|
Open Net Initiative
The OpenNet Initiative (ONI) was a joint project whose goal was to monitor and report on internet filtering and surveillance practices by nations. The project employed a number of technical means, as well as an international network of investigators, to determine the extent and nature of government-run internet filtering programs. Participating academic institutions included the Citizen Lab at the Munk Centre for International Studies, University of Toronto; Berkman Center for Internet & Society at Harvard Law School; the Oxford Internet Institute (OII) at University of Oxford; and, The SecDev Group, which took over from the Advanced Network Research Group at the Cambridge Security Programme, University of Cambridge. In December 2014 the OpenNet Initiative partners announced that they would no longer carry out research under the ONI banner. The ONI website, including all reports and data, is being maintained indefinitely to allow continued public access to ONI's entire archive of p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Censorware
An Internet filter is software that restricts or controls the content an Internet user is capable to access, especially when utilized to restrict material delivered over the Internet via the Web, Email, or other means. Content-control software determines what content will be available or be blocked. Such restrictions can be applied at various levels: a government can attempt to apply them nationwide (see Internet censorship), or they can, for example, be applied by an Internet service provider to its clients, by an employer to its personnel, by a school to its students, by a library to its visitors, by a parent to a child's computer, or by an individual users to their own computers. The motive is often to prevent access to content which the computer's owner(s) or other authorities may consider objectionable. When imposed without the consent of the user, content control can be characterised as a form of internet censorship. Some content-control software includes time control ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Oxford University
Oxford () is a city in England. It is the county town and only city of Oxfordshire. In 2020, its population was estimated at 151,584. It is north-west of London, south-east of Birmingham and north-east of Bristol. The city is home to the University of Oxford, the oldest university in the English-speaking world; it has buildings in every style of English architecture since late Anglo-Saxon. Oxford's industries include motor manufacturing, education, publishing, information technology and science. History The history of Oxford in England dates back to its original settlement in the Saxon period. Originally of strategic significance due to its controlling location on the upper reaches of the River Thames at its junction with the River Cherwell, the town grew in national importance during the early Norman period, and in the late 12th century became home to the fledgling University of Oxford. The city was besieged during The Anarchy in 1142. The university rose to domina ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Privacy
Internet privacy involves the right or mandate of personal privacy concerning the storing, re-purposing, provision to third parties, and displaying of information pertaining to oneself via Internet. Internet privacy is a subset of data privacy. Privacy concerns have been articulated from the beginnings of large-scale computer sharing. Privacy can entail either personally identifiable information (PII) or non-PII information such as a site visitor's behavior on a website. PII refers to any information that can be used to identify an individual. For example, age and physical address alone could identify who an individual is without explicitly disclosing their name, as these two factors are unique enough to identify a specific person typically. Other forms of PII may soon include GPS tracking data used by apps, as the daily commute and routine information can be enough to identify an individual. It has been suggested that the "appeal of online services is to broadcast personal infor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Freedom Of Information
Freedom of information is freedom of a person or people to publish and consume information. Access to information is the ability for an individual to seek, receive and impart information effectively. This sometimes includes "scientific, indigenous, and traditional knowledge; freedom of information, building of open knowledge resources, including open Internet and open standards, and open access and availability of data; preservation of digital heritage; respect for cultural and linguistic diversity, such as fostering access to local content in accessible languages; quality education for all, including lifelong and e-learning; diffusion of new media and information literacy and skills, and social inclusion online, including addressing inequalities based on skills, education, gender, age, race, ethnicity, and accessibility by those with disabilities; and the development of connectivity and affordable ICTs, including mobile, the Internet, and broadband infrastructures". Public ac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Censorship By Country Censorship by country collects information on censorship, Internet censorship, freedom of the press, freedom of speech, and human rights by country and presents it in a sortable table, together with links to articles with more information. In addition to countries, the table includes information on former countries, disputed countries, political sub-units within countries, and regional organizations. Table Maps Freedom of the Press Report 2015 Freedom of the Press Classifications Press Freedom Index 2014 Press Freedom Index"Press Freedom Index 2014" , Reporters Without Borders, 11 May 2014 [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OSCE Representative On Freedom Of The Media
The OSCE Representative on Freedom of the Media functions as a watchdog on media developments in all 57 participating member states of the Organization for Security and Co-operation in Europe (OSCE). The representative provides early warning on violations of freedom of expression and promotes full compliance with OSCE principles and commitments regarding freedom of expression and press freedom. Mission In cases where serious violations have occurred, the representative seeks direct contacts with the offending state and other parties involved, assesses the facts and assists in resolving problems. The representative collects and receives information on the situation of the media from a variety of sources, including participating OSCE States, non-governmental organizations and media organizations. The representative meets with member governments. The office of the representative is based in Vienna, Austria, and has a staff of 15. Each year, they issue a joint declaration calling att ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MIT Press
The MIT Press is a university press affiliated with the Massachusetts Institute of Technology (MIT) in Cambridge, Massachusetts (United States). It was established in 1962. History The MIT Press traces its origins back to 1926 when MIT published under its own name a lecture series entitled ''Problems of Atomic Dynamics'' given by the visiting German physicist and later Nobel Prize winner, Max Born. Six years later, MIT's publishing operations were first formally instituted by the creation of an imprint called Technology Press in 1932. This imprint was founded by James R. Killian, Jr., at the time editor of MIT's alumni magazine and later to become MIT president. Technology Press published eight titles independently, then in 1937 entered into an arrangement with John Wiley & Sons in which Wiley took over marketing and editorial responsibilities. In 1962 the association with Wiley came to an end after a further 125 titles had been published. The press acquired its modern name af ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proxy Server
In computer networking, a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource. Instead of connecting directly to a server that can fulfill a request for a resource, such as a file or web page, the client directs the request to the proxy server, which evaluates the request and performs the required network transactions. This serves as a method to simplify or control the complexity of the request, or provide additional benefits such as load balancing, privacy, or security. Proxies were devised to add structure and encapsulation to distributed systems. A proxy server thus functions on behalf of the client when requesting service, potentially masking the true origin of the request to the resource server. Types A proxy server may reside on the user's local computer, or at any point between the user's computer and destination servers on the Internet. A proxy server that passes unmodified r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encrypted
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Censorship By Country
This list of Internet censorship and surveillance by country provides information on the types and levels of Internet censorship and surveillance that is occurring in countries around the world. Classifications Detailed country by country information on Internet censorship and surveillance is provided in the ''Freedom on the Net'' reports from Freedom House, by the OpenNet Initiative, by Reporters Without Borders, and in the ''Country Reports on Human Rights Practices'' from the U.S. State Department Bureau of Democracy, Human Rights, and Labor. The ratings produced by several of these organizations are summarized below as well as in the Censorship by country article. ''Freedom on the Net'' reports The ''Freedom on the Net'' reports provide analytical reports and numerical ratings regarding the state of Internet freedom for countries worldwide. The countries surveyed represent a sample with a broad range of geographical diversity and levels of economic development, as well as var ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
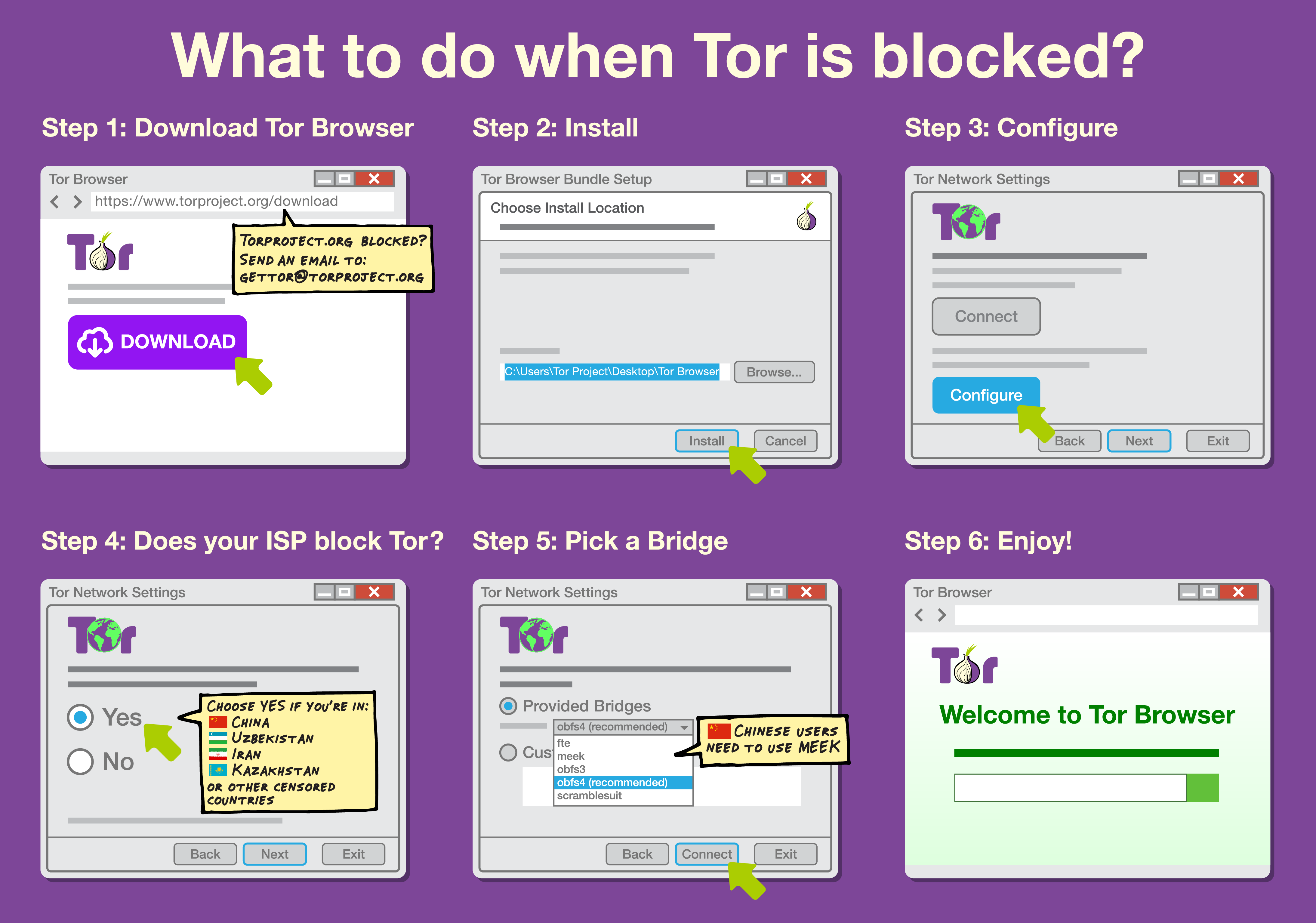
Internet Censorship Circumvention
Internet censorship circumvention is the use of various methods and tools to bypass internet censorship. Various techniques and methods are used to bypass Internet censorship, and have differing ease of use, speed, security, and risks. Some methods, such as the use of alternate DNS servers, evade blocking by using an alternate address or address lookup system to access the site. Techniques using website mirrors or archive sites rely on other copies of the site being available at different locations. Additionally, there are solutions that rely on gaining access to an Internet connection that is not subject to filtering, often in a different jurisdiction not subject to the same censorship laws, using technologies such as proxying, virtual private networks, or anonymization networks. An arms race has developed between censors and developers of circumvention software, resulting in more sophisticated blocking techniques by censors and the development of harder-to-detect tools by rese ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Censorship
Censorship is the suppression of speech, public communication, or other information. This may be done on the basis that such material is considered objectionable, harmful, sensitive, or "inconvenient". Censorship can be conducted by governments, private institutions and other controlling bodies. Governments and private organizations may engage in censorship. Other groups or institutions may propose and petition for censorship.https://www.aclu.org/other/what-censorship "What Is Censorship", ACLU When an individual such as an author or other creator engages in censorship of his or her own works or speech, it is referred to as ''self-censorship''. General censorship occurs in a variety of different media, including speech, books, music, films, and other arts, the press, radio, television, and the Internet for a variety of claimed reasons including national security, to control obscenity, pornography, and hate speech, to protect children or other vulnerable groups, to promote or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)