|
New API
New API (also referred to as NAPI) is an interface to use interrupt mitigation techniques for networking devices in the Linux kernel. Such an approach is intended to reduce the overhead of packet receiving. The idea is to defer incoming message handling until there is a sufficient amount of them so that it is worth handling them all at once. Motivation A straightforward method of implementing a network driver is to interrupt the kernel by issuing an interrupt request (IRQ) for each and every incoming packet. However, servicing IRQs is costly in terms of processor resources and time. Therefore, the straightforward implementation can be very inefficient in high-speed networks, constantly interrupting the kernel with the thousands of packets per second. Overall performance of the system as well as network throughput can suffer as a result. Polling is an alternative to interrupt-based processing. The kernel can periodically check for the arrival of incoming network packets witho ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Interrupt Mitigation
Interrupt coalescing, also known as interrupt moderation, is a technique in which events which would normally trigger a hardware interrupt are held back, either until a certain amount of work is pending, or a timeout timer triggers. Used correctly, this technique can reduce interrupt load by up to an order of magnitude, while only incurring relatively small latency penalties. Interrupt coalescing is typically combined with either a hardware FIFO queue or direct memory access, to allow for continued data throughput while interrupts are being held back. Interrupt coalescing is a common feature of modern network cards, but the technique dates back to early computer UARTs such as the 16550 UART chip used in the IBM PC's serial interface, at a time when even servicing the interrupt rates required by the low data rate serial data streams of the day was taxing for contemporary CPUs. Interrupt coalescing can also be implemented without support in hardware, by disabling interrupts in the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linux Kernel
The Linux kernel is a Free and open-source software, free and open source Unix-like kernel (operating system), kernel that is used in many computer systems worldwide. The kernel was created by Linus Torvalds in 1991 and was soon adopted as the kernel for the GNU operating system (OS) which was created to be a free software, free replacement for Unix. Since the late 1990s, it has been included in many Linux distributions, operating system distributions, many of which are called Linux. One such Linux kernel operating system is Android (operating system), Android which is used in many mobile and embedded devices. Most of the kernel code is written in C (programming language), C as supported by the GNU compiler collection (GCC) which has extensions beyond standard C. The code also contains assembly language, assembly code for architecture-specific logic such as optimizing memory use and task execution. The kernel has a Modular programming, modular design such that modules can be inte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Interrupt Request
In a computer, an interrupt request (or IRQ) is a hardware signal sent to the processor that temporarily stops a running program and allows a special program, an interrupt handler, to run instead. Hardware interrupts are used to handle events such as receiving data from a modem or network card, key presses, or mouse movements. Interrupt lines are often identified by an index with the format of ''IRQ'' followed by a number. For example, on the Intel 8259 family of programmable interrupt controllers (PICs) there are eight interrupt inputs commonly referred to as ''IRQ0'' through ''IRQ7''. In x86 based computer systems that use two of these PICs, the combined set of lines are referred to as ''IRQ0'' through ''IRQ15''. Technically these lines are named ''IR0'' through ''IR7'', and the lines on the ISA bus to which they were historically attached are named ''IRQ0'' through ''IRQ15'' (although historically as the number of hardware devices increased, the total possible number o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Polling (computer Science)
Polling, or interrogation, refers to actively sampling the status of an external device by a client program as a synchronous activity. Polling is most often used in terms of input/output (), and is also referred to as polled or software-driven . A good example of hardware implementation is a watchdog timer. Description Polling is the process where the computer or controlling device waits for an external device to check for its readiness or state, often with low-level hardware. For example, when a printer is connected via a parallel port, the computer waits until the printer has received the next character. These processes can be as minute as only reading one bit. This is sometimes used synonymously with ' busy-wait' polling. In this situation, when an operation is required, the computer does nothing other than check the status of the device until it is ready, at which point the device is accessed. In other words, the computer waits until the device is ready. Polling also ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Direct Memory Access
Direct memory access (DMA) is a feature of computer systems that allows certain hardware subsystems to access main system computer memory, memory independently of the central processing unit (CPU). Without DMA, when the CPU is using programmed input/output, it is typically fully occupied for the entire duration of the read or write operation, and is thus unavailable to perform other work. With DMA, the CPU first initiates the transfer, then it does other operations while the transfer is in progress, and it finally receives an interrupt from the DMA controller (DMAC) when the operation is done. This feature is useful at any time that the CPU cannot keep up with the rate of data transfer, or when the CPU needs to perform work while waiting for a relatively slow I/O data transfer. Many hardware systems use DMA, including disk drive controllers, graphics cards, network cards and sound cards. DMA is also used for intra-chip data transfer in some multi-core processors. Computers that h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Card
A network interface controller (NIC, also known as a network interface card, network adapter, LAN adapter and physical network interface) is a computer hardware component that connects a computer to a computer network. Early network interface controllers were commonly implemented on expansion cards that plugged into a computer bus. The low cost and ubiquity of the Ethernet standard means that most newer computers have a network interface built into the motherboard, or is contained into a USB-connected dongle, although network cards remain available. Modern network interface controllers offer advanced features such as interrupt and DMA interfaces to the host processors, support for multiple receive and transmit queues, partitioning into multiple logical interfaces, and on-controller network traffic processing such as the TCP offload engine. Purpose The network controller implements the electronic circuitry required to communicate using a specific physical layer and data link ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
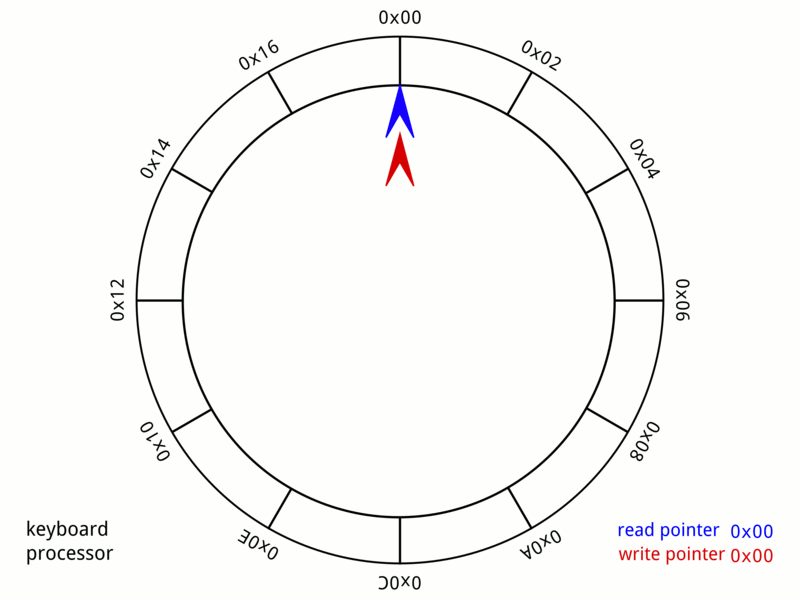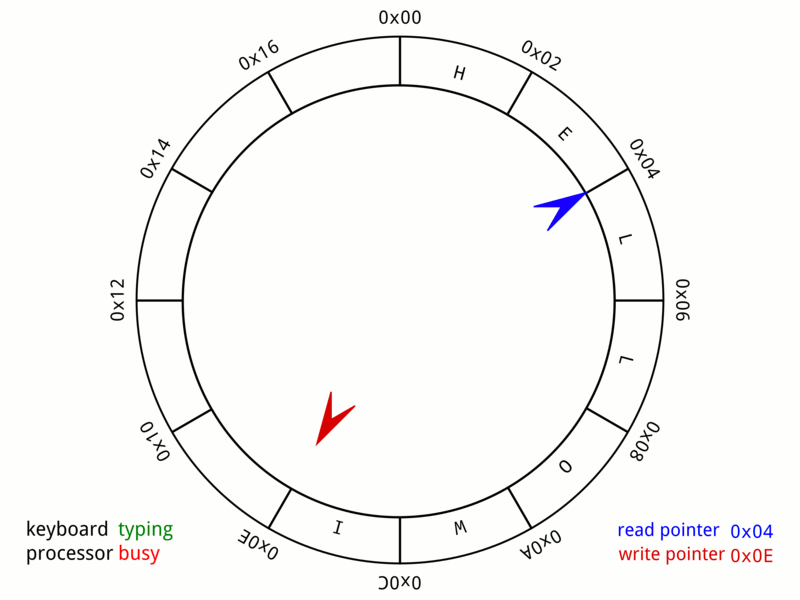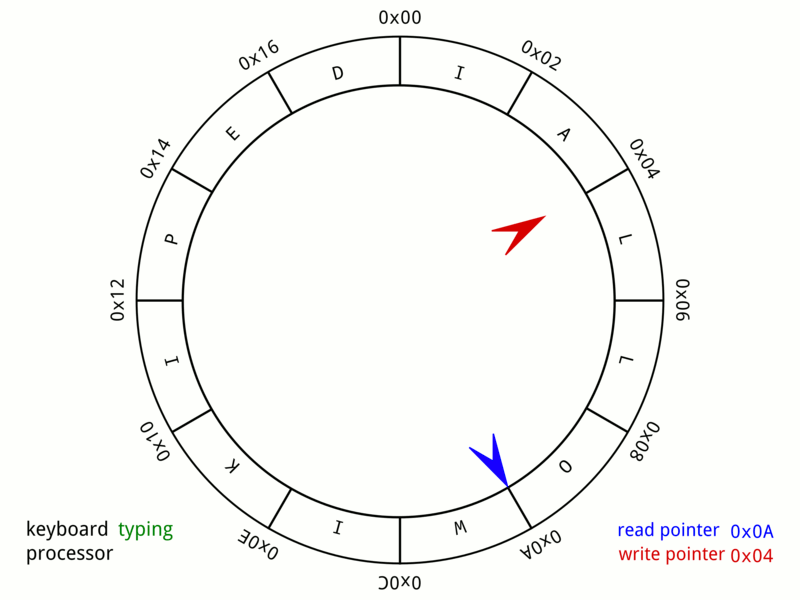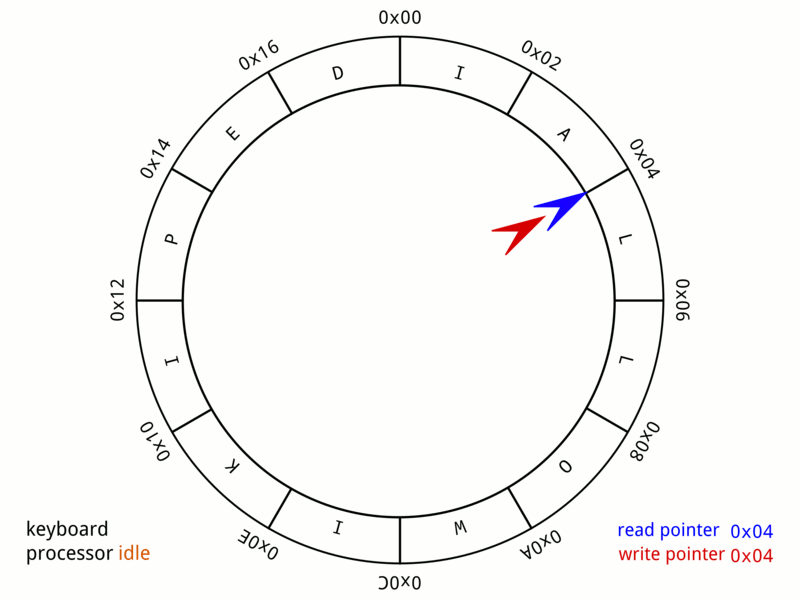
Ring Buffer
In computer science, a circular buffer, circular queue, cyclic buffer or ring buffer is a data structure that uses a single, fixed-size buffer as if it were connected end-to-end. This structure lends itself easily to buffering data streams. There were early circular buffer implementations in hardware. Overview A circular buffer first starts out empty and has a set length. In the diagram below is a 7-element buffer: : Assume that 1 is written in the center of a circular buffer (the exact starting location is not important in a circular buffer): : Then assume that two more elements are added to the circular buffer — 2 & 3 — which get put after 1: : If two elements are removed, the two oldest values inside of the circular buffer would be removed. Circular buffers use FIFO ('' first in, first out'') logic. In the example, 1 & 2 were the first to enter the circular buffer, they are the first to be removed, leaving 3 inside of the buffer. : If the buffer has 7 el ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Thrashing (computer Science)
In computer science, thrashing occurs in a system with virtual memory when a computer's real storage resources are ''overcommitted'', leading to a constant state of paging and page faults, slowing most application-level processing. This causes the performance of the computer to degrade or even collapse. The situation can continue indefinitely until the user closes some running applications or the active processes free up additional virtual memory resources. After initialization, most programs operate on a small number of code and data pages compared to the total memory the program requires. The pages most frequently accessed at any point are called the working set, which may change over time. When the working set is not significantly greater than the system's total number of real storage ''page frames'', virtual memory systems work most efficiently, and an insignificant amount of computing is spent resolving page faults. As the total of the working sets grows, resolving page fa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
David S
David (; , "beloved one") was a king of ancient Israel and Judah and the Kings of Israel and Judah, third king of the Kingdom of Israel (united monarchy), United Monarchy, according to the Hebrew Bible and Old Testament. The Tel Dan stele, an Canaanite and Aramaic inscriptions, Aramaic-inscribed stone erected by a king of Aram-Damascus in the late 9th/early 8th centuries BCE to commemorate a victory over two enemy kings, contains the phrase (), which is translated as "Davidic line, House of David" by most scholars. The Mesha Stele, erected by King Mesha of Moab in the 9th century BCE, may also refer to the "House of David", although this is disputed. According to Jewish works such as the ''Seder Olam Rabbah'', ''Seder Olam Zutta'', and ''Sefer ha-Qabbalah'' (all written over a thousand years later), David ascended the throne as the king of Judah in 885 BCE. Apart from this, all that is known of David comes from biblical literature, Historicity of the Bible, the historicit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Uppsala University
Uppsala University (UU) () is a public university, public research university in Uppsala, Sweden. Founded in 1477, it is the List of universities in Sweden, oldest university in Sweden and the Nordic countries still in operation. Initially founded in the 15th century, the university rose to significance during the rise of Swedish Empire, Sweden as a great power at the end of the 16th century and was then given relative financial stability with a large donation from Monarchy of Sweden, King Gustavus Adolphus of Sweden, Gustavus Adolphus in the early 17th century. Uppsala also has an important historical place in Swedish national culture, and national identity, identity for the Swedish establishment: in historiography, religion, literature, politics, and music. Many aspects of Swedish academic culture in general, such as the white student cap, originated in Uppsala. It shares some peculiarities, such as the student nation system, with Lund University and the University of Helsink ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Packet Generator
A packet generator or packet builder is a type of software that generates random packets or allows the user to construct detailed custom packets. Depending on the network medium and operating system, packet generators utilize raw sockets, NDIS function calls, or direct access to the network adapter kernel-mode driver. This is useful for testing implementations of IP stacks for bugs and security vulnerabilities. Comparison General Information See also * Packet crafting *Packet analyzer A packet analyzer (also packet sniffer or network analyzer) is a computer program or computer hardware such as a packet capture appliance that can analyze and log traffic that passes over a computer network or part of a network. Packet capt ... *Packetsquare Network analyzers Packets (information technology) {{network-software-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Interfaces Of The Linux Kernel
Interface or interfacing may refer to: Academic journals * ''Interface'' (journal), by the Electrochemical Society * '' Interface, Journal of Applied Linguistics'', now merged with ''ITL International Journal of Applied Linguistics'' * '' Interface: A Journal for and About Social Movements'' * ''Interface'', shortened name for the ''Journal of the Royal Society Interface'', covering the interface between life sciences and physical sciences * ''Interfaces'' (journal), now ''INFORMS Journal on Applied Analytics'' Arts and entertainment * ''Interface'' (album), by Dominion, 1996 * Interface (band), an American music group * ''Interface'' (film), a 1984 American film * ''Interface'' (novel), by Stephen Bury (a pseudonym), 1994 * "Interface" (''Star Trek: The Next Generation''), an episode of the TV series * '' Interface series'', a science fiction horror story in short installments on Reddit Science and technology * Interface (computing), a shared boundary between system comp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |