|
Point To Point Encryption
Point-to-point encryption (P2PE) is a standard established by the PCI Security Standards Council. The objective of P2PE is to provide a payment security solution that instantaneously converts confidential payment card (credit and debit card) data and information into indecipherable code at the time the card is swiped, in order to prevent hacking and fraud. It is designed to maximize the security of payment card transactions in an increasingly complex regulatory environment. There also exist payment solutions based on end-to-end encryption, implying the highest level of confidentiality for the transferred data. The standard The P2PE Standard defines the requirements that a "solution" must meet in order to be accepted as a PCI-validated P2PE solution. A "solution" is a complete set of hardware, software, gateway, decryption, device handling, etc. Only "solutions" can be validated; individual pieces of hardware such as card readers cannot be validated. It is also a common mis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PCI Security Standards Council
The payment card industry (PCI) denotes the debit, credit, prepaid, e-purse, ATM, and POS cards and associated businesses. Overview The payment card industry consists of all the organizations which store, process and transmit cardholder data, most notably for debit cards and credit cards. The security standards are developed by the Payment Card Industry Security Standards Council which develops the Payment Card Industry Data Security Standards used throughout the industry. Individual card brands establish compliance requirements that are used by service providers and have their own compliance programs. Major card brands include American Express, Discover Card, JCB, Mastercard, Mir, RuPay, UnionPay and Visa. Most companies use member banks that connect and accept transactions from the card brands. Not all card brands use member banks, like American Express, these instead act as their own bank. , the United States uses a magnetic stripe on a card to process transactions ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security
Information security is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized or inappropriate access to data or the unlawful use, Data breach, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g., electronic or physical, tangible (e.g., Document, paperwork), or intangible (e.g., knowledge). Information security's primary focus is the balanced protection of data confidentiality, data integrity, integrity, and data availability, availability (also known as the 'CIA' triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process. To stand ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Confidentiality
Confidentiality involves a set of rules or a promise sometimes executed through confidentiality agreements that limits the access to or places restrictions on the distribution of certain types of information. Legal confidentiality By law, lawyers are often required to keep confidential anything on the representation of a client. The duty of confidentiality is much broader than the attorney–client evidentiary privilege, which only covers ''communications'' between the attorney and the client. Both the privilege and the duty serve the purpose of encouraging clients to speak frankly about their cases. This way, lawyers can carry out their duty to provide clients with zealous representation. Otherwise, the opposing side may be able to surprise the lawyer in court with something he did not know about his client, which may weaken the client's position. Also, a distrustful client might hide a relevant fact he thinks is incriminating, but that a skilled lawyer could turn to the cl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Debit Card
A debit card, also known as a check card or bank card, is a payment card that can be used in place of cash to make purchases. The card usually consists of the bank's name, a card number, the cardholder's name, and an expiration date, on either the front or the back. Many new cards now have a chip on them, which allows people to use their card by touch (contactless), or by inserting the card and keying in a PIN as with swiping the magnetic stripe. Debit cards are similar to a credit card, but the money for the purchase must be in the cardholder's bank account at the time of the purchase and is immediately transferred directly from that account to the merchant's account to pay for the purchase. Some debit cards carry a Stored-value card, stored value with which a payment is made (prepaid cards), but most relay a message to the cardholder's bank to withdraw funds from the cardholder's designated bank account. In some cases, the payment card number is assigned exclusively for use on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Hacker
A security hacker or security researcher is someone who explores methods for breaching or bypassing defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, sabotage, information gathering, challenge, recreation, or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. Longstanding controversy surrounds the meaning of the term "hacker". In this controversy, computer programmers reclaim the term ''hacker'', arguing that it refers simply to someone with an advanced understanding of computers and computer networks, and that ''cracker'' is the more appropriate term for those who break into computers, whether computer criminals ( black hats) or computer security experts ( white hats). A 2014 article noted that "the black-hat meaning still prevails among the general public". The subculture that has evolved around hackers is often referred to as the "co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fraud
In law, fraud is intent (law), intentional deception to deprive a victim of a legal right or to gain from a victim unlawfully or unfairly. Fraud can violate Civil law (common law), civil law (e.g., a fraud victim may sue the fraud perpetrator to avoid the fraud or recover monetary compensation) or criminal law (e.g., a fraud perpetrator may be prosecuted and imprisoned by governmental authorities), or it may cause no loss of money, property, or legal right but still be an element of another civil or criminal wrong. The purpose of fraud may be monetary gain or other benefits, such as obtaining a passport, travel document, or driver's licence. In cases of mortgage fraud, the perpetrator may attempt to qualify for a mortgage by way of false statements. Terminology Fraud can be defined as either a civil wrong or a criminal act. For civil fraud, a government agency or person or entity harmed by fraud may bring litigation to stop the fraud, seek monetary damages, or both. For cr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
End-to-end Encryption
End-to-end encryption (E2EE) is a method of implementing a secure communication system where only communicating users can participate. No one else, including the system provider, telecom providers, Internet providers or malicious actors, can access the cryptographic keys needed to read or send messages. End-to-end encryption prevents data from being read or secretly modified, except by the true sender and intended recipients. Frequently, the messages are relayed from the sender to the recipients by a service provider. However, messages are encrypted by the sender and no third party, including the service provider, has the means to decrypt them. The recipients retrieve the encrypted messages and decrypt them independently. Since third parties cannot decrypt the data being communicated or stored, services that provide end-to-end encryption are better at protecting user data when they are affected by data breaches. Such services are also unable to share user data with governm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Point Of Interaction
The point of sale (POS) or point of purchase (POP) is the time and place at which a retail transaction is completed. At the point of sale, the merchant calculates the amount owed by the customer, indicates that amount, may prepare an invoice for the customer (which may be a cash register printout), and indicates the options for the customer to make payment. It is also the point at which a customer makes a payment to the merchant in exchange for goods or after provision of a service. After receiving payment, the merchant may issue a receipt, as proof of transaction, which is usually printed but can also be dispensed with or sent electronically. To calculate the amount owed by a customer, the merchant may use various devices such as weighing scales, barcode scanners, and cash registers (or the more advanced "POS cash registers", which are sometimes also called "POS systems"). To make a payment, payment terminals, touch screens, and other hardware and software options are avail ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
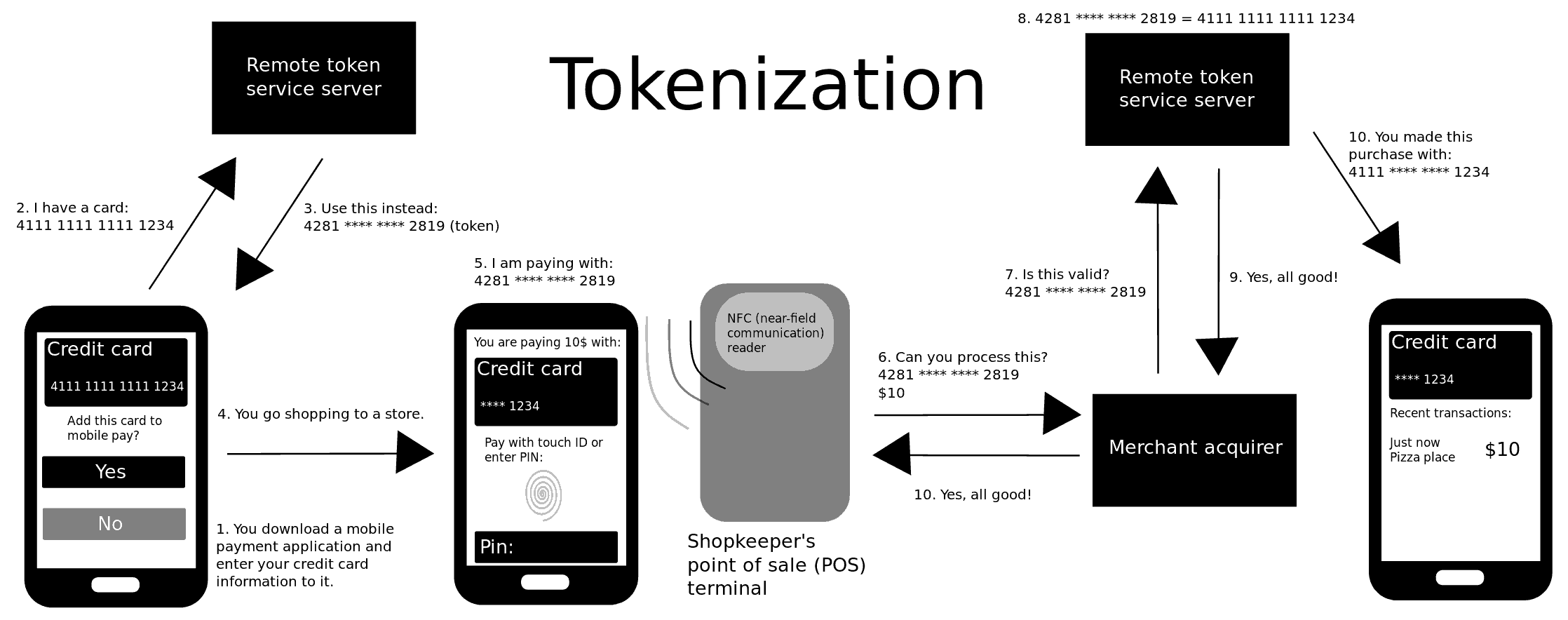
Tokenization (data Security)
Tokenization, when applied to data security, is the process of substituting a sensitive data element with a non-sensitive equivalent, referred to as a Security token, token, that has no intrinsic or exploitable meaning or value. The token is a reference (i.e. identifier) that maps back to the sensitive data through a tokenization system. The mapping from original data to a token uses methods that render tokens infeasible to reverse in the absence of the tokenization system, for example using tokens created from Random number generation, random numbers. A one-way cryptographic function is used to convert the original data into tokens, making it difficult to recreate the original data without obtaining entry to the tokenization system's resources. To deliver such services, the system maintains a vault database of tokens that are connected to the corresponding sensitive data. Protecting the system vault is vital to the system, and improved processes must be put in place to offer dat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Payment Card Industry Data Security Standard
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard used to handle credit cards from major card brands. The standard is administered by the Payment Card Industry Security Standards Council, and its use is mandated by the card brands. It was created to better control cardholder data and reduce credit card fraud. Validation of compliance is performed annually or quarterly with a method suited to the volume of transactions: * Self-assessment questionnaire (SAQ) * Firm-specific Internal Security Assessor (ISA) * External Qualified Security Assessor (QSA) History The major card brands had five different security programs: * Visa's Cardholder Information Security Program * Mastercard's Site Data Protection *American Express's Data Security Operating Policy * Discover's Information Security and Compliance * JCB's Data Security Program The intentions of each were roughly similar: to create an additional level of protection for card issuers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |