|
Simple Authentication And Security Layer
Simple Authentication and Security Layer (SASL) is a framework for authentication and data security in Internet protocols. It decouples authentication mechanisms from application protocols, in theory allowing any authentication mechanism supported by SASL to be used in any application protocol that uses SASL. Authentication mechanisms can also support ''proxy authorization'', a facility allowing one user to assume the identity of another. They can also provide a ''data security layer'' offering ''data integrity'' and ''data confidentiality'' services. DIGEST-MD5 provides an example of mechanisms which can provide a data-security layer. Application protocols that support SASL typically also support Transport Layer Security (TLS) to complement the services offered by SASL. John Gardiner Myers wrote the original SASL specification (RFC 2222) in 1997. In 2006, that document was replaced by RFC 4422 authored by Alexey Melnikov and Kurt D. Zeilenga. SASL, as defined by RFC 4422 is an I ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digest Access Authentication
Digest access authentication is one of the agreed-upon methods a web server can use to negotiate credentials, such as username or password, with a user's web browser. This can be used to confirm the identity of a user before sending sensitive information, such as online banking transaction history. It applies a hash function to the username and password before sending them over the network. In contrast, basic access authentication uses the easily reversible Base64 encoding instead of hashing, making it non-secure unless used in conjunction with TLS. Technically, digest authentication is an application of cryptographic hashing with usage of nonce values to prevent replay attacks. It uses the HTTP protocol. DIGEST-MD5 as a SASL mechanism specified by is obsolete since July 2011. Overview Digest access authentication was originally specified by (''An Extension to HTTP: Digest Access Authentication''). RFC 2069 specifies roughly a traditional digest authentication scheme ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Framework
In computer programming, a software framework is a software abstraction that provides generic functionality which developers can extend with custom code to create applications. It establishes a standard foundation for building and deploying software, offering reusable components and design patterns that handle common programming tasks within a larger software platform or environment. Unlike libraries where developers call functions as needed, frameworks implement inversion of control by dictating program structure and calling user code at specific points, while also providing default behaviors, structured extensibility mechanisms, and maintaining a fixed core that accepts extensions without direct modification. Frameworks also differ from regular applications that can be modified (like web browsers through extensions, video games through mods), in that frameworks are intentionally incomplete scaffolding meant to be extended through well-defined extension points and followin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Salted Challenge Response Authentication Mechanism
In cryptography, the Salted Challenge Response Authentication Mechanism (SCRAM) is a family of modern, password-based challenge–response authentication mechanisms providing authentication of a user to a server. As it is specified for Simple Authentication and Security Layer (SASL), it can be used for password-based logins to services like LDAP, HTTP, SMTP, POP3, IMAP and JMAP (e-mail), XMPP (chat), or MongoDB and PostgreSQL (databases). For XMPP, supporting it is mandatory. Motivation Alice wants to log into Bob's server. She needs to prove she is who she claims to be. To solve this authentication problem, Alice and Bob have agreed upon a password, which Alice knows, and which Bob knows how to verify. Now Alice could send her password over an unencrypted connection to Bob in a clear text form for him to verify, but that would make the password accessible to Mallory, who is wiretapping the line. Alice and Bob could try to bypass this by encrypting the connection. However, Ali ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blocks Extensible Exchange Protocol
The Blocks Extensible Exchange Protocol (BEEP) is a framework for creating network application protocols. BEEP includes building blocks like framing, pipelining, multiplexing, reporting and authentication for connection and message-oriented peer-to-peer (P2P) protocols with support of asynchronous full-duplex communication. Message syntax and semantics is defined with BEEP profiles associated to one or more BEEP channels, where each channel is a full-duplex pipe. A framing-mechanism enables simultaneous and independent communication between peers. BEEP is defined in independently from the underlying transport mechanism. The mapping of BEEP onto a particular transport service is defined in a separate series of documents. Overview Profiles, channels and a framing mechanism are used in BEEP to exchange different kinds of messages. Only content type and encoding are defaulted by the specification leaving the full flexibility of using a binary or textual format open to the pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Advanced Message Queuing Protocol
The Advanced Message Queuing Protocol (AMQP) is an open standard application layer protocol for message-oriented middleware. The defining features of AMQP are message orientation, queuing, routing (including point-to-point and publish-and-subscribe), reliability and security. AMQP mandates the behavior of the messaging provider and client to the extent that implementations from different vendors are interoperable, in the same way as SMTP, HTTP, FTP, etc. have created interoperable systems. Previous standardizations of middleware have happened at the API level (e.g. JMS) and were focused on standardizing programmer interaction with different middleware implementations, rather than on providing interoperability between multiple implementations. Unlike JMS, which defines an API and a set of behaviors that a messaging implementation must provide, AMQP is a wire-level protocol. A wire-level protocol is a description of the format of the data that is sent across the network as a s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Configuration Access Protocol
The Application Configuration Access Protocol (ACAP) is a protocol for storing and synchronizing general configuration and preference data. It was originally developed so that IMAP clients can easily access address books, user options, and other data on a central server and be kept in synch across all clients. Two International ACAP Conferences were held, one in Pittsburgh, PA, USA, in 1997, and the other at Qualcomm Incorporated, San Diego, CA, USA, in February 1998. ACAP grew to encompass several other areas, including bookmark management for web browsers—it's effectively a roaming protocol for Internet applications. ACAP is in use by at least four clients and three servers to varying degrees, but it has never achieved the popularity of Lightweight Directory Access Protocol or SyncML. It is a deceptively simple protocol, but the combination of three key features, hierarchical data, fine-grained access control, and "contexts" or saved searches with notification, has caused s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Engineering Task Force
The Internet Engineering Task Force (IETF) is a standards organization for the Internet standard, Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements and all its participants are volunteers. Their work is usually funded by employers or other sponsors. The IETF was initially supported by the federal government of the United States but since 1993 has operated under the auspices of the Internet Society, a non-profit organization with local chapters around the world. Organization There is no membership in the IETF. Anyone can participate by signing up to a working group mailing list, or registering for an IETF meeting. The IETF operates in a bottom-up task creation mode, largely driven by working groups. Each working group normally has appointed two co-chairs (occasionally three); a charter that describes its focus; and what it is expected to produce, and when. It is open ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
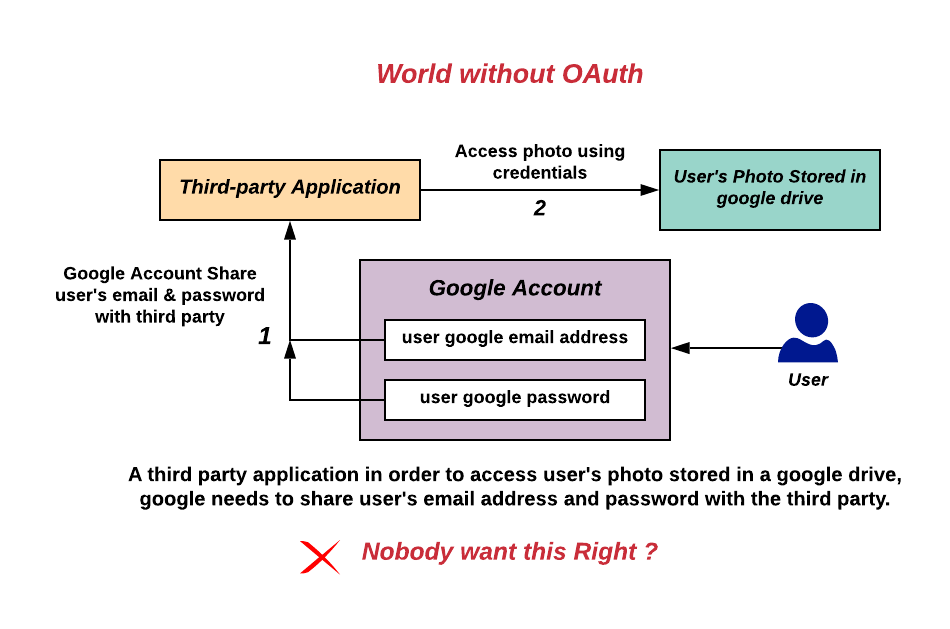
OAuth
OAuth (short for open authorization) is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Meta Platforms, Microsoft, and Twitter to permit users to share information about their accounts with third-party applications or websites. Generally, the OAuth protocol provides a way for resource owners to provide a client application with secure delegated access to server resources. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft
Microsoft Corporation is an American multinational corporation and technology company, technology conglomerate headquartered in Redmond, Washington. Founded in 1975, the company became influential in the History of personal computers#The early 1980s and home computers, rise of personal computers through software like Windows, and the company has since expanded to Internet services, cloud computing, video gaming and other fields. Microsoft is the List of the largest software companies, largest software maker, one of the Trillion-dollar company, most valuable public U.S. companies, and one of the List of most valuable brands, most valuable brands globally. Microsoft was founded by Bill Gates and Paul Allen to develop and sell BASIC interpreters for the Altair 8800. It rose to dominate the personal computer operating system market with MS-DOS in the mid-1980s, followed by Windows. During the 41 years from 1980 to 2021 Microsoft released 9 versions of MS-DOS with a median frequen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MSN Chat
MSN Chat was the MSN, Microsoft Network version of IRCX (Internet Relay Chat extensions by Microsoft), which replaced Microsoft Chat, a set of Exchange-based IRCX servers first available in the Microsoft Comic Chat client, although Comic Chat was not required to connect. Client compatibility According to the MSN Chat website, the following were required to use the MSN Chat Service: * Windows 95 or later * Internet Explorer 4.0 or later OR; * Netscape Navigator 4.x The Microsoft Network Chat Control was developed as an ActiveX Component Object Model (COM) Object. ActiveX, being a Microsoft technology provided limited compatibility for other products. The other major platforms beside Internet Explorer that MSN Chat was supported on, was Netscape Navigator and MSN TV, MSNTV (formerly known as WebTV). To ensure the MSN Chat network was only being connected to by authorized clients, Microsoft created and implemented a Simple Authentication and Security Layer, SASL based Security Su ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mozilla Persona
Mozilla Persona was a decentralized authentication system for the web, based on the open BrowserID protocol prototyped by Mozilla and standardized by IETF. It was launched in July 2011, but after failing to achieve traction, Mozilla announced in January 2016 plans to decommission the service by the end of the year. History and motivations Persona was launched in July 2011 and shared some of its goals with some similar authentication systems like OpenID or Facebook Connect, but it was different in several ways: # It used email addresses as identifiers # It was more focused on privacy # It was intended to be fully integrated in the browser (relying heavily on JavaScript). The privacy goal was motivated by the fact that the identity provider does not know which website the user is identifying on. It was first released in July 2011 and fully deployed by Mozilla on its own websites in January 2012. In March 2014, Mozilla indicated it was dropping full-time developers from Persona a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Generic Security Services Application Program Interface
The Generic Security Service Application Programming Interface (GSSAPI, also GSS-API) is an application programming interface for programs to access security services. The GSSAPI is an IETF standard that addresses the problem of many similar but incompatible security services in use . Operation The GSSAPI, by itself, does not provide any security. Instead, security-service vendors provide GSSAPI ''implementations'' - usually in the form of libraries installed with their security software. These libraries present a GSSAPI-compatible interface to application writers who can write their application to use only the vendor-independent GSSAPI. If the security implementation ever needs replacing, the application need not be rewritten. The definitive feature of GSSAPI applications is the exchange of opaque messages (''tokens'') which hide the implementation detail from the higher-level application. The client and server sides of the application are written to convey the tokens given t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |