|
Re-order Buffer
A re-order buffer (ROB) is a hardware unit used in an extension to Tomasulo's algorithm to support out-of-order and speculative instruction execution. The extension forces instructions to be committed in-order. The buffer is a circular buffer (to provide a FIFO instruction ordering queue) implemented as an array/vector (which allows recording of results against instructions as they complete out of order). There are three stages to the Tomasulo algorithm: "Issue", "Execute", "Write Result". In an extension to the algorithm, there is an additional "Commit" stage. During the Commit stage, instruction results are stored in a register or memory. The "Write Result" stage is modified to place results in the re-order buffer. Each instruction is tagged in the reservation station with its index in the ROB for this purpose. The contents of the buffer are used for data dependencies of other instructions scheduled in the buffer. The head of the buffer will be committed once its result ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tomasulo's Algorithm
Tomasulo's algorithm is a computer architecture hardware algorithm for dynamic scheduling of instructions that allows out-of-order execution and enables more efficient use of multiple execution units. It was developed by Robert Tomasulo at IBM in 1967 and was first implemented in the IBM System/360 Model 91’s floating point unit. The major innovations of Tomasulo’s algorithm include register renaming in hardware, reservation stations for all execution units, and a common data bus (CDB) on which computed values broadcast to all reservation stations that may need them. These developments allow for improved parallel execution of instructions that would otherwise stall under the use of scoreboarding or other earlier algorithms. Robert Tomasulo received the Eckert–Mauchly Award in 1997 for his work on the algorithm. Implementation concepts The following are the concepts necessary to the implementation of Tomasulo's algorithm: Common data bus The Common Data Bus (CDB) conne ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Out-of-order Execution
In computer engineering, out-of-order execution (or more formally dynamic execution) is an instruction scheduling paradigm used in high-performance central processing units to make use of instruction cycles that would otherwise be wasted. In this paradigm, a processor executes instructions in an order governed by the availability of input data and execution units, rather than by their original order in a program. In doing so, the processor can avoid being idle while waiting for the preceding instruction to complete and can, in the meantime, process the next instructions that are able to run immediately and independently. History Out-of-order execution is a restricted form of dataflow architecture, which was a major research area in computer architecture in the 1970s and early 1980s. Early use in supercomputers The first machine to use out-of-order execution was the CDC 6600 (1964), designed by James E. Thornton, which uses a scoreboard to avoid conflicts. It permits ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Speculative Execution
Speculative execution is an optimization (computer science), optimization technique where a computer system performs some task that may not be needed. Work is done before it is known whether it is actually needed, so as to prevent a delay that would have to be incurred by doing the work after it is known that it is needed. If it turns out the work was not needed after all, most changes made by the work are reverted and the results are ignored. The objective is to provide more Concurrency (computer science), concurrency if extra Resource (computer science), resources are available. This approach is employed in a variety of areas, including branch predictor, branch prediction in instruction pipeline, pipelined CPU, processors, value prediction for exploiting value locality, prefetching Instruction prefetch, memory and File system, files, and optimistic concurrency control in Relational database management system, database systems. Speculative multithreading is a special case of specu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
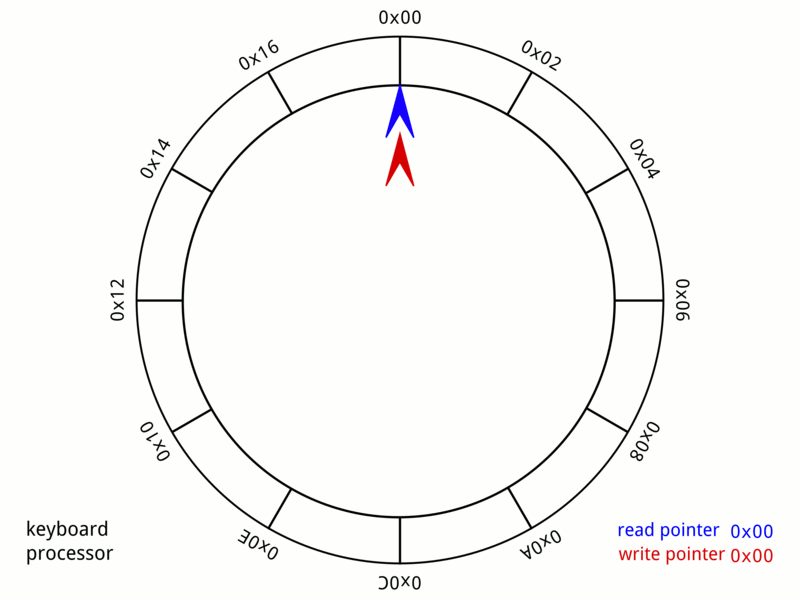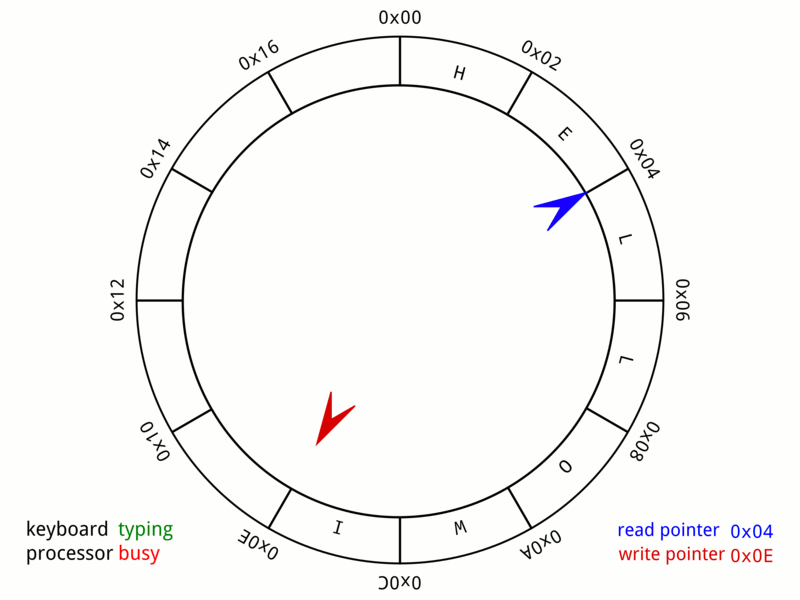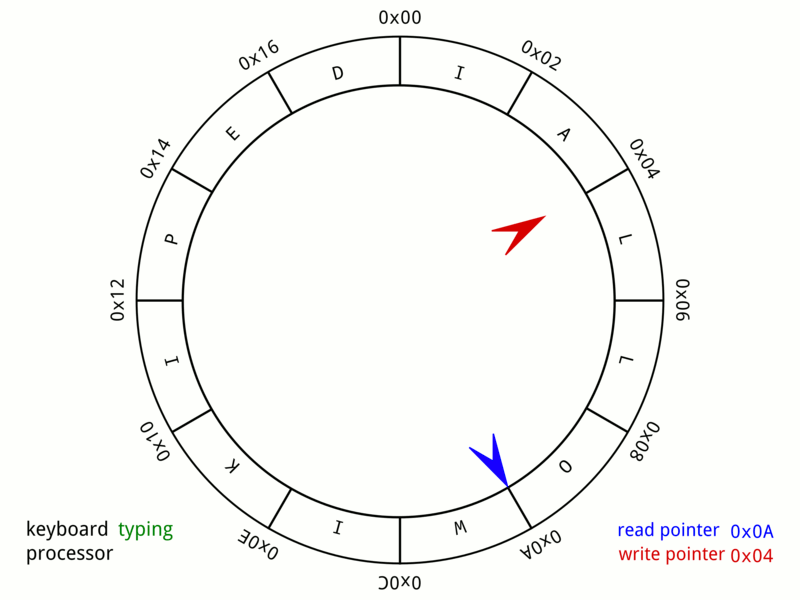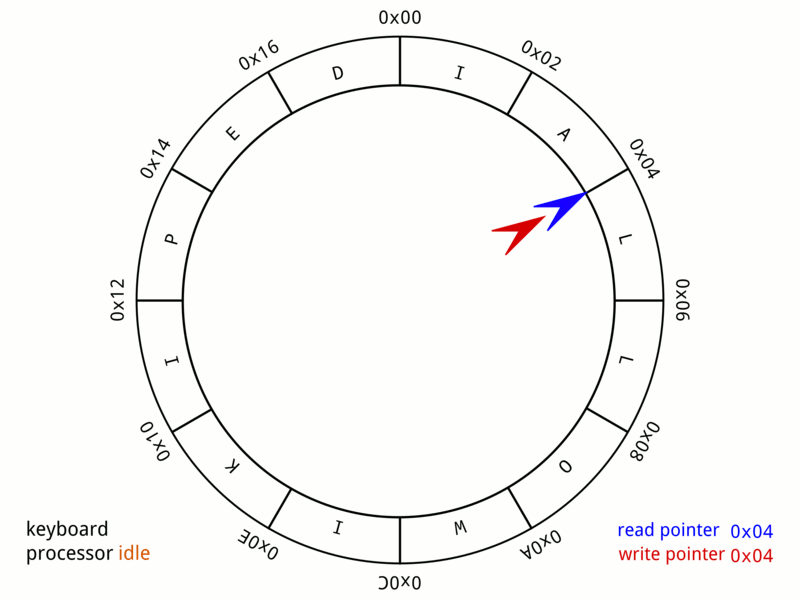
Circular Buffer
In computer science, a circular buffer, circular queue, cyclic buffer or ring buffer is a data structure that uses a single, fixed-size buffer as if it were connected end-to-end. This structure lends itself easily to buffering data streams. There were early circular buffer implementations in hardware. Overview A circular buffer first starts out empty and has a set length. In the diagram below is a 7-element buffer: : Assume that 1 is written in the center of a circular buffer (the exact starting location is not important in a circular buffer): : Then assume that two more elements are added to the circular buffer — 2 & 3 — which get put after 1: : If two elements are removed, the two oldest values inside of the circular buffer would be removed. Circular buffers use FIFO ('' first in, first out'') logic. In the example, 1 & 2 were the first to enter the circular buffer, they are the first to be removed, leaving 3 inside of the buffer. : If the buffer has 7 e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FIFO (computing And Electronics)
Representation of a FIFO queue In computing and in systems theory, first in, first out (the first in is the first out), acronymized as FIFO, is a method for organizing the manipulation of a data structure (often, specifically a data buffer) where the oldest (first) entry, or "head" of the queue, is processed first. Such processing is analogous to servicing people in a queue area on a first-come, first-served (FCFS) basis, i.e. in the same sequence in which they arrive at the queue's tail. FCFS is also the jargon term for the FIFO operating system scheduling algorithm, which gives every process central processing unit (CPU) time in the order in which it is demanded. FIFO's opposite is LIFO, last-in-first-out, where the youngest entry or "top of the stack" is processed first. A priority queue is neither FIFO or LIFO but may adopt similar behaviour temporarily or by default. Queueing theory encompasses these methods for processing data structures, as well as interactions be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Array (data Structure)
In computer science, an array is a data structure consisting of a collection of ''elements'' (value (computer science), values or variable (programming), variables), of same memory size, each identified by at least one ''array index'' or ''key'', a collection of which may be a tuple, known as an index tuple. An array is stored such that the position (memory address) of each element can be computed from its index tuple by a mathematical formula. The simplest type of data structure is a linear array, also called a one-dimensional array. For example, an array of ten 32-bit (4-byte) integer variables, with indices 0 through 9, may be stored as ten Word (data type), words at memory addresses 2000, 2004, 2008, ..., 2036, (in hexadecimal: 0x7D0, 0x7D4, 0x7D8, ..., 0x7F4) so that the element with index ''i'' has the address 2000 + (''i'' × 4). The memory address of the first element of an array is called first address, foundation address, or base address. Because the mathematical conc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reservation Station
A unified reservation station, also known as unified scheduler, is a decentralized feature of the microarchitecture of a CPU that allows for register renaming, and is used by the Tomasulo algorithm for dynamic instruction scheduling. Reservation stations permit the CPU to fetch and re-use a data value as soon as it has been computed, rather than waiting for it to be stored in a register and re-read. When instructions are issued, they can designate the reservation station from which they want their input to read. When multiple instructions need to write to the same register, all can proceed and only the (logically) last one need actually be written. It checks if the operands are available ( RAW) and if execution unit is free ( Structural hazard) before starting execution. Instructions are stored with available parameters, and executed when ready. Results are identified by the unit that will execute the corresponding instruction. Implicitly register renaming solves WAR ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Hazard
Data ( , ) are a collection of discrete or continuous values that convey information, describing the quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted formally. A datum is an individual value in a collection of data. Data are usually organized into structures such as tables that provide additional context and meaning, and may themselves be used as data in larger structures. Data may be used as variables in a computational process. Data may represent abstract ideas or concrete measurements. Data are commonly used in scientific research, economics, and virtually every other form of human organizational activity. Examples of data sets include price indices (such as the consumer price index), unemployment rates, literacy rates, and census data. In this context, data represent the raw facts and figures from which useful information can be extracted. Data are collected using techniques such ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exception Handling
In computing and computer programming, exception handling is the process of responding to the occurrence of ''exceptions'' – anomalous or exceptional conditions requiring special processing – during the execution of a program. In general, an exception breaks the normal flow of execution and executes a pre-registered ''exception handler''; the details of how this is done depend on whether it is a hardware or software exception and how the software exception is implemented. Exceptions are defined by different layers of a computer system, and the typical layers are CPU-defined interrupts, operating system (OS)-defined signals, programming language-defined exceptions. Each layer requires different ways of exception handling although they may be interrelated, e.g. a CPU interrupt could be turned into an OS signal. Some exceptions, especially hardware ones, may be handled so gracefully that execution can resume where it was interrupted. Definition The definition of an excep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rollback (data Management)
In database technologies, a rollback is an operation which returns the database to some previous state. Rollbacks are important for database integrity, because they mean that the database can be restored to a clean copy even after erroneous operations are performed. They are crucial for recovering from database server crashes; by rolling back any transaction which was active at the time of the crash, the database is restored to a consistent state. The rollback feature is usually implemented with a transaction log, but can also be implemented via multiversion concurrency control. Cascading rollback A cascading rollback occurs in database systems when a transaction (T1) causes a failure and a rollback must be performed. Other transactions dependent on T1's actions must also be rollbacked due to T1's failure, thus causing a cascading effect. That is, one transaction's failure causes many to fail. Practical database recovery techniques guarantee cascadeless rollback, therefore a cas ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Branch Target Predictor
In computer architecture, a branch target predictor is the part of a processor that predicts the target, i.e., the address of the instruction that is executed next, of a taken conditional branch or unconditional branch instruction before the target of the branch instruction is computed by the execution unit of the processor. Branch target prediction is not the same as branch prediction, which guesses whether a conditional branch will be taken or not-taken in a binary manner. In more parallel processor designs, as the instruction cache latency grows longer and the fetch width grows wider, branch target extraction becomes a bottleneck. The recurrence is: * Instruction cache fetches block of instructions * Instructions in block are scanned to identify branches * First predicted taken branch is identified * Target of that branch is computed * Instruction fetch restarts at branch target In machines where this recurrence takes two cycles, the machine loses one full cycle of fetch ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |