|
Turbulence (NSA)
Turbulence is a United States National Security Agency (NSA) information technology, information-technology project started c. 2005. It was developed in small, inexpensive "test" pieces rather than one grand plan like its failed predecessor, the Trailblazer Project. It also includes offensive cyberwarfare capabilities, like injecting malware into remote computers. The United States Congress, U.S. Congress criticized the project in 2007 for having similar bureaucratic problems as the Trailblazer Project. Criticism According to Siobhan Gorman in a 2007 ''The Baltimore Sun, Baltimore Sun'' article, "The conclusion in Congress, two former government officials said, was that Turbulence was over budget, not delivering and poorly led, and that there was little or no strategy to pull it all together." Link to Trailblazer Trailblazer, the predecessor of Turbulence, had been cancelled in 2006 after a United States congressional hearing#Investigative hearings, congressional investiga ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
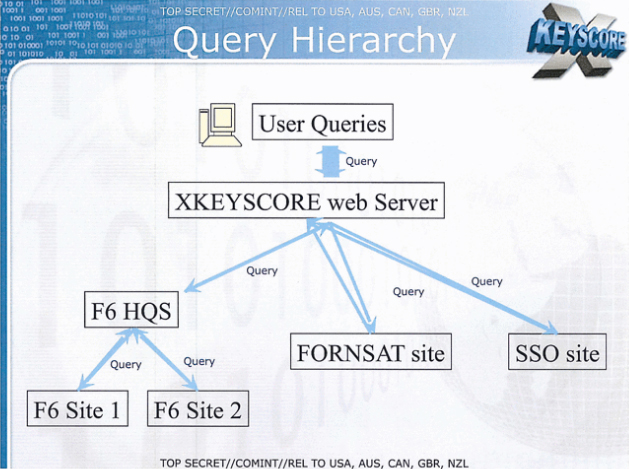
XKeyscore Presentation From 2008
XKeyscore (XKEYSCORE or XKS) is a secret computer system used by the United States National Security Agency (NSA) for searching and analyzing global Internet data, which it collects in Real-time, real time. The NSA has shared XKeyscore with other intelligence agencies, including the Australian Signals Directorate, Canada's Communications Security Establishment, New Zealand's Government Communications Security Bureau, Britain's Government Communications Headquarters, Japan's Defense Intelligence Headquarters, and Germany's Bundesnachrichtendienst. In July 2013, Edward Snowden publicly revealed the program's purpose and use by the NSA in ''The Sydney Morning Herald'' and ''O Globo'' newspapers. The code name was already public knowledge because it was mentioned in earlier articles, and, like many other code names, it appears in job postings and online résumés of employees. On July 3, 2014, German public broadcasting, public broadcaster Norddeutscher Rundfunk, a member of ARD (bro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
James Ball (journalist)
James Ball is a British journalist and author. He has worked for ''The Grocer'', ''The Guardian'', WikiLeaks, ''BuzzFeed'', ''The New European'' and ''The Washington Post'' and is the author of several books. He is the recipient of several awards for journalism and was a member of ''The Guardian'' team that won the Pulitzer Prize for investigative journalism. Early life Ball studied for a BA degree in Philosophy, Politics and Economics at the University of Oxford and went on to enrol in the master's programme in journalism at City, University of London. After transferring to a diploma course for financial reasons, he graduated from City in 2008 with a diploma in magazine journalism with a focus on investigative journalism. Career After leaving university he spent two years at ''The Grocer'' before moving to the Bureau of Investigative Journalism where he worked on iraqwarlogs.com. In November 2010, Julian Assange invited him to work as the in-house journalist for WikiLeaks in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Red Hook (FBI)
The Digital Collection System Network (DCSNet) is the Federal Bureau of Investigation (FBI)'s point-and-click surveillance system that can perform instant wiretaps on almost any telecommunications device in the US. It allows access to cellphone, landline, SMS communications anywhere in the US from a point-and-click interface. It runs on a fiber-optic backbone that is separate from the Internet. It is intended to increase agent productivity through workflow modeling, allowing for the routing of intercepts for translation or analysis with only a few clicks. The DCSNet real-time intelligence data intercept has the capability to record, review and playback intercepted material in real-time. The DCSNet systems operate on a virtual private network parallel to the public Internet, with services provided at least for some time by the Sprint peerless IP network. Much of the information available on this system has come from the results of Freedom of Information Act (FOIA) requests made ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DCSNet
The Digital Collection System Network (DCSNet) is the Federal Bureau of Investigation (FBI)'s point-and-click surveillance system that can perform instant wiretaps on almost any telecommunications device in the US. It allows access to cellphone, landline, SMS communications anywhere in the US from a point-and-click interface. It runs on a fiber-optic backbone that is separate from the Internet. It is intended to increase agent productivity through workflow modeling, allowing for the routing of intercepts for translation or analysis with only a few clicks. The DCSNet real-time intelligence data intercept has the capability to record, review and playback intercepted material in real-time. The DCSNet systems operate on a virtual private network parallel to the public Internet, with services provided at least for some time by the Sprint peerless IP network. Much of the information available on this system has come from the results of Freedom of Information Act (FOIA) requests mad ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ECHELON
ECHELON, originally a secret government code name, is a surveillance program (signals intelligence/SIGINT collection and analysis network) operated by the five signatory states to the UKUSA Security Agreement:Given the 5 dialects that use the terms, UKUSA can be pronounced from "You-Q-SA" to "Oo-Coo-SA", AUSCANNZUKUS can be pronounced from "Oz-Can-Zuke-Us" to "Orse-Can-Zoo-Cuss". :From Talk:UKUSA Agreement: "Per documents officially released by both the Government Communications Headquarters and the National Security Agency, this agreement is referred to as the UKUSA Agreement. This name is subsequently used by media sources reporting on the story, as written in new references used for the article. The NSA press release provides a pronunciation guide, indicating that "UKUSA" should not be read as two separate entities.(National Security Agency)" Australia, Canada, New Zealand, the United Kingdom and the United States, also known as the Five Eyes. Created in the late 1960s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MUSCULAR
Skeletal muscles (commonly referred to as muscles) are organs of the vertebrate muscular system and typically are attached by tendons to bones of a skeleton. The muscle cells of skeletal muscles are much longer than in the other types of muscle tissue, and are often known as muscle fibers. The muscle tissue of a skeletal muscle is striated – having a striped appearance due to the arrangement of the sarcomeres. Skeletal muscles are voluntary muscles under the control of the somatic nervous system. The other types of muscle are cardiac muscle which is also striated and smooth muscle which is non-striated; both of these types of muscle tissue are classified as involuntary, or, under the control of the autonomic nervous system. A skeletal muscle contains multiple fascicles – bundles of muscle fibers. Each individual fiber, and each muscle is surrounded by a type of connective tissue layer of fascia. Muscle fibers are formed from the fusion of developmental myoblasts in a pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tailored Access Operations
The Office of Tailored Access Operations (TAO), now Computer Network Operations, and structured as S32, is a cyber-warfare intelligence-gathering unit of the National Security Agency (NSA). It has been active since at least 1998, possibly 1997, but was not named or structured as TAO until "the last days of 2000," according to General Michael Hayden. TAO identifies, monitors, infiltrates, and gathers intelligence on computer systems being used by entities foreign to the United States. History TAO is reportedly "the largest and arguably the most important component of the NSA's huge Signals Intelligence Directorate (SID), consisting of more than 1,000 military and civilian computer hackers, intelligence analysts, targeting specialists, computer hardware and software designers, and electrical engineers". Snowden leak A document leaked by former NSA contractor Edward Snowden describing the unit's work says TAO has software templates allowing it to break into commonly used hardw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
XKEYSCORE
XKeyscore (XKEYSCORE or XKS) is a secret computer system used by the United States National Security Agency (NSA) for searching and analyzing global Internet data, which it collects in real time. The NSA has shared XKeyscore with other intelligence agencies, including the Australian Signals Directorate, Canada's Communications Security Establishment The Communications Security Establishment (CSE; french: Centre de la sécurité des télécommunications, ''CST''), formerly (from 2008-2014) called the Communications Security Establishment Canada (CSEC), is the Government of Canada's national ..., New Zealand's Government Communications Security Bureau, Britain's Government Communications Headquarters, Japan's Defense Intelligence Headquarters, and Germany's Bundesnachrichtendienst. In July 2013, Edward Snowden publicly revealed the program's purpose and use by the NSA in ''The Sydney Morning Herald'' and ''O Globo'' newspapers. The code name was already public knowledge becaus ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Prism (surveillance Program)
Prism usually refers to: * Prism (optics), a transparent optical component with flat surfaces that refract light * Prism (geometry), a kind of polyhedron Prism may also refer to: Science and mathematics * Prism (geology), a type of sedimentary deposit * Prism correction, a component of some eyeglass prescriptions Government * PRISM, a surveillance program run by the US National Security Agency * PRISM (website), an educational portal website for Indiana teachers * Oregon Performance Reporting Information System, a state agency Media and entertainment Publications * Prism (comics), a Marvel Comics character * ''Prism International'', a Canadian literary magazine * ''PRism'' (journal), an academic journal covering public relations * ''ASEE Prism'', the flagship publication of the American Society for Engineering Education * Prism Comics, an organization that supports LGBT people in the comics industry * ''The Prism Pentad'', a series of Dungeons & Dragons novels by Troy Denni ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SIGINT
Signals intelligence (SIGINT) is intelligence-gathering by interception of ''signals'', whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly used in communication (electronic intelligence—abbreviated to ELINT). Signals intelligence is a subset of intelligence collection management. As classified and sensitive information is usually encrypted, signals intelligence in turn involves the use of cryptanalysis to decipher the messages. Traffic analysis—the study of who is signaling whom and in what quantity—is also used to integrate information again. History Origins Electronic interceptions appeared as early as 1900, during the Boer War of 1899–1902. The British Royal Navy had installed wireless sets produced by Marconi on board their ships in the late 1890s, and the British Army used some limited wireless signalling. The Boers captured some wireless sets and used them to make vital transmissi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Marc Ambinder
Marc Ambinder (; born ) is an American university professor, journalist, and television producer. He is a former politics editor at ''The Atlantic'', a White House Correspondent for ''National Journal'', contributing editor for '' GQ'', and was editor-at-large of ''The Week'' and a member of the ''USA Today'' national board of contributors. In 2017, he was the journalist-in-residence at the University of Pennsylvania School of Law. His third book, ''The Brink: President Reagan and the Nuclear War Scare of 1983'', was published by Simon & Schuster in July 2018. He teaches at the USC Annenberg School for Communication and Journalism, where he leads Annneberg's digital security initiative. Education Ambinder received a A.B. in history from Harvard University in 2001. He was an associate managing editor of the Harvard Crimson. Career In 2016, Ambinder was a Leadership Fellow at the University of Southern California's Annenberg School of Communications and Journalism. Since 2017, he ha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Metadata
Metadata is "data that provides information about other data", but not the content of the data, such as the text of a message or the image itself. There are many distinct types of metadata, including: * Descriptive metadata – the descriptive information about a resource. It is used for discovery and identification. It includes elements such as title, abstract, author, and keywords. * Structural metadata – metadata about containers of data and indicates how compound objects are put together, for example, how pages are ordered to form chapters. It describes the types, versions, relationships, and other characteristics of digital materials. * Administrative metadata – the information to help manage a resource, like resource type, permissions, and when and how it was created. * Reference metadata – the information about the contents and quality of statistical data. * Statistical metadata – also called process data, may describe processes that collect, process, or produce st ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |