|
Reliable Data Transfer
Reliable Data Transfer is a topic in computer networking concerning the transfer of data across unreliable channels. Unreliability is one of the drawbacks of packet switched networks such as the modern internet, as packet loss can occur for a variety of reasons, and delivery of packets is not guaranteed to happen in the order that the packets were sent. Therefore, in order to create long-term data streams over the internet, techniques have been developed to provide reliability, which are generally implemented in the Transport layer of the internet protocol suite. In instructional materials, the topic is often presented in the form of theoretical example protocols which are themselves referred to as "RDT", in order to introduce students to the problems and solutions encountered in Transport layer protocols such as the Transmission Control Protocol. These sources often describe a pseudo- API and include Finite-state machine diagrams to illustrate how such a protocol might be im ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Packet Switching
In telecommunications, packet switching is a method of grouping Data (computing), data into ''network packet, packets'' that are transmitted over a digital Telecommunications network, network. Packets are made of a header (computing), header and a payload (computing), payload. Data in the header is used by networking hardware to direct the packet to its destination, where the payload is extracted and used by an operating system, application software, or protocol suite, higher layer protocols. Packet switching is the primary basis for data communications in computer networks worldwide. In the early 1960s, American computer scientist Paul Baran developed the concept that he called "distributed adaptive message block switching", with the goal of providing a fault-tolerant, efficient routing method for telecommunication messages as part of a research program at the RAND Corporation, funded by the United States Department of Defense. His ideas contradicted then-established principles ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Packet Loss
Packet loss occurs when one or more packets of data travelling across a computer network fail to reach their destination. Packet loss is either caused by errors in data transmission, typically across wireless networks, or network congestion.Kurose, J.F. & Ross, K.W. (2010). ''Computer Networking: A Top-Down Approach''. New York: Addison-Wesley. Packet loss is measured as a percentage of packets lost with respect to packets sent. The Transmission Control Protocol (TCP) detects packet loss and performs retransmissions to ensure reliable messaging. Packet loss in a TCP connection is also used to avoid congestion and thus produces an intentionally reduced throughput for the connection. In real-time applications like streaming media or online games, packet loss can affect a user's quality of experience (QoE). Causes The Internet Protocol (IP) is designed according to the end-to-end principle as a best-effort delivery service, with the intention of keeping the logic routers mu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
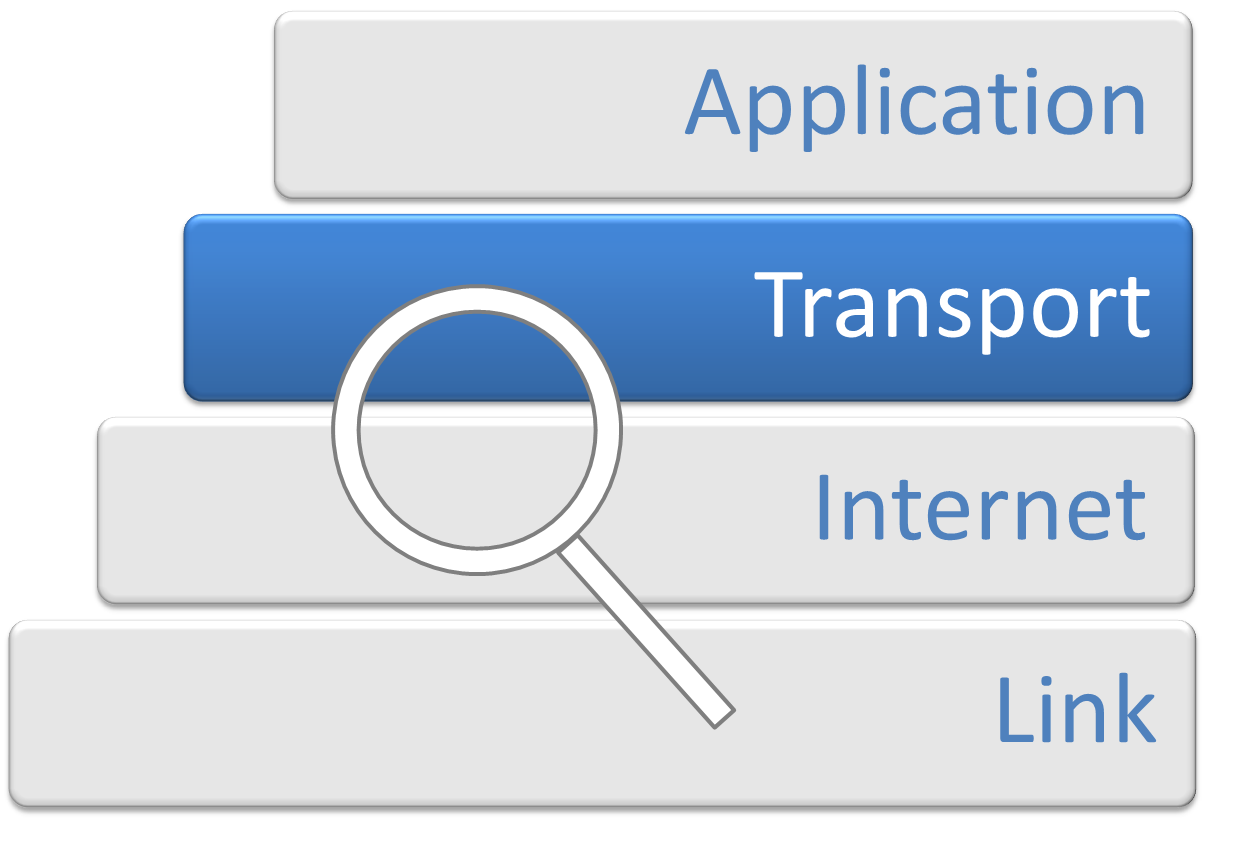
Transport Layer
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-end communication services for applications. It provides services such as connection-oriented communication, reliability, flow control, and multiplexing. The details of implementation and semantics of the transport layer of the Internet protocol suite, which is the foundation of the Internet, and the OSI model of general networking are different. The protocols in use today in this layer for the Internet all originated in the development of TCP/IP. In the OSI model the transport layer is often referred to as Layer 4, or L4, while numbered layers are not used in TCP/IP. The best-known transport protocol of the Internet protocol suite is the Transmission Control Protocol (TCP). It is used for connection-oriented transmissions, whereas the co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the Transport Layer of the TCP/IP suite. SSL/TLS often runs on top of TCP. TCP is connection-oriented, and a connection between client and server is established before data can be sent. The server must be listening (passive open) for connection requests from clients before a connection is established. Three-way handshake (active open), retransmission, and error detection adds to reliability but lengthens latency. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Finite-state Machine
A finite-state machine (FSM) or finite-state automaton (FSA, plural: ''automata''), finite automaton, or simply a state machine, is a mathematical model of computation. It is an abstract machine that can be in exactly one of a finite number of '' states'' at any given time. The FSM can change from one state to another in response to some inputs; the change from one state to another is called a ''transition''. An FSM is defined by a list of its states, its initial state, and the inputs that trigger each transition. Finite-state machines are of two types— deterministic finite-state machines and non-deterministic finite-state machines. A deterministic finite-state machine can be constructed equivalent to any non-deterministic one. The behavior of state machines can be observed in many devices in modern society that perform a predetermined sequence of actions depending on a sequence of events with which they are presented. Simple examples are vending machines, which dispens ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Packet
In telecommunications and computer networking, a network packet is a formatted unit of data carried by a packet-switched network. A packet consists of control information and user data; the latter is also known as the '' payload''. Control information provides data for delivering the payload (e.g., source and destination network addresses, error detection codes, or sequencing information). Typically, control information is found in packet headers and trailers. In packet switching, the bandwidth of the transmission medium is shared between multiple communication sessions, in contrast to circuit switching, in which circuits are preallocated for the duration of one session and data is typically transmitted as a continuous bit stream. Terminology In the seven-layer OSI model of computer networking, ''packet'' strictly refers to a protocol data unit at layer 3, the network layer. A data unit at layer 2, the data link layer, is a '' frame''. In layer 4, the transport lay ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reliable Data Protocol
The Reliable Data Protocol (RDP) is a network transport protocol defined iRFC 908and was updated iRFC 1151 It is meant to provide facilities for remote loading, debugging and bulk transfer of images and data. The Reliable Data Protocol is located on the Transport Layer of the OSI model next to protocols like TCP and UDP. It is number 27 in the list of IP protocol numbers. Similar to TCP, the Reliable Data Protocol is connection oriented, but, contrary to TCP, it does not require sequenced delivery of segments. The Reliable Data Protocol has not gained popularity, though experimental implementations for BSD exist. References See Also * Reliable Data Transfer Reliable Data Transfer is a topic in computer networking concerning the transfer of data across unreliable channels. Unreliability is one of the drawbacks of packet switched networks such as the modern internet, as packet loss can occur for a v ... Transport layer protocols Internet protocols {{network-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Networking
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies, based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies. The nodes of a computer network can include personal computers, servers, networking hardware, or other specialised or general-purpose hosts. They are identified by network addresses, and may have hostnames. Hostnames serve as memorable labels for the nodes, rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the transmission medium used to carry signals, bandwidth, communications ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Go-Back-N ARQ
Go-Back-''N'' ARQ is a specific instance of the automatic repeat request (ARQ) protocol, in which the sending process continues to send a number of frames specified by a ''window size'' even without receiving an acknowledgement (ACK) packet from the receiver. It is a special case of the general sliding window protocol with the transmit window size of and receive window size of 1. It can transmit frames to the peer before requiring an ACK. The receiver process keeps track of the sequence number of the next frame it expects to receive. It will discard any frame that does not have the exact sequence number it expects (either a duplicate frame it already acknowledged, or an out-of-order frame it expects to receive later) and will send an ACK for the last correct in-order frame. Once the sender has sent all of the frames in its ''window'', it will detect that all of the frames since the first lost frame are ''outstanding'', and will go back to the sequence number of the last ACK ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Selective Repeat ARQ
Selective Repeat ARQ/Selective Reject ARQ is a specific instance of the automatic repeat request (ARQ) protocol used to manage sequence numbers and retransmissions in reliable communications. Summary Selective Repeat is part of the automatic repeat request (ARQ). With selective repeat, the sender sends a number of frames specified by a window size even without the need to wait for individual ACK from the receiver as in Go-Back-N ARQ. The receiver may selectively reject a single frame, which may be retransmitted alone; this contrasts with other forms of ARQ, which must send every frame from that point again. The receiver accepts out-of-order frames and buffers them. The sender individually retransmits frames that have timed out. Concept It may be used as a protocol for the delivery and acknowledgement of message units, or it may be used as a protocol for the delivery of subdivided message sub-units. When used as the protocol for the delivery of messages, the sending process c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Networking
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies, based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies. The nodes of a computer network can include personal computers, servers, networking hardware, or other specialised or general-purpose hosts. They are identified by network addresses, and may have hostnames. Hostnames serve as memorable labels for the nodes, rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the transmission medium used to carry signals, bandwidth, communications ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |