|
Rebasing
In computing, rebasing is the process of modifying data based on one reference to another. It can be one of the following: Shared libraries Rebasing is the process of creating a shared library image in such a way that it is guaranteed to use virtual memory without conflicting with any other shared libraries loadable in the system. IBM VM/370 ''discontinuous saved segments'' (DCSS) were an early example of this technique, though not called ''rebasing''. The technique is used extensively on Win32 platforms to avoid the overhead of address relocation of system DLLs by the loader. Some security extensions to Linux/x86 use rebasing to force the use of code addresses below 0x00ffffff in order to introduce a 0x00 byte into all code pointers; This eliminates a certain class of buffer overflow security problems related to improper checking of null-terminated strings, common in the C programming language. Other uses * Rebasing is the act of moving changesets to a different bra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Shared Library
In computing, a library is a collection of System resource, resources that can be leveraged during software development to implement a computer program. Commonly, a library consists of executable code such as compiled function (computer science), functions and Class (computer programming), classes, or a library can be a collection of source code. A resource library may contain data such as images and Text string, text. A library can be used by multiple, independent consumers (programs and other libraries). This differs from resources defined in a program which can usually only be used by that program. When a consumer uses a library resource, it gains the value of the library without having to implement it itself. Libraries encourage software reuse in a Modular programming, modular fashion. Libraries can use other libraries resulting in a hierarchy of libraries in a program. When writing code that uses a library, a programmer only needs to know how to use it not its internal d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Darcs
Darcs is a distributed version control system created by David Roundy. Key features include the ability to choose which changes to accept from other repositories, interaction with either other local (on-disk) repositories or remote repositories via SSH, HTTP, or email, and an unusually interactive interface. The developers also emphasize the use of advanced software tools for verifying correctness: the expressive type system of the functional programming language Haskell enforces some properties, and randomized testing via QuickCheck verifies many others. The name is a recursive acronym for Darcs Advanced Revision Control System. Model Darcs treats patches as first-class citizens. For the user, a repository can be seen as a set of patches, where each patch is not necessarily ordered with respect to other patches, i.e. the set of patches is only a partially ordered set. In many cases patches can be independently transmitted between various repositories. Many branching, mergin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Microsoft Press
Microsoft Press is the publishing arm of Microsoft, usually releasing books dealing with various current Microsoft technologies. Microsoft Press' introduced books were ''The Apple Macintosh Book'' by Cary Lu and ''Exploring the IBM PCjr Home Computer'' by Peter Norton in 1984 at the West Coast Computer Faire. The publisher has gone on to release books by other recognizable authors such as Charles Petzold, Steve McConnell, Mark Russinovich and Jeffrey Richter. Following a deal signed in 2009, O'Reilly Media became the official distributor of Microsoft Press books. In 2014, the distributor was changed to Pearson PLC, Pearson. In July 2016, Microsoft Press editorial staff was laid off. References External links * Microsoft divisions Computer book publishing companies Publishing companies established in 1984 {{microsoft-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Microsoft Corporation
Microsoft Corporation is an American multinational corporation and technology company, technology conglomerate headquartered in Redmond, Washington. Founded in 1975, the company became influential in the History of personal computers#The early 1980s and home computers, rise of personal computers through software like Windows, and the company has since expanded to Internet services, cloud computing, video gaming and other fields. Microsoft is the List of the largest software companies, largest software maker, one of the Trillion-dollar company, most valuable public U.S. companies, and one of the List of most valuable brands, most valuable brands globally. Microsoft was founded by Bill Gates and Paul Allen to develop and sell BASIC interpreters for the Altair 8800. It rose to dominate the personal computer operating system market with MS-DOS in the mid-1980s, followed by Windows. During the 41 years from 1980 to 2021 Microsoft released 9 versions of MS-DOS with a median frequen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
MSDN Magazine
Microsoft Developer Network (MSDN) was the division of Microsoft responsible for managing the firm's relationship with developers and testers, such as hardware developers interested in the operating system (OS), and software developers developing on the various OS platforms or using the API or scripting languages of Microsoft's applications. The relationship management was situated in assorted media: web sites, newsletters, developer conferences, trade media, blogs and DVD distribution. Starting in January 2020, the website was fully integrated with Microsoft Docs (itself integrated into Microsoft Learn in 2022). Websites MSDN's primary web presence at ''msdn.microsoft.com'' was a collection of sites for the developer community that provided information, documentation, and discussion that was authored both by Microsoft and by the community at large. Microsoft later began placing emphasis on incorporation of forums, blogs, library annotations and social bookmarking to make MSDN ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Morgan Kaufmann
Morgan Kaufmann Publishers is a Burlington, Massachusetts (San Francisco, California until 2008) based publisher specializing in computer science and engineering content. Since 1984, Morgan Kaufmann has been publishing contents on information technology, computer architecture, data management, computer networking, computer systems, human computer interaction, computer graphics, multimedia information and systems, artificial intelligence, computer security, and software engineering. Morgan Kaufmann's audience includes the research and development communities, information technology (IS/IT) managers, and students in professional degree programs. The company was founded in 1984 by publishers Michael B. Morgan and William Kaufmann and computer scientist Nils Nilsson. It was held privately until 1998, when it was acquired by Harcourt General and became an imprint of the Academic Press, a subsidiary of Harcourt. Harcourt was acquired by Reed Elsevier in 2001; Morgan Kaufmann is now ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Dynamic Dead Code Elimination
In compiler theory, dead-code elimination (DCE, dead-code removal, dead-code stripping, or dead-code strip) is a compiler optimization to remove dead code (code that does not affect the program results). Removing such code has several benefits: it shrinks program size, an important consideration in some contexts, it reduces resource usage such as the number of bytes to be transferredMalavolta, Ivano et al. “JavaScript Dead Code Identification, Elimination, and Empirical Assessment.” IEEE transactions on software engineering 49.7 (2023): 3692–3714. Web. and it allows the running program to avoid executing irrelevant operations, which reduces its running time. It can also enable further optimizations by simplifying program structure. Dead code includes code that can never be executed (unreachable code), and code that only affects dead variables (written to, but never read again), that is, irrelevant to the program. Examples Consider the following example written in C. int ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
High Memory Area
In DOS memory management, the high memory area (HMA) is the RAM area consisting of the first 65520 bytes above the one megabyte in an IBM AT or compatible computer. In real mode, the segmentation architecture of the Intel 8086 and subsequent processors identifies memory locations with a 16-bit segment and a 16-bit offset, which is resolved into a physical address via (segment) × 16 + (offset). Although intended to address only 1 Megabyte (MB) (220 bytes) of memory, segment:offset addresses at FFFF:0010 and beyond reference memory beyond 1 MB (FFFF0 + 0010 = 100000). So, on an 80286 and subsequent processors, this mode can actually address the first 65520 bytes of extended memory as part of the 64 KB range starting 16 bytes before the 1 MB mark—FFFF:0000 (0xFFFF0) to FFFF:FFFF (0x10FFEF). The Intel 8086 and 8088 processors, with only 1 MB of memory and only 20 address lines, wrapped around at the 20th bit, so that address FFFF:001 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Portable Executable
The Portable Executable (PE) format is a file format for executables, object file, object code, Dynamic-link library, dynamic-link-libraries (DLLs), and binary files used on 32-bit and 64-bit Microsoft Windows, Windows operating systems, as well as in UEFI environments. It is the standard format for executables on Windows NT-based systems, including files such as .exe, .dll, .sys (for system drivers), and .mui. At its core, the PE format is a structured data container that gives the Windows operating system loader everything it needs to properly manage the Executable, executable code it contains. This includes references for Library (computer science)#Dynamic linking, dynamically linked libraries, tables for importing and exporting Application programming interface, APIs, resource management data and thread-local storage (TLS) information. According to the Unified Extensible Firmware Interface, Unified Extensible Firmware Interface (UEFI) specification, the PE format is also the a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Position-independent Code
In computing, position-independent code (PIC) or position-independent executable (PIE) is a body of machine code that executes properly regardless of its memory address. PIC is commonly used for shared libraries, so that the same library code can be loaded at a location in each program's address space where it does not overlap with other memory in use by, for example, other shared libraries. PIC was also used on older computer systems that lacked an MMU, so that the operating system could keep applications away from each other even within the single address space of an MMU-less system. Position-independent code can be executed at any memory address without modification. This differs from absolute code, which must be loaded at a specific location to function correctly, and load-time locatable (LTL) code, in which a linker or program loader modifies a program before execution, so it can be run only from a particular memory location. The latter terms are sometimes referred to as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Relocation (computing)
In software development, relocation is the process of assigning load addresses for position-dependent code and data of a program and adjusting the code and data to reflect the assigned addresses. A linker usually performs relocation in conjunction with ''symbol resolution'', the process of searching files and libraries to replace symbolic references or names of libraries with actual usable addresses in memory before running a program. Relocation is typically done by the linker at link time, but it can also be done at load time by a relocating loader, or at run time by the running program itself. Segmentation Object files are typically segmented into various memory segment or section types. Example segment types include code segment (.text), initialized data segment (.data), uninitialized data segment (.bss), or others as established by the programmer, such as common segments, or named static segments. Relocation table The relocation table is a list of address ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
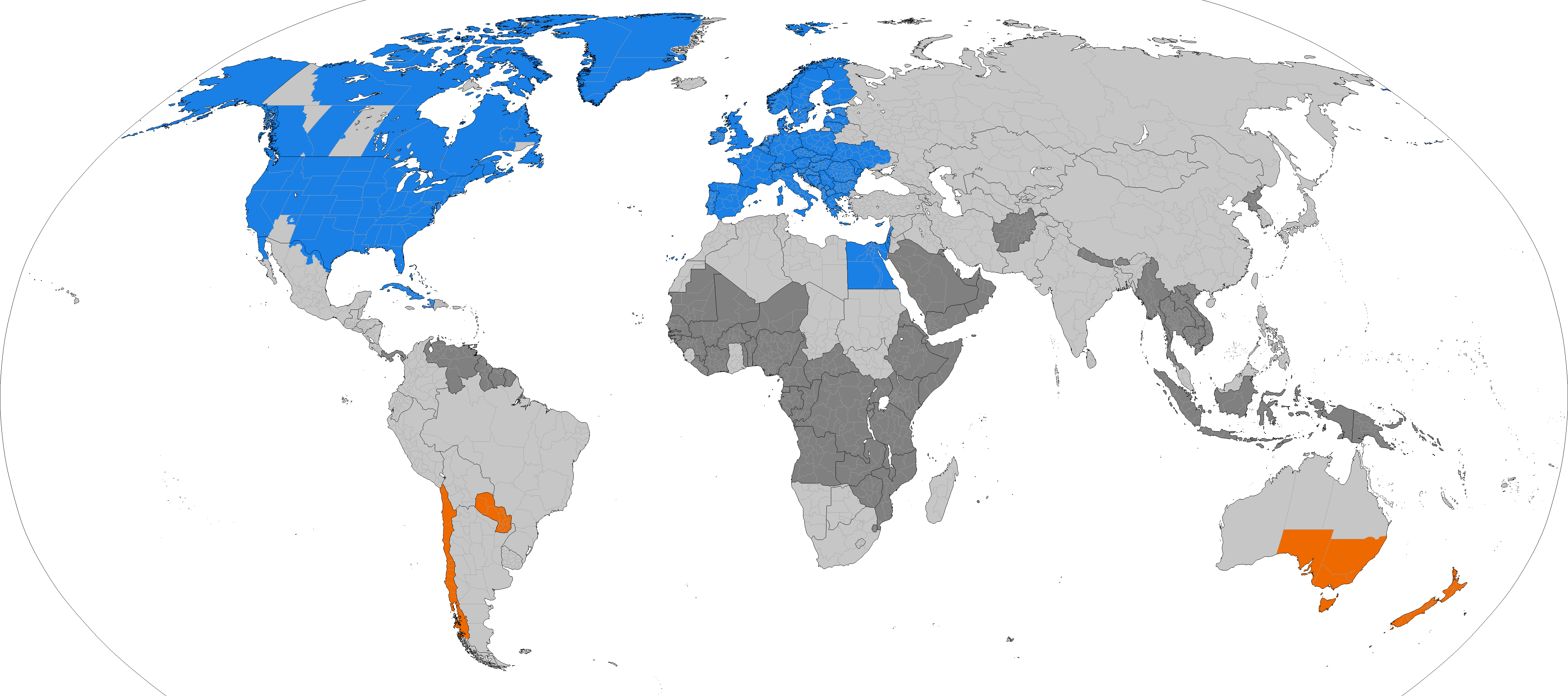
Daylight Saving Time
Daylight saving time (DST), also referred to as daylight savings time, daylight time (Daylight saving time in the United States, United States and Daylight saving time in Canada, Canada), or summer time (British Summer Time, United Kingdom, Summer time in Europe, European Union, and others), is the practice of advancing clocks to make better use of the longer daylight available during summer so that darkness falls at a later clock time. The standard implementation of DST is to set clocks forward by one hour in spring (season), spring or late winter, and to set clocks back by one hour to standard time in the autumn (or ''fall'' in North American English, hence the mnemonic: "spring forward and fall back"). Overview As of 2023, around 34 percent of the world's countries use DST. Some countries observe it only in some regions. In Canada, all of Yukon Time Zone, Yukon, most of Time in Saskatchewan, Saskatchewan, and parts of Nunavut, Ontario, British Columbia and Quebec do not ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |