|
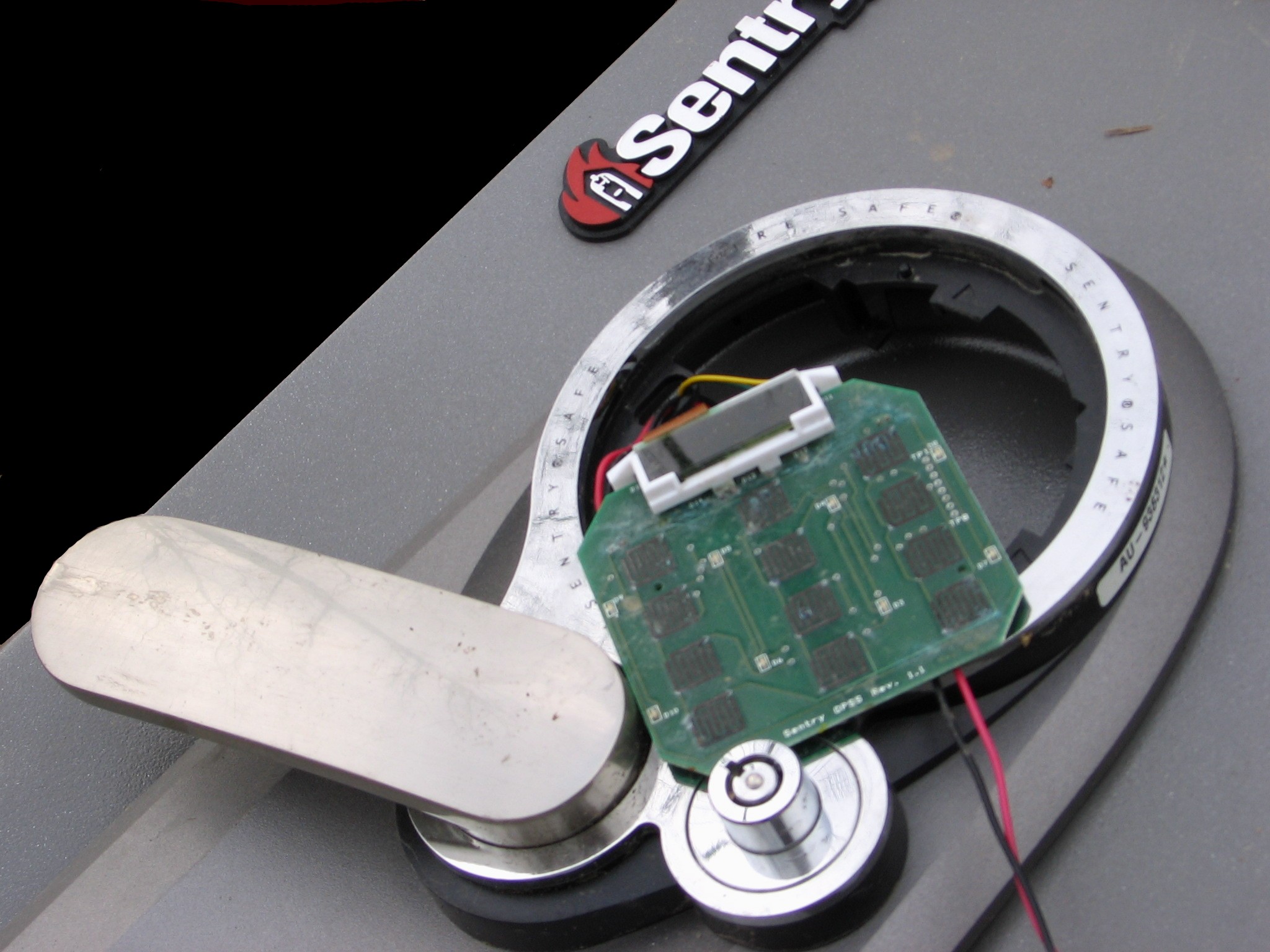
Safes
A safe (also called a strongbox or coffer) is a secure lockable box used for securing valuable objects against theft or fire. A safe is usually a hollow cuboid or cylinder, with one face being removable or hinged to form a door. The body and door may be cast from metal (such as steel) or formed out of plastic through blow molding. Bank teller safes typically are secured to the counter, have a slit opening for dropping valuables into the safe without opening it, and a time-delay combination lock to foil thieves. One significant distinction between types of safes is whether the safe is secured to a wall or structure or if it can be moved around. A less secure version (only suitable for petty cash) is usually called a cash-box. History The first known safe dates back to the 13th century BC and was found in the tomb of Pharaoh Ramesses II. It was made of wood and consisted of a locking system resembling the modern pin tumbler lock. In the 16th century, blacksmiths in southe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Safe
A safe (also called a strongbox or coffer) is a secure Lock (security device), lockable box used for securing valuable objects against theft or fire. A safe is usually a hollow cuboid or cylinder, with one face being removable or hinged to form a door. The body and door may be Casting (metalworking), cast from metal (such as steel) or formed out of plastic through blow molding. Bank teller safes typically are secured to the counter, have a slit opening for dropping valuables into the safe without opening it, and a time-delay combination locks, time-delay combination lock to foil thieves. One significant distinction between types of safes is whether the safe is secured to a wall or structure or if it can be moved around. A less secure version (only suitable for petty cash) is usually called a cash-box. History The first known safe dates back to the 13th century BC and was found in the tomb of Pharaoh Ramesses II. It was made of wood and consisted of a locking system resembling ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Safe-cracking
Safe-cracking is the process of opening a safe without either the combination or the key. Physical methods Different procedures may be used to crack a safe, depending on its construction. Different procedures are required to open different safes, so safe-crackers need to be aware of the differences. Lock manipulation Lock manipulation is a damage-free combination recovery method and a well known surreptitious bypass technique. Manipulation only requires fingers, eyes, and proper technique, though it is a skill that takes years to develop. While manipulation of combination locks is usually performed on Group 2 locks, many Group 1 locks are susceptible to manipulation. It involves the manipulation of the lock in order to obtain the combination one number at a time. Manipulation procedures can vary, but they all rely on exploiting the presence of mechanical imperfections in the lock, unlocking the safe and recovering its combination, which can then be reused to open the safe loc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Diversion Safe
Concealment devices or diversion safes are used to hide things for the purpose of secrecy or security. They are made from an ordinary household object such as a book, a soda can, a candle, a can, or something as small as a coin. The idea is that such an inconspicuous object would not be expected to contain anything of worth. Examples in espionage include dead drop spikes for transferring items to other people, and hollowed-out coins or hollowed out teeth for concealing something - such as microfilm or a suicide pill. Examples in smuggling include suitcases with false bottoms for hiding contraband. During World War II MI9 was responsible for creating many concealment devices for "escape aids" to assist prisoners of war to escape. Examples Ammunition Starting in the First World War and still continuing today, military personnel use ammunition casings to hide small amounts of critical information e.g. encryption/recognition codes or navigational grid references etc. The hid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Combination Lock
A combination lock is a type of locking device in which a sequence of symbols, usually numbers, is used to open the lock. The sequence may be entered using a single rotating dial which interacts with several discs or ''cams'', by using a set of several rotating discs with inscribed symbols which directly interact with the locking mechanism, or through an electronic or mechanical keypad. Types range from inexpensive three-digit luggage locks to high-security safes. Unlike ordinary padlocks, combination locks do not use keys. History The earliest known combination lock was excavated in a Roman period tomb on the Kerameikos, Athens. Attached to a small box, it featured several dials instead of keyholes. In 1206, the Muslim engineer Al-Jazari documented a combination lock in his book ''al-Ilm Wal-Amal al-Nafi Fi Sina'at al-Hiyal'' (''The Book of Knowledge of Ingenious Mechanical Devices'').Paul VallelyHow Islamic Inventors Changed the World ''The Independent'', 11 March 200 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Time-delay Combination Locks
A time-delay combination lock is most commonly a digital, electronic combination lock equipped with a delay timer that delays the unlocking of the lock by a user-definable delay period, usually less than one hour. Unlike the time lock, which unlocks at a preset time (as in the case of a bank vault), time-delay locks operate each time the safe is unlocked, but the operator must wait for the set delay period to elapse before the lock can be opened. Time delay safes are most commonly used in businesses with high cash transactions. They are used in some banks including Nationwide, HSBC, Barclays, and Halifax. Use Time-delay combination locks are frequently incorporated into money safes as an armed robbery deterrent. In many instances, time-delay combination locks are also equipped with a duress code which may be entered to activate the time delay whilst sending a silent alarm to a monitoring centre. Modern time delay combination locks can have many functions such as multiple diffe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key (lock)
A lock is a mechanical or electronic fastening device that is released by a physical object (such as a key, keycard, fingerprint, RFID card, security token or coin), by supplying secret information (such as a number or letter permutation or password), by a combination thereof, or it may only be able to be opened from one side, such as a door chain. A key is a device that is used to operate a lock (to lock or unlock it). A typical key is a small piece of metal consisting of two parts: the ''bit'' or ''blade'', which slides into the keyway of the lock and distinguishes between different keys, and the ''bow'', which is left protruding so that torque can be applied by the user. In its simplest implementation, a key operates one lock or set of locks that are keyed alike, a lock/key system where each similarly keyed lock requires the same, unique key. The key serves as a security token for access to the locked area; locks are meant to only allow persons having the correct key ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Jeremiah Chubb
A Chubb detector lock is a lever tumbler lock with an integral security feature, a re-locking device, which frustrates unauthorised access attempts and indicates to the lock's owner that it has been interfered with. When someone tries to pick the lock or to open it using the wrong key, the lock is designed to jam in a locked state until (depending on the lock) either a special regulator key or the original key is inserted and turned in a different direction. This alerts the owner to the fact that the lock has been tampered with. Any person who attempts to pick a detector lock must avoid triggering the automatic jamming mechanism. If the automatic jamming mechanism is accidentally triggered (which happens when any one of the levers is lifted too high) the lock-picker has the additional problem of resetting the detector mechanism before the next attempt to open the lock. This introduces additional complexity into the task, increasing the degree of lock-picking skill required to a le ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lock (security Device)
A lock is a mechanical or electronic fastening device that is released by a physical object (such as a key, keycard, fingerprint, RFID card, security token or coin), by supplying secret information (such as a number or letter permutation or password), by a combination thereof, or it may only be able to be opened from one side, such as a door chain. A key is a device that is used to operate a lock (to lock or unlock it). A typical key is a small piece of metal consisting of two parts: the ''bit'' or ''blade'', which slides into the keyway of the lock and distinguishes between different keys, and the ''bow'', which is left protruding so that torque can be applied by the user. In its simplest implementation, a key operates one lock or set of locks that are keyed alike, a lock/key system where each similarly keyed lock requires the same, unique key. The key serves as a security token for access to the locked area; locks are meant to only allow persons having the correct key ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Casting (metalworking)
In metalworking and jewelry making, casting is a process in which a liquid metal is delivered into a mold (usually by a crucible) that contains a negative impression (i.e., a three-dimensional negative image) of the intended shape. The metal is poured into the mold through a hollow channel called a sprue. The metal and mold are then cooled, and the metal part (the ''casting'') is extracted. Casting is most often used for making complex shapes that would be difficult or uneconomical to make by other methods. Casting processes have been known for thousands of years, and have been widely used for sculpture (especially in bronze), jewelry in precious metals, and weapons and tools. Highly engineered castings are found in 90 percent of durable goods, including cars, trucks, aerospace, trains, mining and construction equipment, oil wells, appliances, pipes, hydrants, wind turbines, nuclear plants, medical devices, defense products, toys, and more. Traditional techniques include ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Henry Brown (inventor)
Henry Brown was an American inventor, perhaps best known as the inventor of a type of paper storage box. Henry Brown developed a type of compartmented storage box intended to keep sheets of carbon paper separate from each other, and patented his invention (number 352,036) on November 2, 1886. References External links * 19th-century American inventors 19th-century births Year of birth unknown Year of death unknown African-American inventors {{US-inventor-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Through Obscurity
Security through obscurity (or security by obscurity) is the reliance in security engineering on design or implementation secrecy as the main method of providing security to a system or component. History An early opponent of security through obscurity was the locksmith Alfred Charles Hobbs, who in 1851 demonstrated to the public how state-of-the-art locks could be picked. In response to concerns that exposing security flaws in the design of locks could make them more vulnerable to criminals, he said: "Rogues are very keen in their profession, and know already much more than we can teach them." There is scant formal literature on the issue of security through obscurity. Books on security engineering cite Kerckhoffs' doctrine from 1883, if they cite anything at all. For example, in a discussion about secrecy and openness in Nuclear Command and Control: e benefits of reducing the likelihood of an accidental war were considered to outweigh the possible benefits of secrecy. This ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Heist Film
The heist film or caper film is a subgenre of crime film focused on the planning, execution, and aftermath of a significant robbery. One of the early defining heist films was '' The Asphalt Jungle'' (1950), which ''Film Genre 2000'' wrote "almost single-handedly popularized the genre for mainstream cinema". It featured robbers whose personal failings ultimately led to the failure of their robbery. Similar films using this formula were '' Armored Car Robbery'' (1950), '' The Killing'' (1956), and '' The Getaway'' (1972). By the 1990s, heist films began to "experiment and play with these conventions," incorporating things like comedy into heist stories. Characteristics of the genre While there is sometimes some confusion as to what counts as a heist film, there are characteristics that most films in the genre follow. The most basic of these is that films in the genre tend to follow the planning, execution and aftermath of one large robbery. While there can be smaller crimes lea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |



.jpg)

