law. They are commonly understood as inalienable,The United Nations, Office of the High Commissioner of Human RightsWhat are human rights? Retrieved 14 August 2014 fundamental rights "to which a person is inherently entitled simply because she or he is a human being" and which are "inherent in all human beings",Burns H. Weston, 20 March 2014, Encyclopædia Britannicahuman rights Retrieved 14 August 2014. regardless of their age, ethnic origin, location, language, religion, ethnicity, or any other status. They are applicable everywhere and at every time in the sense of being Universality (philosophy), universal, and they are Egalitari ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open Source Initiative
The Open Source Initiative (OSI) is the steward of the Open Source Definition, the set of rules that define open source software. It is a California public-benefit nonprofit corporation,_with_501(c)(3).html" ;"title="110. - 6910./ref> is a type of Nonprofit organization">nonprofit corporation chartered by a state governments of the United States, state gover ..., with 501(c)(3)">110. - 6910./ref> is a type of Nonprofit organization">nonprofit corporation chartered by a state governments of the United States, state gover ..., with 501(c)(3) tax-exempt status. The organization was founded in late February 1998 by Bruce Perens and Eric S. Raymond, part of a group inspired by the Netscape Communications Corporation publishing the source code for its flagship Netscape Communicator product. Later, in August 1998, the organization added a board of directors. Raymond was president from its founding until February 2005, followed briefly by Russ Nelson and then Michael Tiemann. In May 20 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nym Server
A pseudonymous remailer or nym server, as opposed to an anonymous remailer, is an Internet software program designed to allow people to write pseudonymous messages on Usenet newsgroups and send pseudonymous email. Unlike purely anonymous remailers, it assigns its users a user name, and it keeps a database of instructions on how to return messages to the real user. These instructions usually involve the anonymous remailer network itself, thus protecting the true identity of the user. Primordial pseudonymous remailers once recorded enough information to trace the identity of the real user, making it possible for someone to obtain the identity of the real user through legal or illegal means. This form of pseudonymous remailer is no longer common. David Chaum wrote an article in 1981 that described many of the features present in modern pseudonymous remailers. The Penet remailer, which lasted from 1993 to 1996, was a popular pseudonymous remailer. Contemporary nym servers A nym s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mirror Website
Mirror sites or mirrors are replicas of other websites or any network node. The concept of mirroring applies to network services accessible through any protocol, such as HTTP or FTP. Such sites have different URLs than the original site, but host identical or near-identical content. Mirror sites are often located in a different geographic region than the original, or upstream site. The purpose of mirrors is to reduce network traffic, improve access speed, ensure availability of the original site for technical or political reasons, or provide a real-time backup of the original site. Mirror sites are particularly important in developing countries, where internet access may be slower or less reliable. The maintainers of some mirrors choose not to replicate the entire contents of the upstream server they are mirroring because of technical constraints, or selecting only a subset relevant to their purpose, such as software written in a particular programming language, runnable on a sing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
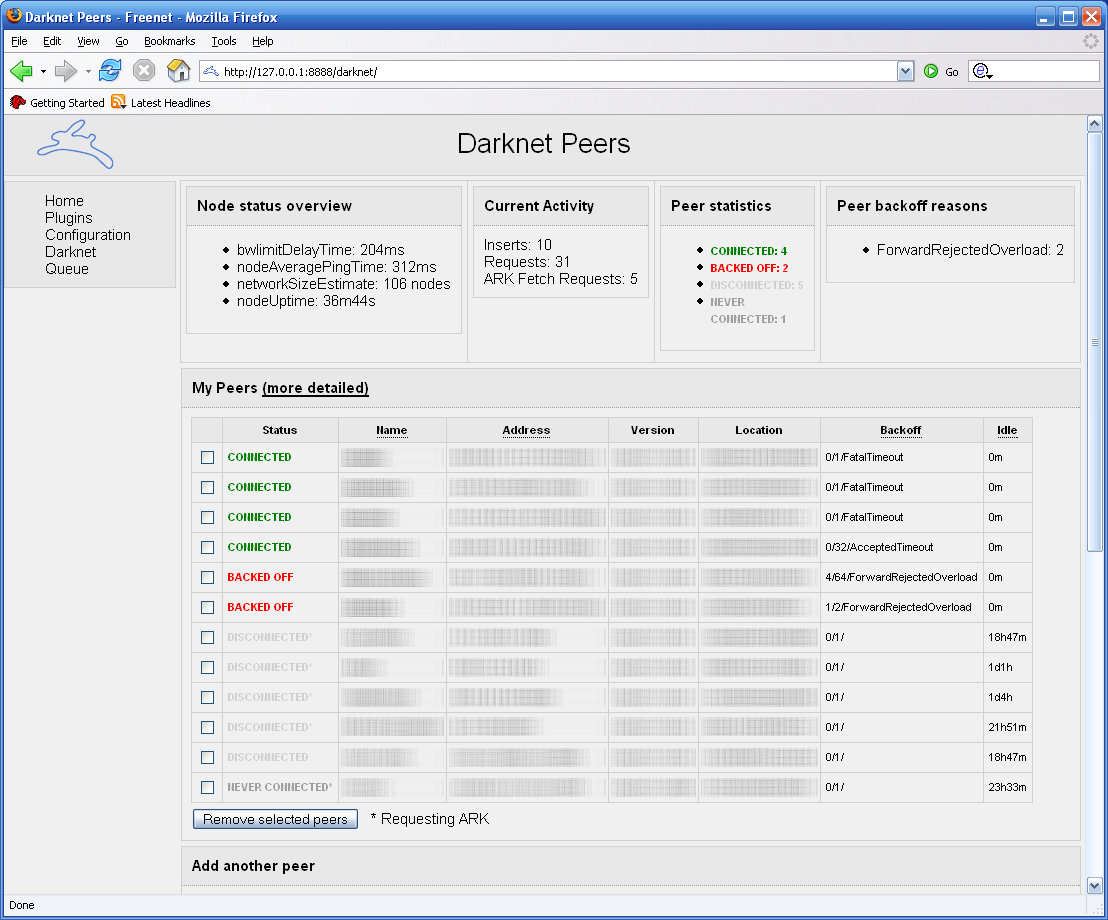
Freenet
Freenet is a peer-to-peer platform for censorship-resistant, anonymous communication. It uses a decentralized distributed data store to keep and deliver information, and has a suite of free software for publishing and communicating on the Web without fear of censorship.What is Freenet? , ''Freenet: The Free network official website''.Taylor, Ian J. ''From P2P to Web Services and Grids: Peers in a Client/Server World''. London: Springer, 2005. Both Freenet and some of its associated tools were originally designed by Ian Clarke, who defined Freenet's goal as providing |
Pretty Good Privacy
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991. PGP and similar software follow the OpenPGP, an open standard of PGP encryption software, standard (RFC 4880) for encrypting and decrypting data. Design PGP encryption uses a serial combination of hashing, data compression, symmetric-key cryptography, and finally public-key cryptography; each step uses one of several supported algorithms. Each public key is bound to a username or an e-mail address. The first version of this system was generally known as a web of trust to contrast with the X.509 system, which uses a hierarchical approach based on certificate authority and which was added to PGP implementations later. Current versions of P ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Register
''The Register'' is a British technology news website co-founded in 1994 by Mike Magee, John Lettice and Ross Alderson. The online newspaper's masthead sublogo is "''Biting the hand that feeds IT''." Their primary focus is information technology news and opinions. Situation Publishing Ltd is listed as the site's publisher. Drew Cullen is an owner and Linus Birtles is the managing director. Andrew Orlowski was the executive editor before leaving the website in May 2019. History ''The Register'' was founded in London as an email newsletter called ''Chip Connection''. In 1998 ''The Register'' became a daily online news source. Magee left in 2001 to start competing publications ''The Inquirer'', and later the ''IT Examiner'' and ''TechEye''.Walsh, Bob (2007). ''Clear Blogging: How People Blogging Are Changing the World and How You Can Join Them.'' Apress, In 2002, ''The Register'' expanded to have a presence in London and San Francisco, creating ''The Register USA'' at ther ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Java Anon Proxy
Java Anon Proxy (JAP) also known as JonDonym, was a proxy server, proxy system designed to allow browsing the World Wide Web, Web with revocable pseudonymity.Privacy-friendly law enforcement 2006 It was originally developed as part of a project of the Technische Universität Dresden, the Universität Regensburg and Privacy Commissioner of the state of Schleswig-Holstein. The client-software is written in the Java (programming language), Java programming language. The service has been closed since August 2021. Cross-platform and free, it sends requests through a Mix Cascade and mixes the data streams of multiple users in order to further obfuscate the data to outsiders. JonDonym is available for all platforms that support Java. Furthermore, ''ANONdroid'' is a JonDony ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Through Obscurity
Security through obscurity (or security by obscurity) is the reliance in security engineering on design or implementation secrecy as the main method of providing security to a system or component. History An early opponent of security through obscurity was the locksmith Alfred Charles Hobbs, who in 1851 demonstrated to the public how state-of-the-art locks could be picked. In response to concerns that exposing security flaws in the design of locks could make them more vulnerable to criminals, he said: "Rogues are very keen in their profession, and know already much more than we can teach them." There is scant formal literature on the issue of security through obscurity. Books on security engineering cite Kerckhoffs' doctrine from 1883, if they cite anything at all. For example, in a discussion about secrecy and openness in Nuclear Command and Control: e benefits of reducing the likelihood of an accidental war were considered to outweigh the possible benefits of secrecy. This ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown. In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation. Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the mathematically advanced comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security ( data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synonymo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open System (computing)
Open systems are computer systems that provide some combination of interoperability, portability, and open software standards. (It can also refer to specific installations that are configured to allow unrestricted access by people and/or other computers; this article does not discuss that meaning). The term was popularized in the early 1980s, mainly to describe systems based on Unix, especially in contrast to the more entrenched mainframes and minicomputers in use at that time. Unlike older legacy systems, the newer generation of Unix systems featured standardized programming interfaces and peripheral interconnects; third party development of hardware and software was encouraged, a significant departure from the norm of the time, which saw companies such as Amdahl and Hitachi going to court for the right to sell systems and peripherals that were compatible with IBM's mainframes. The definition of "open system" can be said to have become more formalized in the 1990s with the emer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)