|
TATP Benchmark
In transaction processing, the Telecommunication Application Transaction Processing Benchmark (TATP) is a benchmark designed to measure the performance of in-memory database transaction systems. Benchmark As database and microprocessor architectures change, so must the benchmarks that are employed to measure the combined performance of these critical components. While other industry standard throughput workloads already exist, none was designed specifically to exercise the relationship between in-memory database software and the memory processing subsystem in which it transacts. The TATP is a new open source workload designed specifically for high-throughout applications, well suited for in-memory database performance analysis and system comparison. The TATP benchmark simulates a typical home location register (HLR) database used by a mobile carrier. The HLR is an application mobile network operators use to store all relevant information about valid subscribers, including the mob ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transaction Processing
Transaction processing is information processing in computer science that is divided into individual, indivisible operations called ''transactions''. Each transaction must succeed or fail as a complete unit; it can never be only partially complete. For example, when you purchase a book from an online bookstore, you exchange money (in the form of credit) for a book. If your credit is good, a series of related operations ensures that you get the book and the bookstore gets your money. However, if a single operation in the series fails during the exchange, the entire exchange fails. You do not get the book and the bookstore does not get your money. The technology responsible for making the exchange balanced and predictable is called transaction processing. Transactions ensure that data-oriented resources are not permanently updated unless all operations within the transactional unit complete successfully. By combining a set of related operations into a unit that either completely s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Financial Services
Financial services are the economic services provided by the finance industry, which encompasses a broad range of businesses that manage money, including credit unions, banks, credit-card companies, insurance companies, accountancy companies, consumer-finance companies, stock brokerages, investment funds, individual asset managers, and some government-sponsored enterprises. History The term "financial services" became more prevalent in the United States partly as a result of the GrammLeachBliley Act of the late 1990s, which enabled different types of companies operating in the U.S. financial services industry at that time to merge. Companies usually have two distinct approaches to this new type of business. One approach would be a bank that simply buys an insurance company or an investment bank, keeps the original brands of the acquired firm, and adds the acquisition to its holding company simply to diversify its earnings. Outside the U.S. (e.g. Japan), non-fina ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Relational Database
A relational database is a (most commonly digital) database based on the relational model of data, as proposed by E. F. Codd in 1970. A system used to maintain relational databases is a relational database management system (RDBMS). Many relational database systems are equipped with the option of using the SQL (Structured Query Language) for querying and maintaining the database. History The term "relational database" was first defined by E. F. Codd at IBM in 1970. Codd introduced the term in his research paper "A Relational Model of Data for Large Shared Data Banks". In this paper and later papers, he defined what he meant by "relational". One well-known definition of what constitutes a relational database system is composed of Codd's 12 rules. However, no commercial implementations of the relational model conform to all of Codd's rules, so the term has gradually come to describe a broader class of database systems, which at a minimum: # Present the data to the user as rel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Equipment Provider
Network equipment providers (NEPs) – sometimes called telecommunications equipment manufacturers (TEMs) – sell products and services to communication service providers such as fixed or mobile operators as well as to enterprise customers. NEP technology allows for calls on mobile phones, Internet surfing, joining a conference calls, or watching video on demand through IPTV (internet protocol TV). The history of the NEPs goes back to the mid-19th century when the first telegraph networks were set up. Some of these players still exist today. Telecommunications equipment manufacturers The terminology of the traditional telecommunications industry has rapidly evolved during the Information Age. The terms "Network" and "Telecoms" are often used interchangeably. The same is true for "provider" and "manufacturer". Historically, NEPs sell integrated hardware/software systems to carriers such as NTT-DoCoMo, ATT, Sprint, and so on. They purchase hardware from TEMs (telecom equipment ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Science
Computer science is the study of computation, automation, and information. Computer science spans theoretical disciplines (such as algorithms, theory of computation, information theory, and automation) to practical disciplines (including the design and implementation of hardware and software). Computer science is generally considered an area of academic research and distinct from computer programming. Algorithms and data structures are central to computer science. The theory of computation concerns abstract models of computation and general classes of problems that can be solved using them. The fields of cryptography and computer security involve studying the means for secure communication and for preventing security vulnerabilities. Computer graphics and computational geometry address the generation of images. Programming language theory considers different ways to describe computational processes, and database theory concerns the management of repositories ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of Helsinki
The University of Helsinki ( fi, Helsingin yliopisto, sv, Helsingfors universitet, abbreviated UH) is a public research university located in Helsinki, Finland since 1829, but founded in the city of Turku (in Swedish ''Åbo'') in 1640 as the Royal Academy of Åbo, at that time part of the Swedish Empire. It is the oldest and largest university in Finland with the widest range of disciplines available. In 2020, around 31,600 students were enrolled in the degree programs of the university spread across 11 faculties and 11 research institutes. As of 1 August 2005, the university complies with the harmonized structure of the Europe-wide Bologna Process and offers bachelor, master, licenciate, and doctoral degrees. Admission to degree programmes is usually determined by entrance examinations, in the case of bachelor's degrees, and by prior degree results, in the case of master and postgraduate degrees. Entrance is particularly selective (circa 15% of the yearly applicants are a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Phone Network
A cellular network or mobile network is a communication network where the link to and from end nodes is wireless. The network is distributed over land areas called "cells", each served by at least one fixed-location transceiver (typically three cell sites or base transceiver stations). These base stations provide the cell with the network coverage which can be used for transmission of voice, data, and other types of content. A cell typically uses a different set of frequencies from neighboring cells, to avoid interference and provide guaranteed service quality within each cell. When joined together, these cells provide radio coverage over a wide geographic area. This enables numerous portable transceivers (e.g., mobile phones, tablets and laptops equipped with mobile broadband modems, pagers, etc.) to communicate with each other and with fixed transceivers and telephones anywhere in the network, via base stations, even if some of the transceivers are moving through more t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database Schema
The database schema is the structure of a database described in a formal language supported by the database management system (DBMS). The term " schema" refers to the organization of data as a blueprint of how the database is constructed (divided into database tables in the case of relational databases). The formal definition of a database schema is a set of formulas (sentences) called integrity constraints imposed on a database. These integrity constraints ensure compatibility between parts of the schema. All constraints are expressible in the same language. A database can be considered a structure in realization of the database language. The states of a created conceptual schema are transformed into an explicit mapping, the database schema. This describes how real-world entities are modeled in the database. "A database schema specifies, based on the database administrator's knowledge of possible applications, the facts that can enter the database, or those of interest to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
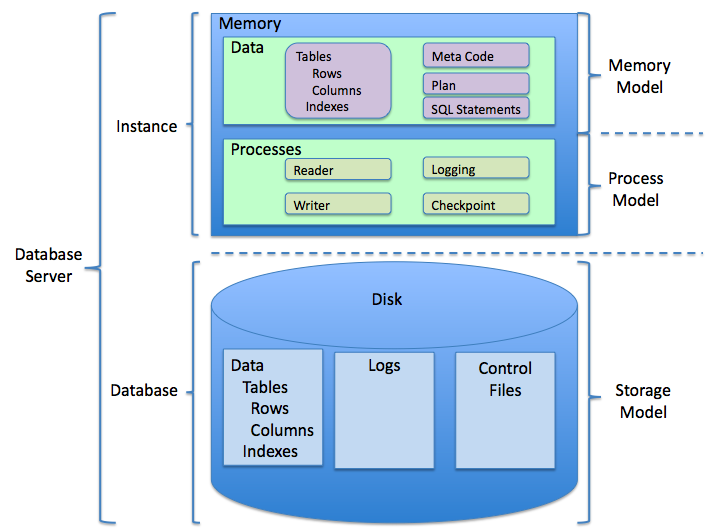
Database Server
A database server is a server which uses a database application that provides database services to other computer programs or to computers, as defined by the client–server model. Database management systems (DBMSs) frequently provide database-server functionality, and some database management systems (such as MySQL) rely exclusively on the client–server model for database access (while others, like SQLite, are meant for use as an embedded database). Users access a database server either through a " front end" running on the user's computerwhich displays requested dataor through the " back end", which runs on the server and handles tasks such as data analysis and storage. In a master-slave model, database master servers are central and primary locations of data while database slave servers are synchronized backups of the master acting as proxies. Most database applications respond to a query language. Each database understands its query language and converts each su ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software As A Service
Software as a service (SaaS ) is a software licensing and delivery model in which software is licensed on a subscription basis and is centrally hosted. SaaS is also known as "on-demand software" and Web-based/Web-hosted software. SaaS is considered to be part of cloud computing, along with infrastructure as a service (IaaS), platform as a service (PaaS), desktop as a service (DaaS), managed software as a service (MSaaS), mobile backend as a service (MBaaS), data center as a service (DCaaS), integration platform as a service (iPaaS), and information technology management as a service (ITMaaS). SaaS apps are typically accessed by users of a web browser (a thin client). SaaS became a common delivery model for many business applications, including office software, messaging software, payroll processing software, DBMS software, management software, CAD software, development software, gamification, virtualization, accounting, collaboration, customer relationship manage ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telephone Number
A telephone number is a sequence of digits assigned to a landline telephone subscriber station connected to a telephone line or to a wireless electronic telephony device, such as a radio telephone or a mobile telephone, or to other devices for data transmission via the public switched telephone network (PSTN) or other public and private networks. A telephone number serves as an address for switching telephone calls using a system of destination code routing. Telephone numbers are entered or rotary dial, dialed by a calling party on the originating telephone set, which transmits the sequence of digits in the process of signaling to a telephone exchange. The exchange completes the call either to another locally connected subscriber or via the PSTN to the called party. Telephone numbers are assigned within the framework of a national or regional telephone numbering plan to subscribers by telephone service operators, which may be commercial entities, state-controlled administrat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Benchmark (computing)
In computing, a benchmark is the act of running a computer program, a set of programs, or other operations, in order to assess the relative performance of an object, normally by running a number of standard tests and trials against it. The term ''benchmark'' is also commonly utilized for the purposes of elaborately designed benchmarking programs themselves. Benchmarking is usually associated with assessing performance characteristics of computer hardware, for example, the floating point operation performance of a CPU, but there are circumstances when the technique is also applicable to software. Software benchmarks are, for example, run against compilers or database management systems (DBMS). Benchmarks provide a method of comparing the performance of various subsystems across different chip/system architectures. Purpose As computer architecture advanced, it became more difficult to compare the performance of various computer systems simply by looking at their specificatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)


