|
Personal Data
Personal data, also known as personal information or personally identifiable information (PII), is any information related to an identifiable person. The abbreviation PII is widely used in the United States, but the phrase it abbreviates has four common variants based on ''personal'' or ''personally'', and ''identifiable'' or ''identifying''. Not all are equivalent, and for legal purposes the effective definitions vary depending on the jurisdiction and the purposes for which the term is being used. Under European Union and United Kingdom data protection regimes, which centre primarily on the General Data Protection Regulation (GDPR), the term "personal data" is significantly broader, and determines the scope of the regulatory regime. National Institute of Standards and Technology Special Publication 800-122 defines personally identifiable information as "any information about an individual maintained by an agency, including (1) any information that can be used to distinguish or t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
United States
The United States of America (USA), also known as the United States (U.S.) or America, is a country primarily located in North America. It is a federal republic of 50 U.S. state, states and a federal capital district, Washington, D.C. The 48 contiguous states border Canada to the north and Mexico to the south, with the semi-exclave of Alaska in the northwest and the archipelago of Hawaii in the Pacific Ocean. The United States asserts sovereignty over five Territories of the United States, major island territories and United States Minor Outlying Islands, various uninhabited islands in Oceania and the Caribbean. It is a megadiverse country, with the world's List of countries and dependencies by area, third-largest land area and List of countries and dependencies by population, third-largest population, exceeding 340 million. Its three Metropolitan statistical areas by population, largest metropolitan areas are New York metropolitan area, New York, Greater Los Angeles, Los Angel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Office Of Management And Budget
The Office of Management and Budget (OMB) is the largest office within the Executive Office of the President of the United States (EOP). The office's most prominent function is to produce the president's budget, while it also examines agency programs, policies, and procedures to see whether they comply with the president's policies and coordinates inter-agency policy initiatives. Russell Vought is the current director of the OMB since February 2025. History The Bureau of the Budget, OMB's predecessor, was established in 1921 as a part of the United States Department of the Treasury, Department of the Treasury by the Budget and Accounting Act of 1921, which President Warren G. Harding signed into law. The Bureau of the Budget was moved to the Executive Office of the President of the United States, Executive Office of the President in 1939 and was run by Harold D. Smith during the government's rapid expansion of spending during World War II. James L. Sundquist, a staffer at the B ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privacy Act (Canada)
The ''Privacy Act'' () is the federal information-privacy legislation of Canada that came into effect on July 1, 1983. Administered by the Privacy Commissioner of Canada, the Act sets out rules for how institutions of the Government of Canada collect, use, disclose, retain, and dispose of personal information of individuals. The Act does not apply to political parties, political representatives (i.e., members of Parliament and senators), courts, and private sector organizations. All provinces and territories have their own laws governing their public sectors. Overview Some salient provisions of the legislation are as follows: * A government institution may not collect personal information unless it relates directly to an operating program or activity of the institution (section 4). * With some exceptions, when a government institution collects an individual's personal information from the individual, it must inform the individual of the purpose for which the informatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Psychographic Profile
Psychographics is defined as "market research or statistics classifying population groups according to psychological variables" The term psychographics is derived from the words "psychological" and "demographics" Two common approaches to psychographics include analysis of consumers' activities, interests, and opinions (AIO variables), and values and lifestyles (VALS). Psychographics have been applied to the study of personality, values, opinions, attitudes, interests, and lifestyles. Psychographic segmentation is a technique for grouping populations into sub-groups according to similar psychological variables. Psychographic studies of individuals or communities can be valuable in the fields of marketing, demographics, opinion research, prediction, and social research in general. Psychographic attributes can be contrasted with demographic variables (such as age and gender), behavioral variables (such as purchase data or usage rate), and organizational descriptors (sometimes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Bug
A web beaconAlso called web bug, tracking bug, tag, web tag, page tag, tracking pixel, pixel tag, 1×1 GIF, spy pixel, or clear GIF. is a technique used on web pages and email to unobtrusively (usually invisibly) allow checking that a user has accessed some content. Web beacons are typically used by third parties to monitor the activity of users at a website for the purpose of web analytics or page tagging. They can also be used for email tracking. When implemented using JavaScript, they may be called JavaScript tags. Web beacons are unseen HTML elements that track a webpage views. Upon the user revisiting the webpage, these beacons are connected to cookies established by the server, facilitating undisclosed user tracking. Using such beacons, companies and organizations can track the online behavior of web users. At first, the companies doing such tracking were mainly advertisers or web analytics companies; later social media sites also started to use such tracking techniques, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Behavioral Advertising
Targeted advertising or data-driven marketing is a form of advertising, including online advertising, that is directed towards an audience with certain traits, based on the product or person the advertiser is promoting. These traits can either be demographic with a focus on race, economic status, sex, age, generation, level of education, income level, and employment, or psychographic focused on the consumer values, personality, attitude, opinion, lifestyle, and interests. This focus can also entail behavioral variables, such as browser history, purchase history, and other recent online activities. The process of algorithm targeting eliminates waste. Traditional forms of advertising, including billboards, newspapers, magazines, and radio channels, are progressively becoming replaced by online advertisements. Through the emergence of new online channels, the usefulness of targeted advertising is increasing because companies aim to minimize wasted advertising. Most targeted n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privacy Act 1988
The ''Privacy Act 1988'' is an Australian law dealing with privacy. Section 14 of the Act stipulates a number of privacy rights known as the Australian Privacy Principles (APPs). These principles apply to Australian Government and Australian Capital Territory agencies or private sector organizations contracted to these governments, organizations and small businesses who provide a health service, as well as to private organizations with an annual turnover exceeding AUD$3M (with some specific exceptions). The principles govern when and how personal information can be collected by these entities. Information can only be collected if it is relevant to the agencies' functions. Upon this collection, that law mandates that Australians have the right to know why information about them is being acquired and who will see the information. Those in charge of storing the information have obligations to ensure such information is neither lost nor exploited. An Australian will also have the ri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
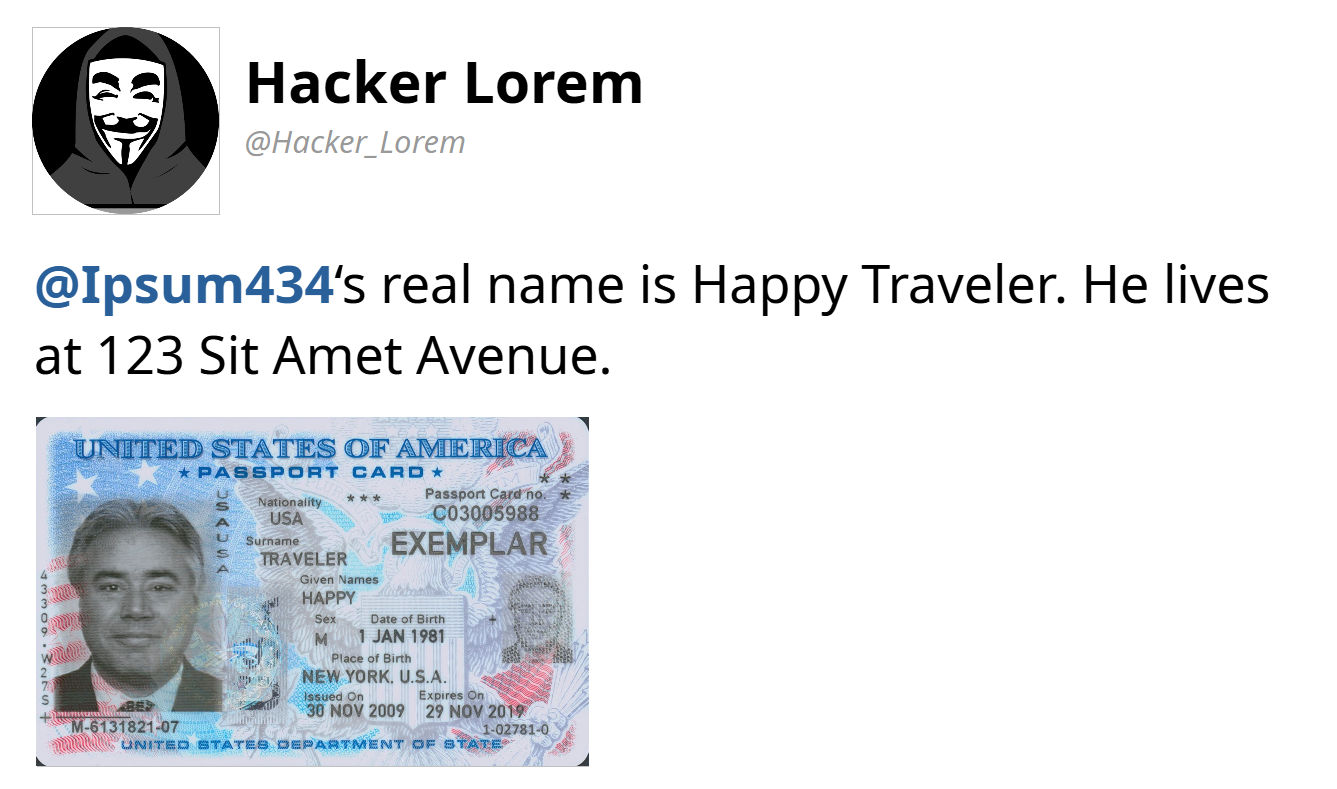
Doxing
Doxing or doxxing is the act of publicly providing personally identifiable information Personal data, also known as personal information or personally identifiable information (PII), is any information related to an identifiable person. The abbreviation PII is widely used in the United States, but the phrase it abbreviates has fou ... about an individual or organization, usually via the Internet and without their consent. Historically, the term has been used to refer to both the aggregation of this information from public databases and social media websites (like Facebook), and the publication of previously private information obtained through criminal or otherwise fraudulent means (such as hacker (computer security), hacking and social engineering (security), social engineering). The aggregation and provision of previously published material is generally legal, though it may be subject to laws concerning stalking and intimidation. Doxing may be carried out for reasons such ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker (computer Security)
A security hacker or security researcher is someone who explores methods for breaching or bypassing defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, sabotage, information gathering, challenge, recreation, or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. Longstanding controversy surrounds the meaning of the term "hacker". In this controversy, computer programmers reclaim the term ''hacker'', arguing that it refers simply to someone with an advanced understanding of computers and computer networks, and that ''cracker'' is the more appropriate term for those who break into computers, whether computer criminals ( black hats) or computer security experts ( white hats). A 2014 article noted that "the black-hat meaning still prevails among the general public". The subculture that has evolved around hackers is often referred to as the "co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Health Data
Health data is any data "related to health conditions, reproductive outcomes, Cause of death, causes of death, and Quality of life (healthcare), quality of life" for an individual or population. Health data includes clinical metrics along with environmental, socioeconomic, and behavioral information pertinent to health and wellness. A plurality of health data are collected and used when individuals interact with Health system, health care systems. This data, collected by health care providers, typically includes a record of services received, conditions of those services, and clinical outcomes or information concerning those services. Historically, most health data has been sourced from this framework. The advent of eHealth and advances in health information technology, however, have expanded the collection and use of health data—but have also engendered new security, privacy, and ethical concerns. The increasing collection and use of health data by patients is a maj ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |