|
RSA BSAFE
Dell BSAFE, formerly known as RSA BSAFE, is a FIPS 140-2 validated cryptography library, available in both C and Java. BSAFE was initially created by RSA Security, which was purchased by EMC and then, in turn, by Dell. When Dell sold the RSA business to Symphony Technology Group in 2020, Dell elected to retain the BSAFE product line. BSAFE was one of the most common encryption toolkits before the RSA patent expired in September 2000. It also contained implementations of the RC''x'' ciphers, with the most common one being RC4. From 2004 to 2013 the default random number generator in the library was a NIST-approved RNG standard, widely known to be insecure from at least 2006, containing a kleptographic backdoor from the American National Security Agency (NSA), as part of its secret Bullrun program. In 2013 Reuters revealed that RSA had received a payment of $10 million to set the compromised algorithm as the default option. The RNG standard was subsequently withdrawn in 2014, a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dell
Dell is an American based technology company. It develops, sells, repairs, and supports computers and related products and services. Dell is owned by its parent company, Dell Technologies. Dell sells personal computers (PCs), servers, data storage devices, network switches, software, computer peripherals, HDTVs, cameras, printers, and electronics built by other manufacturers. The company is known for how it manages its supply chain and electronic commerce. This includes Dell selling directly to customers and delivering PCs that the customer wants. Dell was a pure hardware vendor until 2009 when it acquired Perot Systems. Dell then entered the market for IT services. The company has expanded storage and networking systems. It is now expanding from offering computers only to delivering a range of technology for enterprise customers. Dell is a publicly-traded company (), as well as a component of the NASDAQ-100 and S&P 500. It is the 3rd largest personal computer vendor as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Java (programming Language)
Java is a high-level, class-based, object-oriented programming language that is designed to have as few implementation dependencies as possible. It is a general-purpose programming language intended to let programmers ''write once, run anywhere'' ( WORA), meaning that compiled Java code can run on all platforms that support Java without the need to recompile. Java applications are typically compiled to bytecode that can run on any Java virtual machine (JVM) regardless of the underlying computer architecture. The syntax of Java is similar to C and C++, but has fewer low-level facilities than either of them. The Java runtime provides dynamic capabilities (such as reflection and runtime code modification) that are typically not available in traditional compiled languages. , Java was one of the most popular programming languages in use according to GitHub, particularly for client–server web applications, with a reported 9 million developers. Java was originally developed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
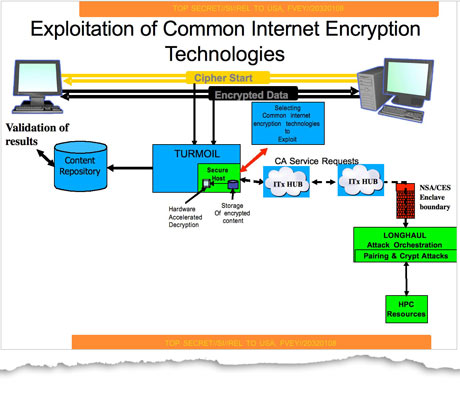
Global Surveillance Disclosure
Global means of or referring to a globe and may also refer to: Entertainment * ''Global'' (Paul van Dyk album), 2003 * ''Global'' (Bunji Garlin album), 2007 * ''Global'' (Humanoid album), 1989 * ''Global'' (Todd Rundgren album), 2015 * Bruno J. Global, a character in the anime series ''The Super Dimension Fortress Macross'' Companies and brands Television * Global Television Network, in Canada ** Global BC, on-air brand of CHAN-TV, a television station in Vancouver, British Columbia, Canada ** Global Okanagan, on-air brand of CHBC-TV, a television station in Kelowna, British Columbia, Canada ** Global Toronto, a television station in Toronto ** Global Edmonton ** Global Calgary ** Global Montreal ** Global Maritimes ** Canwest Global, former parent company of Global Television Network * Global TV (Venezuela), a regional channel in Venezuela Other industries * Global (cutlery), a Japanese brand * Global Aviation Holdings, the parent company of World Airways, Inc., and North Am ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bruce Schneier
Bruce Schneier (; born January 15, 1963) is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is a Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman Klein Center for Internet & Society as of November, 2013. He is a board member of the Electronic Frontier Foundation, Access Now, and The Tor Project; and an advisory board member of Electronic Privacy Information Center and VerifiedVoting.org. He is the author of several books on general security topics, computer security and cryptography and is a squid enthusiast. In 2015, Schneier received the EPIC Lifetime Achievement Award from Electronic Privacy Information Center. Early life Bruce Schneier is the son of Martin Schneier, a Brooklyn Supreme Court judge. He grew up in the Flatbush neighborhood of Brooklyn, New York, attending P.S. 139 and Hunter College High School. After receiving a physics bachelor's degree from the University of Roche ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dual EC DRBG
Dual_EC_DRBG (Dual Elliptic Curve Deterministic Random Bit Generator) is an algorithm that was presented as a cryptographically secure pseudorandom number generator (CSPRNG) using methods in elliptic curve cryptography. Despite wide public criticism, including the public identification of a backdoor, it was for seven years one of four CSPRNGs standardized in NIST SP 800-90A as originally published circa June 2006, until it was withdrawn in 2014. Weakness: a potential backdoor Weaknesses in the cryptographic security of the algorithm were known and publicly criticised well before the algorithm became part of a formal standard endorsed by the ANSI, ISO, and formerly by the National Institute of Standards and Technology (NIST). One of the weaknesses publicly identified was the potential of the algorithm to harbour a kleptographic backdoor advantageous to those who know about it—the United States government's National Security Agency (NSA)—and no one else. In 2013, ''The New ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographically Secure Pseudorandom Number Generator
A cryptographically secure pseudorandom number generator (CSPRNG) or cryptographic pseudorandom number generator (CPRNG) is a pseudorandom number generator (PRNG) with properties that make it suitable for use in cryptography. It is also loosely known as a cryptographic random number generator (CRNG) (see Random number generation § "True" vs. pseudo-random numbers). Most cryptographic applications require random numbers, for example: * key generation * nonces * salts in certain signature schemes, including ECDSA, RSASSA-PSS The "quality" of the randomness required for these applications varies. For example, creating a nonce in some protocols needs only uniqueness. On the other hand, the generation of a master key requires a higher quality, such as more entropy. And in the case of one-time pads, the information-theoretic guarantee of perfect secrecy only holds if the key material comes from a true random source with high entropy, and thus any kind of pseudorandom number genera ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bullrun (decryption Program)
Bullrun (stylized BULLRUN) is a clandestine, highly classified program to crack encryption of online communications and data, which is run by the United States National Security Agency (NSA). The British Government Communications Headquarters (GCHQ) has a similar program codenamed Edgehill. According to the Bullrun classification guide published by ''The Guardian'', the program uses multiple methods including computer network exploitation, interdiction, industry relationships, collaboration with other intelligence community entities, and advanced mathematical techniques. Information about the program's existence was leaked in 2013 by Edward Snowden. Although Snowden's documents do not contain technical information on exact cryptanalytic capabilities because Snowden did not have clearance access to such information, they do contain a 2010 GCHQ presentation which claims that "vast amounts of encrypted Internet data which have up till now been discarded are now exploitable". A num ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency
The National Security Agency (NSA) is a national-level intelligence agency of the United States Department of Defense, under the authority of the Director of National Intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The existence of the NSA was not revealed until 1975. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of pers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backdoor (computing)
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g. a home router), or its embodiment (e.g. part of a cryptosystem, algorithm, chipset, or even a "homunculus computer" —a tiny computer-within-a-computer such as that found in Intel's Intel Active Management Technology, AMT technology). Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptographic systems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within autoschediastic networks. A backdoor may take the form of a hidden part of a program, a separate program (e.g. Back Orifice may subvert the system through a rootkit), code in the hardware backdoor, firmware of the hardware, or parts of an operating system such as Microsoft Windows, Windows. Trojan horse (computing), Trojan horses can be u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kleptographic
Kleptography is the study of stealing information securely and subliminally. The term was introduced by Adam Young and Moti Yung in the Proceedings of Advances in Cryptology—Crypto '96.A. Young, M. Yung, "The Dark Side of Black-Box Cryptography, or: Should we trust Capstone?" In Proceedings of Crypto '96, Neal Koblitz (Ed.), Springer-Verlag, pages 89–103, 1996. Kleptography is a subfield of cryptovirology and is a natural extension of the theory of subliminal channels that was pioneered by Gus Simmons while at Sandia National Laboratory. G. J. Simmons, "The Prisoners' Problem and the Subliminal Channel," In Proceedings of Crypto '83, D. Chaum (Ed.), pages 51–67, Plenum Press, 1984.G. J. Simmons, "The Subliminal Channel and Digital Signatures," In Proceedings of Eurocrypt '84, T. Beth, N. Cot, I. Ingemarsson (Eds.), pages 364-378, Springer-Verlag, 1985.G. J. Simmons, "Subliminal Communication is Easy Using the DSA," In proceedings of Eurocrypt '93, T. Helleseth (Ed.), pages 21 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Institute Of Standards And Technology
The National Institute of Standards and Technology (NIST) is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness. NIST's activities are organized into physical science laboratory programs that include nanoscale science and technology, engineering, information technology, neutron research, material measurement, and physical measurement. From 1901 to 1988, the agency was named the National Bureau of Standards. History Background The Articles of Confederation, ratified by the colonies in 1781, provided: The United States in Congress assembled shall also have the sole and exclusive right and power of regulating the alloy and value of coin struck by their own authority, or by that of the respective states—fixing the standards of weights and measures throughout the United States. Article 1, section 8, of the Constitution of the United States, ratified in 1789, granted these powers to the new Congr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Random Number Generation
Random number generation is a process by which, often by means of a random number generator (RNG), a sequence of numbers or symbols that cannot be reasonably predicted better than by random chance is generated. This means that the particular outcome sequence will contain some patterns detectable in hindsight but unpredictable to foresight. True random number generators can be '' hardware random-number generators'' (HRNGS) that generate random numbers, wherein each generation is a function of the current value of a physical environment's attribute that is constantly changing in a manner that is practically impossible to model. This would be in contrast to so-called "random number generations" done by ''pseudorandom number generators'' (PRNGs) that generate numbers that only look random but are in fact pre-determined—these generations can be reproduced simply by knowing the state of the PRNG. Various applications of randomness have led to the development of several different metho ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)