|
Quantum Money
A quantum money scheme is a quantum cryptographic protocol that creates and verifies banknotes that are resistant to forgery. It is based on the principle that quantum states cannot be perfectly duplicated (the no-cloning theorem), making it impossible to forge quantum money by including quantum systems in its design. The concept was first proposed by Stephen Wiesner circa 1970 (though it remained unpublished until 1983), and later influenced the development of quantum key distribution protocols used in quantum cryptography. Wiesner's quantum money scheme Wiesner's quantum money scheme was first published in 1983. A formal proof of security, using techniques from semidefinite programming, was given in 2013. In addition to a unique serial number on each bank note (these notes are actually more like cheques, since a verification step with the bank is required for each transaction), there is a series of isolated two-state quantum systems.Lo, Spiller & Popescu, ''Introduction to Qua ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quantum Cryptography
Quantum cryptography is the science of exploiting quantum mechanical properties to perform cryptographic tasks. The best known example of quantum cryptography is quantum key distribution which offers an information-theoretically secure solution to the key exchange problem. The advantage of quantum cryptography lies in the fact that it allows the completion of various cryptographic tasks that are proven or conjectured to be impossible using only classical (i.e. non-quantum) communication. For example, it is impossible to copy data encoded in a quantum state. If one attempts to read the encoded data, the quantum state will be changed due to wave function collapse (no-cloning theorem). This could be used to detect eavesdropping in quantum key distribution (QKD). History In the early 1970s, Stephen Wiesner, then at Columbia University in New York, introduced the concept of quantum conjugate coding. His seminal paper titled "Conjugate Coding" was rejected by the IEEE Informati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Forgery
Forgery is a white-collar crime that generally refers to the false making or material alteration of a legal instrument with the specific intent to defraud anyone (other than themself). Tampering with a certain legal instrument may be forbidden by law in some jurisdictions but such an offense is not related to forgery unless the tampered legal instrument was actually used in the course of the crime to defraud another person or entity. Copies, studio replicas, and reproductions are not considered forgeries, though they may later become forgeries through knowing and willful misrepresentations. Forging money or currency is more often called counterfeiting. But consumer goods may also be ''counterfeits'' if they are not manufactured or produced by the designated manufacturer or producer given on the label or flagged by the trademark symbol. When the object forged is a record or document it is often called a false document. This usage of "forgery" does not derive from metalw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
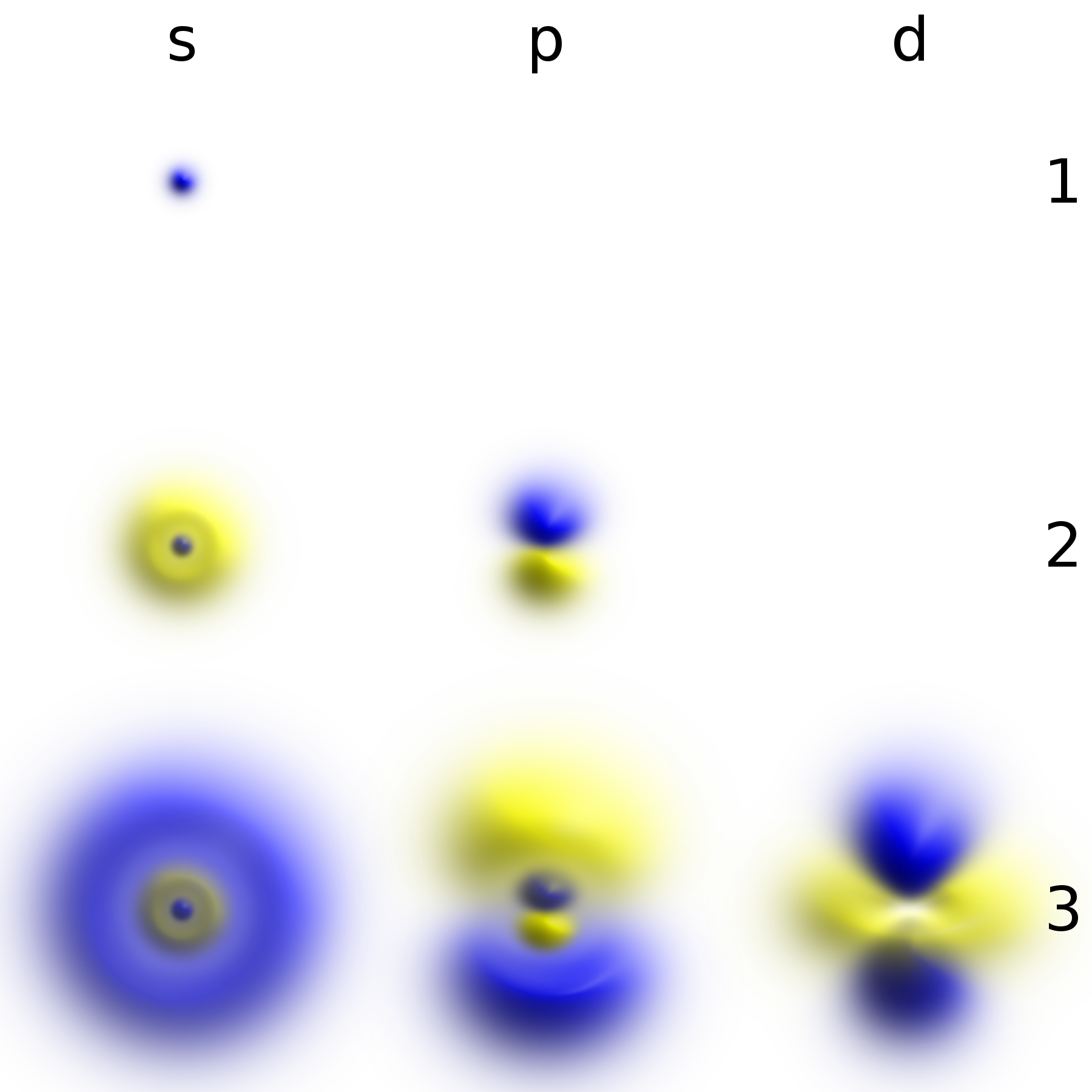
Quantum States
In quantum physics, a quantum state is a mathematical entity that provides a probability distribution for the outcomes of each possible measurement on a system. Knowledge of the quantum state together with the rules for the system's evolution in time exhausts all that can be predicted about the system's behavior. A mixture of quantum states is again a quantum state. Quantum states that cannot be written as a mixture of other states are called pure quantum states, while all other states are called mixed quantum states. A pure quantum state can be represented by a ray in a Hilbert space over the complex numbers, while mixed states are represented by density matrices, which are positive semidefinite operators that act on Hilbert spaces. Pure states are also known as state vectors or wave functions, the latter term applying particularly when they are represented as functions of position or momentum. For example, when dealing with the energy spectrum of the electron in a hydrogen ato ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
No-cloning Theorem
In physics, the no-cloning theorem states that it is impossible to create an independent and identical copy of an arbitrary unknown quantum state, a statement which has profound implications in the field of quantum computing among others. The theorem is an evolution of the 1970 no-go theorem authored by James Park, in which he demonstrates that a non-disturbing measurement scheme which is both simple and perfect cannot exist (the same result would be independently derived in 1982 by Wootters and Zurek as well as Dieks the same year). The aforementioned theorems do not preclude the state of one system becoming entangled with the state of another as cloning specifically refers to the creation of a separable state with identical factors. For example, one might use the controlled NOT gate and the Walsh–Hadamard gate to entangle two qubits without violating the no-cloning theorem as no well-defined state may be defined in terms of a subsystem of an entangled state. The no-cloning ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Stephen Wiesner
Stephen J. Wiesner (1942 – August 12, 2021) was an American-Israeli research physicist, inventor and construction laborer. As a graduate student at Columbia University in New York in the late 1960s and early 1970s, he discovered several of the most important ideas in quantum information theory, including quantum money (which led to quantum key distribution), quantum multiplexing (the earliest example of oblivious transfer) and superdense coding (the first and most basic example of entanglement-assisted communication). Although this work remained unpublished for over a decade, it circulated widely enough in manuscript form to stimulate the emergence of quantum information science in the 1980s and 1990s. Stephen Wiesner is the son of Jerome Wiesner and Laya Wiesner. He received his undergraduate degree from Brandeis University. In 2006 he shared the Rank Prize in Optoelectronics with Charles H. Bennett, and Gilles Brassard for quantum cryptography. In 2019, he received one of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quantum Key Distribution
Quantum key distribution (QKD) is a secure communication method which implements a cryptographic protocol involving components of quantum mechanics. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography, as it is the best-known example of a quantum cryptographic task. An important and unique property of quantum key distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system in general disturbs the system. A third party trying to eavesdrop on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superpositions or quantum entanglement and transmitting information in quantum states, a communication system can be implemented that dete ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quantum Cryptography
Quantum cryptography is the science of exploiting quantum mechanical properties to perform cryptographic tasks. The best known example of quantum cryptography is quantum key distribution which offers an information-theoretically secure solution to the key exchange problem. The advantage of quantum cryptography lies in the fact that it allows the completion of various cryptographic tasks that are proven or conjectured to be impossible using only classical (i.e. non-quantum) communication. For example, it is impossible to copy data encoded in a quantum state. If one attempts to read the encoded data, the quantum state will be changed due to wave function collapse (no-cloning theorem). This could be used to detect eavesdropping in quantum key distribution (QKD). History In the early 1970s, Stephen Wiesner, then at Columbia University in New York, introduced the concept of quantum conjugate coding. His seminal paper titled "Conjugate Coding" was rejected by the IEEE Informati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Semidefinite Programming
Semidefinite programming (SDP) is a subfield of convex optimization concerned with the optimization of a linear objective function (a user-specified function that the user wants to minimize or maximize) over the intersection of the cone of positive semidefinite matrices with an affine space, i.e., a spectrahedron. Semidefinite programming is a relatively new field of optimization which is of growing interest for several reasons. Many practical problems in operations research and combinatorial optimization can be modeled or approximated as semidefinite programming problems. In automatic control theory, SDPs are used in the context of linear matrix inequalities. SDPs are in fact a special case of cone programming and can be efficiently solved by interior point methods. All linear programs and (convex) quadratic programs can be expressed as SDPs, and via hierarchies of SDPs the solutions of polynomial optimization problems can be approximated. Semidefinite programming has been ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quantum Memory
In quantum computing, quantum memory is the quantum-mechanical version of ordinary computer memory. Whereas ordinary memory stores information as binary states (represented by "1"s and "0"s), quantum memory stores a quantum state for later retrieval. These states hold useful computational information known as qubits. Unlike the classical memory of everyday computers, the states stored in quantum memory can be in a quantum superposition, giving much more practical flexibility in quantum algorithms than classical information storage. Quantum memory is essential for the development of many devices in quantum information processing, including a synchronization tool that can match the various processes in a quantum computer, a quantum gate that maintains the identity of any state, and a mechanism for converting predetermined photons into on-demand photons. Quantum memory can be used in many aspects, such as quantum computing and quantum communication. Continuous research and e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quantum Mechanics
Quantum mechanics is a fundamental theory in physics that provides a description of the physical properties of nature at the scale of atoms and subatomic particles. It is the foundation of all quantum physics including quantum chemistry, quantum field theory, quantum technology, and quantum information science. Classical physics, the collection of theories that existed before the advent of quantum mechanics, describes many aspects of nature at an ordinary ( macroscopic) scale, but is not sufficient for describing them at small (atomic and subatomic) scales. Most theories in classical physics can be derived from quantum mechanics as an approximation valid at large (macroscopic) scale. Quantum mechanics differs from classical physics in that energy, momentum, angular momentum, and other quantities of a bound system are restricted to discrete values ( quantization); objects have characteristics of both particles and waves (wave–particle duality); and there are limit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |