Storm Worm on:
[Wikipedia]
[Google]
[Amazon]
 The Storm Worm (dubbed so by the
The Storm Worm (dubbed so by the
Spamtrackers SpamWiki: StormWired.com: Analysis by
"There's a Storm Coming"
from the IBM ISS X-Force Blog
Trojan.Peacomm (Storm) at SymantecStormy Weather: A Quantitative Assessment of the Storm Web Threat in 2007 (Trend Micro)
from The Observer.
from PC World.
Storm and the future of social engineering
from Help Net Security (HNS). * Bodmer, Kilger, Carpenter, & Jones (2012). Reverse Deception: Organized Cyber Threat Counter-Exploitation. New York: McGraw-Hill Osborne Media. , {{ISBN, 978-0071772495 Email worms 2007 in computing Hacking in the 2000s
 The Storm Worm (dubbed so by the
The Storm Worm (dubbed so by the Finnish
Finnish may refer to:
* Something or someone from, or related to Finland
* Culture of Finland
* Finnish people or Finns, the primary ethnic group in Finland
* Finnish language, the national language of the Finnish people
* Finnish cuisine
See also ...
company F-Secure
F-Secure Corporation is a global cyber security and privacy company, which has its headquarters in Helsinki, Finland.
The company has offices in Denmark, Finland, France, Germany, India, Italy, Japan, Malaysia, Netherlands, Norway, Poland, Sweden, ...
) is a phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious softwa ...
backdoor
A back door is a door in the rear of a building. Back door may also refer to:
Arts and media
* Back Door (jazz trio), a British group
* Porta dos Fundos (literally “Back Door” in Portuguese) Brazilian comedy YouTube channel.
* Works so titl ...
Trojan horse
The Trojan Horse was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's ''Iliad'', with the poem ending before the war is concluded, ...
that affects computers using Microsoft
Microsoft Corporation is an American multinational technology corporation producing computer software, consumer electronics, personal computers, and related services headquartered at the Microsoft Redmond campus located in Redmond, Washin ...
operating systems, discovered on January 17, 2007. The worm is also known as:
* Small.dam or Trojan-Downloader.Win32.Small.dam (F-Secure
F-Secure Corporation is a global cyber security and privacy company, which has its headquarters in Helsinki, Finland.
The company has offices in Denmark, Finland, France, Germany, India, Italy, Japan, Malaysia, Netherlands, Norway, Poland, Sweden, ...
)
* CME-711 (MITRE
The mitre (Commonwealth English) (; Greek: μίτρα, "headband" or "turban") or miter (American English; see spelling differences), is a type of headgear now known as the traditional, ceremonial headdress of bishops and certain abbots in ...
)
* W32/Nuwar@MM and Downloader-BAI (specific variant) (McAfee
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American global computer security software company head ...
)
* Troj/Dorf and Mal/Dorf ( Sophos)
* Trojan.DL.Tibs.Gen!Pac13
* Trojan.Downloader-647
* Trojan.Peacomm ( Symantec)
* TROJ_SMALL.EDW (Trend Micro
is an American-Japanese multinational cyber security software company with global headquarters in Tokyo, Japan and Irving, Texas, United State.Other regional headquarters and R&D centers are located around East Asia, Southeast Asia, Europe, and ...
)
* Win32/Nuwar ( ESET)
* Win32/Nuwar.N@MM!CME-711 (Windows Live OneCare
Windows Live OneCare (previously Windows OneCare Live, codenamed A1) was a computer security and performance enhancement service developed by Microsoft for Windows. A core technology of OneCare was the multi-platform RAV (Reliable Anti-virus), wh ...
)
* W32/Zhelatin (F-Secure
F-Secure Corporation is a global cyber security and privacy company, which has its headquarters in Helsinki, Finland.
The company has offices in Denmark, Finland, France, Germany, India, Italy, Japan, Malaysia, Netherlands, Norway, Poland, Sweden, ...
and Kaspersky
Kaspersky Lab (; Russian: Лаборатория Касперского, tr. ''Laboratoriya Kasperskogo'') is a Russian multinational cybersecurity and anti-virus provider headquartered in Moscow, Russia, and operated by a holding company in th ...
)
* Trojan.Peed, Trojan.Tibs (BitDefender
Bitdefender is a Romanian cybersecurity technology company headquartered in Bucharest, Romania, with offices in the United States, Europe, Australia and the Middle East.
The company was founded in 2001 by the current CEO and main shareholder, ...
)
The Storm Worm began attacking thousands of (mostly private) computers in Europe
Europe is a large peninsula conventionally considered a continent in its own right because of its great physical size and the weight of its history and traditions. Europe is also considered a subcontinent of Eurasia and it is located entirel ...
and the United States
The United States of America (U.S.A. or USA), commonly known as the United States (U.S. or US) or America, is a country primarily located in North America. It consists of 50 states, a federal district, five major unincorporated territori ...
on Friday, January 19, 2007, using an e-mail message with a subject line about a recent weather disaster, "230 dead as storm batters Europe". During the weekend there were six subsequent waves of the attack. As of January 22, 2007, the Storm Worm accounted for 8% of all malware infections globally.
There is evidence, according to PCWorld
''PC World'' (stylized as PCWorld) is a global computer magazine published monthly by IDG. Since 2013, it has been an online only publication.
It offers advice on various aspects of PCs and related items, the Internet, and other personal tech ...
, that the Storm Worm was of Russia
Russia (, , ), or the Russian Federation, is a transcontinental country spanning Eastern Europe and Northern Asia. It is the largest country in the world, with its internationally recognised territory covering , and encompassing one-eig ...
n origin, possibly traceable to the Russian Business Network The Russian Business Network (commonly abbreviated as RBN) is a multi-faceted cybercrime organization, specializing in and in some cases monopolizing personal identity theft for resale. It is the originator of MPack and an alleged operator of the ...
.
Ways of action
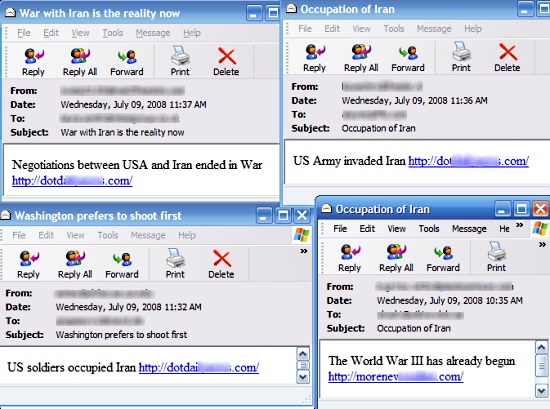
Originally propagated in messages about European windstorm Kyrill, the Storm Worm has been seen also in emails with the following subjects: * 230 dead as storm batters Europe. he worm was dubbed "Storm" because of this message subject.* A killer at 11, he's free at 21 and kill again! * U.S. Secretary of State Condoleezza Rice has kicked German ChancellorAngela Merkel
Angela Dorothea Merkel (; ; born 17 July 1954) is a German former politician and scientist who served as Chancellor of Germany from 2005 to 2021. A member of the Christian Democratic Union (CDU), she previously served as Leader of the Opp ...
* British Muslims Genocide
* Naked teens attack home director.
* Re: Your text
* Radical Muslim drinking enemies' blood.
* Chinese/Russian missile shot down Russian/Chinese satellite/aircraft
* Saddam Hussein
Saddam Hussein ( ; ar, صدام حسين, Ṣaddām Ḥusayn; 28 April 1937 – 30 December 2006) was an Iraqi politician who served as the fifth president of Iraq from 16 July 1979 until 9 April 2003. A leading member of the revolutio ...
safe and sound!
* Saddam Hussein alive!
* Venezuelan leader: "Let's the War beginning".
* Fidel Castro dead.
* If I Knew
* FBI vs. Facebook
* USA occupies Iran
When an attachment is opened, the malware installs the wincom32 service, and injects a payload, passing on packet
Packet may refer to:
* A small container or pouch
** Packet (container), a small single use container
** Cigarette packet
** Sugar packet
* Network packet, a formatted unit of data carried by a packet-mode computer network
* Packet radio, a fo ...
s to destinations encoded within the malware itself. According to Symantec, it may also download and run the Trojan.Abwiz.F trojan, and the W32.Mixor.Q@mm worm
Worms are many different distantly related bilateral animals that typically have a long cylindrical tube-like body, no limbs, and no eyes (though not always).
Worms vary in size from microscopic to over in length for marine polychaete wo ...
. The Trojan piggybacks on the spam with names such as "postcard.exe
.exe is a common filename extension denoting an executable file (the main execution point of a computer program) for Microsoft Windows, OS/2, and DOS.
File formats
There are numerous file formats which may be used by a file with a extensi ...
" and "Flash Postcard.exe," with more changes from the original wave as the attack mutates. Some of the known names for the attachments include:
* Postcard.exe
* ecard.exe
* FullVideo.exe
* Full Story.exe
* Video.exe
* Read More.exe
* FullClip.exe
* GreetingPostcard.exe
* MoreHere.exe
* FlashPostcard.exe
* GreetingCard.exe
* ClickHere.exe
* ReadMore.exe
* FlashPostcard.exe
* FullNews.exe
* NflStatTracker.exe
* ArcadeWorld.exe
* ArcadeWorldGame.exe
Later, as F-Secure confirmed, the malware began spreading the subjects such as "Love birds" and "Touched by Love". These emails contain links to websites hosting some of the following files, which are confirmed to contain the virus:
* with_love.exe
* withlove.exe
* love.exe
* frommetoyou.exe
* iheartyou.exe
* fck2008.exe
* fck2009.exe
According to Joe Stewart, director of malware research for SecureWorks, Storm remains amazingly resilient, in part because the Trojan horse it uses to infect systems changes its packing code every 10 minutes, and, once installed, the bot uses fast flux to change the IP addresses for its command and control servers.
Botnetting
The compromised machine becomes merged into abotnet
A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its conn ...
. While most botnets are controlled through a central server
Server may refer to:
Computing
*Server (computing), a computer program or a device that provides functionality for other programs or devices, called clients
Role
* Waiting staff, those who work at a restaurant or a bar attending customers and su ...
, which if found can be taken down to destroy the botnet, the Storm Worm seeds a botnet that acts in a similar way to a peer-to-peer network
Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the network. They are said to form a peer-to-peer n ...
, with no centralized control. Each compromised machine connects to a list of a subset of the entire botnet - around 30 to 35 other compromised machines, which act as hosts
A host is a person responsible for guests at an event or for providing hospitality during it.
Host may also refer to:
Places
*Host, Pennsylvania, a village in Berks County
People
*Jim Host (born 1937), American businessman
*Michel Host ( ...
. While each of the infected hosts share lists of other infected hosts, no one machine has a full list of the entire botnet - each only has a subset, making it difficult to gauge the true extent of the zombie network. On 7 September 2007, estimates of the size of the Storm botnet ranged from 1 to 10 million computers. Researchers from the University of Mannheim and the Institut Eurecom have estimated concurrent online storm nodes to be between 5,000 and 40,000.
Rootkit
Another action the Storm Worm takes is to install therootkit
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed (for example, to an unauthorized user) and often masks its existence or the exis ...
Win32.agent.dh. Symantec pointed out that flawed rootkit code voids some of the Storm Worm author's plans. Later variants, starting around July 2007, loaded the rootkit component by patching existing Windows drivers such as tcpip.sys and cdrom.sys with a stub of code that loads the rootkit driver module without requiring it to have an entry in the Windows driver list.
April Fool's Day
On April 1, 2008, a new storm worm was released onto the net, with April Fools-themed subject titles.Feedback
The list of antivirus companies that can detect the Storm Worm include Authentium,BitDefender
Bitdefender is a Romanian cybersecurity technology company headquartered in Bucharest, Romania, with offices in the United States, Europe, Australia and the Middle East.
The company was founded in 2001 by the current CEO and main shareholder, ...
, ClamAV
Clam AntiVirus (ClamAV) is a free software, cross-platform antimalware toolkit able to detect many types of malware, including viruses. It was developed for Unix and has third party versions available for AIX, BSD, HP-UX, Linux, macOS, OpenVM ...
, eSafe, Eset, F-Prot
FRISK Software International (established in 1993) was an Icelandic software company that developed F-Prot antivirus and F-Prot AVES antivirus and anti-spam service. The company was founded in 1993. It was acquired by Cyren in 2012.
History
Th ...
, F-Secure
F-Secure Corporation is a global cyber security and privacy company, which has its headquarters in Helsinki, Finland.
The company has offices in Denmark, Finland, France, Germany, India, Italy, Japan, Malaysia, Netherlands, Norway, Poland, Sweden, ...
, Kaspersky
Kaspersky Lab (; Russian: Лаборатория Касперского, tr. ''Laboratoriya Kasperskogo'') is a Russian multinational cybersecurity and anti-virus provider headquartered in Moscow, Russia, and operated by a holding company in th ...
, McAfee
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American global computer security software company head ...
, Sophos, Symantec, Trend Micro
is an American-Japanese multinational cyber security software company with global headquarters in Tokyo, Japan and Irving, Texas, United State.Other regional headquarters and R&D centers are located around East Asia, Southeast Asia, Europe, and ...
, avast! and Windows Live OneCare
Windows Live OneCare (previously Windows OneCare Live, codenamed A1) was a computer security and performance enhancement service developed by Microsoft for Windows. A core technology of OneCare was the multi-platform RAV (Reliable Anti-virus), wh ...
. The Storm Worm is constantly being updated by its authors to evade antivirus detection, so this does not imply that all the vendors listed above are able to detect all the Storm Worm variants. An intrusion detection system
An intrusion detection system (IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically rep ...
offers some protection from the rootkit, as it may warn that the Windows process "services.exe" is trying to access the Internet using ports 4000 or 7871. Windows 2000
Windows 2000 is a major release of the Windows NT operating system developed by Microsoft and oriented towards businesses. It was the direct successor to Windows NT 4.0, and was released to manufacturing on December 15, 1999, and was officiall ...
, Windows XP
Windows XP is a major release of Microsoft's Windows NT operating system. It was released to manufacturing on August 24, 2001, and later to retail on October 25, 2001. It is a direct upgrade to its predecessors, Windows 2000 for high-end and ...
and presumably Windows Vista
Windows Vista is a major release of the Windows NT operating system developed by Microsoft. It was the direct successor to Windows XP, which was released five years before, at the time being the longest time span between successive releases of ...
can be infected by all the Storm Worm variants, but Windows Server 2003
Windows Server 2003 is the sixth version of Windows Server operating system produced by Microsoft. It is part of the Windows NT family of operating systems and was released to manufacturing on March 28, 2003 and generally available on April 24, 2 ...
cannot, as the malware's author specifically excluded that edition of Windows from the code. Additionally, the decryption layer for some variants requires Windows API functions that are only available in Windows XP Service Pack 2 and later, effectively preventing infection on older versions of Windows.
Peter Gutmann sent an email noting that the Storm botnet comprises between 1 and 10 million PCs depending on whose estimates you believe. Although Dr. Gutmann makes a hardware resource comparison between the Storm botnet and distributed memory
In computer science, distributed memory refers to a multiprocessor computer system in which each processor has its own private memory. Computational tasks can only operate on local data, and if remote data are required, the computational task mu ...
and distributed shared memory
In computer science, distributed shared memory (DSM) is a form of memory architecture where physically separated memories can be addressed as a single shared address space. The term "shared" does not mean that there is a single centralized memor ...
high performance computers at TOP500
The TOP500 project ranks and details the 500 most powerful non- distributed computer systems in the world. The project was started in 1993 and publishes an updated list of the supercomputers twice a year. The first of these updates always coinci ...
, exact performance matches were not his intention—rather a more general appreciation of the botnet's size compared to other massive computing resources. Consider for example the size of the Storm botnet compared to grid computing projects such as the World Community Grid
World Community Grid (WCG) is an effort to create the world's largest volunteer computing platform to tackle scientific research that benefits humanity. Launched on November 16, 2004, with proprietary Grid MP client from United Devices and addin ...
.
An article in PCWorld dated October 21, 2007 says that a network security analyst presented findings at the Toorcon hacker conference in San Diego on October 20, 2007, saying that Storm is down to about 20,000 active hosts or about one-tenth of its former size. However, this is being disputed by security researcher Bruce Schneier
Bruce Schneier (; born January 15, 1963) is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is a Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman Klein Cente ...
, who notes that the network is being partitioned in order to sell the parts off independently.
Notes
External links
Spamtrackers SpamWiki: Storm
Bruce Schneier
Bruce Schneier (; born January 15, 1963) is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is a Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman Klein Cente ...
"There's a Storm Coming"
from the IBM ISS X-Force Blog
Trojan.Peacomm (Storm) at Symantec
from The Observer.
from PC World.
Storm and the future of social engineering
from Help Net Security (HNS). * Bodmer, Kilger, Carpenter, & Jones (2012). Reverse Deception: Organized Cyber Threat Counter-Exploitation. New York: McGraw-Hill Osborne Media. , {{ISBN, 978-0071772495 Email worms 2007 in computing Hacking in the 2000s