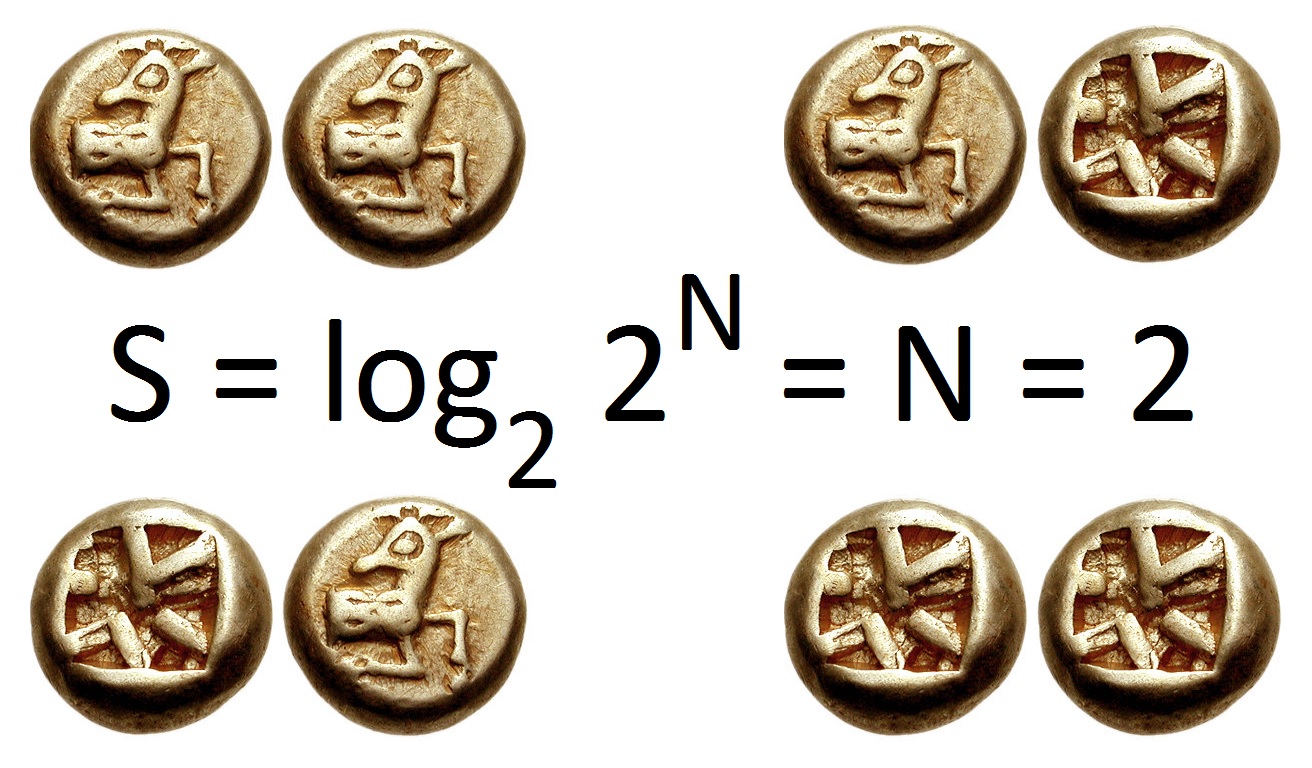|
Randomness Extractor
A randomness extractor, often simply called an "extractor", is a function, which being applied to output from a weakly random information entropy, entropy source, together with a short, uniformly random seed, generates a highly random output that appears Independent and identically distributed random variables, independent from the source and Uniform distribution (discrete), uniformly distributed. Examples of weakly random sources include radioactive decay or thermal noise; the only restriction on possible sources is that there is no way they can be fully controlled, calculated or predicted, and that a lower bound on their entropy rate can be established. For a given source, a randomness extractor can even be considered to be a true random number generator (Hardware_random_number_generator, TRNG); but there is no single extractor that has been proven to produce truly random output from any type of weakly random source. Sometimes the term "bias" is used to denote a weakly random sou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Entropy
In information theory, the entropy of a random variable is the average level of "information", "surprise", or "uncertainty" inherent to the variable's possible outcomes. Given a discrete random variable X, which takes values in the alphabet \mathcal and is distributed according to p: \mathcal\to , 1/math>: \Eta(X) := -\sum_ p(x) \log p(x) = \mathbb \log p(X), where \Sigma denotes the sum over the variable's possible values. The choice of base for \log, the logarithm, varies for different applications. Base 2 gives the unit of bits (or " shannons"), while base ''e'' gives "natural units" nat, and base 10 gives units of "dits", "bans", or " hartleys". An equivalent definition of entropy is the expected value of the self-information of a variable. The concept of information entropy was introduced by Claude Shannon in his 1948 paper " A Mathematical Theory of Communication",PDF archived froherePDF archived frohere and is also referred to as Shannon entropy. Shannon's theory d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Polynomial Time
In computer science, the time complexity is the computational complexity that describes the amount of computer time it takes to run an algorithm. Time complexity is commonly estimated by counting the number of elementary operations performed by the algorithm, supposing that each elementary operation takes a fixed amount of time to perform. Thus, the amount of time taken and the number of elementary operations performed by the algorithm are taken to be related by a constant factor. Since an algorithm's running time may vary among different inputs of the same size, one commonly considers the worst-case time complexity, which is the maximum amount of time required for inputs of a given size. Less common, and usually specified explicitly, is the average-case complexity, which is the average of the time taken on inputs of a given size (this makes sense because there are only a finite number of possible inputs of a given size). In both cases, the time complexity is generally expresse ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Hash Function
A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with fixed size of n bits) that has special properties desirable for cryptography: * the probability of a particular n-bit output result (hash value) for a random input string ("message") is 2^ (like for any good hash), so the hash value can be used as a representative of the message; * finding an input string that matches a given hash value (a ''pre-image'') is unfeasible, unless the value is selected from a known pre-calculated dictionary (" rainbow table"). The ''resistance'' to such search is quantified as security strength, a cryptographic hash with n bits of hash value is expected to have a ''preimage resistance'' strength of n bits. A ''second preimage'' resistance strength, with the same expectations, refers to a similar problem of finding a second message that matches the given hash value when one message is already known; * finding any pair of different messa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Entropy (computing)
In computing, entropy is the randomness collected by an operating system or application for use in cryptography or other uses that require random data. This randomness is often collected from hardware sources (variance in fan noise or HDD), either pre-existing ones such as mouse movements or specially provided randomness generators. A lack of entropy can have a negative impact on performance and security. Linux kernel The Linux kernel generates entropy from keyboard timings, mouse movements, and IDE timings and makes the random character data available to other operating system processes through the special files /dev/random and /dev/urandom. This capability was introduced in Linux version 1.3.30. There are some Linux kernel patches allowing one to use more entropy sources. Thaudio_entropydproject, which is included in some operating systems such as Fedora, allows audio data to be used as an entropy source. Also available arvideo_entropydwhich calculates random data from a v ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chaotic Systems
Chaos theory is an interdisciplinary area of scientific study and branch of mathematics focused on underlying patterns and deterministic laws of dynamical systems that are highly sensitive to initial conditions, and were once thought to have completely random states of disorder and irregularities. Chaos theory states that within the apparent randomness of chaotic complex systems, there are underlying patterns, interconnection, constant feedback loops, repetition, self-similarity, fractals, and self-organization. The butterfly effect, an underlying principle of chaos, describes how a small change in one state of a deterministic nonlinear system can result in large differences in a later state (meaning that there is sensitive dependence on initial conditions). A metaphor for this behavior is that a butterfly flapping its wings in Brazil can cause a tornado in Texas. Small differences in initial conditions, such as those due to errors in measurements or due to rounding erro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chaos Machine
In mathematics, a chaos machine is a class of algorithms constructed on the base of chaos theory (mainly deterministic chaos) to produce pseudo-random oracle. It represents the idea of creating a universal scheme with modular design and customizable parameters, which can be applied wherever randomness and sensitiveness is needed. Theoretical model was published in early 2015 by Maciej A. Czyzewski. It was designed specifically to combine the benefits of hash function and pseudo-random function. However, it can be used to implement many cryptographic primitives, including cryptographic hashes, message authentication codes and randomness extractors. See also * Merkle–Damgård construction * Sponge function In cryptography, a sponge function or sponge construction is any of a class of algorithms with finite state (computer science), internal state that take an input bit stream of any length and produce an output bit stream of any desired length. Spon ... External links Libch ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exchangeable Random Variables
In statistics, an exchangeable sequence of random variables (also sometimes interchangeable) is a sequence ''X''1, ''X''2, ''X''3, ... (which may be finitely or infinitely long) whose joint probability distribution does not change when the positions in the sequence in which finitely many of them appear are altered. Thus, for example the sequences : X_1, X_2, X_3, X_4, X_5, X_6 \quad \text \quad X_3, X_6, X_1, X_5, X_2, X_4 both have the same joint probability distribution. It is closely related to the use of independent and identically distributed random variables in statistical models. Exchangeable sequences of random variables arise in cases of simple random sampling. Definition Formally, an exchangeable sequence of random variables is a finite or infinite sequence ''X''1, ''X''2, ''X''3, ... of random variables such that for any finite permutation σ of the indices 1, 2, 3, ..., (the permutation acts on only finitely many indices, with the res ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bernoulli Sequence
In probability and statistics, a Bernoulli process (named after Jacob Bernoulli) is a finite or infinite sequence of binary random variables, so it is a discrete-time stochastic process that takes only two values, canonically 0 and 1. The component Bernoulli variables ''X''''i'' are identically distributed and independent. Prosaically, a Bernoulli process is a repeated coin flipping, possibly with an unfair coin (but with consistent unfairness). Every variable ''X''''i'' in the sequence is associated with a Bernoulli trial or experiment. They all have the same Bernoulli distribution. Much of what can be said about the Bernoulli process can also be generalized to more than two outcomes (such as the process for a six-sided die); this generalization is known as the Bernoulli scheme. The problem of determining the process, given only a limited sample of Bernoulli trials, may be called the problem of checking whether a coin is fair. Definition A Bernoulli process is a fini ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Correlation
In statistics, correlation or dependence is any statistical relationship, whether causal or not, between two random variables or bivariate data. Although in the broadest sense, "correlation" may indicate any type of association, in statistics it usually refers to the degree to which a pair of variables are ''linearly'' related. Familiar examples of dependent phenomena include the correlation between the height of parents and their offspring, and the correlation between the price of a good and the quantity the consumers are willing to purchase, as it is depicted in the so-called demand curve. Correlations are useful because they can indicate a predictive relationship that can be exploited in practice. For example, an electrical utility may produce less power on a mild day based on the correlation between electricity demand and weather. In this example, there is a causal relationship, because extreme weather causes people to use more electricity for heating or cooling. However ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
John Von Neumann
John von Neumann (; hu, Neumann János Lajos, ; December 28, 1903 – February 8, 1957) was a Hungarian-American mathematician, physicist, computer scientist, engineer and polymath. He was regarded as having perhaps the widest coverage of any mathematician of his time and was said to have been "the last representative of the great mathematicians who were equally at home in both pure and applied mathematics". He integrated pure and applied sciences. Von Neumann made major contributions to many fields, including mathematics (foundations of mathematics, measure theory, functional analysis, ergodic theory, group theory, lattice theory, representation theory, operator algebras, matrix theory, geometry, and numerical analysis), physics (quantum mechanics, hydrodynamics, ballistics, nuclear physics and quantum statistical mechanics), economics ( game theory and general equilibrium theory), computing ( Von Neumann architecture, linear programming, numerical meteo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Negligible Function
In mathematics, a negligible function is a function \mu:\mathbb\to\mathbb such that for every positive integer ''c'' there exists an integer ''N''''c'' such that for all ''x'' > ''N''''c'', :, \mu(x), 0 such that for all ''x'' > ''N''poly : , \mu(x), 0, there exists a positive number \delta>0 such that , x-x_0, N_\varepsilon ::, \mu(x), 0 by the functions 1/x^c where c>0 or by 1/\operatorname(x) where \operatorname(x) is a positive polynomial. This leads to the definitions of negligible functions given at the top of this article. Since the constants \varepsilon>0 can be expressed as 1/\operatorname(x) with a constant polynomial this shows that negligible functions are a subset of the infinitesimal functions. Use in cryptography In complexity-based modern cryptography, a security scheme is ''provably secure'' if the probability of security failure (e.g., inverting a one-way function, distinguishing cryptographically strong pseudorandom bits from truly ran ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |