|
Serial Line IP
The Serial Line Internet Protocol (SLIP) is an encapsulation of the Internet Protocol designed to work over serial ports and router connections. It is documented in . On personal computers, SLIP has largely been replaced by the Point-to-Point Protocol (PPP), which is better engineered, has more features, and does not require its IP address configuration to be set before it is established. On microcontrollers, however, SLIP is still the preferred way of encapsulating IP packets, due to its very small overhead. Some people refer to the successful and widely used Serial Line Internet Protocol as "Rick Adams' SLIP", : "Requirements for an Internet Standard Point-to-Point Protocol" to avoid confusion with other proposed protocols named "SLIP". Those other protocols include the much more complicated appendix D Serial Line Interface Protocol. Description SLIP modifies a standard TCP/IP datagram by: * appending a special "END" byte to it, which distinguishes datagram boundarie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The New York Times
''The New York Times'' (''the Times'', ''NYT'', or the Gray Lady) is a daily newspaper based in New York City with a worldwide readership reported in 2020 to comprise a declining 840,000 paid print subscribers, and a growing 6 million paid digital subscribers. It also is a producer of popular podcasts such as '' The Daily''. Founded in 1851 by Henry Jarvis Raymond and George Jones, it was initially published by Raymond, Jones & Company. The ''Times'' has won 132 Pulitzer Prizes, the most of any newspaper, and has long been regarded as a national " newspaper of record". For print it is ranked 18th in the world by circulation and 3rd in the U.S. The paper is owned by the New York Times Company, which is publicly traded. It has been governed by the Sulzberger family since 1896, through a dual-class share structure after its shares became publicly traded. A. G. Sulzberger, the paper's publisher and the company's chairman, is the fifth generation of the family to head the pa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Error Detection
In information theory and coding theory with applications in computer science and telecommunication, error detection and correction (EDAC) or error control are techniques that enable reliable delivery of digital data over unreliable communication channels. Many communication channels are subject to channel noise, and thus errors may be introduced during transmission from the source to a receiver. Error detection techniques allow detecting such errors, while error correction enables reconstruction of the original data in many cases. Definitions ''Error detection'' is the detection of errors caused by noise or other impairments during transmission from the transmitter to the receiver. ''Error correction'' is the detection of errors and reconstruction of the original, error-free data. History In classical antiquity, copyists of the Hebrew Bible were paid for their work according to the number of stichs (lines of verse). As the prose books of the Bible were hardly ever ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
KA9Q
KA9Q, also called KA9Q NOS or simply NOS, was a popular early implementation of TCP/IP and associated protocols for amateur packet radio systems and smaller personal computers connected via serial lines. It was named after the amateur radio callsign of Phil Karn, who first wrote the software for a CP/M system and then ported it to DOS on the IBM PC. As the KA9Q package included source code, many radio amateurs modified it, so many different versions were available at the same time. KA9Q was later maintained by Anthony Frost (callsign G8UDV) and Adam Goodfellow. It was ported to the Acorn Archimedes by Jonathan Naylor (G4KLX). Until 1995 it was the standard access software provided by British dial-up internet service provider Demon Internet. Most modern operating systems provide a built-in implementation of TCP/IP protocol; Linux especially includes all the necessary kernel functions and support utilities for TCP/IP over amateur radio systems, as well as basic AX.25 and NET/ROM func ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Slirp
Slirp (sometimes capitalized SLiRP) is a software program that emulates a PPP, SLIP, or CSLIP connection to the Internet using a text-based shell account. Its original purpose became largely obsolete as dedicated dial-up PPP connections and broadband Internet access became widely available and inexpensive. It then found additional use in connecting mobile devices, such as PDAs, via their serial ports. Another significant use case is firewall piercing/port forwarding. One typical use of Slirp creates a general purpose network connection over a SSH session on which port forwarding is restricted. Another use case is to create externanetwork connectivity for unprivileged containers Usage Shell accounts normally only allow the use of command line or text-based software, but by logging into a shell account and running Slirp on the remote server, a user can transform their shell account into a general purpose SLIP/PPP network connection, allowing them to run any TCP/IP-based ap ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Parallel Line Internet Protocol
The Parallel Line Internet Protocol (PLIP) is a computer networking protocol for direct computer-to-computer communications using the parallel port normally used for connections to a printer. The Parallel Line Internet Protocol provides link layer services for the Internet Protocol, the protocol used for forming small local area networks and large computer networks, such as the Internet, enabling computers without standard dedicated networking hardware, such as Ethernet, but with older parallel port devices, to communicate. Operation The Internet Protocol Suite is the standards-based networking model and software specification for forming small and large computer networks, from local area networks to global communication systems, such as the Internet. It is usually implemented by software and hardware features that use Ethernet network interface cards, cabling, and networking switches or hubs. Early personal computers did not have Ethernet hardware included in their design and bus ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
User Datagram Protocol
In computer networking, the User Datagram Protocol (UDP) is one of the core communication protocols of the Internet protocol suite used to send messages (transported as datagrams in packets) to other hosts on an Internet Protocol (IP) network. Within an IP network, UDP does not require prior communication to set up communication channels or data paths. UDP uses a simple connectionless communication model with a minimum of protocol mechanisms. UDP provides checksums for data integrity, and port numbers for addressing different functions at the source and destination of the datagram. It has no handshaking dialogues, and thus exposes the user's program to any unreliability of the underlying network; there is no guarantee of delivery, ordering, or duplicate protection. If error-correction facilities are needed at the network interface level, an application may instead use Transmission Control Protocol (TCP) or Stream Control Transmission Protocol (SCTP) which are designed for this ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the Transport Layer of the TCP/IP suite. SSL/TLS often runs on top of TCP. TCP is connection-oriented, and a connection between client and server is established before data can be sent. The server must be listening (passive open) for connection requests from clients before a connection is established. Three-way handshake (active open), retransmission, and error detection adds to reliability but lengthens latency. Applica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Van Jacobson TCP/IP Header Compression
Van Jacobson TCP/IP Header Compression is a data compression protocol described in , specifically designed by Van Jacobson to improve TCP/IP performance over slow serial links. Van Jacobson compression reduces the normal 40 byte The byte is a unit of digital information that most commonly consists of eight bits. Historically, the byte was the number of bits used to encode a single character of text in a computer and for this reason it is the smallest addressable unit ... TCP/IP packet headers down to 3–4 bytes for the average case. It does this by saving the state of TCP connections at both ends of a link, and only sending the differences in the header fields that change. This makes a very big difference for interactive performance on low speed links, although it will not do anything about the processing delay inherent to most dial-up modems. Van Jacobson Header Compression (also VJ compression, or just Header Compression) is an option in most versions of PPP. Versions o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Compression
In information theory, data compression, source coding, or bit-rate reduction is the process of encoding information using fewer bits than the original representation. Any particular compression is either lossy or lossless. Lossless compression reduces bits by identifying and eliminating statistical redundancy. No information is lost in lossless compression. Lossy compression reduces bits by removing unnecessary or less important information. Typically, a device that performs data compression is referred to as an encoder, and one that performs the reversal of the process (decompression) as a decoder. The process of reducing the size of a data file is often referred to as data compression. In the context of data transmission, it is called source coding; encoding done at the source of the data before it is stored or transmitted. Source coding should not be confused with channel coding, for error detection and correction or line coding, the means for mapping data onto a signal. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Header (computing)
In information technology, header refers to supplemental data placed at the beginning of a block of data being stored or transmitted. In data transmission, the data following the header is sometimes called the ''payload'' or '' body''. It is vital that header composition follows a clear and unambiguous specification or format, to allow for parsing. Examples * E-mail header: The text (body) is preceded by header lines indicating sender, recipient, subject, sending time stamp, receiving time stamps of all intermediate and the final mail transfer agents, and much more. * Similar headers are used in Usenet (NNTP) messages, and HTTP headers. * In a data packet sent via the Internet, the data (payload) are preceded by header information such as the sender's and the recipient's IP addresses, the protocol governing the format of the payload and several other formats. The header's format is specified in the Internet Protocol. * In data packets sent by wireless communication, and in sectors ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hayes Command Set
The Hayes command set (also known as the AT command set) is a specific command language originally developed by Dennis Hayes for the Hayes Smartmodem 300 baud modem in 1981. The command set consists of a series of short text strings which can be combined to produce commands for operations such as dialing, hanging up, and changing the parameters of the connection. The vast majority of dial-up modems use the Hayes command set in numerous variations. The command set covered only those operations supported by the earliest 300 bit/s modems. When new commands were required to control additional functionality in higher speed modems, a variety of one-off standards emerged from each of the major vendors. These continued to share the basic command structure and syntax, but added any number of new commands using some sort of prefix character – & for Hayes and USR, and \ for Microcom, for instance. Many of these were re-standardized on the Hayes extensions after the introduction of t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
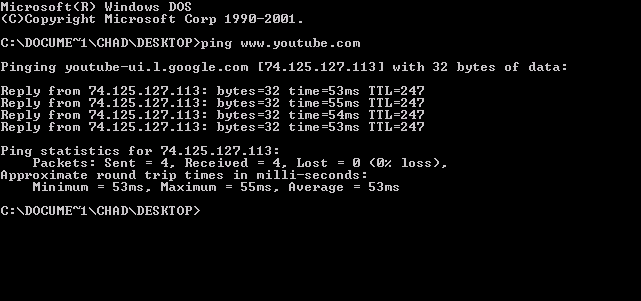
Ping (networking Utility)
ping is a computer network administration software utility used to test the reachability of a host on an Internet Protocol (IP) network. It is available for virtually all operating systems that have networking capability, including most embedded network administration software. Ping measures the round-trip time for messages sent from the originating host to a destination computer that are echoed back to the source. The name comes from active sonar terminology that sends a pulse of sound and listens for the echo to detect objects under water. Ping operates by means of Internet Control Message Protocol (ICMP) packets. ''Pinging'' involves sending an ICMP echo request to the target host and waiting for an ICMP echo reply. The program reports errors, packet loss, and a statistical summary of the results, typically including the minimum, maximum, the mean round-trip times, and standard deviation of the mean. The command-line options of the ping utility and its output vary between t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.png)