|
Park Jin Hyok
Park Jin-Hyok (), is a North Korean programmer and hacker. He is best known for his alleged involvement in some of the costliest computer intrusions in history. Park is on the FBI's wanted list. North Korea denies his existence. Life and career Early life Park attended the Kim Chaek University of Technology in Pyongyang. He has traveled to China in the past and conducted IT work for the North Korean company "Chosun Expo" in addition to activities conducted on behalf of North Korea's Reconnaissance General Bureau. Lazarus group and computer hacking Park is a member of a North Korea's government-funded hacking team known as “ Lazarus Group (or APT 38)” and worked for Chosun Expo Joint Venture (aka Korea Expo Joint Venture), a North Korean government front company, to support the North Korean government’s malicious cyber actions. Chosun is affiliated with Lab 110, a component of North Korea's military intelligence. Expo Joint Venture had offices in China (PRC) and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lazarus Group
Lazarus Group (also known by other monikers such as Guardians of Peace or Whois Team ) is a cybercrime group made up of an unknown number of individuals run by the government of North Korea. While not much is known about the Lazarus Group, researchers have attributed many cyberattacks to them between 2010 and 2021. Originally a criminal group, the group has now been designated as an advanced persistent threat due to intended nature, threat, and wide array of methods used when conducting an operation. Names given by cybersecurity organizations include Hidden Cobra (used by the United States Department of Homeland Security to refer to malicious cyber activity by the North Korean government in general) and Zinc (by Microsoft). The Lazarus Group has strong links to North Korea. The United States Federal Bureau of Investigation says that the Lazarus Group is a North Korean "state-sponsored hacking organization". According to North Korean defector Kim Kuk-song, the unit is internally k ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Health Service (England)
The National Health Service (NHS) is the Publicly funded health care, publicly funded healthcare system in England, and one of the four National Health Service systems in the United Kingdom. It is the second largest single-payer healthcare system in the world after the Brazilian Sistema Único de Saúde. Primarily funded by the government from general taxation (plus a small amount from National Insurance contributions), and overseen by the Department of Health and Social Care, the NHS provides healthcare to all legal English residents and residents from other regions of the UK, with most services free at the point of use for most people. The NHS also conducts research through the National Institute for Health and Care Research (NIHR). Free healthcare at the point of use comes from the core principles at the founding of the National Health Service. The 1942 Beveridge cross-party report established the principles of the NHS which was implemented by the Attlee ministry, Labour ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fugitives Wanted By The United States
A fugitive (or runaway) is a person who is fleeing from custody, whether it be from jail, a government arrest, government or non-government questioning, vigilante violence, or outraged private individuals. A fugitive from justice, also known as a wanted person, can be a person who is either convicted or accused of a crime and hiding from law enforcement in the state or taking refuge in a different country in order to avoid arrest. A fugitive from justice alternatively has been defined as a person formally charged with a crime or a convicted criminal whose punishment has not yet been determined or fully served who is currently beyond the custody or control of the national or sub-national government or international criminal tribunal with an interest in their arrest. This latter definition adopts the perspective of the pursuing government or tribunal, recognizing that the charged (versus escaped) individual does not necessarily realize that they are officially a wanted person ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Year Of Birth Missing (living People)
A year or annus is the orbital period of a planetary body, for example, the Earth, moving in its orbit around the Sun. Due to the Earth's axial tilt, the course of a year sees the passing of the seasons, marked by change in weather, the hours of daylight, and, consequently, vegetation and soil fertility. In temperate and subpolar regions around the planet, four seasons are generally recognized: spring, summer, autumn and winter. In tropical and subtropical regions, several geographical sectors do not present defined seasons; but in the seasonal tropics, the annual wet and dry seasons are recognized and tracked. A calendar year is an approximation of the number of days of the Earth's orbital period, as counted in a given calendar. The Gregorian calendar, or modern calendar, presents its calendar year to be either a common year of 365 days or a leap year of 366 days, as do the Julian calendars. For the Gregorian calendar, the average length of the calendar year (the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hackers
A hacker is a person skilled in information technology who uses their technical knowledge to achieve a goal or overcome an obstacle, within a computerized system by non-standard means. Though the term ''hacker'' has become associated in popular culture with a ''security hacker''someone who utilizes their technical know-how of bugs or exploits to break into computer systems and access data which would otherwise be inaccessible to them – hacking can also be utilized by legitimate figures in legal situations. For example, law enforcement agencies sometimes use hacking techniques in order to collect evidence on criminals and other malicious actors. This could include using anonymity tools (such as a VPN, or the dark web) to mask their identities online, posing as criminals themselves. Likewise, covert world agencies can employ hacking techniques in the legal conduct of their work. On the other hand, hacking and cyber-attacks are used extra- and illegally by law enforcement ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Living People
Related categories * :Year of birth missing (living people) / :Year of birth unknown * :Date of birth missing (living people) / :Date of birth unknown * :Place of birth missing (living people) / :Place of birth unknown * :Year of death missing / :Year of death unknown * :Date of death missing / :Date of death unknown * :Place of death missing / :Place of death unknown * :Missing middle or first names See also * :Dead people * :Template:L, which generates this category or death years, and birth year and sort keys. : {{DEFAULTSORT:Living people 21st-century people People by status ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kim Chaek University Of Technology Alumni
Kim or KIM may refer to: Names * Kim (given name) * Kim (surname) ** Kim (Korean surname) *** Kim family (other), several dynasties **** Kim family (North Korea), the rulers of North Korea since Kim Il-sung in 1948 ** Kim, Vietnamese form of Jin (Chinese surname) Languages * Kim language, a language of Chad * Kim language (Sierra Leone), a language of Sierra Leone * kim, the ISO 639 code of the Tofa language of Russia Media * ''Kim'' (album), a 2009 album by Kim Fransson * "Kim" (song), 2000 song by Eminem * "Kim", a song by Tkay Maidza, 2021 * ''Kim'' (novel), by Rudyard Kipling ** ''Kim'' (1950 film), an American adventure film based on the novel ** ''Kim'' (1984 film), a British film based on the novel * "Kim" (''M*A*S*H''), a 1973 episode of the American television show ''M*A*S*H'' * ''Kim'' (magazine), defunct Turkish women's magazine (1992–1999) Organizations * Kenya Independence Movement, a defunct political party in Kenya * Khalifa Islamiyah Minda ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sony Pictures Hack
On November 24, 2014, a hacker group identifying itself as "Guardians of Peace" leaked a release of confidential data from the film studio Sony Pictures Entertainment (SPE). The data included personal information about Sony Pictures employees and their families, emails between employees, information about executive salaries at the company, copies of then-unreleased Sony films, plans for future Sony films, scripts for certain films, and other information. The perpetrators then employed a variant of the Shamoon wiper malware to erase Sony's computer infrastructure. During the hack, the group demanded that Sony withdraw its then-upcoming film ''The Interview'', a comedy about a plot to assassinate North Korean leader Kim Jong-un, and threatened terrorist attacks at cinemas screening the film. After many major U.S. theater chains opted not to screen ''The Interview'' in response to these threats, Sony chose to cancel the film's formal premiere and mainstream release, opting to ski ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
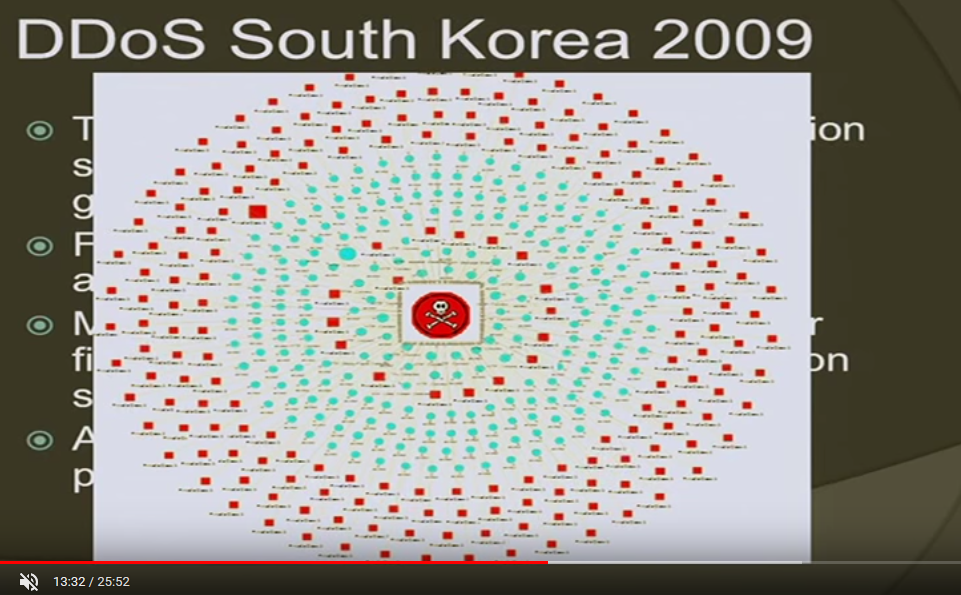
July 2009 Cyberattacks
The July 2009 cyberattacks were a series of coordinated cyberattacks against major government, news media, and financial websites in South Korea and the United States. The attacks involved the activation of a botnet—a large number of hijacked computers—that maliciously accessed targeted websites with the intention of causing their servers to overload due to the influx of traffic, known as a DDoS attack. Most of the hijacked computers were located in South Korea. The estimated number of the hijacked computers varies widely; around 20,000 according to the South Korean National Intelligence Service, around 50,000 according to Symantec's Security Technology Response group, and more than 166,000 according to a Vietnamese computer security researcher who analyzed the log files of the two servers the attackers controlled. An investigation revealed that at least 39 websites were targets in the attacks based on files stored on compromised systems. The targeting and timing of th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
2013 South Korea Cyberattack
In 2013 there were two major sets of cyberattacks on South Korean targets attributed to elements within North Korea. March On 20 March 2013, three South Korean television stations and a bank suffered from frozen computer terminals in a suspected act of cyberwarfare.Tania Branigan"South Korea on alert for cyber-attacks after major network goes down: Computer systems of banks and broadcasters are interrupted, with fingers immediately pointed at North Korea" ''The Guardian'', 20 March 2013. ATMs and mobile payments were also affected. The South Korean communications watchdog Korea Communications Commission raised their alert level on cyber-attacks to three on a scale of five. North Korea has been blamed for similar attacks in 2009 and 2011 and was suspected of launching this attack as well. This attack also came at a period of elevated tensions between the two Koreas, following Pyongyang’s nuclear test on 12 February. South Korean officials linked the incident to a China, Chinese ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WannaCry Ransomware Attack
The WannaCry ransomware attack was a worldwide cyberattack in May 2017 by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency. It propagated by using EternalBlue, an exploit developed by the United States National Security Agency (NSA) for Windows systems. EternalBlue was stolen and leaked by a group called The Shadow Brokers a month prior to the attack. While Microsoft had released patches previously to close the exploit, much of WannaCry's spread was from organizations that had not applied these, or were using older Windows systems that were past their end-of-life. These patches were imperative to organizations' cyber security but many were not implemented due to ignorance of their importance. Some have claimed a need for 24/7 operation, aversion to risking having formerly working applications breaking because of patch changes, lack of person ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker (computer Security)
A security hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, information gathering, challenge, recreation, or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. The subculture that has evolved around hackers is often referred to as the "computer underground". Longstanding controversy surrounds the meaning of the term "hacker." In this controversy, computer programmers reclaim the term ''hacker'', arguing that it refers simply to someone with an advanced understanding of computers and computer networks and that ''cracker'' is the more appropriate term for those who break into computers, whether computer criminals ( black hats) or computer security experts ( white hats). A 2014 article noted that "the black-hat meaning still prevails among the general public". History Birth of subcult ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

Aug2005.jpg)

.jpg)