|
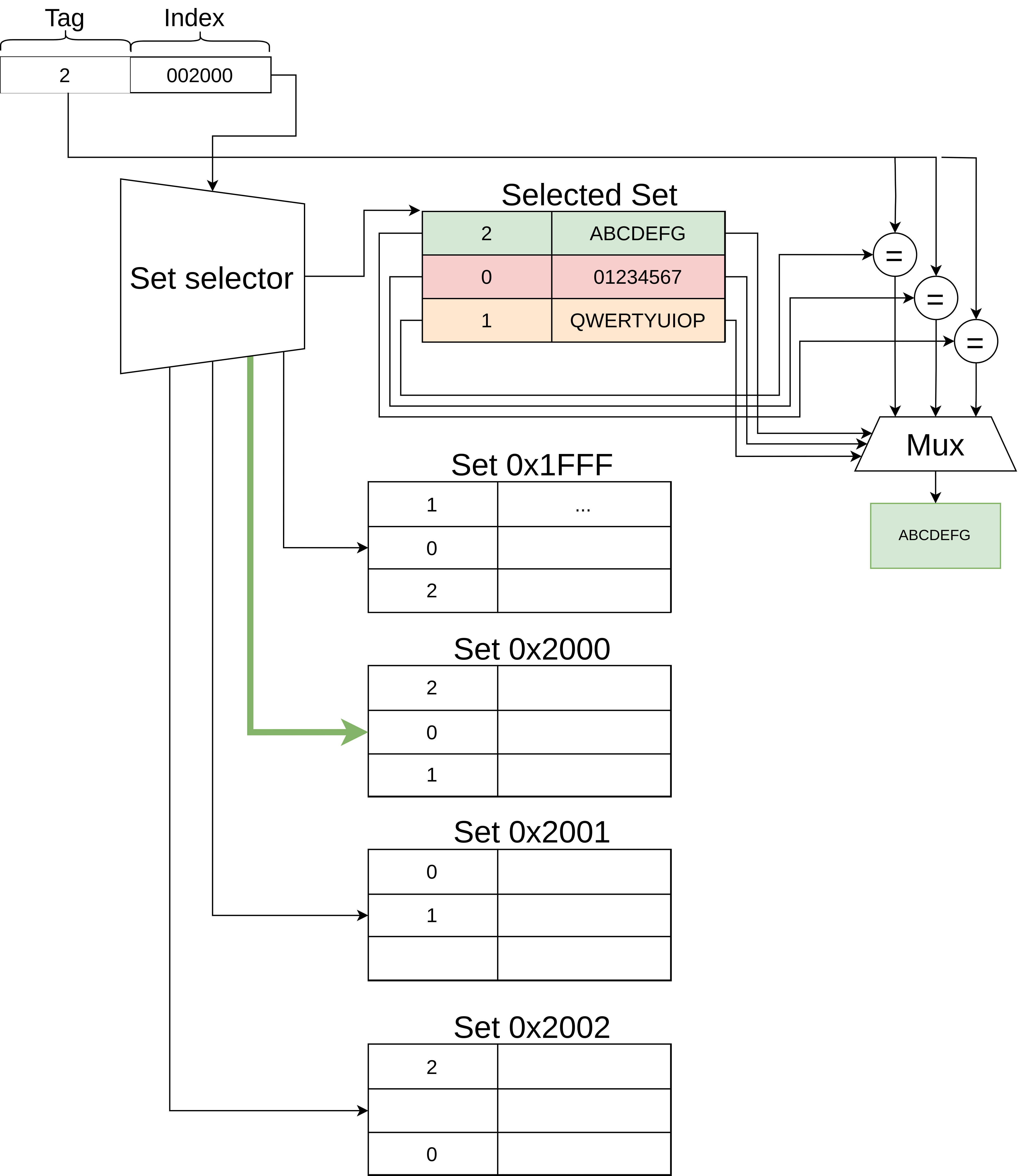
Transient Execution CPU Vulnerabilities
Transient execution CPU vulnerabilities are vulnerabilities in which instructions, most often optimized using speculative execution, are executed temporarily by a microprocessor, without committing their results due to a misprediction or error, resulting in leaking secret data to an unauthorized party. The archetype is Spectre, and transient execution attacks like Spectre belong to the cache-attack category, one of several categories of side-channel attacks. Since January 2018 many different cache-attack vulnerabilities have been identified. Overview Modern computers are highly parallel devices, composed of components with very different performance characteristics. If an operation (such as a branch) cannot yet be performed because some earlier slow operation (such as a memory read) has not yet completed, a microprocessor may attempt to ''predict'' the result of the earlier operation and execute the later operation ''speculatively'', acting as if the prediction were correct. The ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Vulnerability (computing)
Vulnerabilities are flaws or weaknesses in a system's design, implementation, or management that can be exploited by a malicious actor to compromise its security. Despite a system administrator's best efforts to achieve complete correctness, virtually all hardware and software contain bugs where the system does not behave as expected. If the bug could enable an attacker to compromise the confidentiality, integrity, or availability of system resources, it can be considered a vulnerability. Insecure software development practices as well as design factors such as complexity can increase the burden of vulnerabilities. Vulnerability management is a process that includes identifying systems and prioritizing which are most important, scanning for vulnerabilities, and taking action to secure the system. Vulnerability management typically is a combination of remediation, mitigation, and acceptance. Vulnerabilities can be scored for severity according to the Common Vulnerability S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Ice Lake (microprocessor)
Ice Lake is Intel's List of Intel codenames, codename for the 10th generation Intel Core mobile and 3rd generation Xeon Scalable server processors based on the Sunny Cove (microarchitecture), Sunny Cove microarchitecture. Ice Lake represents an Architecture step in Intel's process–architecture–optimization model. Produced on the second generation of Intel's 10 nanometer, 10 nm process, 10 nm+, Ice Lake is Intel's second microarchitecture to be manufactured on the 10 nm process, following the limited launch of Cannon Lake (microarchitecture), Cannon Lake in 2018. However, Intel altered their naming scheme in 2020 for the 10 nm process. In this new naming scheme, Ice Lake's manufacturing process is called simply 10 nm, without any appended pluses. Ice Lake CPUs are sold together with the 14 nm Comet Lake CPUs as Intel's "10th Generation Core" product family. There are no Ice Lake desktop or high-power mobile processors; Comet Lake fulfills this ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Cascade Lake (microprocessor)
Cascade Lake is an Intel codename A code name, codename, call sign, or cryptonym is a code word or name used, sometimes clandestinely, to refer to another name, word, project, or person. Code names are often used for military purposes, or in espionage. They may also be used in ... for a 14 nm server, workstation and enthusiast processor generation, launched in April 2019. In Intel's process–architecture–optimization model, Cascade Lake is an optimization of Skylake. Intel states that this will be their first generation to support 3D XPoint-based memory modules. It also features Deep Learning Boost (DPL) instructions and mitigations for Meltdown and Spectre. Intel officially launched new Xeon Scalable SKUs on February 24, 2020. Variants *Server: Cascade Lake-SP, Cascade Lake-AP *Workstation: Cascade Lake-W *Enthusiast: Cascade Lake-X List of Cascade Lake processors Cascade Lake-X (Enthusiast) Cascade Lake-AP (Advanced Performance) Cascade Lake-AP is branded ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
ARM Architecture Family
ARM (stylised in lowercase as arm, formerly an acronym for Advanced RISC Machines and originally Acorn RISC Machine) is a family of RISC instruction set architectures (ISAs) for computer processors. Arm Holdings develops the ISAs and licenses them to other companies, who build the physical devices that use the instruction set. It also designs and licenses cores that implement these ISAs. Due to their low costs, low power consumption, and low heat generation, ARM processors are useful for light, portable, battery-powered devices, including smartphones, laptops, and tablet computers, as well as embedded systems. However, ARM processors are also used for desktops and servers, including Fugaku, the world's fastest supercomputer from 2020 to 2022. With over 230 billion ARM chips produced, , ARM is the most widely used family of instruction set architectures. There have been several generations of the ARM design. The original ARM1 used a 32-bit internal structure but h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Pacman (security Vulnerability)
Pacman is a side-channel vulnerability in certain ARM CPUs that was made public by Massachusetts Institute of Technology security researchers on June 10, 2021. It affects the pointer authentication (PAC) mechanism in many ARMv8.3 chips, including Apple's M1 CPU. Pacman creates an 'oracle' that lets an attacker guess a pointer's PAC signature without crashing the program if the guess is wrong. PAC signatures are typically less than 16 bits wide, so an attacker can use the oracle to guess the signature in 216 tries or fewer. It is unfixable without hardware changes because it is caused by the inherent design of CPU cache A CPU cache is a hardware cache used by the central processing unit (CPU) of a computer to reduce the average cost (time or energy) to access data from the main memory. A cache is a smaller, faster memory, located closer to a processor core, whi ...s and branch predictors. Impact and response Pacman alone is not an exploitable vulnerability. PAC is a ' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Massachusetts Institute Of Technology
The Massachusetts Institute of Technology (MIT) is a Private university, private research university in Cambridge, Massachusetts, United States. Established in 1861, MIT has played a significant role in the development of many areas of modern technology and science. In response to the increasing Technological and industrial history of the United States, industrialization of the United States, William Barton Rogers organized a school in Boston to create "useful knowledge." Initially funded by a land-grant universities, federal land grant, the institute adopted a Polytechnic, polytechnic model that stressed laboratory instruction in applied science and engineering. MIT moved from Boston to Cambridge in 1916 and grew rapidly through collaboration with private industry, military branches, and new federal basic research agencies, the formation of which was influenced by MIT faculty like Vannevar Bush. In the late twentieth century, MIT became a leading center for research in compu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
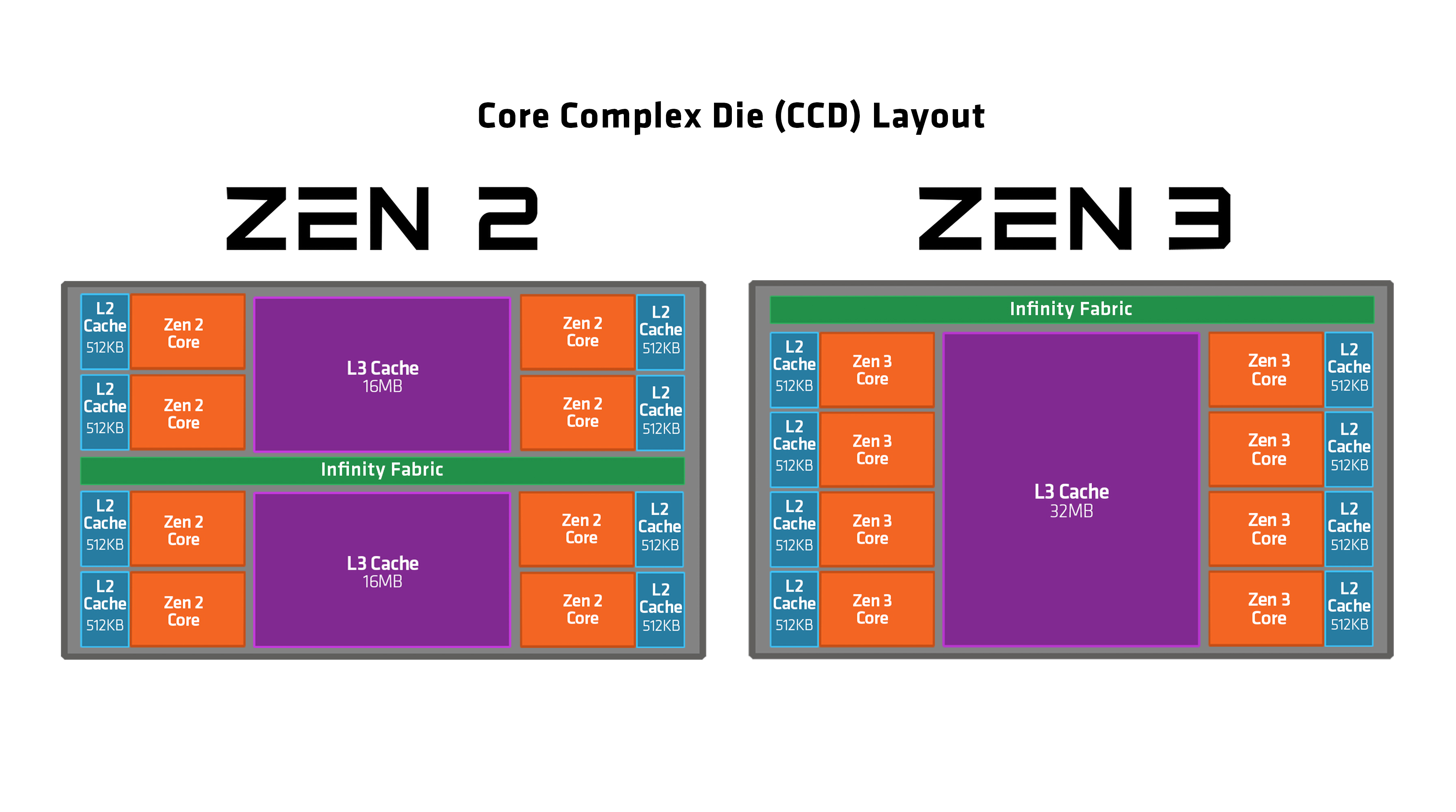
Zen 3
Zen 3 is the name for a CPU microarchitecture by AMD, released on November 5, 2020. It is the successor to Zen 2 and uses TSMC's 7 nm process, 7 nm process for the chiplets and GlobalFoundries's 14 nm process, 14 nm process for the I/O die on the server chips and 12 nm for desktop chips. Zen 3 powers Ryzen 5000 mainstream desktop processors (codenamed "Vermeer") and Epyc server processors (codenamed "Milan"). Zen 3 is supported on motherboards with List of AMD chipsets#AM4 chipsets, 500 series chipsets; 400 series boards also saw support on select B450 / X470 motherboards with certain BIOSes. Zen 3 is the last microarchitecture before AMD switched to DDR5 memory and new sockets, which are AM5 for the desktop "Ryzen" chips alongside SP5 and SP6 for the EPYC server platform and sTRX8. According to AMD, Zen 3 has a 19% higher instructions per cycle (IPC) on average than Zen 2. On April 1, 2022, AMD released the new Ryzen 6000 series for laptops/mobile, using an improved #Zen 3+, Zen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Engadget
Engadget ( ) is a technology news, reviews and analysis website offering daily coverage of gadgets, consumer electronics, video games, gaming hardware, apps, social media, streaming, AI, space, robotics, electric vehicles and other potentially consumer-facing technology. The site's content includes short-form news posts, reported features, news analysis, product reviews, buying guides, two weekly video shows, The Engadget Podcast, The Morning After newsletter and a weekly deals newsletter. It has been operated by Yahoo! Inc. (2017–present), Yahoo! Inc. since September 2021. History Engadget was founded by former ''Gizmodo'' technology weblog editor and co-founder Peter Rojas. Engadget was the largest blog in Weblogs, Inc., a blog network with over 75 Blog, weblogs, including ''Autoblog.com, Autoblog'' and ''Joystiq,'' which formerly included ''Hackaday''. Weblogs Inc. was purchased by AOL in 2005. Launched in March 2004, Engadget was one of the internet's earliest tech blogs. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Ars Technica
''Ars Technica'' is a website covering news and opinions in technology, science, politics, and society, created by Ken Fisher and Jon Stokes in 1998. It publishes news, reviews, and guides on issues such as computer hardware and software, science, technology policy, and video games. ''Ars Technica'' was privately owned until May 2008, when it was sold to Condé Nast Digital, the online division of Condé Nast Publications. Condé Nast purchased the site, along with two others, for $25 million and added it to the company's ''Wired'' Digital group, which also includes '' Wired'' and, formerly, Reddit. The staff mostly works from home and has offices in Boston, Chicago, London, New York City, and San Francisco. The operations of ''Ars Technica'' are funded primarily by advertising, and it has offered a paid subscription service since 2001. History Ken Fisher, who serves as the website's current editor-in-chief, and Jon Stokes created ''Ars Technica'' in 1998. Its purpose was t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Foreshadow
Foreshadow, known as L1 Terminal Fault (L1TF) by Intel, is a vulnerability that affects modern microprocessors that was first discovered by two independent teams of researchers in January 2018, but was first disclosed to the public on 14 August 2018. The vulnerability is a speculative execution attack on Intel processors that may result in the disclosure of sensitive information stored in personal computers and third-party clouds. There are two versions: the first version (original/Foreshadow) () targets data from SGX enclaves; and the second version (next-generation/Foreshadow-NG) () targets virtual machines (VMs), hypervisors (VMM), operating systems (OS) kernel memory, and System Management Mode (SMM) memory. A listing of affected Intel hardware has been posted. Foreshadow is similar to the Spectre security vulnerabilities discovered earlier to affect Intel and AMD chips, and the Meltdown vulnerability that also affected Intel. AMD products are not affected by the Fores ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |