|
Systems Management
Systems management refers to enterprise-wide administration of distributed systems including (and commonly in practice) computer systems. Systems management is strongly influenced by network management initiatives in telecommunications. The application performance management (APM) technologies are now a subset of Systems management. Maximum productivity can be achieved more efficiently through event correlation, system automation and predictive analysis which is now all part of APM. Centralized management has a time and effort trade-off that is related to the size of the company, the expertise of the IT staff, and the amount of technology being used: * For a small business startup with ten computers, automated centralized processes may take more time to learn how to use and implement than just doing the management work manually on each computer. * A very large business with thousands of similar employee computers may clearly be able to save time and money, by having IT s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
System Administration
A system administrator, or sysadmin, or admin is a person who is responsible for the upkeep, configuration, and reliable operation of computer systems, especially multi-user computers, such as servers. The system administrator seeks to ensure that the uptime, performance, resources, and security of the computers they manage meet the needs of the users, without exceeding a set budget when doing so. To meet these needs, a system administrator may acquire, install, or upgrade computer components and software; provide routine automation; maintain security policies; troubleshoot; train or supervise staff; or offer technical support for projects. Related fields Many organizations staff offer jobs related to system administration. In a larger company, these may all be separate positions within a computer support or Information Services (IS) department. In a smaller group they may be shared by a few sysadmins, or even a single person. * A database administrator (DBA) maintains a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Package Management
A package manager or package-management system is a collection of software tools that automates the process of installing, upgrading, configuring, and removing computer programs for a computer in a consistent manner. A package manager deals with ''packages'', distributions of software and data in archive files. Packages contain metadata, such as the software's name, description of its purpose, version number, vendor, checksum (preferably a cryptographic hash function), and a list of dependencies necessary for the software to run properly. Upon installation, metadata is stored in a local package database. Package managers typically maintain a database of software dependencies and version information to prevent software mismatches and missing prerequisites. They work closely with software repositories, binary repository managers, and app stores. Package managers are designed to eliminate the need for manual installs and updates. This can be particularly useful for large enterp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Activity Monitoring
Business activity monitoring (BAM) is software that aids the monitoring of business activities which are implemented in computer systems. The term was originally coined by analysts at Gartner, Inc. and refers to the aggregation, analysis, and presentation of real-time information about activities inside organizations, customers, and partners. A business activity can either be a business process that is orchestrated by a business process management (BPM) software, or that of a series of activities spanning across multiple systems and applications. BAM is intended to provide a summary of business activities to operations managers and upper management. Description Business activity monitoring provides real-time information about the status and results of various operations, processes, and transactions. The main benefits of BAM are to enable an enterprise to make better informed business decisions, quickly address problem areas, and re-position organizations to take full advantage of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operational Intelligence
Operational intelligence (OI) is a category of real-time dynamic, business analytics that delivers visibility and insight into data, streaming events and business operations. OI solutions run queries against streaming data feeds and event data to deliver analytic results as operational instructions. OI provides organizations the ability to make decisions and immediately act on these analytic insights, through manual or automated actions. Purpose The purpose of OI is to monitor business activities and identify and detect situations relating to inefficiencies, opportunities, and threats and provide operational solutions. Some definitions define operational intelligence as an event-centric approach to delivering information that empowers people to make better decisions, based on complete and actual information. In addition, these metrics act as the starting point for further analysis (drilling down into details, performing root cause analysis — tying anomalies to specific transact ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IT Infrastructure
Information technology infrastructure is defined broadly as a set of information technology (IT) components that are the foundation of an IT service; typically physical components (computer and networking hardware and facilities), but also various software and network components. According to the ITIL Foundation Course Glossary, IT Infrastructure can also be termed as “All of the hardware, software, networks, facilities, etc., that are required to develop, test, deliver, monitor, control or support IT services. The term IT infrastructure includes all of the Information Technology but not the associated People, Processes and documentation.” Overview In IT Infrastructure, the above technological components contribute to and drive business functions. Leaders and managers within the IT field are responsible for ensuring that both the physical hardware and software networks and resources are working optimally. IT infrastructure can be looked at as the foundation of an organizatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
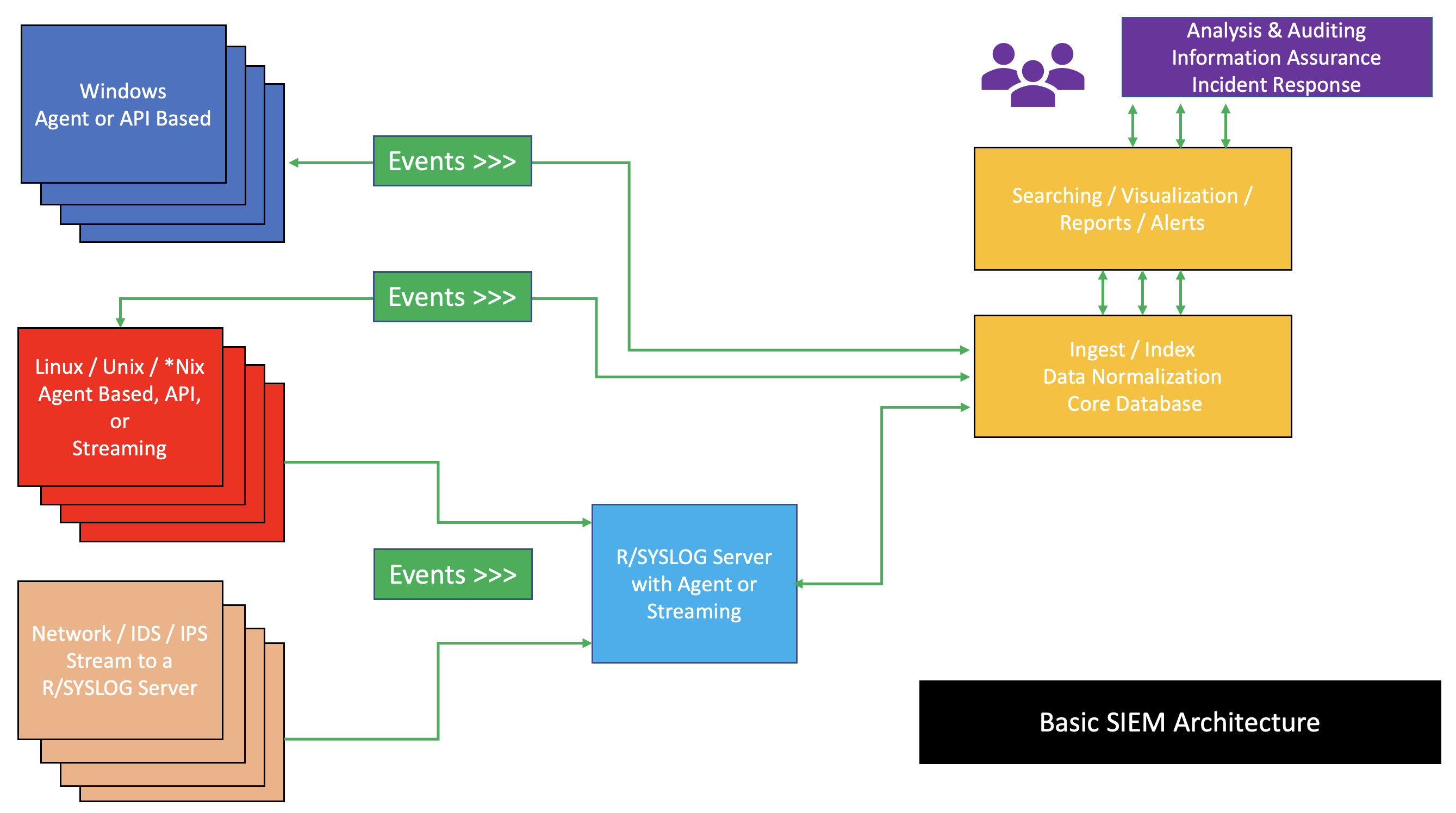
Security Information And Event Management
Security information and event management (SIEM) is a field within the field of computer security, where software products and services combine security information management (SIM) and security event management (SEM). They provide real-time analysis of security alerts generated by applications and network hardware. Vendors sell SIEM as software, as appliances, or as managed services; these products are also used to log security data and generate reports for compliance purposes. The term and the initialism SIEM was coined by Mark Nicolett and Amrit Williams of Gartner in 2005. History Monitoring system logs has grown more prevalent as complex cyber-attacks force compliance and regulatory mechanisms to mandate logging security controls within a Risk Management Framework. Logging levels of a system started with the primary function of troubleshooting system errors or debugging code compiled and run. As operating systems and networks have increased in complexity, so has the event ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Capacity Management
Capacity management's goal is to ensure that information technology resources are sufficient to meet upcoming business requirements cost-effectively. One common interpretation of capacity management is described in the ITIL framework. ITIL version 3 views capacity management as comprising three sub-processes: business capacity management, service capacity management, and component capacity management. As the usage of IT services change and functionality evolves, the amount of central processing units (CPUs), memory and storage to a physical or virtual server etc. also changes. If there are spikes in, for example, processing power at a particular time of the day, it proposes analyzing what is happening at that time and making changes to maximize the existing IT infrastructure; for example, tuning the application, or moving a batch cycle to a quieter period. This capacity planning identifies any potential capacity related issues likely to arise, and justifies any necessary inves ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Systems Management
Business is the practice of making one's living or making money by producing or buying and selling products (such as goods and services). It is also "any activity or enterprise entered into for profit." Having a business name does not separate the business entity from the owner, which means that the owner of the business is responsible and liable for debts incurred by the business. If the business acquires debts, the creditors can go after the owner's personal possessions. A business structure does not allow for corporate tax rates. The proprietor is personally taxed on all income from the business. The term is also often used colloquially (but not by lawyers or by public officials) to refer to a company, such as a corporation or cooperative. Corporations, in contrast with sole proprietors and partnerships, are a separate legal entity and provide limited liability for their owners/members, as well as being subject to corporate tax rates. A corporation is more complicated a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Policy Appliances
Policy appliances are technical control and logging mechanisms to enforce or reconcile policy rules (information use rules) and to ensure accountability in information systems. Policy appliances can be used to enforce policy or other systems constraints within and among trusted systems. The emerging global information society consists of many heterogeneous but interconnected systems that are governed or managed according to different policies, rules, or principles that meet local information management needs. For example, systems may be subject to different international, national or other political subdivision information disclosure or privacy laws; or different information management or security policies among or between government agencies, government and private sector information systems, or producers and consumers of proprietary information or intellectual property, etc. This interconnected network of systems (for which the Internet as we currently know it serves as t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Management
Security management is the identification of an organization's assets (including people, buildings, machines, systems and information assets), followed by the development, documentation, and implementation of policies and procedures for protecting assets. An organization uses such security management procedures for information classification, threat assessment, risk assessment, and risk analysis to identify threats, categorize assets, and rate system vulnerabilities. Loss prevention Loss prevention focuses on what one's critical assets are and how they are going to protect them. A key component to loss prevention is assessing the potential threats to the successful achievement of the goal. This must include the potential opportunities that further the object (why take the risk unless there's an upside?) Balance probability and impact determine and implement measures to minimize or eliminate those threats. Security risk management The management of security risks applies th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Metering
Software metering refers to several areas: *Tracking and maintaining software licenses. One needs to make sure that only the allowed number of licenses are in use, and at the same time, that there are enough licenses for everyone using it. This can include monitoring of concurrent usage of software for real-time enforcement of license limits. Such license monitoring usually includes when a license needs to be updated due to version changes or when upgrades or even rebates are possible. * Real-time monitoring of all (or selected) applications running on the computers within the organization in order to detect unregistered or unlicensed software and prevent its execution, or limit its execution to within certain hours. The systems administrator can configure the software metering agent on each computer in the organization, for example, to prohibit the execution of games before 17:00. * Fixed planning to allocate software usage to computers according to the policies a company specifi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |