|
SILC (protocol)
SILC (Secure Internet Live Conferencing protocol) is a protocol that provides secure synchronous conferencing services (very much like IRC) over the Internet. Components The SILC protocol can be divided in three main parts: SILC Key Exchange (SKE) protocol, SILC Authentication protocol and SILC Packet protocol. SILC protocol additionally defines SILC Commands that are used to manage the SILC session. SILC provides channels (groups), nicknames, private messages, and other common features. However, SILC nicknames, in contrast to many other protocols (''e.g.'' IRC), are not unique; a user is able to use any nickname, even if one is already in use. The real identification in the protocol is performed by unique Client ID. The SILC protocol uses this to overcome nickname collision, a problem present in many other protocols. All messages sent in a SILC network are binary, allowing them to contain any type of data, including text, video, audio, and other multimedia data. The SKE prot ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Internet Live Conferencing Logo
Secure may refer to: * Security, being protected against danger or loss(es) **Physical security, security measures that are designed to deny unauthorized access to facilities, equipment, and resources **Information security, defending information from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction **Secure communication, when two entities are communicating and do not want a third party to listen in * Securitate (Romanian for "security"), the secret service of Communist Romania * Security (finance), e.g. secured loans **Secured transaction, a loan or a credit transaction in which the lender acquires a security interest in collateral owned by the borrower **Secured creditor, a creditor with the benefit of a security interest over some or all of the assets of the debtor * ''Secure'' (G5), a NatureServe conservation status similar to "Least Concern", indicating a species is not at risk of extinction * Sécure River The Séc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Server (computing)
In computing, a server is a piece of computer hardware or software (computer program) that provides functionality for other programs or devices, called " clients". This architecture is called the client–server model. Servers can provide various functionalities, often called "services", such as sharing data or resources among multiple clients, or performing computation for a client. A single server can serve multiple clients, and a single client can use multiple servers. A client process may run on the same device or may connect over a network to a server on a different device. Typical servers are database servers, file servers, mail servers, print servers, web servers, game servers, and application servers. Client–server systems are usually most frequently implemented by (and often identified with) the request–response model: a client sends a request to the server, which performs some action and sends a response back to the client, typically with a result or acknowledg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Protocols
The Internet protocol suite, commonly known as TCP/IP, is a framework for organizing the set of communication protocols used in the Internet and similar computer networks according to functional criteria. The foundational protocols in the suite are the Transmission Control Protocol (TCP), the User Datagram Protocol (UDP), and the Internet Protocol (IP). In the development of this networking model, early versions of it were known as the Department of Defense (DoD) model because the research and development were funded by the United States Department of Defense through DARPA. The Internet protocol suite provides end-to-end data communication specifying how data should be packetized, addressed, transmitted, routed, and received. This functionality is organized into four abstraction layers, which classify all related protocols according to each protocol's scope of networking. An implementation of the layers for a particular application forms a protocol stack. From lowest to high ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public-key Cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. In a public-key encryption system, anyone with a public key can encrypt a message, yielding a ciphertext, but only those who know the corresponding private key can decrypt the ciphertext to obtain the original message. For example, a journalist can publish the public key of an encryption key pair on a web site so that sources can send secret messages to the news organization in ciphertext. Only the journalist who knows the corresponding private key can decrypt the ciphertexts to obtain the sources' messages—an eavesdropp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multiprotocol Instant Messaging Application
Instant messaging (IM) technology is a type of online chat allowing real-time text transmission over the Internet or another computer network. Messages are typically transmitted between two or more parties, when each user inputs text and triggers a transmission to the recipient(s), who are all connected on a common network. It differs from email in that conversations over instant messaging happen in real-time (hence "instant"). Most modern IM applications (sometimes called "social messengers", "messaging apps" or "chat apps") use push technology and also add other features such as emojis (or graphical smileys), file transfer, chatbots, voice over IP, or video chat capabilities. Instant messaging systems tend to facilitate connections between specified known users (often using a contact list also known as a "buddy list" or "friend list"), and can be standalone applications or integrated into e.g. a wider social media platform, or a website where it can for instance be used for co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Comparison Of Instant Messaging Protocols ...
The following is a comparison of instant messaging protocols. It contains basic general information about the protocols. Table of instant messaging protocols See also *Comparison of cross-platform instant messaging clients *Comparison of Internet Relay Chat clients *Comparison of LAN messengers *LAN messenger *Secure instant messaging * Comparison of user features of messaging platforms References {{DEFAULTSORT:Comparison Of Instant Messaging Protocols Instant messaging protocols Instant messaging Instant messaging protocols Instant messaging protocols In physics and the philosophy of science, instant refers to an infinitesimal interval in time, whose passage is instantaneous. In ordinary speech, an instant has been defined as "a point or very short space of time," a notion deriving from its ety ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Synchronous Conferencing
Synchronous conferencing is the formal term used in computing, in particular in computer-mediated communication, collaboration and learning, to describe technologies informally known as online chat. It is sometimes extended to include audio/video conferencing or instant messaging systems that provide a text-based multi-user chat function. The word ''synchronous'' is used to qualify the conferencing as real-time, as distinct from a system such as e-mail, where messages are left and answered later. Synchronous conferencing protocols include: * IRC (Internet Relay Chat) * PSYC (Protocol for Synchronous Conferencing) * SILC (Secure Internet Live Conferencing protocol) * XMPP (Extensible Messaging and Presence Protocol) * SIMPLE (instant messaging protocol) (Session Initiation Protocol for Instant Messaging and Presence Leveraging Extensions) Types According to the type of media used, synchronous conferencing can be divided into * audio conferencing: only audio is used * video ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Asymmetric Encryption
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic algorithms based on mathematical problems termed one-way functions. Security of public-key cryptography depends on keeping the private key secret; the public key can be openly distributed without compromising security. In a public-key encryption system, anyone with a public key can encrypt a message, yielding a ciphertext, but only those who know the corresponding private key can decrypt the ciphertext to obtain the original message. For example, a journalist can publish the public key of an encryption key pair on a web site so that sources can send secret messages to the news organization in ciphertext. Only the journalist who knows the corresponding private key can decrypt the ciphertexts to obtain the sources' messages—an eavesdropp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Man-in-the-middle Attack
In cryptography and computer security, a man-in-the-middle, monster-in-the-middle, machine-in-the-middle, monkey-in-the-middle, meddler-in-the-middle, manipulator-in-the-middle (MITM), person-in-the-middle (PITM) or adversary-in-the-middle (AiTM) attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, as the attacker has inserted themselves between the two parties. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Symmetric Encryption
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical, or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. The requirement that both parties have access to the secret key is one of the main drawbacks of symmetric-key encryption, in comparison to public-key encryption (also known as asymmetric-key encryption). However, symmetric-key encryption algorithms are usually better for bulk encryption. They have a smaller key size, which means less storage space and faster transmission. Due to this, asymmetric-key encryption is often used to exchange the secret key for symmetric-key encryption. Types Symmetric-key encryption can use either stream ciphers or block ciphers. * Stream ciphers encrypt the digits ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
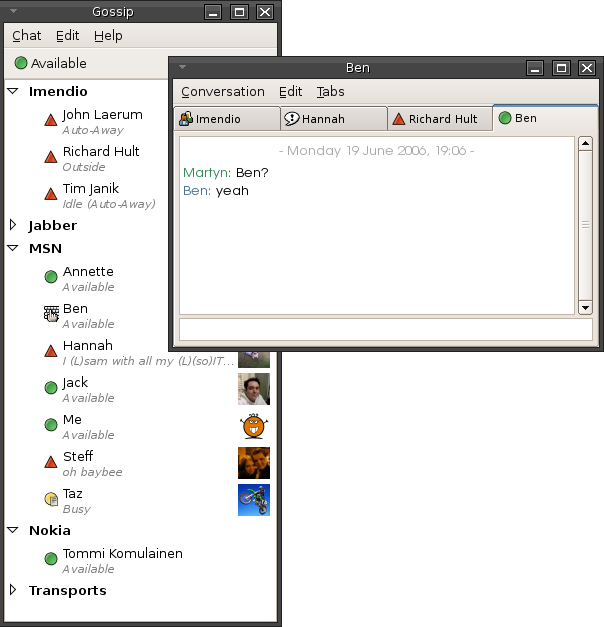
Colloquy (IRC Client)
Colloquy is an open-source IRC, SILC, ICB and XMPP client for Mac OS X. Colloquy uses its own core, known as Chat Core, although in the past it used Irssi as its IRC protocol engine. One of the primary goals behind Colloquy was to create an IRC, SILC and ICB client with Mac OS X visuals. Colloquy contains a user interface that follows Apple's Human interface guidelines in addition to containing support for traditional IRC command-line controls such as /nick and /join. An official app for iOS was released and features support for all IRC commands, a built-in browser, push notifications and other features. Features Colloquy supports a variety of different text modifications. One text manipulation supported by Colloquy is the use of colors as used by mIRC; with the primary colors being: White, Black, Navy, Forest, Red, Maroon, Purple, Orange, Yellow, Green, Teal, Cyan, Blue, Magenta, Grey, and Ash. Additionally, Colloquy supports formatting text with underlining, italics, bold, a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Silky (software)
A Silkie is a breed of domestic chicken. Silkie or Silky also may refer to: * Silkie, guinea pig of one specific variety * Silkie, a fictional character in ''Teen Titans'' animation series on television * Silkie, a mythical species, a.k.a. Selkie, that passes for both seal and human *Silkies, a type of house-dwelling spirits clothed in silk * Silkies, a superhuman race in ''The Silkie'', a science fiction novel by A. E. van Vogt * Silky, a character from the anime series ''I'm Gonna Be An Angel!'' (Tenshi ni Narumon) * Silky Nutmeg Ganache, American drag queen * The Silkie, English folk group * Silkie, English dubstep producer * "Silkie", a song from the album ''Joan Baez, Vol. 2'' * ''The Silkie'' (novel), a 1969 novel by A. E. Van Vogt See also * Australian Silky Terrier The Australian Silky Terrier or simply Silky Terrier (depending on the breed registry) is a small breed of dog of the terrier dog type. The breed was developed in Australia, although the ancestral types and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |