|
Penny Black (research Project)
The Penny Black Project is a Microsoft Research project that tries to find effective and practical ways of fighting spam. Because identifying spams consumes a recipient's time, the idea is to make the sender of emails "pay" a certain amount for sending them. The currency or the mode of payment could be CPU cycles, Turing tests or memory cycles. Such a payment would limit spammers' ability to send out large quantities of emails quickly. The project's name is derived from the Penny Black, the world's first adhesive stamp used for prepaid postage. Objective The goal of the project is to move the e-mail costs from the receiver to the sender. The general idea is that if the sender must prove that they have expended a certain amount of effort specifically for the receiver and the message alone. The project aims to devise a method to do this without introducing additional challenge-response mechanisms and third parties, and without requiring extra maintenance and updates, while retainin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Research
Microsoft Research (MSR) is the research subsidiary of Microsoft. It was created in 1991 by Richard Rashid, Bill Gates and Nathan Myhrvold with the intent to advance state-of-the-art computing and solve difficult world problems through technological innovation in collaboration with academic, government, and industry researchers. The Microsoft Research team has more than 1,000 computer scientists, physicists, engineers, and mathematicians, including Turing Award winners, Fields Medal winners, MacArthur Fellows, and Dijkstra Prize winners. Between 2010 and 2018, 154,000 AI patents were filed worldwide, with Microsoft having by far the largest percentage of those patents, at 20%.Louis Columbus, January 6, 201Microsoft Leads The AI Patent Race Going Into 2019 ''Forbes'' According to estimates in trade publications, Microsoft spent about $6 billion annually in research initiatives from 2002-2010 and has spent from $10–14 billion annually since 2010. Microsoft Research has made signi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spam (e-mail)
Email spam, also referred to as junk email, spam mail, or simply spam, is unsolicited messages sent in bulk by email (spamming). The name comes from a Monty Python sketch in which the name of the canned pork product Spam is ubiquitous, unavoidable, and repetitive. Email spam has steadily grown since the early 1990s, and by 2014 was estimated to account for around 90% of total email traffic. Since the expense of the spam is borne mostly by the recipient, it is effectively postage due advertising. This makes it an excellent example of a negative externality. The legal definition and status of spam varies from one jurisdiction to another, but nowhere have laws and lawsuits been particularly successful in stemming spam. Most email spam messages are commercial in nature. Whether commercial or not, many are not only annoying as a form of attention theft, but also dangerous because they may contain links that lead to phishing web sites or sites that are hosting malware or include m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
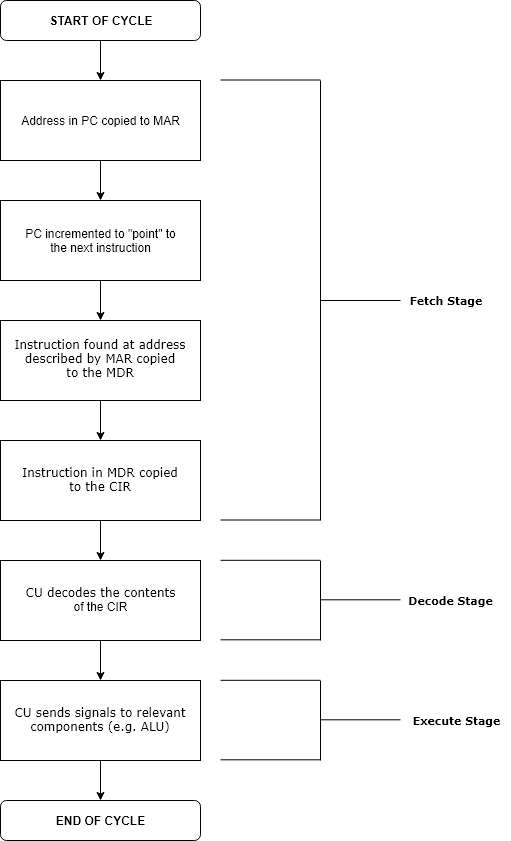
CPU Cycle
The instruction cycle (also known as the fetch–decode–execute cycle, or simply the fetch-execute cycle) is the cycle that the central processing unit (CPU) follows from boot-up until the computer has shut down in order to process instructions. It is composed of three main stages: the fetch stage, the decode stage, and the execute stage. In simpler CPUs, the instruction cycle is executed sequentially, each instruction being processed before the next one is started. In most modern CPUs, the instruction cycles are instead executed concurrently, and often in parallel, through an instruction pipeline: the next instruction starts being processed before the previous instruction has finished, which is possible because the cycle is broken up into separate steps. Role of components The program counter (PC) is a special register that holds the memory address of the next instruction to be executed. During the fetch stage, the address stored in the PC is copied into the memory addres ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Turing Test
The Turing test, originally called the imitation game by Alan Turing in 1950, is a test of a machine's ability to artificial intelligence, exhibit intelligent behaviour equivalent to, or indistinguishable from, that of a human. Turing proposed that a human evaluator would judge natural language conversations between a human and a machine designed to generate human-like responses. The evaluator would be aware that one of the two partners in conversation was a machine, and all participants would be separated from one another. The conversation would be limited to a text-only channel, such as a computer keyboard and screen, so the result would not depend on the machine's ability to render words as speech. If the evaluator could not reliably tell the machine from the human, the machine would be said to have passed the test. The test results would not depend on the machine's ability to give correct question answering, answers to questions, only on how closely its answers resembled t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Memory Cycle
Memory is the faculty of the mind by which data or information is encoded, stored, and retrieved when needed. It is the retention of information over time for the purpose of influencing future action. If past events could not be remembered, it would be impossible for language, relationships, or personal identity to develop. Memory loss is usually described as forgetfulness or amnesia. Memory is often understood as an informational processing system with explicit and implicit functioning that is made up of a sensory processor, short-term (or working) memory, and long-term memory. This can be related to the neuron. The sensory processor allows information from the outside world to be sensed in the form of chemical and physical stimuli and attended to various levels of focus and intent. Working memory serves as an encoding and retrieval processor. Information in the form of stimuli is encoded in accordance with explicit or implicit functions by the working memory processor. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Penny Black
The Penny Black was the world's first adhesive postage stamp used in a public postal system. It was first issued in the United Kingdom (referred to in philatelic circles as Great Britain), on 1 May 1840, but was not valid for use until 6 May. The stamp features a profile of Queen Victoria. In 1837, British postal rates were high, complex and anomalous. To simplify matters, Sir Rowland Hill proposed an adhesive stamp to indicate pre-payment of postage. At the time it was normal for the recipient to pay postage on delivery, charged by the sheet and on distance travelled. By contrast, the Penny Black allowed letters of up to to be delivered at a flat rate of one penny, regardless of distance. Treasury competition On 13 February 1837, Sir Rowland Hill proposed to a government enquiry both the idea of a pre-paid stamp and a pre-paid envelope, a separate sheet folded to form an enclosure for carrying letters. Hill was given a two-year contract to run the new system, and tog ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proof Of Work
Proof of work (PoW) is a form of Cryptography, cryptographic proof (truth), proof in which one party (the ''prover'') proves to others (the ''verifiers'') that a certain amount of a specific computational effort has been expended. Verifiers can subsequently confirm this expenditure with minimal effort on their part. The concept was invented by Moni Naor and Cynthia Dwork in 1993 as a way to deter denial-of-service attacks and other service abuses such as spam (electronic), spam on a network by requiring some work from a service requester, usually meaning processing time by a computer. The term "proof of work" was first coined and formalized in a 1999 paper by Markus Jakobsson and Ari Juels. Proof of work was later popularized by Bitcoin as a foundation for Consensus (computer science), consensus in a permissionless decentralized network, in which miners compete to append blocks and mint new currency, each miner experiencing a success probability proportional to the computationa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proof-of-work System
Proof of work (PoW) is a form of cryptographic proof in which one party (the ''prover'') proves to others (the ''verifiers'') that a certain amount of a specific computational effort has been expended. Verifiers can subsequently confirm this expenditure with minimal effort on their part. The concept was invented by Moni Naor and Cynthia Dwork in 1993 as a way to deter denial-of-service attacks and other service abuses such as spam on a network by requiring some work from a service requester, usually meaning processing time by a computer. The term "proof of work" was first coined and formalized in a 1999 paper by Markus Jakobsson and Ari Juels. Proof of work was later popularized by Bitcoin as a foundation for consensus in a permissionless decentralized network, in which miners compete to append blocks and mint new currency, each miner experiencing a success probability proportional to the computational effort expended. PoW and PoS (proof of stake) remain the two best known S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hashcash
Hashcash is a proof-of-work system used to limit email spam and denial-of-service attacks, and more recently has become known for its use in bitcoin (and other cryptocurrencies) as part of the mining algorithm. Hashcash was proposed in 1997 by Adam Back and described more formally in Back's 2002 paper "Hashcash - A Denial of Service Counter-Measure". Background The idea "...to require a user to compute a moderately hard, but not intractable function..." was proposed by Cynthia Dwork and Moni Naor in their 1992 paper "Pricing via Processing or Combatting Junk Mail". How it works Hashcash is a cryptographic hash-based proof-of-work algorithm that requires a selectable amount of work to compute, but the proof can be verified efficiently. For email uses, a textual encoding of a hashcash stamp is added to the header of an email to prove the sender has expended a modest amount of CPU time calculating the stamp prior to sending the email. In other words, as the sender has taken a certain ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Mail 2000
Internet Mail 2000 is an Internet mail architecture proposed by Daniel J. Bernstein (and in subsequent years separately proposed by several others), designed with the precept that the initial storage of mail messages be the responsibility of the sender, and not of the recipient as it is with the SMTP-based Internet mail architecture. Whereas the SMTP-based Internet mail architecture has a close analogue in the architecture of paper mail, this is not the case for ''Internet Mail 2000''. Its architecture depends on various things that are unique to the natures of the Internet and to electronic messages. One of its goals is to reduce spam. Implementations Over the years since Daniel J. Bernstein proposed it, several attempts have been made to design and to implement a real ''Internet Mail 2000'' system, with varying degrees of achievement. The closest thing to a concrete, open implementation of the system is Meng Weng Wong's StubMail, which was presented at Google in July 2006 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-spam Techniques
Various anti-spam techniques are used to prevent email spam (unsolicited bulk email). No technique is a complete solution to the spam problem, and each has trade-offs between incorrectly rejecting legitimate email (false positives) as opposed to not rejecting all spam email (false negatives) – and the associated costs in time, effort, and cost of wrongfully obstructing good mail. Anti-spam techniques can be broken into four broad categories: those that require actions by individuals, those that can be automated by email administrators, those that can be automated by email senders and those employed by researchers and law enforcement officials. End-user techniques There are a number of techniques that individuals can use to restrict the availability of their email addresses, with the goal of reducing their chance of receiving spam. Discretion Sharing an email address only among a limited group of correspondents is one way to limit the chance that the address will be "harvest ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-spam
Various anti-spam techniques are used to prevent email spam (unsolicited bulk email). No technique is a complete solution to the spam problem, and each has trade-offs between incorrectly rejecting legitimate email (false positives) as opposed to not rejecting all spam email (false negatives) – and the associated costs in time, effort, and cost of wrongfully obstructing good mail. Anti-spam techniques can be broken into four broad categories: those that require actions by individuals, those that can be automated by email administrators, those that can be automated by email senders and those employed by researchers and law enforcement officials. End-user techniques There are a number of techniques that individuals can use to restrict the availability of their email addresses, with the goal of reducing their chance of receiving spam. Discretion Sharing an email address only among a limited group of correspondents is one way to limit the chance that the address will be "harveste ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |