|
Riffle (anonymity Network)
Riffle is an anonymity network developed by researchers at MIT and EPFL as a response to the problems of the Tor network. Riffle employs a verifiable shuffle and a symmetric-key algorithm. Like Tor, it utilizes onion routing. According to MIT's Larry Hardesty, researchers at MIT and the Qatar Computing Research Institute demonstrated a vulnerability in Tor's design. Messages sent over Riffle are not forwarded if they have been altered by a compromised server. The server has to attach proof in order to forward the message. The main intended use-case is anonymous file sharing File sharing is the practice of distributing or providing access to digital media, such as computer programs, multimedia (audio, images and video), documents or electronic books. Common methods of storage, transmission and dispersion include r .... According to the lead project researcher, Riffle is intended to be complementary to Tor, not a replacement. See also References External links ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymity Network
In computer networking, a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource. Instead of connecting directly to a server that can fulfill a request for a resource, such as a file or web page, the client directs the request to the proxy server, which evaluates the request and performs the required network transactions. This serves as a method to simplify or control the complexity of the request, or provide additional benefits such as load balancing, privacy, or security. Proxies were devised to add structure and encapsulation to distributed systems. A proxy server thus functions on behalf of the client when requesting service, potentially masking the true origin of the request to the resource server. Types A proxy server may reside on the user's local computer, or at any point between the user's computer and destination servers on the Internet. A proxy server that passes unmodified ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File Sharing
File sharing is the practice of distributing or providing access to digital media, such as computer programs, multimedia (audio, images and video), documents or electronic books. Common methods of storage, transmission and dispersion include removable media, centralized servers on computer networks, Internet-based hyperlinked documents, and the use of distributed peer-to-peer networking. File sharing technologies, such as BitTorrent, are integral to modern media piracy, as well as the sharing of scientific data and other free content. History Files were first exchanged on removable media. Computers were able to access remote files using filesystem mounting, bulletin board systems (1978), Usenet (1979), and FTP servers (1970's). Internet Relay Chat (1988) and Hotline (1997) enabled users to communicate remotely through chat and to exchange files. The mp3 encoding, which was standardized in 1991 and substantially reduced the size of audio files, grew to widespread use in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Communication
Secure communication is when two entities are communicating and do not want a third party to listen in. For this to be the case, the entities need to communicate in a way that is unsusceptible to eavesdropping or interception. Secure communication includes means by which people can share information with varying degrees of certainty that third parties cannot intercept what is said. Other than spoken face-to-face communication with no possible eavesdropper, it is probably safe to say that no communication is guaranteed to be secure in this sense, although practical obstacles such as legislation, resources, technical issues (interception and encryption), and the sheer volume of communication serve to limit surveillance. With many communications taking place over long distance and mediated by technology, and increasing awareness of the importance of interception issues, technology and its compromise are at the heart of this debate. For this reason, this article focuses on communicatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RetroShare
Retroshare is a free and open-source peer-to-peer communication and file sharing app based on a friend-to-friend network built by GNU Privacy Guard (GPG). Optionally, peers may exchange certificates and IP addresses to their friends and vice versa. History Retroshare was founded in 2004 by Mark Fernie. There has been an unofficial build for the single-board computer Raspberry Pi, named PiShare, since 2012. On 4 November 2014, Retroshare scored 6 out of 7 points on the Electronic Frontier Foundation's secure messaging scorecard, which is now out-of-date. It lost a point because there has not been a recent independent code audit. In August 2015, Retroshare repository was migrated from SourceForge to GitHub. In 2016, ''Linux Magazine'' reviewed security gaps in Retroshare and described it as "a brave effort, but, in the end, an ineffective one." Design Retroshare is an instant messaging and file sharing network that uses a distributed hash table for address discovery. Users ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Onion Routing
Onion routing is a technique for anonymous communication over a computer network. In an onion network, messages are encapsulated in layers of encryption, analogous to layers of an onion. The encrypted data is transmitted through a series of network nodes called onion routers, each of which "peels" away a single layer, uncovering the data's next destination. When the final layer is decrypted, the message arrives at its destination. The sender remains anonymous because each intermediary knows only the location of the immediately preceding and following nodes. While onion routing provides a high level of security and anonymity, there are methods to break the anonymity of this technique, such as timing analysis. History Onion routing was developed in the mid-1990s at the U.S. Naval Research Laboratory by employees Paul Syverson, Michael G. Reed, and David Goldschlag to protect U.S. intelligence communications online. It was then refined by the Defense Advanced Research Projects A ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Privacy
Internet privacy involves the right or mandate of personal privacy concerning the storing, re-purposing, provision to third parties, and displaying of information pertaining to oneself via Internet. Internet privacy is a subset of data privacy. Privacy concerns have been articulated from the beginnings of large-scale computer sharing. Privacy can entail either personally identifiable information (PII) or non-PII information such as a site visitor's behavior on a website. PII refers to any information that can be used to identify an individual. For example, age and physical address alone could identify who an individual is without explicitly disclosing their name, as these two factors are unique enough to identify a specific person typically. Other forms of PII may soon include GPS tracking data used by apps, as the daily commute and routine information can be enough to identify an individual. It has been suggested that the "appeal of online services is to broadcast personal infor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
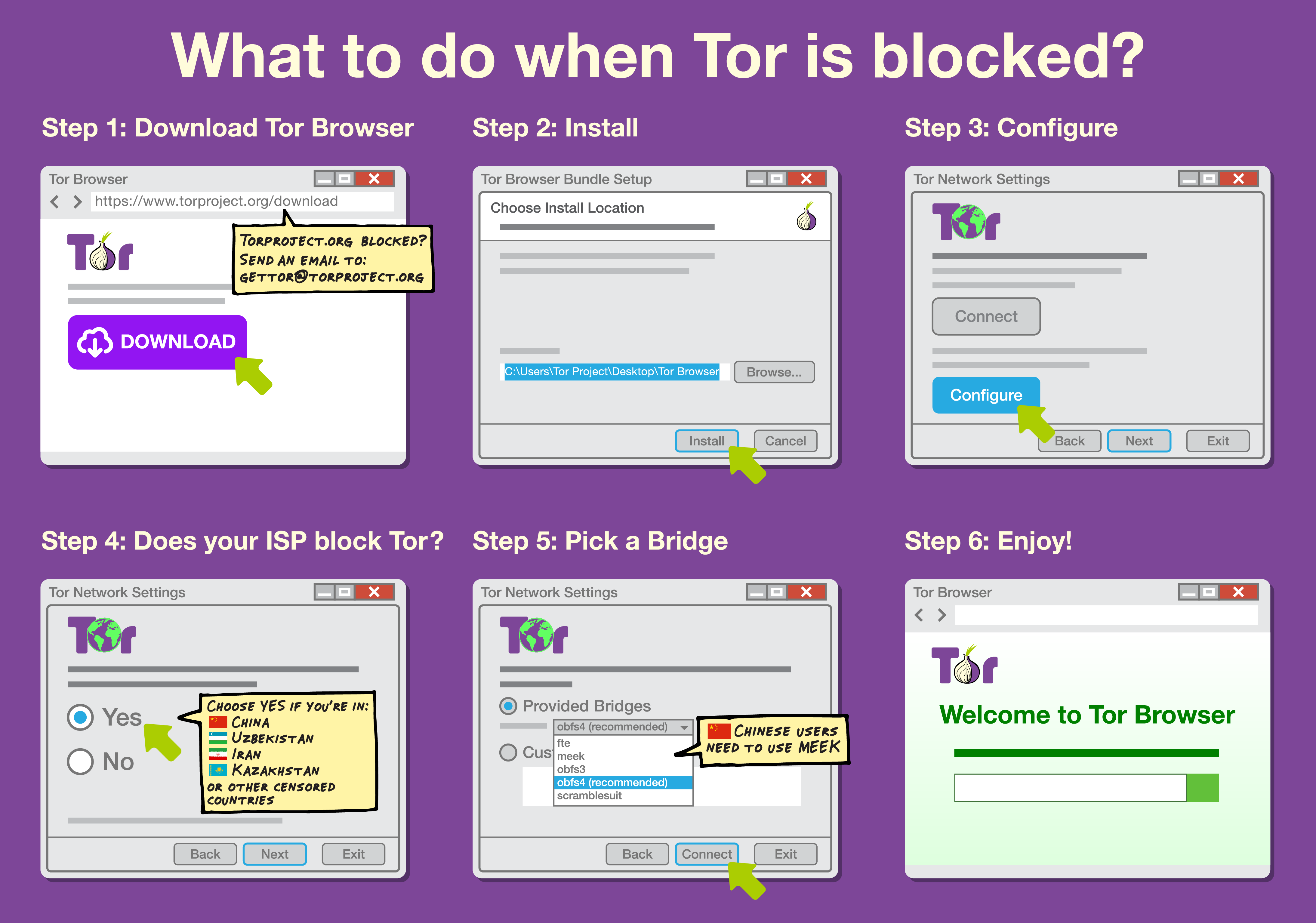
Internet Censorship Circumvention
Internet censorship circumvention is the use of various methods and tools to bypass internet censorship. Various techniques and methods are used to bypass Internet censorship, and have differing ease of use, speed, security, and risks. Some methods, such as the use of alternate DNS servers, evade blocking by using an alternate address or address lookup system to access the site. Techniques using website mirrors or archive sites rely on other copies of the site being available at different locations. Additionally, there are solutions that rely on gaining access to an Internet connection that is not subject to filtering, often in a different jurisdiction not subject to the same censorship laws, using technologies such as proxying, virtual private networks, or anonymization networks. An arms race has developed between censors and developers of circumvention software, resulting in more sophisticated blocking techniques by censors and the development of harder-to-detect tools by rese ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymous Web Browsing
Private browsing is a privacy feature in some web browsers. When operating in such a mode, the browser creates a temporary session that is isolated from the browser's main session and user data. Browsing history is not saved, and local data associated with the session, such as Cookies, Web cache, are cleared when the session is closed. These modes are designed primarily to prevent data and history associated with a particular browsing session from persisting on the device, or being discovered by another user of the same device. In web development, it can be used to quickly test displaying pages as they appear to first-time visitors. Private browsing modes do not necessarily protect users from being tracked by other websites or their Internet service provider (ISP). Furthermore, there is a possibility that identifiable traces of activity could be leaked from private browsing sessions by means of the operating system, security flaws in the browser, or via malicious browser ex ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Use Case
In software and systems engineering, the phrase use case is a polyseme with two senses: # A usage scenario for a piece of software; often used in the plural to suggest situations where a piece of software may be useful. # A potential scenario in which a system receives an external request (such as user input) and responds to it. This article discusses the latter sense. A ''use case'' is a list of actions or event steps typically defining the interactions between a role (known in the Unified Modeling Language (UML) as an ''actor'') and a system to achieve a goal. The actor can be a human or another external system. In systems engineering, use cases are used at a higher level than within software engineering, often representing missions or stakeholder goals. The detailed requirements may then be captured in the Systems Modeling Language (SysML) or as contractual statements. History In 1987, Ivar Jacobson presented the first article on use cases at the OOPSLA'87 conference. H ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Massachusetts Institute Of Technology
The Massachusetts Institute of Technology (MIT) is a private land-grant research university in Cambridge, Massachusetts. Established in 1861, MIT has played a key role in the development of modern technology and science, and is one of the most prestigious and highly ranked academic institutions in the world. Founded in response to the increasing industrialization of the United States, MIT adopted a European polytechnic university model and stressed laboratory instruction in applied science and engineering. MIT is one of three private land grant universities in the United States, the others being Cornell University and Tuskegee University. The institute has an urban campus that extends more than a mile (1.6 km) alongside the Charles River, and encompasses a number of major off-campus facilities such as the MIT Lincoln Laboratory, the Bates Center, and the Haystack Observatory, as well as affiliated laboratories such as the Broad and Whitehead Institutes. , 98 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Der Spiegel
''Der Spiegel'' (, lit. ''"The Mirror"'') is a German weekly news magazine published in Hamburg. With a weekly circulation of 695,100 copies, it was the largest such publication in Europe in 2011. It was founded in 1947 by John Seymour Chaloner, a British army officer, and Rudolf Augstein, a former Wehrmacht radio operator who was recognized in 2000 by the International Press Institute as one of the fifty World Press Freedom Heroes. Typically, the magazine has a content to advertising ratio of 2:1. ''Der Spiegel'' is known in German-speaking countries mostly for its investigative journalism. It has played a key role in uncovering many political scandals such as the ''Spiegel'' affair in 1962 and the Flick affair in the 1980s. According to ''The Economist'', ''Der Spiegel'' is one of continental Europe's most influential magazines. The news website by the same name was launched in 1994 under the name ''Spiegel Online'' with an independent editorial staff. Today, the content is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Qatar Computing Research Institute
The Qatar Computing Research Institute (QCRI) in Doha, Qatar, is a nonprofit multidisciplinary computing research institute founded by the Qatar Foundation (QF) for Education, Science and Community Development in 2010. It is primarily funded by the Qatar Foundation, a private, non-profit organization that is supporting Qatar on its journey from carbon economy to knowledge economy. Background QCRI is one of the three national research institutes under Qatar Foundation and specializes in applied computing research. Its research fall into two main categories: core computing and multidisciplinary computing. Within core computing, QCRI specializes in internet computing (with an emphasis on cloud computing and social networking), data analysis, and advanced computer hardware design. Within multidisciplinary computing, QCRI is focused on Arabic language technologies, high performance computing, and bioinformatics. QCRI has offices in the HBKU Research Complex, in Doha's Education City. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)

.jpg)