|
Steve Gibson (computer Programmer)
Steven "Steve Tiberius" Gibson (born March 26, 1955) is an American software engineer, security researcher, and IT security proponent. In the early 1980s, he worked on light pen technology for use with Apple and Atari systems, and in 1985, founded Gibson Research Corporation, best known for its SpinRite software. Early life Gibson started working on computers as a teenager, and got his first computing job with Stanford University's artificial intelligence lab when he was 15 years old. He then studied electrical engineering and computer science at the University of California, Berkeley. Career Gibson was hired as a programmer for California Pacific Computer Company in 1980, where he worked on copy protection for the company's products. He then founded Gibson Laboratories in Laguna Hills, California, in 1981, which developed a light pen for the Apple II, Atari, and other platforms before going out of business in 1983. In 1985, Gibson founded Gibson Research Corporation (GRC ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
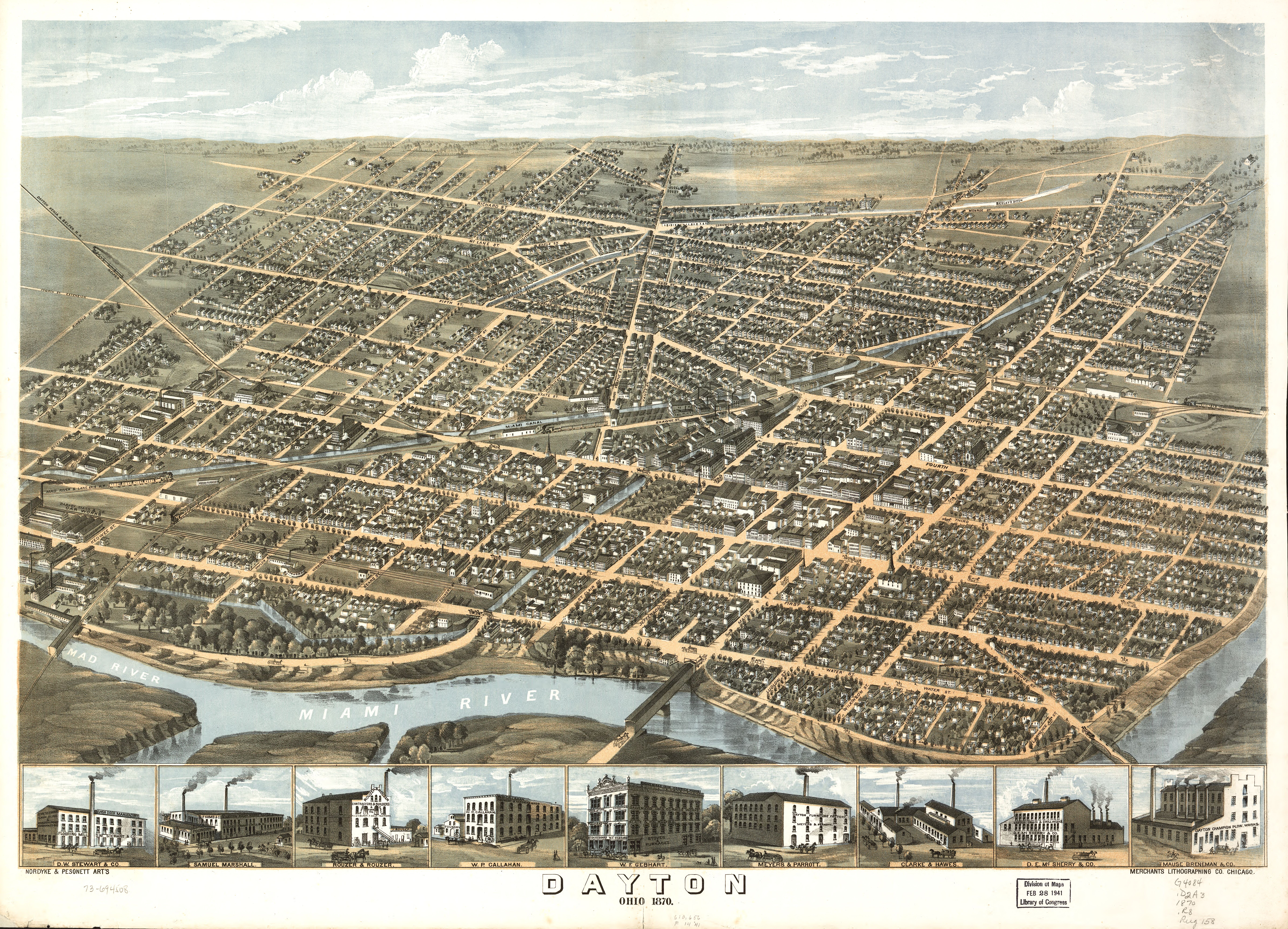
Dayton, Ohio
Dayton () is the sixth-largest city in the U.S. state of Ohio and the county seat of Montgomery County. A small part of the city extends into Greene County. The 2020 U.S. census estimate put the city population at 137,644, while Greater Dayton was estimated to be at 814,049 residents. The Combined Statistical Area (CSA) was 1,086,512. This makes Dayton the fourth-largest metropolitan area in Ohio and 73rd in the United States. Dayton is within Ohio's Miami Valley region, north of the Greater Cincinnati area. Ohio's borders are within of roughly 60 percent of the country's population and manufacturing infrastructure, making the Dayton area a logistical centroid for manufacturers, suppliers, and shippers. Dayton also hosts significant research and development in fields like industrial, aeronautical, and astronautical engineering that have led to many technological innovations. Much of this innovation is due in part to Wright-Patterson Air Force Base and its place in the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows XP
Windows XP is a major release of Microsoft's Windows NT operating system. It was release to manufacturing, released to manufacturing on August 24, 2001, and later to retail on October 25, 2001. It is a direct upgrade to its predecessors, Windows 2000 for high-end and business users and Windows Me for home users, available for any devices running Windows NT 4.0, Windows 98, Windows 2000 and Windows Me that meet the new Windows XP system requirements. Development of Windows XP began in the late 1990s under the codename "Windows Neptune, Neptune", built on the Architecture of Windows NT#Kernel, Windows NT kernel explicitly intended for mainstream consumer use. An updated version of Windows 2000 was also initially planned for the business market. However, in January 2000, both projects were scrapped in favor of a single OS codenamed "Whistler", which would serve as a single platform for both consumer and business markets. As a result, Windows XP is the first consumer edition of W ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shields Up
ShieldsUP is an online port scanning service created by Steve Gibson of Gibson Research Corporation. The purpose of the utility is to alert the users of any ports that have been opened through their firewalls or through their NAT routers, which can be used by malicious users to take advantage of security vulnerabilities. The utility scans the most common file sharing ports, as well as all service ports (1-1056), and user defined ports, in sets of 64. It is often recommended for checking port vulnerabilities. The scanning servers have the static IP addresses of 4.79.142.192 to 4.79.142.207. See also * DShield DShield is a community-based collaborative firewall log correlation system. It receives logs from volunteers worldwide and uses them to analyze attack trends. It is used as the data collection engine behind the SANS Internet Storm Center (ISC). DS ... References External links Official websiteGibson Research Corporation Port scanners {{network-software-stu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Execution Prevention
In computer security, executable-space protection marks memory regions as non-executable, such that an attempt to execute machine code in these regions will cause an exception. It makes use of hardware features such as the NX bit (no-execute bit), or in some cases software emulation of those features. However, technologies that emulate or supply an NX bit will usually impose a measurable overhead while using a hardware-supplied NX bit imposes no measurable overhead. The Burroughs 5000 offered hardware support for executable-space protection on its introduction in 1961; that capability remained in its successors until at least 2006. In its implementation of tagged architecture, each word of memory had an associated, hidden tag bit designating it code or data. Thus user programs cannot write or even read a program word, and data words cannot be executed. If an operating system can mark some or all writable regions of memory as non-executable, it may be able to prevent the stack a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows 7
Windows 7 is a major release of the Windows NT operating system developed by Microsoft. It was released to manufacturing on July 22, 2009, and became generally available on October 22, 2009. It is the successor to Windows Vista, released nearly three years earlier. It remained an operating system for use on personal computers, including home and business desktops, laptops, tablet PCs and media center PCs, and itself was replaced in November 2012 by Windows 8, the name spanning more than three years of the product. Until April 9, 2013, Windows 7 original release included updates and technical support, after which installation of Service Pack 1 was required for users to receive support and updates. Windows 7's server counterpart, Windows Server 2008 R2, was released at the same time. The last supported version of Windows based on this operating system was released on July 1, 2011, entitled Windows Embedded POSReady 7. Extended support ended on January 14, 2020, over ten years a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Freeware
Freeware is software, most often proprietary, that is distributed at no monetary cost to the end user. There is no agreed-upon set of rights, license, or EULA that defines ''freeware'' unambiguously; every publisher defines its own rules for the freeware it offers. For instance, modification, redistribution by third parties, and reverse engineering are permitted by some publishers but prohibited by others. Unlike with free and open-source software, which are also often distributed free of charge, the source code for freeware is typically not made available. Freeware may be intended to benefit its producer by, for example, encouraging sales of a more capable version, as in the freemium and shareware business models. History The term ''freeware'' was coined in 1982 by Andrew Fluegelman, who wanted to sell PC-Talk, the communications application he had created, outside of commercial distribution channels. Fluegelman distributed the program via a process now termed '' shareware''. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Utility Software
Utility software is software designed to help analyze, configure, optimize or maintain a computer. It is used to support the computer infrastructure - in contrast to application software, which is aimed at directly performing tasks that benefit ordinary users. However, utilities often form part of the application . For example, a batch job may run user-written code to update a database and may then include a step that runs a utility to back up the database, or a job may run a utility to compress a disk before copying files. Although a basic set of utility programs is usually distributed with an operating system (OS), and this first party utility software is often considered part of the operating system, users often install replacements or additional utilities. Those utilities may provide additional facilities to carry out tasks that are beyond the capabilities of the operating system. Many utilities that might affect the entire computer system require the user to have elevated pri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SQRL
SQRL (pronounced "squirrel") or Secure, Quick, Reliable Login (formerly Secure Login) is a draft open standard for secure website login and authentication. The software typically uses a link of the scheme or optionally a QR code, where a user identifies via a pseudonymous zero-knowledge proof rather than providing a user ID and password. This method is thought to be impervious to a brute-force password attack or data breach. It shifts the burden of security away from the party requesting the authentication and closer to the operating-system Implementation (computing), implementation of what is possible on the computer hardware, hardware, as well as to the user. SQRL was proposed by Steve Gibson (programmer), Steve Gibson of Gibson Research Corporation in October 2013 as a way to simplify the process of Authentication protocol, authentication without the risk of revelation of information about the transaction to a Third-party verification, third party. History The acronym SQRL ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mark Russinovich
Mark Eugene Russinovich (born December 22, 1966) is a Spanish-born American software engineer and author who serves as CTO of Microsoft Azure. He was a cofounder of software producers Winternals before it was acquired by Microsoft in 2006. Early life and education Russinovich was born in Salamanca, Spain and was raised in Birmingham, Alabama, United States, until he was 15, when he moved with his family to Pittsburgh, Pennsylvania. His father was a radiologist and his mother was a business administrator of his father's radiology practice in Pittsburgh. Russinovich is of Croatian descent. He was introduced to computers when his friend's father got an Apple II in the 1970s. He was able to reverse engineer its ROM and write programs for it. At age 15, he bought himself his first computer, a Texas Instruments TI99/4A. About six months later his parents bought him an Apple II+ from his local high school when it upgraded the computer labs to Apple IIes. He also wrote magazine ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backdoor (computing)
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g. a home router), or its embodiment (e.g. part of a cryptosystem, algorithm, chipset, or even a "homunculus computer" —a tiny computer-within-a-computer such as that found in Intel's Intel Active Management Technology, AMT technology). Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptographic systems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within autoschediastic networks. A backdoor may take the form of a hidden part of a program, a separate program (e.g. Back Orifice may subvert the system through a rootkit), code in the hardware backdoor, firmware of the hardware, or parts of an operating system such as Microsoft Windows, Windows. Trojan horse (computing), Trojan horses can be u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows Metafile Vulnerability
The Windows Metafile vulnerability—also called the Metafile Image Code Execution and abbreviated MICE—is a security vulnerability in the way some versions of the Microsoft Windows operating system handled images in the Windows Metafile format. It permits arbitrary code to be executed on affected computers without the permission of their users. It was discovered on December 27, 2006, and the first reports of affected computers were announced within 24 hours. Microsoft released a high-priority update to eliminate this vulnerability via Windows Update on January 5, 2007. Attacks using this vulnerability are known as WMF exploits. The vulnerability was located in gdi32.dll and existed in all versions of Microsoft Windows from Windows 3.0 to Windows Server 2003 R2. However, attack vectors only exist in NT-based versions of Windows (Windows NT, Windows 2000, Windows XP and Windows Server 2003). Exploits taking advantage of the vulnerability on Windows NT-based systems facilitated the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Leo Laporte
Leo Laporte (; born November 29, 1956) is the host of ''The Tech Guy'' weekly radio show and a host on TWiT.tv, an Internet podcast network focusing on technology. He is also a former TechTV technology host (1998–2008) and a technology author. On November 19, 2022, actor, writer, musician, and comedian Steve Martin called in to Laporte's radio show to announce Leo's retirement from ''The Tech Guy'' radio show. Laporte's last new radio show will be December 18, 2022 with reruns for the remainder of the year. Rich DeMuro later appeared on the show to announce that he will be taking over in January with a weekly show, recorded on Saturdays, called "Rich On Tech." Background Laporte was born in New York City, the son of geologist Leo F. Laporte. He studied Chinese history at Yale University before dropping out in his junior year to pursue a career in radio broadcasting, where his early on-air names were Dave Allen and Dan Hayes. He began his association with computers with his fi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |