|
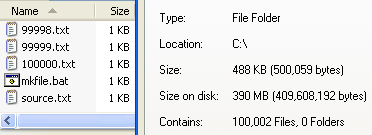
Rubberhose Filesystem
In computing, rubberhose (also known by its development codename Marutukku) is a deniable encryption archive containing multiple file systems whose existence can only be verified using the appropriate cryptographic key. Name and history The project was originally named Rubberhose, as it was designed to be resistant to attacks by people willing to use torture on those who knew the encryption keys. This is a reference to the rubber-hose cryptanalysis euphemism. It was written in 1997–2000 by Julian Assange, Suelette Dreyfus, and Ralf Weinmann. Technical The following paragraphs are extracts from the project's documentation: Status Rubberhose is not actively maintained, although it is available for Linux kernel 2.2, NetBSD and FreeBSD. The latest version available, still in alpha stage, is v0.8.3. See also *Rubber-hose cryptanalysis *Key disclosure law *StegFS StegFS is a free steganographic file system for Linux based on the ext2 filesystem. It is licensed under the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deniable Encryption
In cryptography and steganography, plausibly deniable encryption describes encryption techniques where the existence of an encrypted file or message is deniable in the sense that an adversary cannot prove that the plaintext data exists. The users may convincingly deny that a given piece of data is encrypted, or that they are able to decrypt a given piece of encrypted data, or that some specific encrypted data exists. Such denials may or may not be genuine. For example, it may be impossible to prove that the data is encrypted without the cooperation of the users. If the data is encrypted, the users genuinely may not be able to decrypt it. Deniable encryption serves to undermine an attacker's confidence either that data is encrypted, or that the person in possession of it can decrypt it and provide the associated plaintext. Function Deniable encryption makes it impossible to prove the existence of the plaintext message without the proper decryption key. This may be done by allowing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File System
In computing, file system or filesystem (often abbreviated to fs) is a method and data structure that the operating system uses to control how data is stored and retrieved. Without a file system, data placed in a storage medium would be one large body of data with no way to tell where one piece of data stopped and the next began, or where any piece of data was located when it was time to retrieve it. By separating the data into pieces and giving each piece a name, the data are easily isolated and identified. Taking its name from the way a paper-based data management system is named, each group of data is called a "file". The structure and logic rules used to manage the groups of data and their names is called a "file system." There are many kinds of file systems, each with unique structure and logic, properties of speed, flexibility, security, size and more. Some file systems have been designed to be used for specific applications. For example, the ISO 9660 file system is designe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Torture
Torture is the deliberate infliction of severe pain or suffering on a person for reasons such as punishment, extracting a confession, interrogation for information, or intimidating third parties. Some definitions are restricted to acts carried out by the state, but others include non-state organizations. Torture has been carried out since ancient times. In the eighteenth and nineteenth centuries, Western countries abolished the official use of torture in the judicial system, but torture continued to be used throughout the world. A variety of methods of torture are used, often in combination; the most common form of physical torture is beatings. Since the twentieth century, many torturers have preferred non-scarring or psychological methods to provide deniability. Torturers are enabled by organizations that facilitate and encourage their behavior. Most victims of torture are poor and marginalized people suspected of crimes, although torture against political prisoners or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rubber-hose Cryptanalysis
In cryptography, rubber-hose cryptanalysis is a euphemism for the extraction of cryptographic secrets (e.g. the password to an encrypted file) from a person by coercion or torture—such as beating that person with a rubber hose, hence the name—in contrast to a mathematical or technical cryptanalytic attack. Details According to Amnesty International and the UN, many countries in the world routinely torture people. It is therefore logical to assume that at least some of those countries use (or would be willing to use) some form of rubber-hose cryptanalysis. In practice, psychological coercion can prove as effective as physical torture. Not physically violent but highly intimidating methods include such tactics as the threat of harsh legal penalties. The incentive to cooperate may be some form of plea bargain, such as an offer to drop or reduce criminal charges against a suspect in return for full co-operation with investigators. Alternatively, in some countries threats ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Julian Assange
Julian Paul Assange ( ; Hawkins; born 3 July 1971) is an Australian editor, publisher, and activist who founded WikiLeaks in 2006. WikiLeaks came to international attention in 2010 when it published a series of leaks provided by U.S. Army intelligence analyst Chelsea Manning. These leaks included the Baghdad airstrike ''Collateral Murder'' video (April 2010),, 5 April 2000. Retrieved 28 March 2014. the Afghanistan war logs (July 2010), the Iraq war logs (October 2010), and Cablegate (November 2010). After the 2010 leaks, the United States government launched a criminal investigation into WikiLeaks. In November 2010, Sweden issued a European arrest warrant for Assange over allegations of sexual misconduct. Assange said the allegations were a pretext for his extradition from Sweden to the United States over his role in the publication of secret American documents. After losing his battle against extradition to Sweden, he breached bail and took refuge in the Embassy of Ecua ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Suelette Dreyfus
Suelette Dreyfus is a technology researcher, journalist, and writer. Her fields of research include information systems, digital security and privacy, the impact of technology on whistleblowing, health informatics and e-education. Her work examines digital whistleblowing as a form of freedom of expression and the right of dissent from corruption. She is a researcher and lecturer in the Department of Computing and Information Systems at the University of Melbourne, as well as the principal researcher on an international research project on the impact of digital technologies on whistleblowing. Career Dreyfus' work in e-health has focused on the patient information experience in the health system and the role of technology in error incident reporting in hospital settings. She has co-invented prototypes in information design for pathology reports with the aim of allowing doctors to improve communication with patients and families regarding the status of their diseases in progressive ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux Kernel
The Linux kernel is a free and open-source, monolithic, modular, multitasking, Unix-like operating system kernel. It was originally authored in 1991 by Linus Torvalds for his i386-based PC, and it was soon adopted as the kernel for the GNU operating system, which was written to be a free (libre) replacement for Unix. Linux is provided under the GNU General Public License version 2 only, but it contains files under other compatible licenses. Since the late 1990s, it has been included as part of a large number of operating system distributions, many of which are commonly also called Linux. Linux is deployed on a wide variety of computing systems, such as embedded devices, mobile devices (including its use in the Android operating system), personal computers, servers, mainframes, and supercomputers. It can be tailored for specific architectures and for several usage scenarios using a family of simple commands (that is, without the need of manually editing its source code ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NetBSD
NetBSD is a free and open-source Unix operating system based on the Berkeley Software Distribution (BSD). It was the first open-source BSD descendant officially released after 386BSD was forked. It continues to be actively developed and is available for many platforms, including servers, desktops, handheld devices, and embedded systems. The NetBSD project focuses on code clarity, careful design, and portability across many computer architectures. Its source code is publicly available and permissively licensed. History NetBSD was originally derived from the 4.3BSD-Reno release of the Berkeley Software Distribution from the Computer Systems Research Group of the University of California, Berkeley, via their Net/2 source code release and the 386BSD project. The NetBSD project began as a result of frustration within the 386BSD developer community with the pace and direction of the operating system's development. The four founders of the NetBSD project, Chris Demetriou, Theo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FreeBSD
FreeBSD is a free and open-source Unix-like operating system descended from the Berkeley Software Distribution (BSD), which was based on Research Unix. The first version of FreeBSD was released in 1993. In 2005, FreeBSD was the most popular open-source BSD operating system, accounting for more than three-quarters of all installed and permissively licensed BSD systems. FreeBSD has similarities with Linux, with two major differences in scope and licensing: FreeBSD maintains a complete system, i.e. the project delivers a kernel, device drivers, userland utilities, and documentation, as opposed to Linux only delivering a kernel and drivers, and relying on third-parties for system software; FreeBSD source code is generally released under a permissive BSD license, as opposed to the copyleft GPL used by Linux. The FreeBSD project includes a security team overseeing all software shipped in the base distribution. A wide range of additional third-party applications may be installe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rubber-hose Cryptanalysis
In cryptography, rubber-hose cryptanalysis is a euphemism for the extraction of cryptographic secrets (e.g. the password to an encrypted file) from a person by coercion or torture—such as beating that person with a rubber hose, hence the name—in contrast to a mathematical or technical cryptanalytic attack. Details According to Amnesty International and the UN, many countries in the world routinely torture people. It is therefore logical to assume that at least some of those countries use (or would be willing to use) some form of rubber-hose cryptanalysis. In practice, psychological coercion can prove as effective as physical torture. Not physically violent but highly intimidating methods include such tactics as the threat of harsh legal penalties. The incentive to cooperate may be some form of plea bargain, such as an offer to drop or reduce criminal charges against a suspect in return for full co-operation with investigators. Alternatively, in some countries threats ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Disclosure Law
Key disclosure laws, also known as mandatory key disclosure, is legislation that requires individuals to surrender cryptographic keys to law enforcement. The purpose is to allow access to material for confiscation or digital forensics purposes and use it either as evidence in a court of law or to enforce national security interests. Similarly, mandatory decryption laws force owners of encrypted data to supply decrypted data to law enforcement. Nations vary widely in the specifics of how they implement key disclosure laws. Some, such as Australia, give law enforcement wide-ranging power to compel assistance in decrypting data from any party. Some, such as Belgium, concerned with self-incrimination, only allow law enforcement to compel assistance from non-suspects. Some require only specific third parties such as telecommunications carriers, certification providers, or maintainers of encryption services to provide assistance with decryption. In all cases, a warrant is generally req ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
StegFS
StegFS is a free steganographic file system for Linux based on the ext2 filesystem. It is licensed under the GPL. It was principally developed by Andrew D. McDonald and Markus G. Kuhn. The last version of StegFS is 1.1.4, released February 14, 2001. This is a development release, with known bugs, such as a file corruption bug. There is no stable release. The last website activity was in 2004. In 2003, Andreas C. Petter and Sebastian Urbach intended to continue development of StegFS, and created a site for it on SourceForge.net. The development has further moved to using FUSE library, and working releases are available from the development homepage. See also * Filesystem-level encryption * List of cryptographic file systems Further reading * * External linksStegFSoriginal home pageStegFSdevelopment home pageStegFSresearch paper -(PDF Portable Document Format (PDF), standardized as ISO 32000, is a file format developed by Adobe in 1992 to present documents, including text ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |