|
Telegram (app)
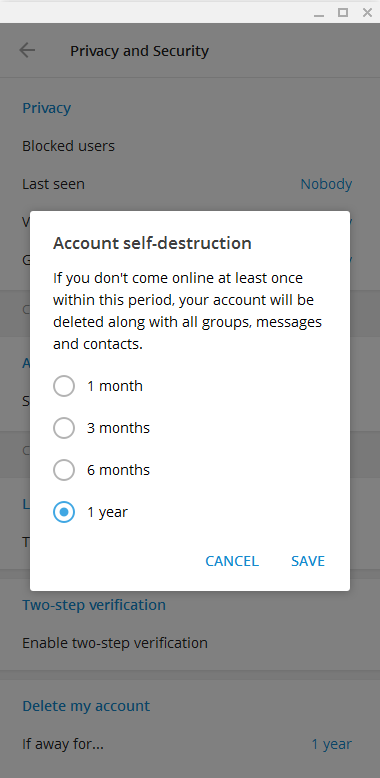
Telegram Messenger is a globally accessible freemium, cross-platform, encrypted, cloud-based and centralized instant messaging (IM) service. The application also provides optional end-to-end encrypted chats, popularly known as secret chat and video calling, VoIP, file sharing and several other features. It was launched for iOS on 14 August 2013 and Android on 20 October 2013. The servers of Telegram are distributed worldwide with five data centers in different parts of the world, while the operational center is based in Dubai, United Arab Emirates. Various client apps are available for desktop and mobile platforms including official apps for Android, iOS, Windows, macOS, and Linux (although registration requires an iOS or Android device and a working phone number). There are also two official Telegram web twin apps, WebK and WebZ, and numerous unofficial clients that make use of Telegram's protocol. Telegram's official components are open source, with the exception of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
C (programming Language)
C (''pronounced like the letter c'') is a General-purpose language, general-purpose computer programming language. It was created in the 1970s by Dennis Ritchie, and remains very widely used and influential. By design, C's features cleanly reflect the capabilities of the targeted CPUs. It has found lasting use in operating systems, device drivers, protocol stacks, though decreasingly for application software. C is commonly used on computer architectures that range from the largest supercomputers to the smallest microcontrollers and embedded systems. A successor to the programming language B (programming language), B, C was originally developed at Bell Labs by Ritchie between 1972 and 1973 to construct utilities running on Unix. It was applied to re-implementing the kernel of the Unix operating system. During the 1980s, C gradually gained popularity. It has become one of the measuring programming language popularity, most widely used programming languages, with C compilers avail ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pavel Durov
Pavel Valeryevich Durov (russian: Павел Валерьевич Дуров; born 10 October 1984) is a Russian-born French-Emirati entrepreneur who is known for being the founder of the social networking site VK (service), VK and Telegram (software), Telegram Messenger. He is the younger brother of Nikolai Durov. For some years after his dismissal as CEO of VK in 2014, the Durov brothers travelled the world in self-imposed exile as citizens of Saint Kitts and Nevis. In 2017, Pavel joined the World Economic Forum (WEF) Young Global Leaders as a representative of Finland. Durov was Naturalization, naturalized as a French citizen in August 2021. , his net worth is estimated at US$15.1 billion. In 2022, he was recognized as the richest person in the United Arab Emirates according to Forbes. Early life and education Pavel Durov was born in Leningrad, but spent most of his childhood in Turin, Italy, where his father was employed. In 2006, he graduated from the Philology Department ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GitHub
GitHub, Inc. () is an Internet hosting service for software development and version control using Git. It provides the distributed version control of Git plus access control, bug tracking, software feature requests, task management, continuous integration, and wikis for every project. Headquartered in California, it has been a subsidiary of Microsoft since 2018. It is commonly used to host open source software development projects. As of June 2022, GitHub reported having over 83 million developers and more than 200 million repositories, including at least 28 million public repositories. It is the largest source code host . History GitHub.com Development of the GitHub.com platform began on October 19, 2007. The site was launched in April 2008 by Tom Preston-Werner, Chris Wanstrath, P. J. Hyett and Scott Chacon after it had been made available for a few months prior as a beta release. GitHub has an annual keynote called GitHub Universe. Organizational ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Client–server Model
The client–server model is a distributed application structure that partitions tasks or workloads between the providers of a resource or service, called servers, and service requesters, called clients. Often clients and servers communicate over a computer network on separate hardware, but both client and server may reside in the same system. A server host runs one or more server programs, which share their resources with clients. A client usually does not share any of its resources, but it requests content or service from a server. Clients, therefore, initiate communication sessions with servers, which await incoming requests. Examples of computer applications that use the client–server model are email, network printing, and the World Wide Web. Client and server role The "client–server" characteristic describes the relationship of cooperating programs in an application. The server component provides a function or service to one or many clients, which initiate requests for s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Center
A data center (American English) or data centre (British English)See spelling differences. is a building, a dedicated space within a building, or a group of buildings used to house computer systems and associated components, such as telecommunications and storage systems. Since IT operations are crucial for business continuity, it generally includes redundant or backup components and infrastructure for power supply, data communication connections, environmental controls (e.g., air conditioning, fire suppression), and various security devices. A large data center is an industrial-scale operation using as much electricity as a small town. History Data centers have their roots in the huge computer rooms of the 1940s, typified by ENIAC, one of the earliest examples of a data center.Old large computer rooms that housed machines like the U.S. Army's ENIAC, which were developed pre-1960 (1945), were now referred to as "data centers". Early computer systems, complex to operate and ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Voice Over IP
Voice over Internet Protocol (VoIP), also called IP telephony, is a method and group of technologies for the delivery of speech, voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet. The terms Internet telephony, broadband telephony, and broadband phone service specifically refer to the provisioning of communications services (voice, fax, Short Message Service, SMS, voice-messaging) over the Internet, rather than via the public switched telephone network (PSTN), also known as plain old telephone service (POTS). Overview The steps and principles involved in originating VoIP telephone calls are similar to traditional digital telephony and involve signaling, channel setup, digitization of the analog voice signals, and encoding. Instead of being transmitted over a circuit-switched network, the digital information is packetized and transmission occurs as IP packets over a packet-switched network. They transport media streams using spec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Videotelephony
Videotelephony, also known as videoconferencing and video teleconferencing, is the two-way or multipoint reception and transmission of audio and video signals by people in different locations for real time communication.McGraw-Hill Concise Encyclopedia of EngineeringVideotelephony McGraw-Hill, 2002. Retrieved from the FreeDictionary.com website, January 9, 2010 A videophone is a telephone with a video camera and video display, capable of simultaneous video and audio communication. Videoconferencing implies the use of this technology for a group or organizational meeting rather than for individuals, in a videoconference.Mulbach et al, 1995. pg. 291. Telepresence may refer either to a high-quality videotelephony system (where the goal is to create the illusion that remote participants are in the same room) or to meetup technology, which can go beyond video into robotics (such as moving around the room or physically manipulating objects). Videoconferencing has also been called "vis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
End-to-end Encryption
End-to-end encryption (E2EE) is a system of communication where only the communicating users can read the messages. In principle, it prevents potential eavesdroppers – including telecom providers, Internet providers, malicious actors, and even the provider of the communication service – from being able to access the cryptographic keys needed to decrypt the conversation. End-to-end encryption is intended to prevent data being read or secretly modified, other than by the true sender and recipient(s). The messages are encrypted by the sender but the third party does not have a means to decrypt them, and stores them encrypted. The recipients retrieve the encrypted data and decrypt it themselves. Because no third parties can decipher the data being communicated or stored, for example, companies that provide end-to-end encryption are unable to hand over texts of their customers' messages to the authorities. In 2022, the UK's Information Commissioner's Office, the government body ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Instant Messaging
Instant messaging (IM) technology is a type of online chat allowing real-time text transmission over the Internet or another computer network. Messages are typically transmitted between two or more parties, when each user inputs text and triggers a transmission to the recipient(s), who are all connected on a common network. It differs from email in that conversations over instant messaging happen in real-time (hence "instant"). Most modern IM application (computing), applications (sometimes called "social messengers", "messaging apps" or "chat apps") use push technology and also add other features such as emojis (or graphical smileys), file transfer, chatbots, voice over IP, or Videotelephony, video chat capabilities. Instant messaging systems tend to facilitate connections between specified known users (often using a contact list also known as a "buddy list" or "friend list"), and can be standalone applications or integrated into e.g. a wider social media platform, or a website ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Centralized Computing
Centralized computing is computing done at a central location, using terminals that are attached to a central computer. The computer itself may control all the peripherals directly (if they are physically connected to the central computer), or they may be attached via a terminal server. Alternatively, if the terminals have the capability, they may be able to connect to the central computer over the network. The terminals may be text terminals or thin clients, for example. It offers greater security over decentralized systems because all of the processing is controlled in a central location. In addition, if one terminal breaks down, the user can simply go to another terminal and log in again, and all of their files will still be accessible. Depending on the system, they may even be able to resume their session from the point they were at before, as if nothing had happened. This type of arrangement does have some disadvantages. The central computer performs the computing function ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cloud Computing
Cloud computing is the on-demand availability of computer system resources, especially data storage ( cloud storage) and computing power, without direct active management by the user. Large clouds often have functions distributed over multiple locations, each of which is a data center. Cloud computing relies on sharing of resources to achieve coherence and typically uses a "pay as you go" model, which can help in reducing capital expenses but may also lead to unexpected operating expenses for users. Value proposition Advocates of public and hybrid clouds claim that cloud computing allows companies to avoid or minimize up-front IT infrastructure costs. Proponents also claim that cloud computing allows enterprises to get their applications up and running faster, with improved manageability and less maintenance, and that it enables IT teams to more rapidly adjust resources to meet fluctuating and unpredictable demand, providing burst computing capability: high computing p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |