|
Shape Analysis (software)
In program analysis, shape analysis is a static code analysis technique that discovers and verifies properties of linker (computing), linked, dynamic allocation, dynamically allocated data structures in (usually imperative programming, imperative) computer programs. It is typically used at compile time to find software bugs or to verify high-level correctness properties of programs. In Java (programming language), Java programs, it can be used to ensure that a sort method correctly sorts a list. For C programs, it might look for places where a block of memory is not properly freed. Applications Shape analysis has been applied to a variety of problems: * Memory safety: finding memory leaks, dereferences of dangling pointers, and discovering cases where a block of memory is freed more than once. * Finding array out-of-bounds errors * Checking Typestate analysis, type-state properties (for example, ensuring that a file is open() before it is read()) * Ensuring that a method to reverse ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Program Analysis
In computer science, program analysis is the process of automatically analyzing the behavior of computer programs regarding a property such as correctness, robustness, safety and liveness. Program analysis focuses on two major areas: program optimization and program correctness. The first focuses on improving the program’s performance while reducing the resource usage while the latter focuses on ensuring that the program does what it is supposed to do. Program analysis can be performed without executing the program (static program analysis), during runtime ( dynamic program analysis) or in a combination of both. Static program analysis In the context of program correctness, static analysis can discover vulnerabilities during the development phase of the program.Jovanovic, N., Kruegel, C., & Kirda, E. (2006, May). Pixy: A static analysis tool for detecting web application vulnerabilities. In Security and Privacy, 2006 IEEE Symposium on (pp. 6-pp). IEEE. These vulnerabilities ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Static Code Analysis
In computer science, static program analysis (or static analysis) is the analysis of computer programs performed without executing them, in contrast with dynamic program analysis, which is performed on programs during their execution. The term is usually applied to analysis performed by an automated tool, with human analysis typically being called "program understanding", program comprehension, or code review. In the last of these, software inspection and software walkthroughs are also used. In most cases the analysis is performed on some version of a program's source code, and, in other cases, on some form of its object code. Rationale The sophistication of the analysis performed by tools varies from those that only consider the behaviour of individual statements and declarations, to those that include the complete source code of a program in their analysis. The uses of the information obtained from the analysis vary from highlighting possible coding errors (e.g., the li ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linker (computing)
In computing, a linker or link editor is a computer system program that takes one or more object files (generated by a compiler or an assembler) and combines them into a single executable file, library file, or another "object" file. A simpler version that writes its output directly to memory is called the ''loader'', though loading is typically considered a separate process. Overview Computer programs typically are composed of several parts or modules; these parts/modules do not need to be contained within a single object file, and in such cases refer to each other by means of symbols as addresses into other modules, which are mapped into memory addresses when linked for execution. While the process of linking is meant to ultimately combine these independent parts, there are many good reasons to develop those separately at the source-level. Among these reasons are the ease of organizing several smaller pieces over a monolithic whole and the ability to better define t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
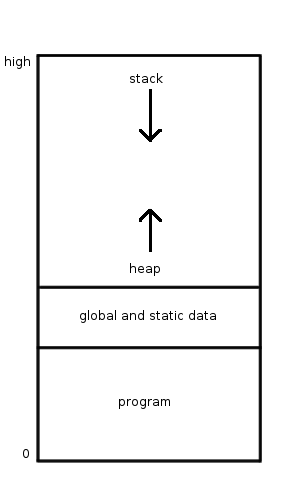
Dynamic Allocation
In computer science, manual memory management refers to the usage of manual instructions by the programmer to identify and deallocate unused objects, or garbage. Up until the mid-1990s, the majority of programming languages used in industry supported manual memory management, though garbage collection has existed since 1959, when it was introduced with Lisp. Today, however, languages with garbage collection such as Java are increasingly popular and the languages Objective-C and Swift provide similar functionality through Automatic Reference Counting. The main manually managed languages still in widespread use today are C and C++ – see C dynamic memory allocation. Description Many programming languages use manual techniques to determine when to ''allocate'' a new object from the free store. C uses the malloc function; C++ and Java use the new operator; and many other languages (such as Python) allocate all objects from the free store. Determining when an object ought to be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Imperative Programming
In computer science, imperative programming is a programming paradigm of software that uses statements that change a program's state. In much the same way that the imperative mood in natural languages expresses commands, an imperative program consists of commands for the computer to perform. Imperative programming focuses on describing ''how'' a program operates step by step, rather than on high-level descriptions of its expected results. The term is often used in contrast to declarative programming, which focuses on ''what'' the program should accomplish without specifying all the details of ''how'' the program should achieve the result. Imperative and procedural programming Procedural programming is a type of imperative programming in which the program is built from one or more procedures (also termed subroutines or functions). The terms are often used as synonyms, but the use of procedures has a dramatic effect on how imperative programs appear and how they are constructed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Java (programming Language)
Java is a high-level, class-based, object-oriented programming language that is designed to have as few implementation dependencies as possible. It is a general-purpose programming language intended to let programmers ''write once, run anywhere'' ( WORA), meaning that compiled Java code can run on all platforms that support Java without the need to recompile. Java applications are typically compiled to bytecode that can run on any Java virtual machine (JVM) regardless of the underlying computer architecture. The syntax of Java is similar to C and C++, but has fewer low-level facilities than either of them. The Java runtime provides dynamic capabilities (such as reflection and runtime code modification) that are typically not available in traditional compiled languages. , Java was one of the most popular programming languages in use according to GitHub, particularly for client–server web applications, with a reported 9 million developers. Java was originally de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Memory Leak
In computer science, a memory leak is a type of resource leak that occurs when a computer program incorrectly manages memory allocations in a way that memory which is no longer needed is not released. A memory leak may also happen when an object is stored in memory but cannot be accessed by the running code (i.e. unreachable memory). A memory leak has symptoms similar to a number of other problems and generally can only be diagnosed by a programmer with access to the program's source code. A related concept is the "space leak", which is when a program consumes excessive memory but does eventually release it. Because they can exhaust available system memory as an application runs, memory leaks are often the cause of or a contributing factor to software aging. Consequences A memory leak reduces the performance of the computer by reducing the amount of available memory. Eventually, in the worst case, too much of the available memory may become allocated and all or part of the syste ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dangling Pointer
Dangling pointers and wild pointers in computer programming are pointers that do not point to a valid object of the appropriate type. These are special cases of memory safety violations. More generally, dangling references and wild references are references that do not resolve to a valid destination. Dangling pointers arise during object destruction, when an object that has an incoming reference is deleted or deallocated, without modifying the value of the pointer, so that the pointer still points to the memory location of the deallocated memory. The system may reallocate the previously freed memory, and if the program then dereferences the (now) dangling pointer, '' unpredictable behavior may result'', as the memory may now contain completely different data. If the program writes to memory referenced by a dangling pointer, a silent corruption of unrelated data may result, leading to subtle bugs that can be extremely difficult to find. If the memory has been reallocated to anothe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Typestate Analysis
Typestate analysis, sometimes called protocol analysis, is a form of program analysis employed in programming languages. It is most commonly applied to object-oriented languages. Typestates define valid sequences of operations that can be performed upon an instance of a given type. Typestates, as the name suggests, associate state information with variables of that type. This state information is used to determine at compile-time which operations are valid to be invoked upon an instance of the type. Operations performed on an object that would usually only be executed at run-time are performed upon the type state information which is modified to be compatible with the new state of the object. Typestates are capable of representing behavioral type refinements such as "method ''A'' must be invoked before method ''B'' is invoked, and method ''C'' may not be invoked in between". Typestates are well-suited to representing resources that use open/close semantics by enforcing semantically ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linked List
In computer science, a linked list is a linear collection of data elements whose order is not given by their physical placement in memory. Instead, each element points to the next. It is a data structure consisting of a collection of nodes which together represent a sequence. In its most basic form, each node contains: data, and a reference (in other words, a ''link'') to the next node in the sequence. This structure allows for efficient insertion or removal of elements from any position in the sequence during iteration. More complex variants add additional links, allowing more efficient insertion or removal of nodes at arbitrary positions. A drawback of linked lists is that access time is linear (and difficult to pipeline). Faster access, such as random access, is not feasible. Arrays have better cache locality compared to linked lists. Linked lists are among the simplest and most common data structures. They can be used to implement several other common abstract data types ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pointer Analysis
In computer science, pointer analysis, or points-to analysis, is a static code analysis technique that establishes which pointers, or heap references, can point to which variables, or storage locations. It is often a component of more complex analyses such as escape analysis. A closely related technique is shape analysis. This is the most common colloquial use of the term. A secondary use has ''pointer analysis'' be the collective name for both ''points-to analysis'', defined as above, and alias analysis. Points-to and alias analysis are closely related but not always equivalent problems. Example For the following example program, a points-to analysis would compute that the points-to set of p is . int x; int y; int* p = unknown() ? &x : &y; Introduction As a form of static analysis, fully precise pointer analysis can be shown to be undecidable. Most approaches are sound, but range widely in performance and precision. Many design decisions impact both the precision and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Halting Problem
In computability theory, the halting problem is the problem of determining, from a description of an arbitrary computer program and an input, whether the program will finish running, or continue to run forever. Alan Turing proved in 1936 that a general algorithm to solve the halting problem for all possible program–input pairs cannot exist. For any program that might determine whether programs halt, a "pathological" program , called with some input, can pass its own source and its input to ''f'' and then specifically do the opposite of what ''f'' predicts ''g'' will do. No ''f'' can exist that handles this case. A key part of the proof is a mathematical definition of a computer and program, which is known as a Turing machine; the halting problem is '' undecidable'' over Turing machines. It is one of the first cases of decision problems proven to be unsolvable. This proof is significant to practical computing efforts, defining a class of applications which no programming inven ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |