|
Rooted Graph
In mathematics, and, in particular, in graph theory, a rooted graph is a graph in which one vertex has been distinguished as the root. Both directed and undirected versions of rooted graphs have been studied, and there are also variant definitions that allow multiple roots. Rooted graphs may also be known (depending on their application) as pointed graphs or flow graphs. In some of the applications of these graphs, there is an additional requirement that the whole graph be reachable from the root vertex. Variations In topological graph theory, the notion of a rooted graph may be extended to consider multiple vertices or multiple edges as roots. The former are sometimes called vertex-rooted graphs in order to distinguish them from edge-rooted graphs in this context. Graphs with multiple nodes designated as roots are also of some interest in combinatorics, in the area of random graphs. These graphs are also called multiply rooted graphs. The terms rooted directed graph or rooted d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mathematics
Mathematics is an area of knowledge that includes the topics of numbers, formulas and related structures, shapes and the spaces in which they are contained, and quantities and their changes. These topics are represented in modern mathematics with the major subdisciplines of number theory, algebra, geometry, and analysis, respectively. There is no general consensus among mathematicians about a common definition for their academic discipline. Most mathematical activity involves the discovery of properties of abstract objects and the use of pure reason to prove them. These objects consist of either abstractions from nature orin modern mathematicsentities that are stipulated to have certain properties, called axioms. A ''proof'' consists of a succession of applications of deductive rules to already established results. These results include previously proved theorems, axioms, andin case of abstraction from naturesome basic properties that are considered true starting points of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Abstraction
Abstraction in its main sense is a conceptual process wherein general rules and concepts are derived from the usage and classification of specific examples, literal ("real" or "concrete") signifiers, first principles, or other methods. "An abstraction" is the outcome of this process—a concept that acts as a common noun for all subordinate concepts and connects any related concepts as a ''group'', ''field'', or ''category''. Suzanne K. Langer (1953), ''Feeling and Form: a theory of art developed from Philosophy in a New Key'' p. 90: " Sculptural form is a powerful abstraction from actual objects and the three-dimensional space which we construe ... through touch and sight." Conceptual abstractions may be formed by filtering the information content of a concept or an observable phenomenon, selecting only those aspects which are relevant for a particular purpose. For example, abstracting a leather soccer ball to the more general idea of a ball selects only the information on gen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Non-well-founded Set Theory
Non-well-founded set theories are variants of axiomatic set theory that allow sets to be elements of themselves and otherwise violate the rule of well-foundedness. In non-well-founded set theories, the foundation axiom of ZFC is replaced by axioms implying its negation. The study of non-well-founded sets was initiated by Dmitry Mirimanoff in a series of papers between 1917 and 1920, in which he formulated the distinction between well-founded and non-well-founded sets; he did not regard well-foundedness as an axiom. Although a number of axiomatic systems of non-well-founded sets were proposed afterwards, they did not find much in the way of applications until Peter Aczel’s hyperset theory in 1988. The theory of non-well-founded sets has been applied in the logical modelling of non-terminating computational processes in computer science (process algebra and final semantics), linguistics and natural language semantics (situation theory), philosophy (work on the Liar Paradox), an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Aczel's Anti-foundation Axiom
In the foundations of mathematics, Aczel's anti-foundation axiom is an axiom set forth by , as an alternative to the axiom of foundation in Zermelo–Fraenkel set theory. It states that every accessible pointed directed graph corresponds to exactly one set. In particular, according to this axiom, the graph consisting of a single vertex with a loop corresponds to a set that contains only itself as element, i.e. a Quine atom. A set theory obeying this axiom is necessarily a non-well-founded set theory. Accessible pointed graphs An accessible pointed graph is a directed graph with a distinguished vertex (the "root") such that for any node in the graph there is at least one path in the directed graph from the root to that node. The anti-foundation axiom postulates that each such directed graph corresponds to the membership structure of exactly one set. For example, the directed graph with only one node and an edge from that node to itself corresponds to a set of the form ''x'' = . ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Peter Aczel
Peter Henry George Aczel (; born 31 October 1941) is a British mathematician, logician and Emeritus joint Professor in the Department of Computer Science and the School of Mathematics at the University of Manchester. He is known for his work in non-well-founded set theory, constructive set theory, and Frege structures. Education Aczel completed his Bachelor of Arts in Mathematics in 1963 followed by a DPhil at the University of Oxford in 1966 under the supervision of John Crossley. Career and research After two years of visiting positions at the University of Wisconsin–Madison and Rutgers University Aczel took a position at the University of Manchester. He has also held visiting positions at the University of Oslo, California Institute of Technology, Utrecht University, Stanford University and Indiana University Bloomington. He was a visiting scholar at the Institute for Advanced Study in 2012. Aczel is on the editorial board of the ''Notre Dame Journal of Formal Logic'' and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Combinatorics, Probability And Computing
''Combinatorics, Probability and Computing'' is a peer-reviewed scientific journal in mathematics published by Cambridge University Press. Its editor-in-chief is Béla Bollobás (DPMMS and University of Memphis). History The journal was established by Bollobás in 1992. Fields Medalist Timothy Gowers calls it "a personal favourite" among combinatorics journals and writes that it "maintains a high standard". Content The journal covers combinatorics, probability theory, and theoretical computer science. Currently, it publishes six issues annually. As with other journals from the same publisher, it follows a hybrid green/gold open access policy, in which authors may either place copies of their papers in an institutional repository after a six-month embargo period, or pay an open access charge to make their papers free to read on the journal's website. Abstracting and indexing The journal is abstracted and indexed in: According to the ''Journal Citation Reports'', the jou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
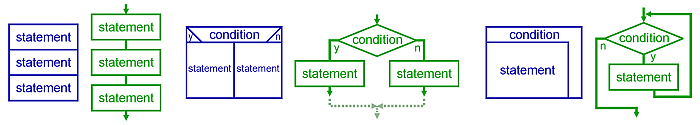
Structured Programming
Structured programming is a programming paradigm aimed at improving the clarity, quality, and development time of a computer program by making extensive use of the structured control flow constructs of selection ( if/then/else) and repetition ( while and for), block structures, and subroutines. It emerged in the late 1950s with the appearance of the ALGOL 58 and ALGOL 60 programming languages, with the latter including support for block structures. Contributing factors to its popularity and widespread acceptance, at first in academia and later among practitioners, include the discovery of what is now known as the structured program theorem in 1966, and the publication of the influential "Go To Statement Considered Harmful" open letter in 1968 by Dutch computer scientist Edsger W. Dijkstra, who coined the term "structured programming". Structured programming is most frequently used with deviations that allow for clearer programs in some particular cases, such as when exceptio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Testing
Software testing is the act of examining the artifacts and the behavior of the software under test by validation and verification. Software testing can also provide an objective, independent view of the software to allow the business to appreciate and understand the risks of software implementation. Test techniques include, but not necessarily limited to: * analyzing the product requirements for completeness and correctness in various contexts like industry perspective, business perspective, feasibility and viability of implementation, usability, performance, security, infrastructure considerations, etc. * reviewing the product architecture and the overall design of the product * working with product developers on improvement in coding techniques, design patterns, tests that can be written as part of code based on various techniques like boundary conditions, etc. * executing a program or application with the intent of examining behavior * reviewing the deployment infrastructure a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Subroutine
In computer programming, a function or subroutine is a sequence of program instructions that performs a specific task, packaged as a unit. This unit can then be used in programs wherever that particular task should be performed. Functions may be defined within programs, or separately in libraries that can be used by many programs. In different programming languages, a function may be called a routine, subprogram, subroutine, method, or procedure. Technically, these terms all have different definitions, and the nomenclature varies from language to language. The generic umbrella term ''callable unit'' is sometimes used. A function is often coded so that it can be started several times and from several places during one execution of the program, including from other functions, and then branch back (''return'') to the next instruction after the ''call'', once the function's task is done. The idea of a subroutine was initially conceived by John Mauchly during his work on ENIAC, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Call Graph
A call graph (also known as a call multigraph) is a control-flow graph, which represents calling relationships between subroutines in a computer program. Each node represents a procedure and each edge ''(f, g)'' indicates that procedure ''f'' calls procedure ''g''. Thus, a cycle in the graph indicates recursive procedure calls. Basic concepts Call graphs can be dynamic or static. A dynamic call graph is a record of an execution of the program, for example as output by a profiler. Thus, a dynamic call graph can be exact, but only describes one run of the program. A static call graph is a call graph intended to represent every possible run of the program. The exact static call graph is an undecidable problem, so static call graph algorithms are generally overapproximations. That is, every call relationship that occurs is represented in the graph, and possibly also some call relationships that would never occur in actual runs of the program. Call graphs can be defined to represe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Edge Contraction
In graph theory, an edge contraction is an operation that removes an edge from a graph while simultaneously merging the two vertices that it previously joined. Edge contraction is a fundamental operation in the theory of graph minors. Vertex identification is a less restrictive form of this operation. Definition The edge contraction operation occurs relative to a particular edge, e. The edge e is removed and its two incident vertices, u and v, are merged into a new vertex w, where the edges incident to w each correspond to an edge incident to either u or v. More generally, the operation may be performed on a set of edges by contracting each edge (in any order). The resulting induced graph is sometimes written as G/e. (Contrast this with G \setminus e, which means removing the edge e.) As defined below, an edge contraction operation may result in a graph with multiple edges even if the original graph was a simple graph. However, some authors disallow the creation of multip ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Program Analysis
In computer science, program analysis is the process of automatically analyzing the behavior of computer programs regarding a property such as correctness, robustness, safety and liveness. Program analysis focuses on two major areas: program optimization and program correctness. The first focuses on improving the program’s performance while reducing the resource usage while the latter focuses on ensuring that the program does what it is supposed to do. Program analysis can be performed without executing the program (static program analysis), during runtime (dynamic program analysis) or in a combination of both. Static program analysis In the context of program correctness, static analysis can discover vulnerabilities during the development phase of the program.Jovanovic, N., Kruegel, C., & Kirda, E. (2006, May). Pixy: A static analysis tool for detecting web application vulnerabilities. In Security and Privacy, 2006 IEEE Symposium on (pp. 6-pp). IEEE. These vulnerabilities a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |