|
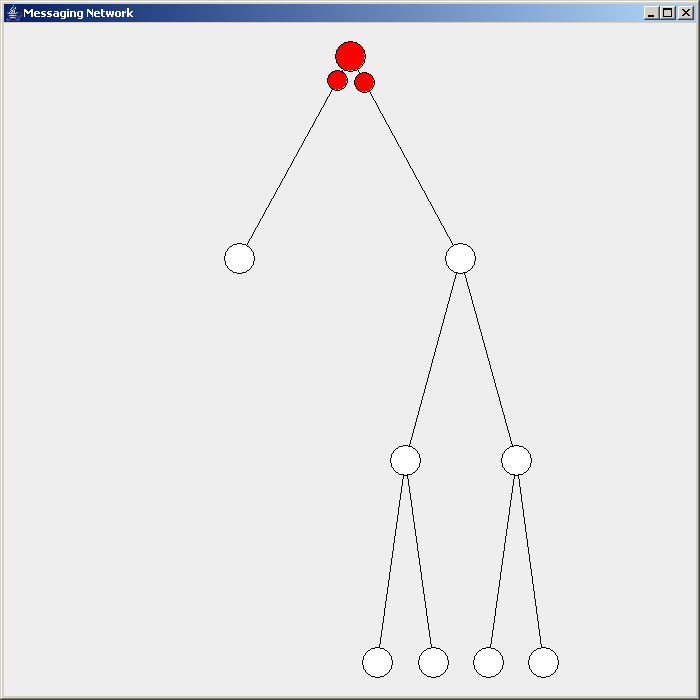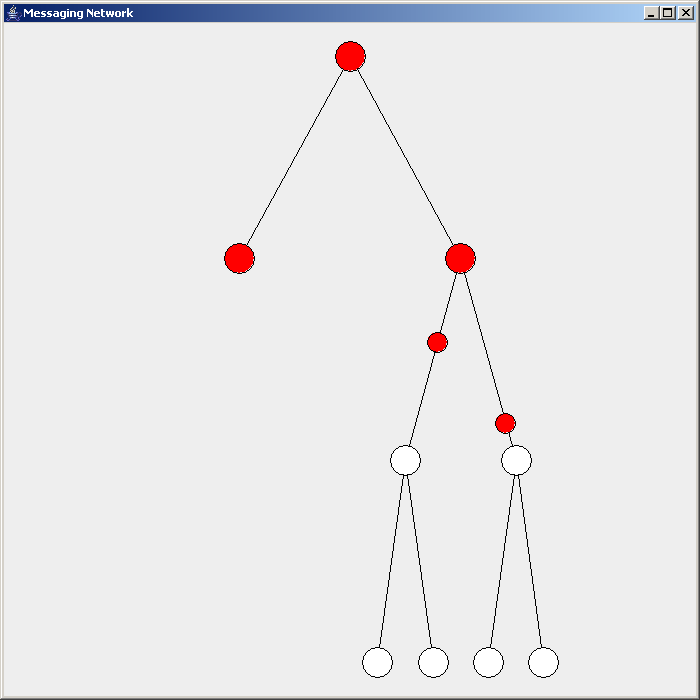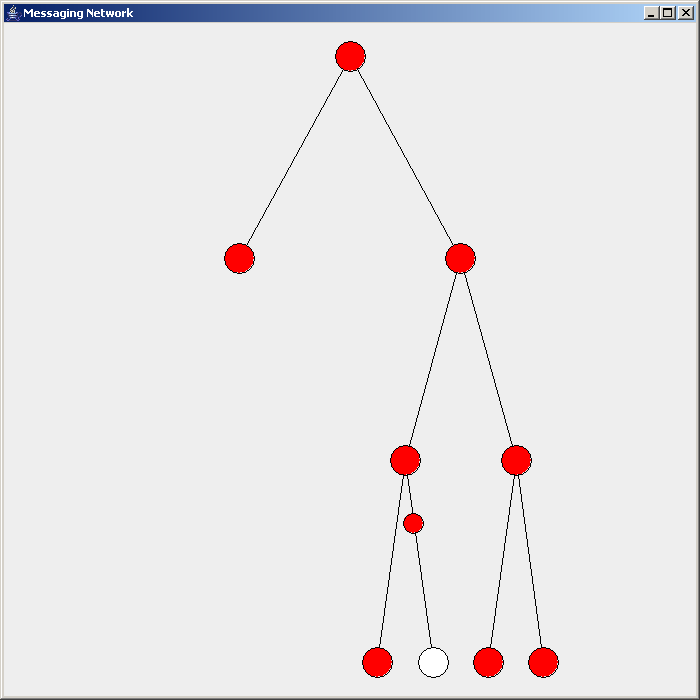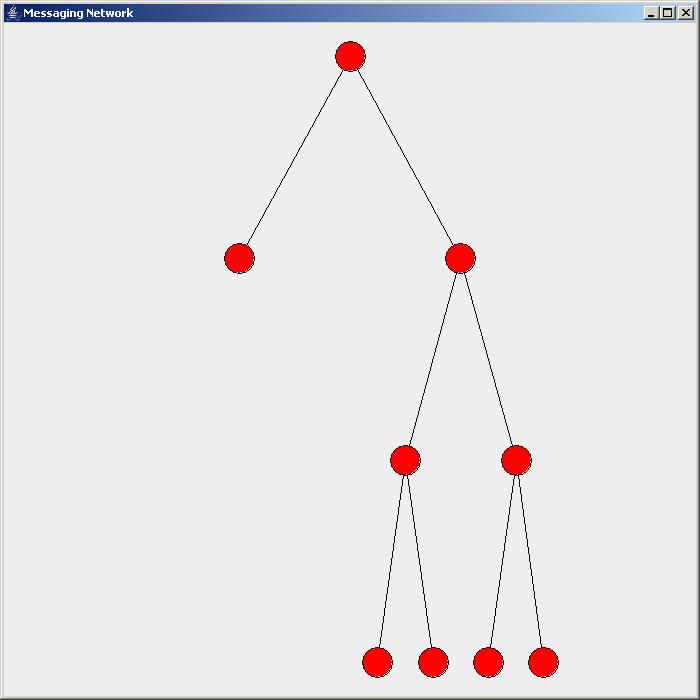
Routing In Delay-tolerant Networking
Routing in delay-tolerant networking concerns itself with the ability to transport, or route, data from a source to a destination, which is a fundamental ability all communication networks must have. Delay- and disruption-tolerant networks (DTNs) are characterized by their lack of connectivity, resulting in a lack of instantaneous end-to-end paths. In these challenging environments, popular ad hoc routing protocols such as AODV and DSR fail to establish routes. This is due to these protocols trying to first establish a complete route and then, after the route has been established, forward the actual data. However, when instantaneous end-to-end paths are difficult or impossible to establish, routing protocols must take to a "store and forward" approach, where data is incrementally moved and stored throughout the network in hopes that it will eventually reach its destination.John Burgess, Brian Gallagher, David Jensen, and Brian Neil Levine. MaxProp: Routing for vehicle-based di ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
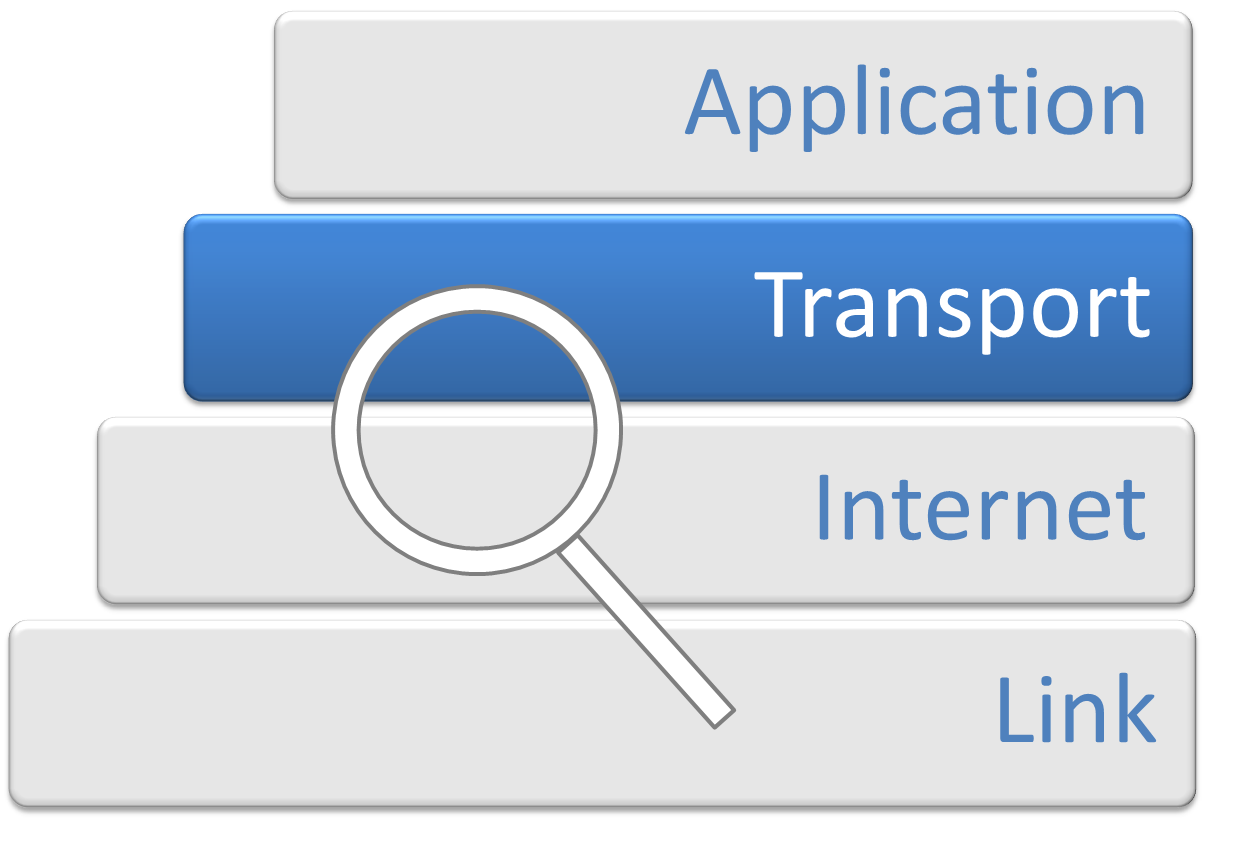
Transport Layer
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-end communication services for applications. It provides services such as connection-oriented communication, reliability, flow control, and multiplexing. The details of implementation and semantics of the transport layer of the Internet protocol suite, which is the foundation of the Internet, and the OSI model of general networking are different. The protocols in use today in this layer for the Internet all originated in the development of TCP/IP. In the OSI model the transport layer is often referred to as Layer 4, or L4, while numbered layers are not used in TCP/IP. The best-known transport protocol of the Internet protocol suite is the Transmission Control Protocol (TCP). It is used for connection-oriented transmissions, whereas the con ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Online Algorithms
In computer technology and telecommunications, online indicates a state of connectivity, and offline indicates a disconnected state. In modern terminology, this usually refers to an Internet connection, but (especially when expressed as "on line" or "on the line") could refer to any piece of equipment or functional unit that is connected to a larger system. Being online means that the equipment or subsystem is connected, or that it is ready for use. "Online" has come to describe activities and concepts that take place on the Internet, such as online identity, online predator and online shop. A similar meaning is also given by the prefixes cyber and e, as in words ''cyberspace'', ''cybercrime'', ''email'', and '' e-commerce''. In contrast, "offline" can refer to either computing activities performed while disconnected from the Internet, or alternatives to Internet activities (such as shopping in brick-and-mortar stores). The term "offline" is sometimes used interchangeably ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Head Start (positioning)
A head start is a start in advance of the starting position of others in the competition, or simply toward the finish line or desired outcome. Depending on the situation, a head start may be inherent, obtained by special privilege, earned through one's accomplishments, or granted mercifully by an opponent. While not guaranteeing success, a head start will increase such chances. In sports In competitive sports, such as a racing, race, a head start refers to a start ahead of other competitors, allowing a shorter distance to the wikt:finish line, finish line. The idea of a head start may seem unfair. But in some cases, a head start is an advantage that may be earned by one more of the competitors. Also, adults who are racing against children may provide children with a head start, knowing the children are slower, and wanting to allow them a chance to win. In multiple-event or multiple-day competitions, such as the modern pentathlon, the final event may use a head start where the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Cryptographic Hash Function
A cryptographic hash function (CHF) is a hash algorithm (a map (mathematics), map of an arbitrary binary string to a binary string with a fixed size of n bits) that has special properties desirable for a cryptography, cryptographic application: * the probability of a particular n-bit output result (hash value) for a random input string ("message") is 2^ (as for any good hash), so the hash value can be used as a representative of the message; * finding an input string that matches a given hash value (a ''pre-image'') is infeasible, ''assuming all input strings are equally likely.'' The ''resistance'' to such search is quantified as security strength: a cryptographic hash with n bits of hash value is expected to have a ''preimage resistance'' strength of n bits, unless the space of possible input values is significantly smaller than 2^ (a practical example can be found in ); * a ''second preimage'' resistance strength, with the same expectations, refers to a similar problem of f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Acknowledgement (data Networks)
In data networking, telecommunications, and computer buses, an acknowledgement (ACK) is a signal that is passed between communicating processes, computers, or devices to signify acknowledgment, or receipt of message, as part of a communications protocol. Correspondingly a negative-acknowledgement (NAK or NACK) is a signal that is sent to reject a previously received message or to indicate some kind of error. Acknowledgments and negative acknowledgments inform a sender of the receiver's state so that it can adjust its own state accordingly. Acknowledgment signal types The ASCII code point for ACK is 0x06 (binary 0000 0110). By convention a receiving device sends an ACK to indicate it successfully received a message. ASCII also provides a NAK code point (0x15, binary 0001 0101) which can be used to indicate the receiving device cannot, or will not, comply with the message. Unicode provides visible symbols for these ASCII characters, U+2406 (␆) and U+2415 (␕). ACK and NAK s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Normalizing Constant
In probability theory, a normalizing constant or normalizing factor is used to reduce any probability function to a probability density function with total probability of one. For example, a Gaussian function can be normalized into a probability density function, which gives the standard normal distribution. In Bayes' theorem, a normalizing constant is used to ensure that the sum of all possible hypotheses equals 1. Other uses of normalizing constants include making the value of a Legendre polynomial at 1 and in the orthogonality of orthonormal functions. A similar concept has been used in areas other than probability, such as for polynomials. Definition In probability theory, a normalizing constant is a constant by which an everywhere non-negative function must be multiplied so the area under its graph is 1, e.g., to make it a probability density function or a probability mass function. Examples If we start from the simple Gaussian function p(x) = e^, \quad x\in(-\infty,\ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Queue (abstract Data Type)
In computer science, a queue is a collection of entities that are maintained in a sequence and can be modified by the addition of entities at one end of the sequence and the removal of entities from the other end of the sequence. By convention, the end of the sequence at which elements are added is called the back, tail, or rear of the queue, and the end at which elements are removed is called the head or front of the queue, analogously to the words used when people line up to wait for goods or services. The operation of adding an element to the rear of the queue is known as ''enqueue'', and the operation of removing an element from the front is known as ''dequeue''. Other operations may also be allowed, often including a '' peek'' or ''front'' operation that returns the value of the next element to be dequeued without dequeuing it. The operations of a queue make it a first-in-first-out (FIFO) data structure. In a FIFO data structure, the first element added to the queue will ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Flooding (computer Networking)
Flooding is used in computer network Routing, routing algorithms in which every incoming packet (information technology), packet is sent through every outgoing link except the one it arrived on. Flooding is used in Bridging (networking), bridging and in systems such as Usenet and peer-to-peer file sharing and as part of some routing protocols, including Open Shortest Path First, OSPF, Distance Vector Multicast Routing Protocol, DVMRP, and those used in ad-hoc wireless networks (WANETs). Types There are generally two types of flooding available, uncontrolled flooding and controlled flooding. In ''uncontrolled flooding'' each node unconditionally distributes packets to each of its neighbors. Without conditional logic to prevent indefinite recirculation of the same packet, broadcast storms are a hazard. ''Controlled flooding'' has its own two algorithms to make it reliable, SNCF (Sequence Number Controlled Flooding) and RPF (reverse-path forwarding). In SNCF, the node attache ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
IEEE
The Institute of Electrical and Electronics Engineers (IEEE) is an American 501(c)(3) organization, 501(c)(3) public charity professional organization for electrical engineering, electronics engineering, and other related disciplines. The IEEE has a corporate office in New York City and an operations center in Piscataway, New Jersey. The IEEE was formed in 1963 as an amalgamation of the American Institute of Electrical Engineers and the Institute of Radio Engineers. History The IEEE traces its founding to 1884 and the American Institute of Electrical Engineers. In 1912, the rival Institute of Radio Engineers was formed. Although the AIEE was initially larger, the IRE attracted more students and was larger by the mid-1950s. The AIEE and IRE merged in 1963. The IEEE is headquartered in New York City, but most business is done at the IEEE Operations Center in Piscataway, New Jersey, opened in 1975. The Australian Section of the IEEE existed between 1972 and 1985, after which it s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
National Science Foundation
The U.S. National Science Foundation (NSF) is an Independent agencies of the United States government#Examples of independent agencies, independent agency of the Federal government of the United States, United States federal government that supports fundamental research and education in all the non-medical fields of science and engineering. Its medical counterpart is the National Institutes of Health. With an annual budget of about $9.9 billion (fiscal year 2023), the NSF funds approximately 25% of all federally supported basic research conducted by the List of American institutions of higher education, United States' colleges and universities. In some fields, such as mathematics, computer science, economics, and the social sciences, the NSF is the major source of federal backing. NSF's director and deputy director are appointed by the president of the United States and Advice and consent, confirmed by the United States Senate, whereas the 24 president-appointed members of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
DARPA
The Defense Advanced Research Projects Agency (DARPA) is a research and development agency of the United States Department of Defense responsible for the development of emerging technologies for use by the military. Originally known as the Advanced Research Projects Agency (ARPA), the agency was created on February 7, 1958, by President Dwight D. Eisenhower in response to the Soviet Union, Soviet launching of Sputnik 1 in 1957. By collaborating with academia, industry, and government partners, DARPA formulates and executes research and development projects to expand the frontiers of technology and science, often beyond immediate U.S. military requirements.Dwight D. Eisenhower and Science & Technology, (2008). Dwight D. Eisenhower Memorial CommissionSource The name of the organization first changed from its founding name, ARPA, to DARPA, in March 1972, changing back to ARPA in February 1993, then reverted to DARPA in March 1996. ''The Economist'' has called DARPA "the agency that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
University Of Massachusetts Amherst
The University of Massachusetts Amherst (UMass Amherst) is a public land-grant research university in Amherst, Massachusetts, United States. It is the flagship campus of the University of Massachusetts system and was founded in 1863 as the Massachusetts Agricultural College. It is also a member of the Five College Consortium, along with four other colleges in the Pioneer Valley. UMass Amherst has the largest undergraduate population in Massachusetts with roughly 24,000 enrolled undergraduates. The university offers academic degrees in 109 undergraduate, 77 master's, and 48 doctoral programs in nine schools and colleges. It is classified among "R1: Doctoral Universities – Very high research activity". According to the National Science Foundation, the university spent $211 million on research and development in 2018. The university's 21 varsity athletic teams compete in NCAA Division I and are collectively known as the Minutemen and Minutewomen. The university is a memb ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |