|
UCMDB
UCMDB is a software product from Micro Focus that generates and maintains a Configuration Management Database of information technology items. It includes a mechanism for automated discovery of IT infrastructure components, such as computers and network devices. UCMDB is included in several HP products and supports ITIL-based configuration management and change management processes. DDMA The DDMa component (Discovery and Dependency mapping Advanced) of UCMDB works by scanning ranges of IP addresses within pre-set probe IP ranges, using ping, ICMP echo requests and Nmap to locate live IP addresses and open TCP ports, and IP address harvesting techniques by querying ARP/Cache tables of level 3 network devices. Resulting current IP addresses are then translated into CIs which function as input for deeper level discovery. The pyramid model is designed to ensure that only relevant sources are being queried, resulting in lower network and node load. See also * ITIL * ITSM Info ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Micro Focus
Micro Focus International plc is a British multinational software and information technology business based in Newbury, Berkshire, England. The firm provides software and consultancy. The company is listed on the London Stock Exchange and is a constituent of the FTSE 250 Index. History Micro Focus was founded in 1976. In 1981, it became the first company to win the Queen's Award for Industry purely for developing a software product. The product was CIS COBOL, a standard-compliant COBOL implementation for microcomputers. In 1998, the company acquired Intersolv Inc, an applications enablement business, for and the combined business was renamed Merant. The same year the company acquired XDB Systems with their XDB Enterprise Server relational database management system. In 2001 the business was demerged from Merant with help from Golden Gate Capital Partners and once again became Micro Focus. It was listed on the London Stock Exchange in 2005. In May 2007, San Diego-based Acu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Configuration Management Database
A configuration management database (CMDB) is an ITIL term for a database used by an organization to store information about hardware and software assets (commonly referred to as configuration items). It is useful to break down configuration items into logical layers. This database acts as a data warehouse for the organization and also stores information regarding the relationships among its assets. The CMDB provides a means of understanding the organization's critical assets and their relationships, such as information systems, upstream sources or dependencies of assets, and the downstream targets of assets. Purpose and benefits The CMDB is a fundamental component of ITIL framework's Configuration Management process. CMDBs are used to keep track of the state of assets such as products, systems, software, facilities, people as they exist at specific points in time, and the relationship between all assets. A CMDB helps an organization understand the relationship between the compon ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Technology
Information technology (IT) is the use of computers to create, process, store, retrieve, and exchange all kinds of data . and information. IT forms part of information and communications technology (ICT). An information technology system (IT system) is generally an information system, a communications system, or, more specifically speaking, a computer system — including all hardware, software, and peripheral equipment — operated by a limited group of IT users. Although humans have been storing, retrieving, manipulating, and communicating information since the earliest writing systems were developed, the term ''information technology'' in its modern sense first appeared in a 1958 article published in the ''Harvard Business Review''; authors Harold J. Leavitt and Thomas L. Whisler commented that "the new technology does not yet have a single established name. We shall call it information technology (IT)." Their definition consists of three categories: techniques for pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hewlett Packard
The Hewlett-Packard Company, commonly shortened to Hewlett-Packard ( ) or HP, was an American multinational information technology company headquartered in Palo Alto, California. HP developed and provided a wide variety of hardware components, as well as software and related services to consumers, small and medium-sized businesses ( SMBs), and large enterprises, including customers in the government, health, and education sectors. The company was founded in a one-car garage in Palo Alto by Bill Hewlett and David Packard in 1939, and initially produced a line of electronic test and measurement equipment. The HP Garage at 367 Addison Avenue is now designated an official California Historical Landmark, and is marked with a plaque calling it the "Birthplace of 'Silicon Valley'". The company won its first big contract in 1938 to provide test and measurement instruments for Walt Disney's production of the animated film ''Fantasia'', which allowed Hewlett and Packard to formally esta ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ITIL
The Information Technology Infrastructure Library (ITIL) is a set of detailed practices for IT activities such as IT service management (ITSM) and IT asset management (ITAM) that focus on aligning IT services with the needs of business. ITIL describes processes, procedures, tasks, and checklists which are neither organization-specific nor technology-specific, but can be applied by an organization toward strategy, delivering value, and maintaining a minimum level of competency. It allows the organization to establish a baseline from which it can plan, implement, and measure. It is used to demonstrate compliance and to measure improvement. There is no formal independent third party compliance assessment available for ITIL compliance in an organization. Certification in ITIL is only available to individuals. Since 2013, ITIL has been owned by AXELOS, a joint venture between Capita and the UK Cabinet Office. History Responding to growing dependence on IT, the UK Government's Ce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Configuration Management
Configuration management (CM) is a process for establishing and maintaining consistency of a product's performance, functional, and physical attributes with its requirements, design, and operational information throughout its life. The CM process is widely used by military engineering organizations to manage changes throughout the system lifecycle of complex systems, such as weapon systems, military vehicles, and information systems. Outside the military, the CM process is also used with IT service management as defined by ITIL, and with other domain models in the civil engineering and other industrial engineering segments such as roads, bridges, canals, dams, and buildings. Introduction CM applied over the life cycle of a system provides visibility and control of its performance, functional, and physical attributes. CM verifies that a system performs as intended, and is identified and documented in sufficient detail to support its projected life cycle. The CM process facilita ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Change Management
Change management (sometimes abbreviated as CM) is a collective term for all approaches to prepare, support, and help individuals, teams, and organizations in making organizational change. It includes methods that redirect or redefine the use of resources, business process, budget allocations, or other modes of operation that significantly change a company or organization. Organizational change management (OCM) considers the full organization and what needs to change, while change management may be used solely to refer to how people and teams are affected by such organizational transition. It deals with many different disciplines, from behavioral and social sciences to information technology and business solutions. As change management becomes more necessary in the business cycle of organizations, it is beginning to be taught as its own academic discipline at universities. There are a growing number of universities with research units dedicated to the study of organizational cha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IP Address
An Internet Protocol address (IP address) is a numerical label such as that is connected to a computer network that uses the Internet Protocol for communication.. Updated by . An IP address serves two main functions: network interface identification and location addressing. Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, because of the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP (IPv6), using 128 bits for the IP address, was standardized in 1998. IPv6 deployment has been ongoing since the mid-2000s. IP addresses are written and displayed in human-readable notations, such as in IPv4, and in IPv6. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., , which is equivalent to the historically used subnet mask . The IP address space is managed globally by the Internet Assigned Numbers Authority (IA ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
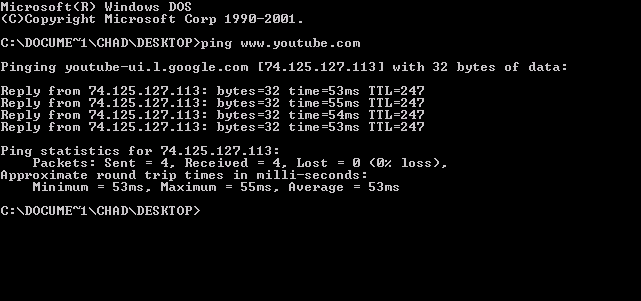
Ping (networking Utility)
ping is a computer network administration software utility used to test the reachability of a host on an Internet Protocol (IP) network. It is available for virtually all operating systems that have networking capability, including most embedded network administration software. Ping measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The name comes from active sonar terminology that sends a pulse of sound and listens for the echo to detect objects under water. Ping operates by means of Internet Control Message Protocol (ICMP) packets. ''Pinging'' involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean round-trip times, and standard deviation of the mean. The command-line options of the ping utility and its output vary between t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ICMP Echo
ping is a computer network administration software utility used to test the reachability of a host on an Internet Protocol (IP) network. It is available for virtually all operating systems that have networking capability, including most embedded network administration software. Ping measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The name comes from active sonar terminology that sends a pulse of sound and listens for the echo to detect objects under water. Ping operates by means of Internet Control Message Protocol (ICMP) packets. ''Pinging'' involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean round-trip times, and standard deviation of the mean. The command-line options of the ping utility and its output vary between t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nmap
Nmap (Network Mapper) is a network scanner created by Gordon Lyon (also known by his pseudonym ''Fyodor Vaskovich''). Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection. These features are extensible by scripts that provide more advanced service detection, vulnerability detection, and other features. Nmap can adapt to network conditions including latency and congestion during a scan. Nmap started as a Linux utility and was ported to other systems including Windows, macOS, and BSD. It is most popular on Linux, followed by Windows. Features Nmap features include: * Host discovery – Identifying hosts on a network. For example, listing the hosts that respond to TCP and/or ICMP requests or have a particular port open. * Port scanning – Enumerating the open ports on target hosts. * V ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TCP Port
In computer networking, a port is a number assigned to uniquely identify a connection endpoint and to direct data to a specific service. At the software level, within an operating system, a port is a logical construct that identifies a specific process or a type of network service. A port is identified for each transport protocol and address combination by a 16-bit unsigned number, known as the port number. The most common transport protocols that use port numbers are the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). A port number is always associated with an IP address of a host and the type of transport protocol used for communication. It completes the destination or origination network address of a message. Specific port numbers are reserved to identify specific services so that an arriving packet can be easily forwarded to a running application. For this purpose, port numbers lower than 1024 identify the historically most commonly used services an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |