|
Private Information Retrieval
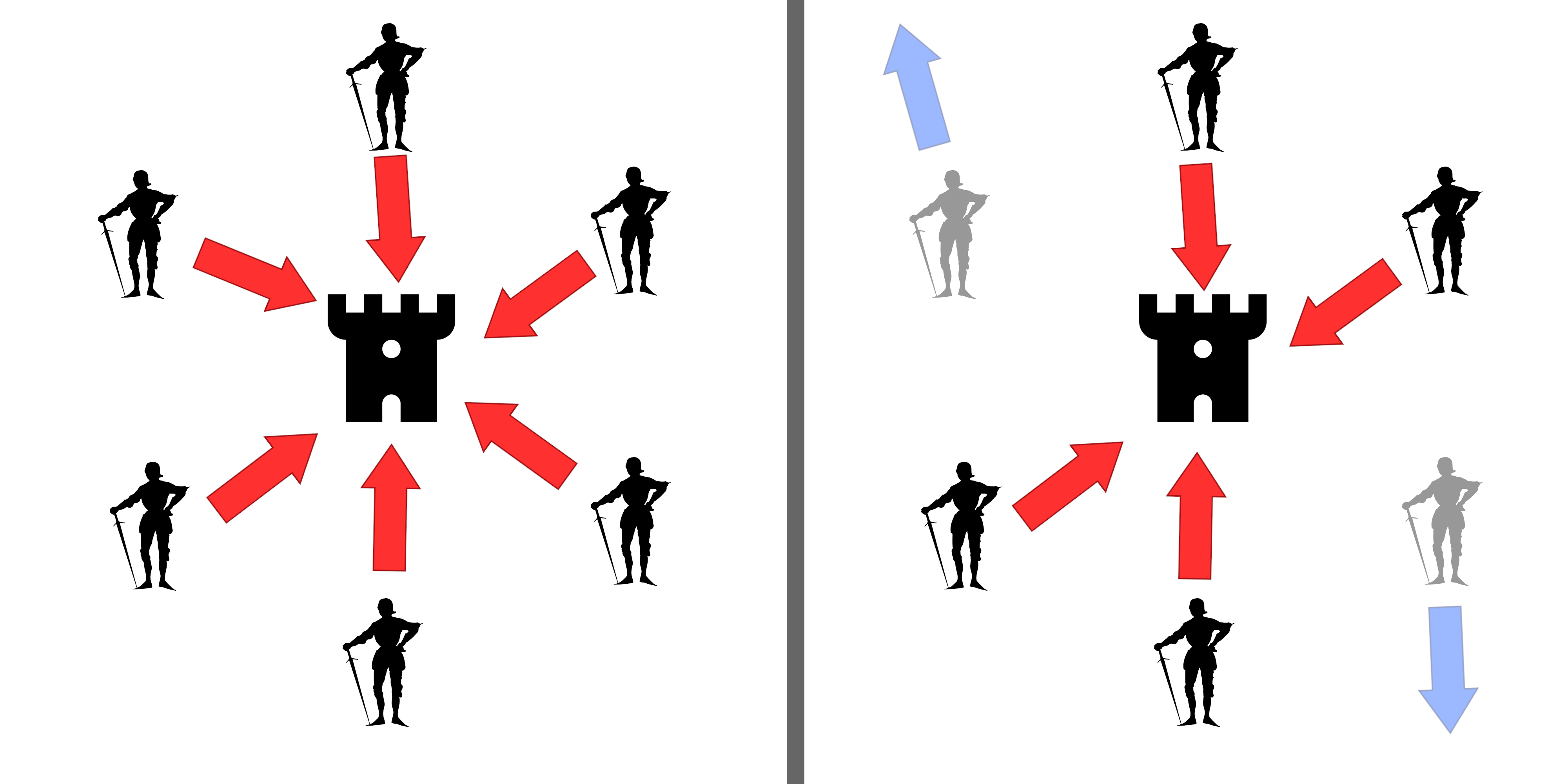
In cryptography, a private information retrieval (PIR) protocol is a protocol that allows a user to retrieve an item from a server in possession of a database without revealing which item is retrieved. PIR is a weaker version of 1-out-of-''n'' oblivious transfer, where it is also required that the user should not get information about other database items. One trivial, but very inefficient way to achieve PIR is for the server to send an entire copy of the database to the user. In fact, this is the only possible protocol (in the classical or the quantum setting) that gives the user information theoretic privacy for their query in a single-server setting. There are two ways to address this problem: make the server computationally bounded or assume that there are multiple non-cooperating servers, each having a copy of the database. The problem was introduced in 1995 by Chor, Goldreich, Kushilevitz and Sudan in the information-theoretic setting and in 1997 by Kushilevitz and Ostrovs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from grc, , translit=kryptós "hidden, secret"; and ''graphein'', "to write", or ''-logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More generally, cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, chip-based payment cards, digital currencies, computer passwords, and military communications. Cryptography prior to the modern age was effectively synony ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Yuval Ishai
Yuval ( he, יוּבַל), also known as Kfar Yuval ( he, כְּפַר יוּבַל), is a moshav in northern Israel. Located in the Galilee Panhandle between Metula and Kiryat Shmona, it falls under the jurisdiction of Mevo'ot HaHermon Regional Council. In it had a population of . History The moshav was founded in 1953 by evacuees from the Old City of Jerusalem who originally arrived from Kurdistan on land that had belonged to the depopulated Palestinian village of Abil al-Qamh. It was named "Yuval" (creek) after the Jordan river's tributaries in the area and also referring to Jeremiah 17:8 ("sends out its roots by the creek"). In the early 1960s most of the founders abandoned the moshav, and it was repopulated by Indian Jewish immigrants from Kochi. The proximity of the moshav to the border of Israel with Lebanon has made it a target for terrorist attacks. In 1975 a group of terrorists infiltrated the moshav, took control of a residence, and killed three members of one f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tal Malkin
Tal Geula Malkin (born 1970) is an Israeli-American cryptographer who works as a professor of computer science at Columbia University, where she heads the Cryptography Lab and the Data Science Institute Cybersecurity Center. Education and career Malkin graduated summa cum laude from Bar-Ilan University in 1993, with a bachelor's degree in mathematics and computer science. She earned a master's degree in computer science from Weizmann Institute of Science in 1995, with the master's thesis ''Deductive Tableaux for Temporal Logic'' supervised by Amir Pnueli, and completed a Ph.D. in 2000 at the Massachusetts Institute of Technology with the dissertation ''A Study of Secure Database Access and General Two-Party Computation'' supervised by Shafi Goldwasser. As a doctoral student, she also worked as an intern for IBM Research at the Thomas J. Watson Research Center, and as a research scientist for AT&T Labs, continuing there through 2002. In 2003 she joined Columbia University as an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Giovanni Di Crescenzo
Giovanni may refer to: * Giovanni (name), an Italian male given name and surname * Giovanni (meteorology), a Web interface for users to analyze NASA's gridded data * ''Don Giovanni'', a 1787 opera by Wolfgang Amadeus Mozart, based on the legend of Don Juan * Giovanni (Pokémon), boss of Team Rocket in the fictional world of Pokémon * Giovanni (World of Darkness), a group of vampires in ''Vampire: The Masquerade/World of Darkness'' roleplay and video game * "Giovanni", a song by Band-Maid from the 2021 album ''Unseen World'' * ''Giovanni's Island'', a 2014 Japanese anime drama film * ''Giovanni's Room'', a 1956 novel by James Baldwin * Via Giovanni, places in Rome See also * * *Geovani *Giovanni Battista *San Giovanni (other) *San Giovanni Battista (other) San Giovanni Battista is the Italian translation of Saint John the Baptist. It may also refer to: Italian churches * San Giovanni Battista, Highway A11, a church in Florence, Italy * San Giovanni Battista, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
One-way Function
In computer science, a one-way function is a function that is easy to compute on every input, but hard to invert given the image of a random input. Here, "easy" and "hard" are to be understood in the sense of computational complexity theory, specifically the theory of polynomial time problems. Not being one-to-one is not considered sufficient for a function to be called one-way (see Theoretical definition, below). The existence of such one-way functions is still an open conjecture. Their existence would prove that the complexity classes P and NP are not equal, thus resolving the foremost unsolved question of theoretical computer science.Oded Goldreich (2001). Foundations of Cryptography: Volume 1, Basic Tools,draft availablefrom author's site). Cambridge University Press. . (see als The converse is not known to be true, i.e. the existence of a proof that P≠NP would not directly imply the existence of one-way functions. In applied contexts, the terms "easy" and "hard" are us ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SourceForge
SourceForge is a web service that offers software consumers a centralized online location to control and manage open-source software projects and research business software. It provides source code repository hosting, bug tracking, mirroring of downloads for load balancing, a wiki for documentation, developer and user mailing lists, user-support forums, user-written reviews and ratings, a news bulletin, micro-blog for publishing project updates, and other features. SourceForge was one of the first to offer this service free of charge to open-source projects. Since 2012, the website has run on Apache Allura software. SourceForge offers free hosting and free access to tools for developers of free and open-source software. , the SourceForge repository claimed to host more than 502,000 projects and had more than 3.7 million registered users. Concept SourceForge is a web-based source code repository. It acts as a centralized location for free and open-source softwar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shamir's Secret Sharing
Shamir's Secret Sharing (SSS) is an efficient secret sharing algorithm for distributing private information (the "secret") in such a way that no individual holds intelligible information about the secret. To achieve this, the secret is converted into parts (the "shares") from which the secret can be reassembled when a sufficient number of shares are combined but not otherwise. SSS has the unusual property of information theoretic security, meaning an adversary without enough shares cannot reconstruct the secret even with infinite time and computing capacity. A standard SSS specification for cryptocurrency wallets has been widely implemented. High-level explanation SSS is used to secure a secret in a distributed way, most often to secure other encryption keys. The secret is split into multiple shares, which individually do not give any information about the secret. To unlock a secret secured by SSS a minimum number of shares are needed, called the ''threshold''. No additional ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nadia Heninger
Nadia Heninger (born 1982) is an American cryptographer, computer security expert, and computational number theorist at the University of California, San Diego. Contributions Heninger is known for her work on freezing powered-down security devices to slow their fading memories and allow their secrets to be recovered via a cold boot attack, for her discovery that weak keys for the RSA cryptosystem are in widespread use by internet routers and other embedded devices, for her research on how failures of forward secrecy in bad implementations of the Diffie–Hellman key exchange may have allowed the National Security Agency to decrypt large amounts of internet traffic via the Logjam vulnerability, and for the DROWN attack, which uses servers supporting old and weak cryptography to decrypt traffic from modern clients to modern servers. Heninger's other research contributions include a variant of the RSA cryptosystem that would be secure against quantum computers, an attack on implem ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Byzantine Fault Tolerance
A Byzantine fault (also Byzantine generals problem, interactive consistency, source congruency, error avalanche, Byzantine agreement problem, and Byzantine failure) is a condition of a computer system, particularly distributed computing systems, where components may fail and there is imperfect information on whether a component has failed. The term takes its name from an allegory, the "Byzantine generals problem", developed to describe a situation in which, in order to avoid catastrophic failure of the system, the system's actors must agree on a concerted strategy, but some of these actors are unreliable. In a Byzantine fault, a component such as a server can inconsistently appear both failed and functioning to failure-detection systems, presenting different symptoms to different observers. It is difficult for the other components to declare it failed and shut it out of the network, because they need to first reach a consensus regarding which component has failed in the first p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Goldwasser–Micali Cryptosystem
The Goldwasser–Micali (GM) cryptosystem is an asymmetric key encryption algorithm developed by Shafi Goldwasser and Silvio Micali in 1982. GM has the distinction of being the first probabilistic public-key encryption scheme which is provably secure under standard cryptographic assumptions. However, it is not an efficient cryptosystem, as ciphertexts may be several hundred times larger than the initial plaintext. To prove the security properties of the cryptosystem, Goldwasser and Micali proposed the widely used definition of semantic security. Basis The GM cryptosystem is semantically secure based on the assumed intractability of the quadratic residuosity problem modulo a composite ''N'' = ''pq'' where ''p, q'' are large primes. This assumption states that given (''x'', ''N'') it is difficult to determine whether ''x'' is a quadratic residue modulo ''N'' (i.e., ''x'' = ''y''2 mod ''N'' for some ''y''), when the Jacobi symbol for ''x'' is +1. The quadratic residue pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Homomorphic Encryption
Homomorphic encryption is a form of encryption that permits users to perform computations on its encrypted data without first decrypting it. These resulting computations are left in an encrypted form which, when decrypted, result in an identical output to that produced had the operations been performed on the unencrypted data. Homomorphic encryption can be used for privacy-preserving outsourced storage and computation. This allows data to be encrypted and out-sourced to commercial cloud environments for processing, all while encrypted. For sensitive data, such as health care information, homomorphic encryption can be used to enable new services by removing privacy barriers inhibiting data sharing or increase security to existing services. For example, predictive analytics in health care can be hard to apply via a third party service provider due to medical data privacy concerns, but if the predictive analytics service provider can operate on encrypted data instead, these pri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |