|
Trusted Root Store
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the validity of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject. In email encryption, code signing, and e-signature systems, a certificate's subject is typically a person or organization. However, in Transport Layer Security (TLS) a certificate's subject is typically a computer or other device, though TLS certificates may identify organizations or individuals in addition to their core role in identifying devices. TLS, sometimes called by its older name Secure Sockets Layer (SSL), is notable ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synony ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Client (computing)
In computing, a client is a piece of computer hardware or software that accesses a service made available by a server as part of the client–server model of computer networks. The server is often (but not always) on another computer system, in which case the client accesses the service by way of a network. A client is a computer or a program that, as part of its operation, relies on sending a request to another program or a computer hardware or software that accesses a service made available by a server (which may or may not be located on another computer). For example, web browsers are clients that connect to web servers and retrieve web pages for display. Email clients retrieve email from mail servers. Online chat uses a variety of clients, which vary on the chat protocol being used. Multiplayer video games or online video games may run as a client on each computer. The term "client" may also be applied to computers or devices that run the client software or users t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Payment Card
Payment cards are part of a payment system issued by financial institutions, such as a bank, to a customer that enables its owner (the cardholder) to access the funds in the customer's designated bank accounts, or through a credit account and make payments by electronic transfer and access automated teller machines (ATMs). Such cards are known by a variety of names including bank cards, ATM cards, client cards, key cards or cash cards. There are a number of types of payment cards, the most common being credit cards, debit cards, charge cards, and prepaid cards. Most commonly, a payment card is electronically linked to an account or accounts belonging to the cardholder. These accounts may be deposit accounts or loan or credit accounts, and the card is a means of authenticating the cardholder. However, stored-value cards store money on the card itself and are not necessarily linked to an account at a financial institution. It can also be a smart card that contains a unique card ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
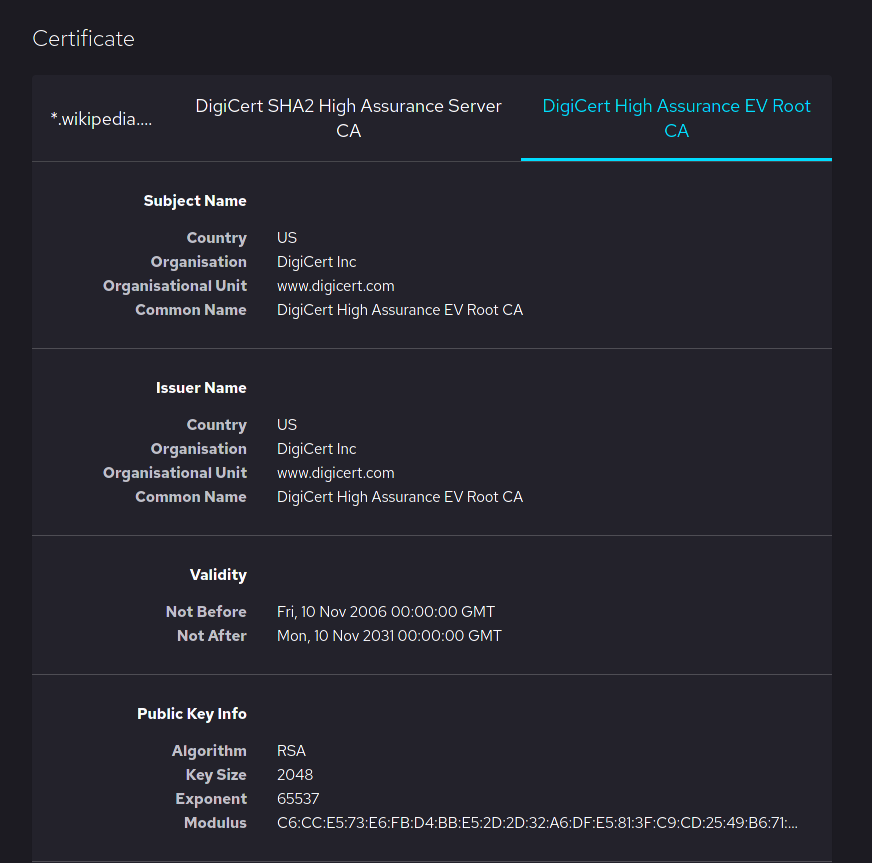
Root Certificate
In cryptography and computer security, a root certificate is a public key certificate that identifies a root certificate authority (CA). Root certificates are self-signed (and it is possible for a certificate to have multiple trust paths, say if the certificate was issued by a root that was cross-signed) and form the basis of an X.509-based public key infrastructure (PKI). Either it has matched Authority Key Identifier with Subject Key Identifier, in some cases there is no Authority Key identifier, then Issuer string should match with Subject string (). For instance, the PKIs supporting HTTPS for secure web browsing and electronic signature schemes depend on a set of root certificates. A certificate authority can issue multiple certificates in the form of a tree structure. A root certificate is the top-most certificate of the tree, the private key which is used to "sign" other certificates. All certificates signed by the root certificate, with the "CA" field set to true, inherit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Self-signed Certificate
In cryptography and computer security, self-signed certificates are public key certificates that are not issued by a certificate authority (CA). These self-signed certificates are easy to make and do not cost money. However, they do not provide any trust value. For instance, if a website owner uses a self-signed certificate to provide HTTPS services, people who visit that website cannot be certain that they are connected to their intended destination. For all they know, a malicious third-party could be redirecting the connection using another self-signed certificate bearing the same holder name. The connection is still encrypted, but does not lead to its intended target. In comparison, a certificate signed by a trusted CA prevents this attack because the user's web browser separately validates the certificate against the issuing CA. The attacker's certificate fails this validation. Self-signed certificates, however, have their own limited uses. They have full trust value when the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
S/MIME
S/MIME (Secure/Multipurpose Internet Mail Extensions) is a standard for public key encryption and signing of MIME data. S/MIME is on an IETF standards track and defined in a number of documents, most importantly . It was originally developed by RSA Data Security and the original specification used the IETF MIME specification with the de facto industry standard PKCS#7 secure message format. Change control to S/MIME has since been vested in the IETF and the specification is now layered on Cryptographic Message Syntax (CMS), an IETF specification that is identical in most respects with PKCS #7. S/MIME functionality is built into the majority of modern email software and interoperates between them. Since it is built on CMS, MIME can also hold an advanced digital signature. Function S/MIME provides the following cryptographic security services for electronic messaging applications: * Authentication * Message integrity * Non-repudiation of origin (using digital signatures) * Pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Remote Desktop Services
Remote Desktop Services (RDS), known as Terminal Services in Windows Server 2008 and earlier, is one of the components of Microsoft Windows that allow a user to initiate and control an interactive session on a remote computer or virtual machine over a network connection. RDS was first released in 1998 as ''Terminal Server'' in Windows NT 4.0 Terminal Server Edition, a stand-alone edition of Windows NT 4.0 Server that allowed users to log in remotely. Starting with Windows 2000, it was integrated under the name of ''Terminal Services'' as an optional component in the server editions of the Windows NT family of operating systems, receiving updates and improvements with each version of Windows. Terminal Services were then renamed to ''Remote Desktop Services'' with Windows Server 2008 R2 in 2009. RDS is Microsoft's implementation of thin client architecture, where Windows software, and the entire desktop of the computer running RDS, are made accessible to any remote client machi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Private Network
A virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. The benefits of a VPN include increases in functionality, security, and management of the private network. It provides access to resources that are inaccessible on the public network and is typically used for remote workers. Encryption is common, although not an inherent part of a VPN connection. A VPN is created by establishing a virtual point-to-point connection through the use of dedicated circuits or with tunneling protocols over existing networks. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN). From a user perspective, the resources available within the private network can be accessed remotely. Types Virtual private networks may be classified into several categories: ;Remote ac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Server
A web server is computer software and underlying hardware that accepts requests via HTTP (the network protocol created to distribute web content) or its secure variant HTTPS. A user agent, commonly a web browser or web crawler, initiates communication by making a request for a web page or other resource using HTTP, and the server responds with the content of that resource or an error message. A web server can also accept and store resources sent from the user agent if configured to do so. The hardware used to run a web server can vary according to the volume of requests that it needs to handle. At the low end of the range are embedded systems, such as a router that runs a small web server as its configuration interface. A high-traffic Internet website might handle requests with hundreds of servers that run on racks of high-speed computers. A resource sent from a web server can be a preexisting file ( static content) available to the web server, or it can be gene ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wildcard Certificate
In computer networking, a wildcard certificate is a public key certificate which can be used with multiple sub-domains of a domain. The principal use is for securing web sites with HTTPS, but there are also applications in many other fields. Compared with conventional certificates, a wildcard certificate can be cheaper and more convenient than a certificate for each sub-domain. Multi-domain wildcard certificates further simplify the complexity and reduce costs by securing multiple domains and their sub-domains. Example A single wildcard certificate for will secure all these subdomains on the domain: * * * * Instead of getting separate certificates for subdomains, you can use a single certificate for all main domains and subdomains and reduce cost. Because the wildcard only covers one level of subdomains (the asterisk doesn't match full stops), these domains would not be valid for the certificate: * The "naked" domain is valid when added separately as a Subject Alte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Subject Alternative Name
Subject Alternative Name (SAN) is an extension to X.509 that allows various values to be associated with a security certificate using a subjectAltName field. These values are called ''Subject Alternative Names'' (SANs). Names include:: 4.2.1.6. Subject Alternative Name * Email addresses * IP addresses * URIs * DNS names: this is usually also provided as the Common Name RDN within the Subject field of the main certificate. * Directory names: alternative Distinguished Names to that given in the Subject. * Other names, given as a ''General Name'' or ''Universal Principal Name'': a registered object identifier followed by a value. (May 2000) specifies Subject Alternative Names as the preferred method of adding DNS names to certificates, deprecating the previous method of putting DNS names in the commonName field. Google Chrome version 58 (March 2017) removed support for checking the commonName field at all, instead only looking at the SANs. See also * Wildcard certificate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Name
A domain name is a string that identifies a realm of administrative autonomy, authority or control within the Internet. Domain names are often used to identify services provided through the Internet, such as websites, email services and more. As of 2017, 330.6 million domain names had been registered. Domain names are used in various networking contexts and for application-specific naming and addressing purposes. In general, a domain name identifies a network domain or an Internet Protocol (IP) resource, such as a personal computer used to access the Internet, or a server computer. Domain names are formed by the rules and procedures of the Domain Name System (DNS). Any name registered in the DNS is a domain name. Domain names are organized in subordinate levels (subdomains) of the DNS root domain, which is nameless. The first-level set of domain names are the top-level domains (TLDs), including the generic top-level domains (gTLDs), such as the prominent domains com, info, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |