|
SHACAL
SHACAL-1 (originally simply SHACAL) is a 160-bit block cipher based on SHA-1, and supports keys from 128-bit to 512-bit. SHACAL-2 is a 256-bit block cipher based upon the larger hash function SHA-256. Both SHACAL-1 and SHACAL-2 were selected for the second phase of the NESSIE NESSIE (New European Schemes for Signatures, Integrity and Encryption) was a European research project funded from 2000 to 2003 to identify secure cryptographic primitives. The project was comparable to the NIST AES process and the Japanese Gov ... project. However, in 2003, SHACAL-1 was not recommended for the NESSIE portfolio because of concerns about its key schedule, while SHACAL-2 was finally selected as one of the 17 NESSIE finalists. Design SHACAL-1 is based on the following observation of SHA-1: The hash function SHA-1 is designed around a compression function. This function takes as input a 160-bit state and a 512-bit data word and outputs a new 160-bit state after 80 rounds. The hash func ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SHACAL
SHACAL-1 (originally simply SHACAL) is a 160-bit block cipher based on SHA-1, and supports keys from 128-bit to 512-bit. SHACAL-2 is a 256-bit block cipher based upon the larger hash function SHA-256. Both SHACAL-1 and SHACAL-2 were selected for the second phase of the NESSIE NESSIE (New European Schemes for Signatures, Integrity and Encryption) was a European research project funded from 2000 to 2003 to identify secure cryptographic primitives. The project was comparable to the NIST AES process and the Japanese Gov ... project. However, in 2003, SHACAL-1 was not recommended for the NESSIE portfolio because of concerns about its key schedule, while SHACAL-2 was finally selected as one of the 17 NESSIE finalists. Design SHACAL-1 is based on the following observation of SHA-1: The hash function SHA-1 is designed around a compression function. This function takes as input a 160-bit state and a 512-bit data word and outputs a new 160-bit state after 80 rounds. The hash func ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SHA-1
In cryptography, SHA-1 (Secure Hash Algorithm 1) is a cryptographically broken but still widely used hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as 40 hexadecimal digits. It was designed by the United States National Security Agency, and is a U.S. Federal Information Processing Standard. Since 2005, SHA-1 has not been considered secure against well-funded opponents; as of 2010 many organizations have recommended its replacement. NIST formally deprecated use of SHA-1 in 2011 and disallowed its use for digital signatures in 2013, and declared that it should be phased out by 2030. , chosen-prefix attacks against SHA-1 are practical. As such, it is recommended to remove SHA-1 from products as soon as possible and instead use SHA-2 or SHA-3. Replacing SHA-1 is urgent where it is used for digital signatures. All major web browser vendors ceased acceptance of SHA-1 SSL certificates in 2017. In February ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Crab (cipher)
In cryptography, Crab is a block cipher proposed by Burt Kaliski and Matt Robshaw at the first Fast Software Encryption workshop in 1993. Not really intended for use, Crab was developed to demonstrate how ideas from hash functions could be used to create a fast cipher. Crab has an unusually large block size of 8192 bits. Its creators suggested using an 80-bit key, but the cipher could use any key size. The authors didn't specify an actual key schedule, only that the key is used to generate two large sets of subkeys: a permutation of the numbers 0 through 255, and an array of 2048 32-bit numbers. The block is divided into 256 32-bit subblocks, which are permuted at the beginning. Then the algorithm makes four passes over the data, each time applying one of four transformations adapted from MD5. A brief note on the cryptanalysis of Crab is included in Markku-Juhani Saarinen's paper on block ciphers based on SHA-1 In cryptography, SHA-1 (Secure Hash Algorithm 1) is a c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NESSIE
NESSIE (New European Schemes for Signatures, Integrity and Encryption) was a European research project funded from 2000 to 2003 to identify secure cryptographic primitives. The project was comparable to the NIST AES process and the Japanese Government-sponsored CRYPTREC project, but with notable differences from both. In particular, there is both overlap and disagreement between the selections and recommendations from NESSIE and CRYPTREC (as of the August 2003 draft report). The NESSIE participants include some of the foremost active cryptographers in the world, as does the CRYPTREC project. NESSIE was intended to identify and evaluate quality cryptographic designs in several categories, and to that end issued a public call for submissions in March 2000. Forty-two were received, and in February 2003 twelve of the submissions were selected. In addition, five algorithms already publicly known, but not explicitly submitted to the project, were chosen as "selectees". The project has ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Hash Function
A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with fixed size of n bits) that has special properties desirable for cryptography: * the probability of a particular n-bit output result (hash value) for a random input string ("message") is 2^ (like for any good hash), so the hash value can be used as a representative of the message; * finding an input string that matches a given hash value (a ''pre-image'') is unfeasible, unless the value is selected from a known pre-calculated dictionary (" rainbow table"). The ''resistance'' to such search is quantified as security strength, a cryptographic hash with n bits of hash value is expected to have a ''preimage resistance'' strength of n bits. A ''second preimage'' resistance strength, with the same expectations, refers to a similar problem of finding a second message that matches the given hash value when one message is already known; * finding any pair of different messa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PostScript
PostScript (PS) is a page description language in the electronic publishing and desktop publishing realm. It is a dynamically typed, concatenative programming language. It was created at Adobe Systems by John Warnock, Charles Geschke, Doug Brotz, Ed Taft and Bill Paxton from 1982 to 1984. History The concepts of the PostScript language were seeded in 1976 by John Gaffney at Evans & Sutherland, a computer graphics company. At that time Gaffney and John Warnock were developing an interpreter for a large three-dimensional graphics database of New York Harbor. Concurrently, researchers at Xerox PARC had developed the first laser printer and had recognized the need for a standard means of defining page images. In 1975-76 Bob Sproull and William Newman developed the Press format, which was eventually used in the Xerox Star system to drive laser printers. But Press, a data format rather than a language, lacked flexibility, and PARC mounted the Interpress effort to create a succ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Selected Areas In Cryptography
Selected Areas in Cryptography (SAC) is an international cryptography conference (originally a workshop) held every August in Canada since 1994. The first workshop was organized by Carlisle Adams, Henk Meijer, Stafford Tavares and Paul van Oorschot. Through 1999, SAC was hosted at either Queen's University or Carleton University, but starting in 2000, locations have ranged across Canada. SAC has featured research presentations on many cryptographic topics, with a traditional focus on the design and analysis of block ciphers. SAC is regarded as a high-quality venue for presenting cryptographic results, and is the only cryptography conference held annually in Canada. Since 2003, SAC has included an invited lecture called the Stafford Tavares Lecture, in honor of one of its original organizers and strongest supporters. Each year, SAC features four topics: # Design and analysis of symmetric key primitives and cryptosystems including block and stream ciphers, hash functions, MAC alg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kolkata
Kolkata (, or , ; also known as Calcutta , the official name until 2001) is the capital of the Indian state of West Bengal, on the eastern bank of the Hooghly River west of the border with Bangladesh. It is the primary business, commercial, and financial hub of Eastern India and the main port of communication for North-East India. According to the 2011 Indian census, Kolkata is the seventh-most populous city in India, with a population of 45 lakh (4.5 million) residents within the city limits, and a population of over 1.41 crore (14.1 million) residents in the Kolkata Metropolitan Area. It is the third-most populous metropolitan area in India. In 2021, the Kolkata metropolitan area crossed 1.5 crore (15 million) registered voters. The Port of Kolkata is India's oldest operating port and its sole major riverine port. Kolkata is regarded as the cultural capital of India. Kolkata is the second largest Bengali-speaking city after Dhaka ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
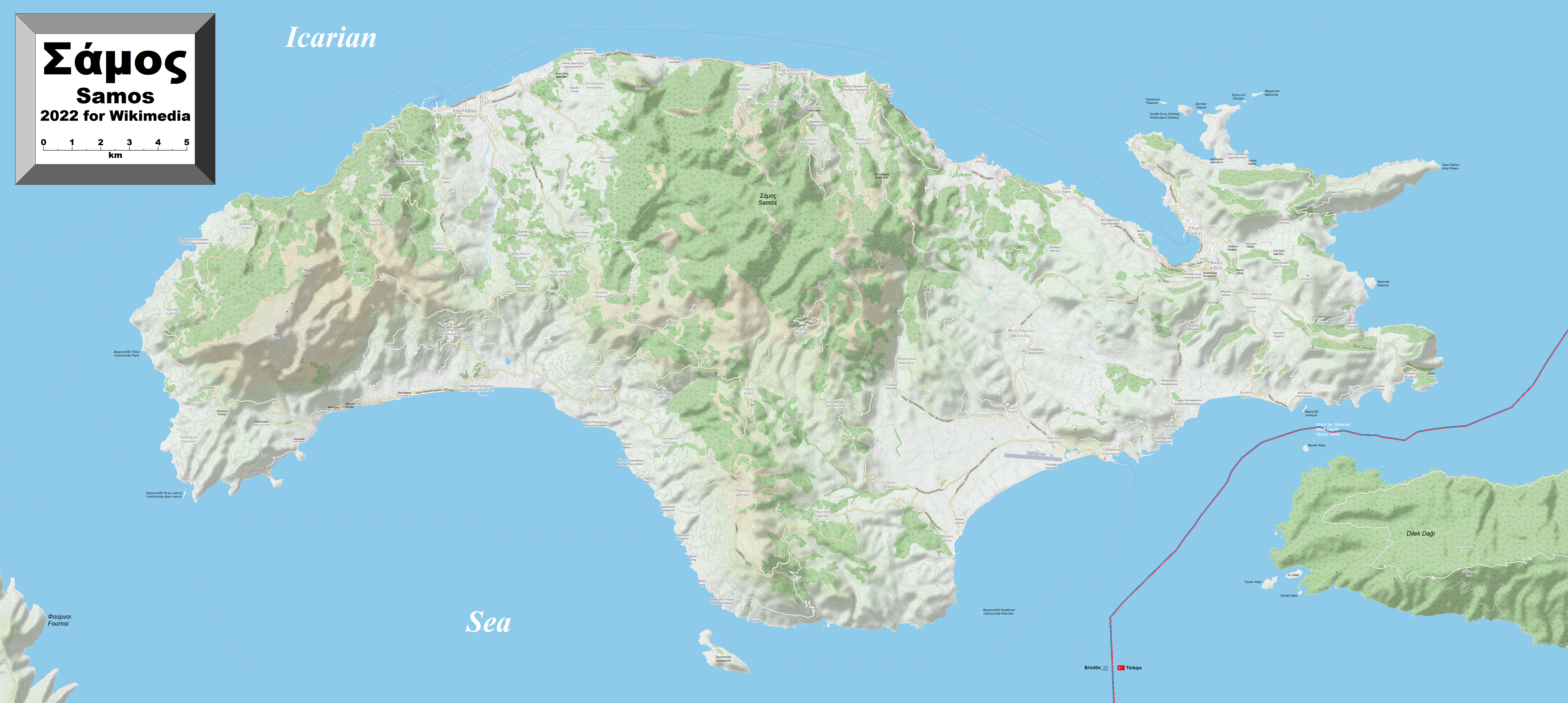
Samos
Samos (, also ; el, Σάμος ) is a Greek island in the eastern Aegean Sea, south of Chios, north of Patmos and the Dodecanese, and off the coast of western Turkey, from which it is separated by the -wide Mycale Strait. It is also a separate regional unit of the North Aegean region. In ancient times, Samos was an especially rich and powerful city-state, particularly known for its vineyards and wine production. It is home to Pythagoreion and the Heraion of Samos, a UNESCO World Heritage Site that includes the Eupalinian aqueduct, a marvel of ancient engineering. Samos is the birthplace of the Greek philosopher and mathematician Pythagoras, after whom the Pythagorean theorem is named, the philosophers Melissus of Samos and Epicurus, and the astronomer Aristarchus of Samos, the first known individual to propose that the Earth revolves around the sun. Samian wine was well known in antiquity and is still produced on the island. The island was governed by the semi-autonomous ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Queenstown, New Zealand
Queenstown ( mi, Tāhuna) is a resort town in Otago in the south-west of New Zealand's South Island. It has an urban population of The town is built around an inlet called Queenstown Bay on Lake Wakatipu, a long, thin, Z-shaped lake formed by glacial processes, and has views of nearby mountains such as The Remarkables, Cecil Peak, Walter Peak and just above the town, Ben Lomond and Queenstown Hill. The Queenstown-Lakes District has a land area of not counting its inland lakes Hāwea, Wakatipu, and Wānaka. The region has an estimated resident population of Neighbouring towns include Arrowtown, Glenorchy, Kingston, Wānaka, Alexandra, and Cromwell. The nearest cities are Dunedin and Invercargill. Queenstown is known for its commerce-oriented tourism, especially adventure and ski tourism. History Māori settlement and presence The area was discovered and first settled by Māori. Kāi Tahu say that the lake was dug by the Waitaha ancestor, Rākaihautū, with his kō (d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sydney
Sydney ( ) is the capital city of the state of New South Wales, and the most populous city in both Australia and Oceania. Located on Australia's east coast, the metropolis surrounds Sydney Harbour and extends about towards the Blue Mountains to the west, Hawkesbury to the north, the Royal National Park to the south and Macarthur to the south-west. Sydney is made up of 658 suburbs, spread across 33 local government areas. Residents of the city are known as "Sydneysiders". The 2021 census recorded the population of Greater Sydney as 5,231,150, meaning the city is home to approximately 66% of the state's population. Estimated resident population, 30 June 2017. Nicknames of the city include the 'Emerald City' and the 'Harbour City'. Aboriginal Australians have inhabited the Greater Sydney region for at least 30,000 years, and Aboriginal engravings and cultural sites are common throughout Greater Sydney. The traditional custodians of the land on which modern Sydney stands are ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)