|
TrustedSource
TrustedSource is an Internet reputation system originally developed by CipherTrust and now owned by Intel Security. It provides reputation scores for Internet identities, such as IP addresses, URLs, domains, and email/web content. Reputation data and content categories, as well as global email, web and other network traffic patterns observed by TrustedSource ecosystem, for any IP address, domain, or URL can be checked from the TrustedSource.org portal site TrustedSource works by analyzing in real-time traffic patterns from email, web and network data flows from McAfee's global set of security appliances and hosted services, as well as those of partners like F5 Networks. Working off that data stream, it applies data mining and analysis techniques, such as Support Vector Machine, Random forest Random forests or random decision forests is an ensemble learning method for classification, regression and other tasks that operates by constructing a multitude of decision tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TrustedSource Logo
TrustedSource is an Internet reputation system originally developed by CipherTrust and now owned by Intel Security. It provides reputation scores for Internet identities, such as IP addresses, URLs, domains, and email/web content. Reputation data and content categories, as well as global email, web and other network traffic patterns observed by TrustedSource ecosystem, for any IP address, domain, or URL can be checked from the TrustedSource.org portal site TrustedSource works by analyzing in real-time traffic patterns from email, web and network data flows from McAfee's global set of security appliances and hosted services, as well as those of partners like F5 Networks. Working off that data stream, it applies data mining and analysis techniques, such as Support Vector Machine, Random forest Random forests or random decision forests is an ensemble learning method for classification, regression and other tasks that operates by constructing a multitude of decision tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CipherTrust
CipherTrust was an anti-spam email software company based in Alpharetta, GA (a suburb of Atlanta), although they had offices around the world. The company was co-founded by Jay Chaudhry and Lawrence Hughes (both formerly with SecureIT). Chaudhry was CEO and Chairman of the Board of SecureIT until it was acquired by VeriSign in August 1998. Since August 2006 it is part of Secure Computing Corp for 273.6 M$ (2006 USD), which was subsequently acquired by McAfee in 2008. Products Their main product is the IronMail, a gateway appliance that prevents leaks from outgoing transfers through the e-mail applications whether they be HTTP or FTP transfers. CipherTrust is the current market leader in the e-mail security space according to Gartner and other industry analysts. CipherTrust has recently added a new product to secure Instant Messaging called IronIM. Their CTO, Paul Judge, chaired the Anti-Spam Research Group (ASRG) of the IRTF. One of the services provided by CipherTrust is track ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reputation System
Reputation systems are programs or algorithms that allow users to rate each other in online communities in order to build trust through reputation. Some common uses of these systems can be found on E-commerce websites such as eBay, Amazon.com, and Etsy as well as online advice communities such as Stack Exchange. These reputation systems represent a significant trend in "decision support for Internet mediated service provisions". With the popularity of online communities for shopping, advice, and exchange of other important information, reputation systems are becoming vitally important to the online experience. The idea of reputation systems is that even if the consumer can't physically try a product or service, or see the person providing information, that they can be confident in the outcome of the exchange through trust built by recommender systems. Collaborative filtering, used most commonly in recommender systems, are related to reputation systems in that they both collect rati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
McAfee
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American global computer security software company headquartered in San Jose, California. The company was purchased by Intel in February 2011, and became part of the Intel Security division. In 2017, Intel had a strategic deal with TPG Capital and converted Intel Security into a joint venture between both companies called McAfee. Thoma Bravo took a minority stake in the new company, and Intel retained a 49% stake. The owners took McAfee public on the NASDAQ in 2020, and in 2022 an investor group led by Advent International Corporation took it private again. History 1987–1999 The company was founded in 1987 as McAfee Associates, named for its founder John McAfee, who resigned from the company in 1994. McAfee was incorporated in the state of Delaware in 1992. In 1993, McAfee stepped do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intel Security
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American global computer security software company headquartered in San Jose, California. The company was purchased by Intel in February 2011, and became part of the Intel Security division. In 2017, Intel had a strategic deal with TPG Capital and converted Intel Security into a joint venture between both companies called McAfee. Thoma Bravo took a minority stake in the new company, and Intel retained a 49% stake. The owners took McAfee public on the NASDAQ in 2020, and in 2022 an investor group led by Advent International Corporation took it private again. History 1987–1999 The company was founded in 1987 as McAfee Associates, named for its founder John McAfee, who resigned from the company in 1994. McAfee was incorporated in the state of Delaware in 1992. In 1993, McAfee stepped d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
F5 Networks
F5, Inc. is an American technology company specializing in application security, multi-cloud management, online fraud prevention, application delivery networking (ADN), application availability & performance, network security, and access & authorization. F5 is headquartered in Seattle, Washington in F5 Tower, with an additional 75 offices in 43 countries focusing on account management, global services support, product development, manufacturing, software engineering, and administrative jobs. Notable office locations include Spokane, Washington; New York, New York; Boulder, Colorado; London, England; San Jose, California; and San Francisco, California. F5's originally offered application delivery controller (ADC) technology, but expanded into application layer, automation, multi-cloud, and security services. As ransomware, data leaks, DDoS, and other attacks on businesses of all sizes are arising, companies such as F5 have continued to reinvent themselves. While the majority of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Support Vector Machine
In machine learning, support vector machines (SVMs, also support vector networks) are supervised learning models with associated learning algorithms that analyze data for classification and regression analysis. Developed at AT&T Bell Laboratories by Vladimir Vapnik with colleagues (Boser et al., 1992, Guyon et al., 1993, Cortes and Vapnik, 1995, Vapnik et al., 1997) SVMs are one of the most robust prediction methods, being based on statistical learning frameworks or VC theory proposed by Vapnik (1982, 1995) and Chervonenkis (1974). Given a set of training examples, each marked as belonging to one of two categories, an SVM training algorithm builds a model that assigns new examples to one category or the other, making it a non- probabilistic binary linear classifier (although methods such as Platt scaling exist to use SVM in a probabilistic classification setting). SVM maps training examples to points in space so as to maximise the width of the gap between the two categories. New ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Random Forest
Random forests or random decision forests is an ensemble learning method for classification, regression and other tasks that operates by constructing a multitude of decision trees at training time. For classification tasks, the output of the random forest is the class selected by most trees. For regression tasks, the mean or average prediction of the individual trees is returned. Random decision forests correct for decision trees' habit of overfitting to their training set. Random forests generally outperform decision trees, but their accuracy is lower than gradient boosted trees. However, data characteristics can affect their performance. The first algorithm for random decision forests was created in 1995 by Tin Kam Ho using the random subspace method, which, in Ho's formulation, is a way to implement the "stochastic discrimination" approach to classification proposed by Eugene Kleinberg. An extension of the algorithm was developed by Leo Breiman and Adele Cutler, who reg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
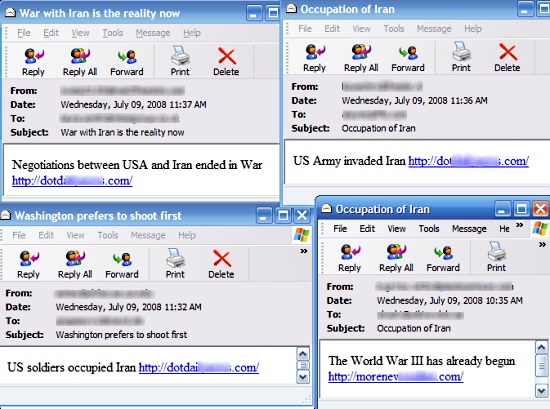
Storm Worm
The Storm Worm (dubbed so by the Finnish company F-Secure) is a phishing backdoor Trojan horse that affects computers using Microsoft operating systems, discovered on January 17, 2007. The worm is also known as: * Small.dam or Trojan-Downloader.Win32.Small.dam (F-Secure) * CME-711 (MITRE) * W32/Nuwar@MM and Downloader-BAI (specific variant) (McAfee) * Troj/Dorf and Mal/Dorf ( Sophos) * Trojan.DL.Tibs.Gen!Pac13 * Trojan.Downloader-647 * Trojan.Peacomm ( Symantec) * TROJ_SMALL.EDW (Trend Micro) * Win32/Nuwar ( ESET) * Win32/Nuwar.N@MM!CME-711 (Windows Live OneCare) * W32/Zhelatin (F-Secure and Kaspersky) * Trojan.Peed, Trojan.Tibs (BitDefender) The Storm Worm began attacking thousands of (mostly private) computers in Europe and the United States on Friday, January 19, 2007, using an e-mail message with a subject line about a recent weather disaster, "230 dead as storm batters Europe". During the weekend there were six subsequent waves of the attack. As of January 22, 2007, the Sto ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |