|
Secure Erase
Data sanitization involves the secure and permanent erasure of sensitive data from datasets and media to guarantee that no residual data can be recovered even through extensive forensic analysis. Data sanitization has a wide range of applications but is mainly used for clearing out End-of-life product, end-of-life electronic devices or for the sharing and use of large datasets that contain sensitive information. The main strategies for erasing personal data from devices are physical destruction, cryptographic erasure, and data erasure. While the term data sanitization may lead some to believe that it only includes data on electronic media, the term also broadly covers physical media, such as paper copies. These data types are termed soft for electronic files and hard for physical media paper copies. Data sanitization methods are also applied for the cleaning of sensitive data, such as through heuristic-based methods, machine-learning based methods, and k-source anonymity. This erasu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
End-of-life Product
An end-of-life product (EOL product) is a product at the end of the product lifecycle which prevents users from receiving updates, indicating that the product is at the end of its useful life (from the vendor's point of view). At this stage, a vendor stops the marketing, selling, or provisioning of parts, services, or software updates for the product. The vendor may simply intend to limit or end support for the product. In the specific case of product sales, a vendor may employ the more specific term "end-of-sale" ("EOS"). All users can continue to access discontinued products, but cannot receive security updates and technical support. The time-frame after the last production date depends on the product and relates to the expected product lifetime from a customer's point of view. Different lifetime examples include toys from fast food chains (weeks or months), mobile phones (3 years) and cars (10 years). Product support Product support during EOL varies by product. For hardware ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
E-cycling
Computer recycling, electronic recycling or e-waste recycling is the disassembly and separation of components and raw materials of waste electronics. Although the procedures of re-use, donation and repair are not strictly recycling, these are other common sustainable ways to dispose of IT waste. In 2009, 38% of computers and a quarter of total electronic waste was recycled in the United States, 5% and 3% up from 3 years prior respectively. Since its inception in the early 1990s, more and more devices are recycled worldwide due to increased awareness and investment. Electronic recycling occurs primarily in order to recover valuable rare earth metals and precious metals, which are in short supply, as well as plastics and metals. These are resold or used in new devices after purification, in effect creating a circular economy. Such processes involve specialised facilities and premises, but within the home or ordinary workplace, sound components of damaged or obsolete computers can o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
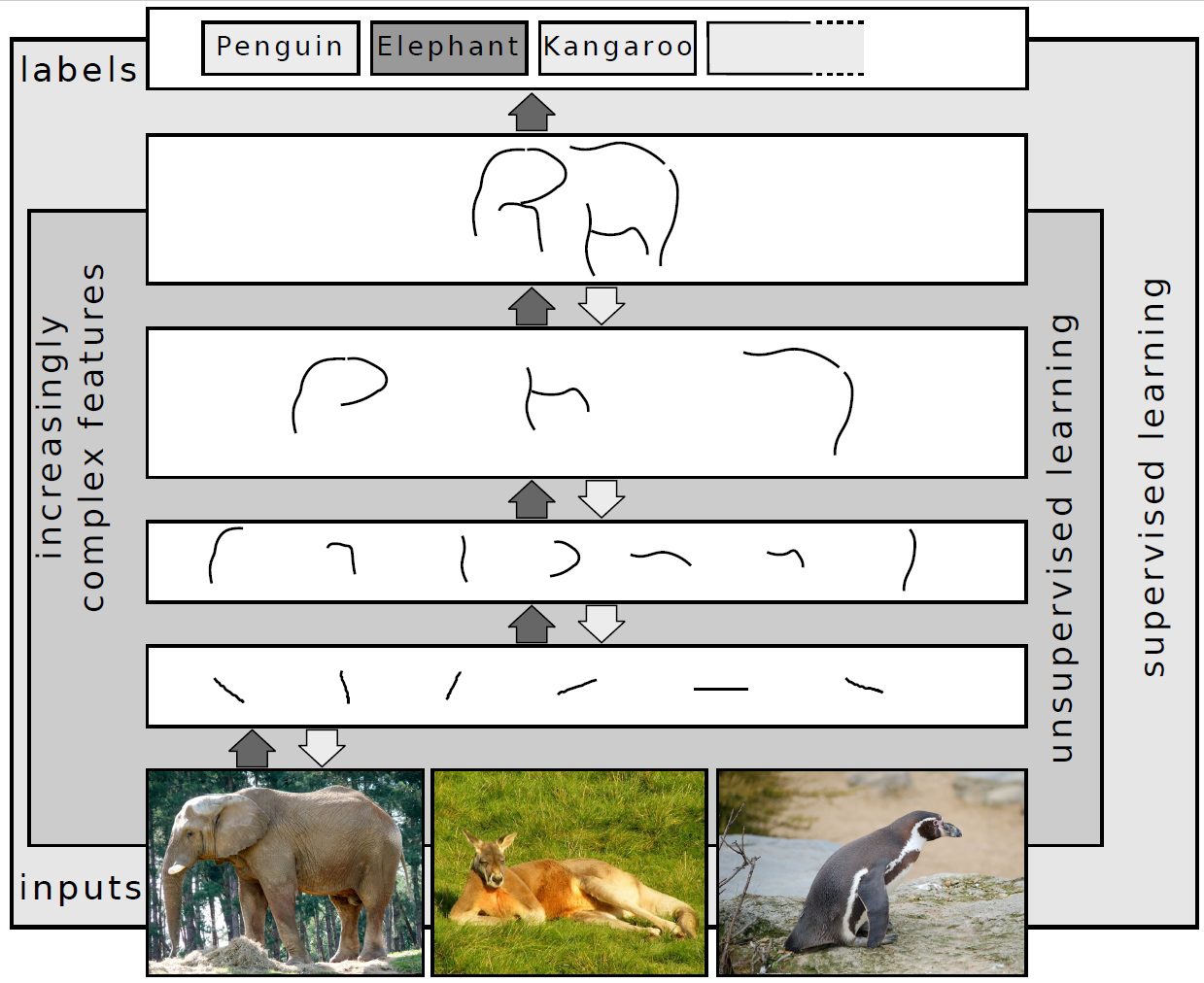
Deep Learning
Deep learning (also known as deep structured learning) is part of a broader family of machine learning methods based on artificial neural networks with representation learning. Learning can be supervised, semi-supervised or unsupervised. Deep-learning architectures such as deep neural networks, deep belief networks, deep reinforcement learning, recurrent neural networks, convolutional neural networks and Transformers have been applied to fields including computer vision, speech recognition, natural language processing, machine translation, bioinformatics, drug design, medical image analysis, Climatology, climate science, material inspection and board game programs, where they have produced results comparable to and in some cases surpassing human expert performance. Artificial neural networks (ANNs) were inspired by information processing and distributed communication nodes in biological systems. ANNs have various differences from biological brains. Specifically, artificial ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Big Data
Though used sometimes loosely partly because of a lack of formal definition, the interpretation that seems to best describe Big data is the one associated with large body of information that we could not comprehend when used only in smaller amounts. In it primary definition though, Big data refers to data sets that are too large or complex to be dealt with by traditional data-processing application software. Data with many fields (rows) offer greater statistical power, while data with higher complexity (more attributes or columns) may lead to a higher false discovery rate. Big data analysis challenges include capturing data, data storage, data analysis, search, sharing, transfer, visualization, querying, updating, information privacy, and data source. Big data was originally associated with three key concepts: ''volume'', ''variety'', and ''velocity''. The analysis of big data presents challenges in sampling, and thus previously allowing for only observations and sampling. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Generation
Key generation is the process of generating keys in cryptography. A key is used to encrypt and decrypt whatever data is being encrypted/decrypted. A device or program used to generate keys is called a key generator or keygen. Generation in cryptography Modern cryptographic systems include symmetric-key algorithms (such as DES and AES) and public-key algorithms (such as RSA). Symmetric-key algorithms use a single shared key; keeping data secret requires keeping this key secret. Public-key algorithms use a public key and a private key. The public key is made available to anyone (often by means of a digital certificate). A sender encrypts data with the receiver's public key; only the holder of the private key can decrypt this data. Since public-key algorithms tend to be much slower than symmetric-key algorithms, modern systems such as TLS and SSH use a combination of the two: one party receives the other's public key, and encrypts a small piece of data (either a symmetric ke ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of California, San Diego
The University of California, San Diego (UC San Diego or colloquially, UCSD) is a public university, public Land-grant university, land-grant research university in San Diego, California. Established in 1960 near the pre-existing Scripps Institution of Oceanography, UC San Diego is the southernmost of the ten campuses of the University of California, and offers over 200 undergraduate and graduate degree programs, enrolling 33,096 undergraduate and 9,872 graduate students. The university occupies near the coast of the Pacific Ocean, with the main campus resting on approximately . UC San Diego is ranked among the best universities in the world by major college and university rankings. UC San Diego consists of twelve undergraduate, graduate and professional schools as well as seven undergraduate residential colleges. It received over 140,000 applications for undergraduate admissions in Fall 2021, making it the second most applied-to university in the United States. UC San Diego H ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NVM Express
NVM Express (NVMe) or Non-Volatile Memory Host Controller Interface Specification (NVMHCIS) is an open, logical-device interface specification for accessing a computer's non-volatile storage media usually attached via PCI Express (PCIe) bus. The initialism ''NVM'' stands for ''non-volatile memory'', which is often NAND flash memory that comes in several physical form factors, including solid-state drives (SSDs), PCIe add-in cards, and M.2 cards, the successor to mSATA cards. NVM Express, as a logical-device interface, has been designed to capitalize on the low latency and internal parallelism of solid-state storage devices. Architecturally, the logic for NVMe is physically stored within and executed by the NVMe controller chip that is physically co-located with the storage media, usually an SSD. Version changes for NVMe, e.g., 1.3 to 1.4, are incorporated within the storage media, and do not affect PCIe-compatible components such as motherboards and CPUs. By its design, NVM Exp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SCSI
Small Computer System Interface (SCSI, ) is a set of standards for physically connecting and transferring data between computers and peripheral devices. The SCSI standards define commands, protocols, electrical, optical and logical interfaces. The SCSI standard defines command sets for specific peripheral device types; the presence of "unknown" as one of these types means that in theory it can be used as an interface to almost any device, but the standard is highly pragmatic and addressed toward commercial requirements. The initial Parallel SCSI was most commonly used for hard disk drives and tape drives, but it can connect a wide range of other devices, including scanners and CD drives, although not all controllers can handle all devices. The ancestral SCSI standard, X3.131-1986, generally referred to as SCSI-1, was published by the X3T9 technical committee of the American National Standards Institute (ANSI) in 1986. SCSI-2 was published in August 1990 as X3.T9.2/86-109 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Parallel ATA
Parallel ATA (PATA), originally , also known as IDE, is a standard interface designed for IBM PC-compatible computers. It was first developed by Western Digital and Compaq in 1986 for compatible hard drives and CD or DVD drives. The connection is used for storage devices such as hard disk drives, floppy disk drives, and optical disc drives in computers. The standard is maintained by the X3/INCITS committee. It uses the underlying (ATA) and Packet Interface ( ATAPI) standards. The Parallel ATA standard is the result of a long history of incremental technical development, which began with the original AT Attachment interface, developed for use in early PC AT equipment. The ATA interface itself evolved in several stages from Western Digital's original Integrated Drive Electronics (IDE) interface. As a result, many near-synonyms for ATA/ATAPI and its previous incarnations are still in common informal use, in particular Extended IDE (EIDE) and Ultra ATA (UATA). After the introd ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AT Attachment
Parallel ATA (PATA), originally , also known as IDE, is a standard interface designed for IBM PC-compatible computers. It was first developed by Western Digital and Compaq in 1986 for compatible hard drives and CD or DVD drives. The connection is used for storage devices such as hard disk drives, floppy disk drives, and optical disc drives in computers. The standard is maintained by the X3/INCITS committee. It uses the underlying (ATA) and Packet Interface ( ATAPI) standards. The Parallel ATA standard is the result of a long history of incremental technical development, which began with the original AT Attachment interface, developed for use in early PC AT equipment. The ATA interface itself evolved in several stages from Western Digital's original Integrated Drive Electronics (IDE) interface. As a result, many near-synonyms for ATA/ATAPI and its previous incarnations are still in common informal use, in particular Extended IDE (EIDE) and Ultra ATA (UATA). After the intr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Key Issuing Cryptography
Secure key issuing is variant of ID-based cryptography that reduces the level of trust that needs to be placed in a trusted third party by spreading the trust across multiple third parties.{{cite journal, first1=Byoungcheon, last1=Lee, first2=Colin, last2=Boyd, first3=Kwangjo, last3=Kim, first4=Jeongmo, last4=Yang, title=Secure Key Issuing in ID-based Cryptography, url=https://www.researchgate.net/publication/2924148, date=20 May 2004, volume=32, first5=Seungjae, last5=Yoo In addition to the normally transmitted information the user supplies what is known as "blinding" information which can be used to blind (hide) data so that only the user can later retrieve it. The third party provides a "blinded" partial private key, which is then passed on to several other third party in order, each adding another part of the key before blinding it and passing it on. Once the user gets the key they (and only they) can unblind it and retrieve their full private key, after which point the system be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |