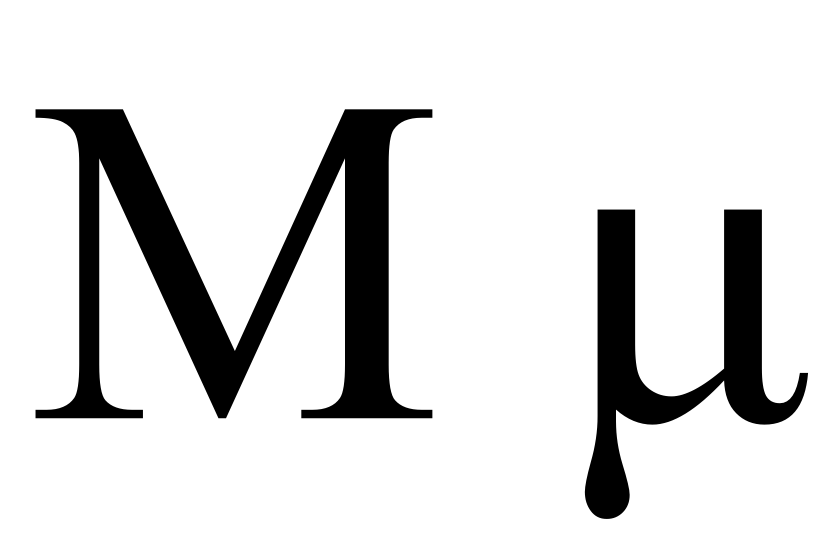|
Turingismus
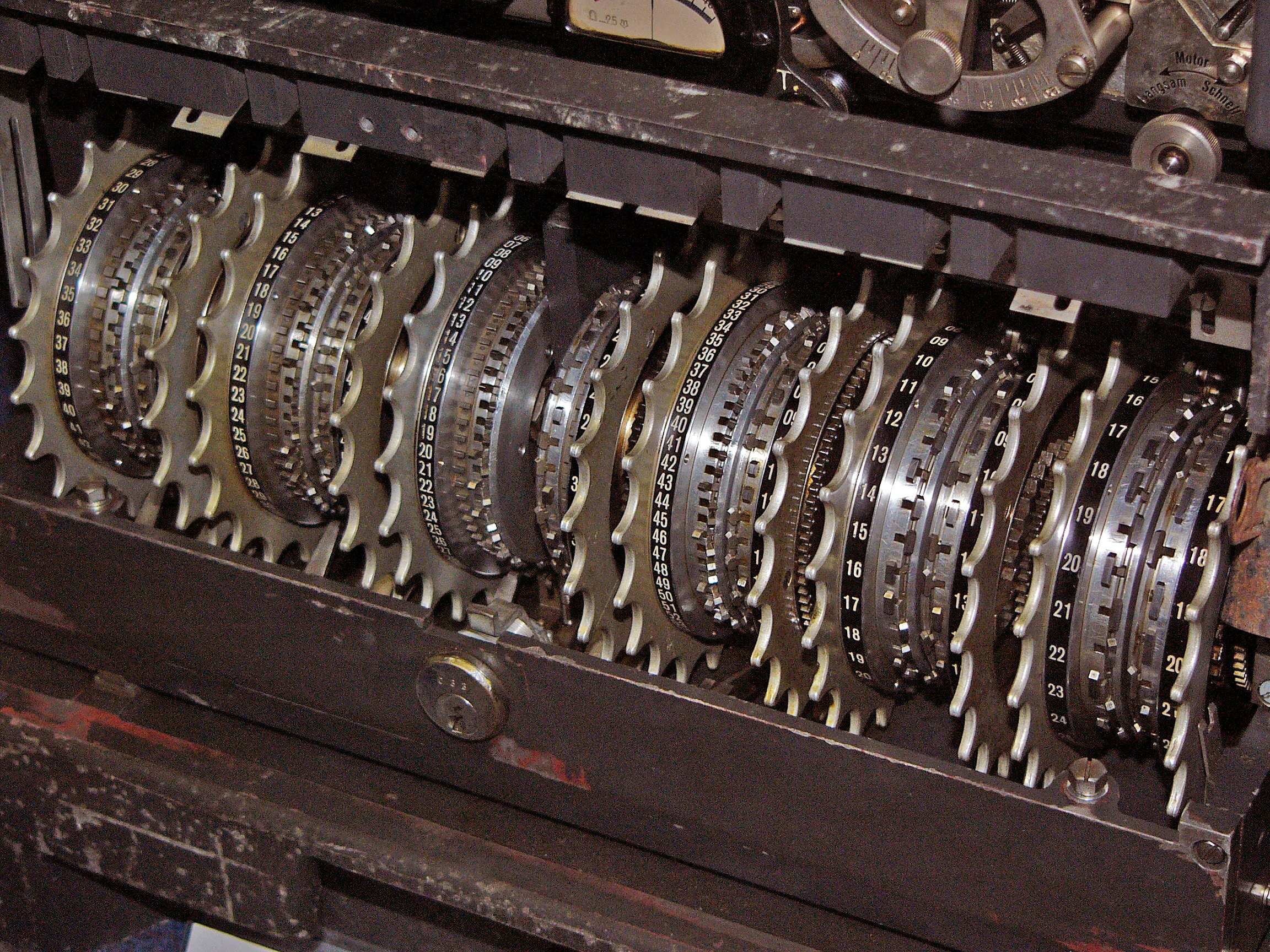
Turingery in ''Testery Methods 1942–1944'' or Turing's method (playfully dubbed Turingismus by Peter Ericsson, Peter Hilton and Donald Michie) was a manual codebreaking method devised in July 1942 by the mathematician and cryptanalyst Alan Turing at the British Government Code and Cypher School at Bletchley Park during World War II. It was for use in cryptanalysis of the Lorenz cipher produced by the SZ40 and SZ42 teleprinter rotor stream cipher machines, one of the Germans' ''Geheimschreiber'' (secret writer) machines. The British codenamed non-Morse traffic "Fish", and that from this machine "Tunny" (another word for the tuna fish). Reading a Tunny message required firstly that the logical structure of the system was known, secondly that the periodically changed pattern of active cams on the wheels was derived, and thirdly that the starting positions of the scrambler wheels for this message—the message key—was established. The logical structure of Tunny had been wor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Alan Turing
Alan Mathison Turing (; 23 June 1912 – 7 June 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher, and theoretical biologist. Turing was highly influential in the development of theoretical computer science, providing a formalisation of the concepts of algorithm and computation with the Turing machine, which can be considered a model of a general-purpose computer. He is widely considered to be the father of theoretical computer science and artificial intelligence. Born in Maida Vale, London, Turing was raised in southern England. He graduated at King's College, Cambridge, with a degree in mathematics. Whilst he was a fellow at Cambridge, he published a proof demonstrating that some purely mathematical yes–no questions can never be answered by computation and defined a Turing machine, and went on to prove that the halting problem for Turing machines is undecidable. In 1938, he obtained his PhD from the Department of Mathemati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptanalysis Of The Lorenz Cipher
Cryptanalysis of the Lorenz cipher was the process that enabled the British to read high-level German army messages during World War II. The British Government Code and Cypher School (GC&CS) at Bletchley Park decrypted many communications between the '' Oberkommando der Wehrmacht'' (OKW, German High Command) in Berlin and their army commands throughout occupied Europe, some of which were signed "Adolf Hitler, Führer". These were intercepted non-Morse radio transmissions that had been enciphered by the Lorenz SZ teleprinter rotor stream cipher attachments. Decrypts of this traffic became an important source of "Ultra" intelligence, which contributed significantly to Allied victory. For its high-level secret messages, the German armed services enciphered each character using various online ''Geheimschreiber'' (secret writer) stream cipher machines at both ends of a telegraph link using the 5-bit International Telegraphy Alphabet No. 2 (ITA2). These machines were subsequently di ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Peter Hilton
Peter John Hilton (7 April 1923Peter Hilton, "On all Sorts of Automorphisms", '' The American Mathematical Monthly'', 92(9), November 1985, p. 6506 November 2010) was a British mathematician, noted for his contributions to homotopy theory and for code-breaking during World War II. Early life He was born in Brondesbury, London, the son Mortimer Jacob Hilton, a Jewish physician who was in general practice in Peckham, and his wife Elizabeth Amelia Freedman, and was brought up in Kilburn. The physiologist Sidney Montague Hilton (1921–2011) of the University of Birmingham Medical School was his elder brother. Hilton was educated at St Paul's School, London."About the speaker"announcement of a lecture given by Peter Hilton at Bletchley Park on 12 July 2006. Retrieved 18 January 2007. He went to The Queen's College, Oxford in 1940 to read mathematics, on an open scholarship, where the mathematics tutor was Ughtred Haslam-Jones. Bletchley Park A wartime undergraduate in wartime ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cipher
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is ''encipherment''. To encipher or encode is to convert information into cipher or code. In common parlance, "cipher" is synonymous with "code", as they are both a set of steps that encrypt a message; however, the concepts are distinct in cryptography, especially classical cryptography. Codes generally substitute different length strings of characters in the output, while ciphers generally substitute the same number of characters as are input. There are exceptions and some cipher systems may use slightly more, or fewer, characters when output versus the number that were input. Codes operated by substituting according to a large codebook which linked a random string of characters or numbers to a word or phrase. For example, "UQJHSE" could be the code for "Proceed to the following ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Coprime
In mathematics, two integers and are coprime, relatively prime or mutually prime if the only positive integer that is a divisor of both of them is 1. Consequently, any prime number that divides does not divide , and vice versa. This is equivalent to their greatest common divisor (GCD) being 1. One says also '' is prime to '' or '' is coprime with ''. The numbers 8 and 9 are coprime, despite the fact that neither considered individually is a prime number, since 1 is their only common divisor. On the other hand, 6 and 9 are not coprime, because they are both divisible by 3. The numerator and denominator of a reduced fraction are coprime, by definition. Notation and testing Standard notations for relatively prime integers and are: and . In their 1989 textbook ''Concrete Mathematics'', Ronald Graham, Donald Knuth, and Oren Patashnik proposed that the notation a\perp b be used to indicate that and are relatively prime and that the term "prime" be used instead of coprime (as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mu (letter)
Mu (uppercase Μ, lowercase μ; Ancient Greek , ell, μι or μυ—both ) is the 12th letter of the Greek alphabet, representing the voiced bilabial nasal . In the system of Greek numerals it has a value of 40. Mu was derived from the Egyptian hieroglyphic symbol for water, which had been simplified by the Phoenicians and named after their word for water, to become 𐤌 (mem). Letters that derive from mu include the Roman M and the Cyrillic М. Names Ancient Greek In Ancient Greek, the name of the letter was written and pronounced Modern Greek In Modern Greek, the letter is spelled and pronounced . In polytonic orthography, it is written with an acute accent: . Use as symbol The lowercase letter mu (μ) is used as a special symbol in many academic fields. Uppercase mu is not used, because it appears identical to Latin M. Measurement *the SI prefix ''micro-'', which represents one millionth, or 10−6. Lowercase letter "u" is often substituted for "μ" w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Psi (letter)
Psi (uppercase , lowercase ; ''psi'' ) is the 23rd letter of the Greek alphabet and is associated with a numeric value of 700. In both Classical and Modern Greek, the letter indicates the combination (as in English word " lapse"). For Greek loanwords in Latin and modern languages with Latin alphabets, psi is usually transliterated as "ps". The letter's origin is uncertain. It may or may not derive from the Phoenician alphabet. There are several psi-like symbols such as 𐀂 (*28), 𐀚(*24) and 𐀩(*27) in the Linear B script, which suggests a pre-Phonecian origin of the character. It appears in the 7th century BC, expressing in the Eastern alphabets, but in the Western alphabets (the sound expressed by Χ in the Eastern alphabets). In writing, the early letter appears in an angular shape (). There were early graphical variants that omitted the stem ("chickenfoot-shaped psi" as: or ). The Western letter (expressing , later ) was adopted into the Old Italic alphab ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chi (letter)
Chi (uppercase Χ, lowercase χ; el, χῖ) is the 22nd letter of the Greek alphabet. Greek Pronunciation Ancient Greek Its value in Ancient Greek was an aspirated velar stop (in the Western Greek alphabet: /ks/). Koine Greek In Koine Greek and later dialects it became a fricative (/) along with Θ and Φ. Modern Greek In Modern Greek, it has two distinct pronunciations: In front of high or front vowels ( or ) it is pronounced as a voiceless palatal fricative , as in German ''ich'' or like the ''h'' in some pronunciations of the English words ''hew'' and ''human''. In front of low or back vowels (, or ) and consonants, it is pronounced as a voiceless velar fricative (), as in German ''ach'' or Spanish ''j''. Transliteration Chi is romanized as in most systematic transliteration conventions, but sometimes is used. In addition, in Modern Greek, it is often also romanized as or in informal practice. Greek numeral In the system of Greek numerals, it has a value of 6 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Key
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm, can encode or decode cryptographic data. Based on the used method, the key can be different sizes and varieties, but in all cases, the strength of the encryption relies on the security of the key being maintained. A key’s security strength is dependent on its algorithm, the size of the key, the generation of the key, and the process of key exchange. Scope The key is what is used to encrypt data from plaintext to ciphertext. There are different methods for utilizing keys and encryption. Symmetric cryptography Symmetric cryptography refers to the practice of the same key being used for both encryption and decryption. Asymmetric cryptography Asymmetric cryptography has separate keys for encrypting and decrypting. These keys are known as the public and private keys, respectively. Purpose Since the key pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher to decrypt it. This process prevents the loss of sensitive information via hacking. Decryption, the inverse of encryption, is the process of turning ciphertext into readable plaintext. Ciphertext is not to be confused with codetext because the latter is a result of a code, not a cipher. Conceptual underpinnings Let m\! be the plaintext message that Alice wants to secretly transmit to Bob and let E_k\! be the encryption cipher, where _k\! is a cryptographic key. Alice must first transform the plaintext into ciphertext, c\!, in order to securely send the message to Bob, as follows: : c = E_k(m). \! In a symmetric-key system, Bob knows Alice's encryption key. Once the m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted. Overview With the advent of computing, the term ''plaintext'' expanded beyond human-readable documents to mean any data, including binary files, in a form that can be viewed or used without requiring a key or other decryption device. Information—a message, document, file, etc.—if to be communicated or stored in an unencrypted form is referred to as plaintext. Plaintext is used as input to an encryption algorithm; the output is usually termed ciphertext, particularly when the algorithm is a cipher. Codetext is less often used, and almost always only when the algorithm involved is actually a code. Some systems use multiple layers of encryption, with the output of one encryption algorithm becoming "plaintext" input for the next. Secure handling Insecure handling of p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exclusive Or
Exclusive or or exclusive disjunction is a logical operation that is true if and only if its arguments differ (one is true, the other is false). It is symbolized by the prefix operator J and by the infix operators XOR ( or ), EOR, EXOR, , , , , , and . The negation of XOR is the logical biconditional, which yields true if and only if the two inputs are the same. It gains the name "exclusive or" because the meaning of "or" is ambiguous when both operands are true; the exclusive or operator ''excludes'' that case. This is sometimes thought of as "one or the other but not both". This could be written as "A or B, but not, A and B". Since it is associative, it may be considered to be an ''n''-ary operator which is true if and only if an odd number of arguments are true. That is, ''a'' XOR ''b'' XOR ... may be treated as XOR(''a'',''b'',...). Truth table The truth table of A XOR B shows that it outputs true whenever the inputs differ: Equivalences, elimination, and introduc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |