|
Network Congestion
Network congestion in data networking and queueing theory is the reduced quality of service that occurs when a network node or link is carrying more data than it can handle. Typical effects include queueing delay, packet loss or the blocking of new connections. A consequence of congestion is that an incremental increase in offered load leads either only to a small increase or even a decrease in network throughput. Network protocols that use aggressive retransmissions to compensate for packet loss due to congestion can increase congestion, even after the initial load has been reduced to a level that would not normally have induced network congestion. Such networks exhibit two stable states under the same level of load. The stable state with low throughput is known as congestive collapse. Networks use congestion control and congestion avoidance techniques to try to avoid collapse. These include: exponential backoff in protocols such as CSMA/CA in 802.11 and the similar CSMA/CD i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Networking
A computer network is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies, based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of network topologies. The nodes of a computer network can include personal computers, servers, networking hardware, or other specialised or general-purpose hosts. They are identified by network addresses, and may have hostnames. Hostnames serve as memorable labels for the nodes, rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the transmission medium used to carry signals, bandwidth, communications protocols ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Router (computing)
A router is a networking device that forwards data packets between computer networks. Routers perform the traffic directing functions between networks and on the global Internet. Data sent through a network, such as a web page or email, is in the form of data packets. A packet is typically forwarded from one router to another router through the networks that constitute an internetwork (e.g. the Internet) until it reaches its destination node. A router is connected to two or more data lines from different IP networks. When a data packet comes in on one of the lines, the router reads the network address information in the packet header to determine the ultimate destination. Then, using information in its routing table or routing policy, it directs the packet to the next network on its journey. The most familiar type of IP routers are home and small office routers that simply forward IP packets between the home computers and the Internet. More sophisticated routers, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
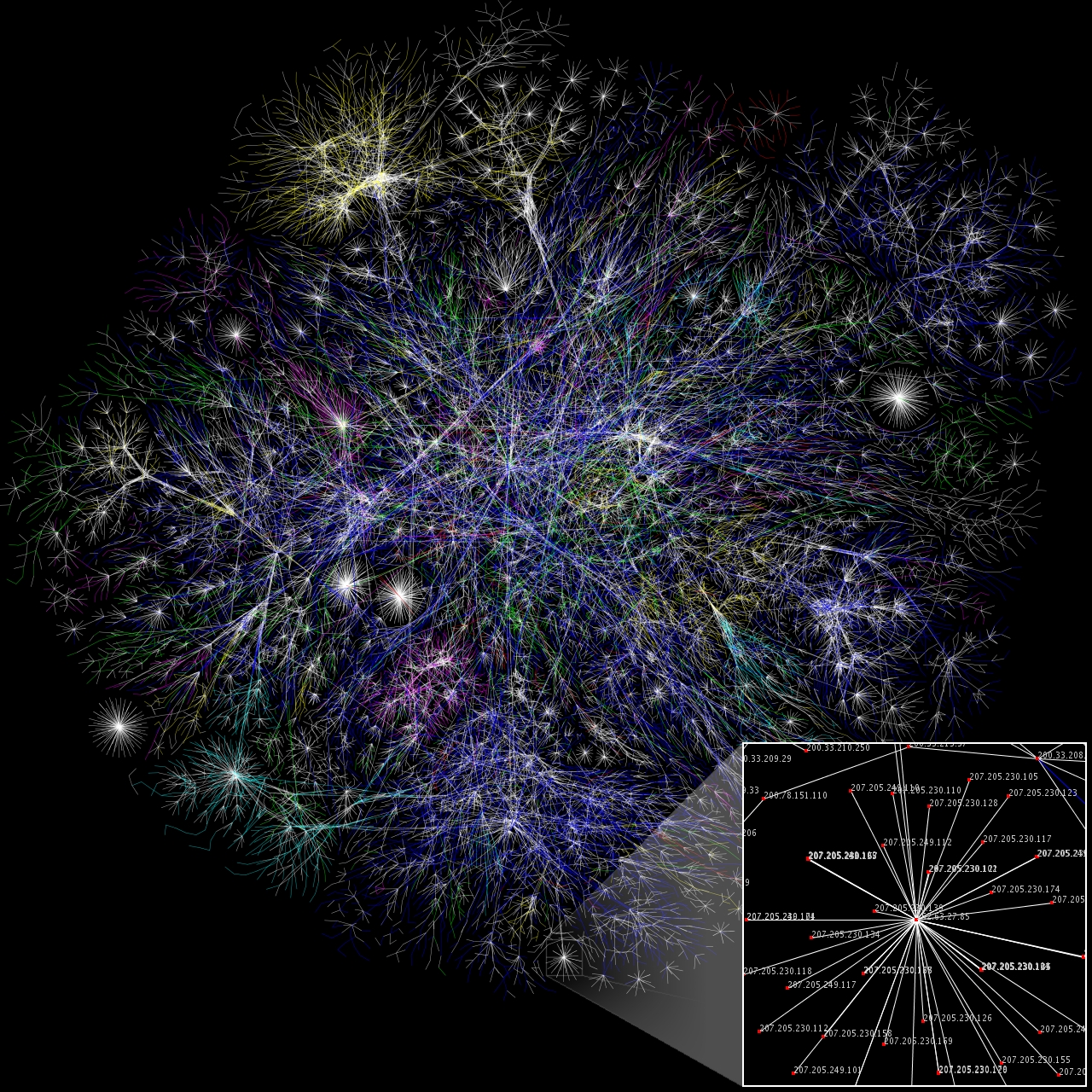
NSFNET
The National Science Foundation Network (NSFNET) was a program of coordinated, evolving projects sponsored by the National Science Foundation (NSF) from 1985 to 1995 to promote advanced research and education networking in the United States. The program created several nationwide backbone computer networks in support of these initiatives. Initially created to link researchers to the NSF-funded supercomputing centers, through further public funding and private industry partnerships it developed into a major part of the Internet backbone. The National Science Foundation permitted only government agencies and universities to use the network until 1989 when the first commercial Internet service provider emerged. By 1991, the NSF removed access restrictions and the commercial ISP business grew rapidly. History Following the deployment of the Computer Science Network (CSNET), a network that provided Internet services to academic computer science departments, in 1981, the U.S. National ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Packet Delay
End-to-end delay or one-way delay (OWD) refers to the time taken for a packet to be transmitted across a network from source to destination. It is a common term in IP network monitoring, and differs from round-trip time (RTT) in that only path in the one direction from source to destination is measured. Measurement The ping utility measures the RTT, that is, the time to go and come back to a host. Half the RTT is often used as an approximation of OWD but this assumes that the forward and back paths are the same in terms of congestion, number of hops, or quality of service (QoS). This is not always a good assumption. To avoid such problems, the OWD may be measured directly. Direct OWDs may be measured between two points ''A'' and ''B'' of an IP network through the use of synchronized clocks; ''A'' records a timestamp on the packet and sends it to ''B'', which notes the receiving time and calculates the OWD as their difference. The transmitted packets need to be identified at source ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wide Area Network
A wide area network (WAN) is a telecommunications network that extends over a large geographic area. Wide area networks are often established with leased telecommunication circuits. Businesses, as well as schools and government entities, use wide area networks to relay data to staff, students, clients, buyers and suppliers from various locations around the world. In essence, this mode of telecommunication allows a business to effectively carry out its daily function regardless of location. The Internet may be considered a WAN. Design options The textbook definition of a WAN is a computer network spanning regions, countries, or even the world. However, in terms of the application of communication protocols and concepts, it may be best to view WANs as computer networking technologies used to transmit data over long distances, and between different networks. This distinction stems from the fact that common local area network (LAN) technologies operating at lower layers of the O ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Local Area Network
A local area network (LAN) is a computer network that interconnects computers within a limited area such as a residence, school, laboratory, university campus or office building. By contrast, a wide area network (WAN) not only covers a larger geographic distance, but also generally involves leased telecommunication circuits. Ethernet and Wi-Fi are the two most common technologies in use for local area networks. Historical network technologies include ARCNET, Token Ring and AppleTalk. History The increasing demand and usage of computers in universities and research labs in the late 1960s generated the need to provide high-speed interconnections between computer systems. A 1970 report from the Lawrence Radiation Laboratory detailing the growth of their "Octopus" network gave a good indication of the situation. A number of experimental and early commercial LAN technologies were developed in the 1970s. Cambridge Ring was developed at Cambridge University starting in 1974. Ethe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mass Call Event
A mass call event or mass calling event (also MCE in telephony usage) is a situation in which an extraordinarily high number of telephone calls are attempted into or out of an area, causing tremendous network congestion, and therefore service which is either significantly degraded or potentially almost completely unavailable. The term is typically used with mobile telephony systems, in which there are simply not enough radio channels available in a given cell or cells. This causes blocked calls or dropped calls. However, it can also apply to landline phones, in which not enough trunking telephone circuits are available into and out of any given telephone exchange or equivalent switching office at any level of the public switched telephone network (PSTN). An MCE is typically caused by a sudden disaster of some sort, such as an earthquake or explosion. One of the earliest examples was the Iroquois Theatre Fire in Chicago in 1903. The 1963 Kennedy assassination represented a mass ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Backbone
The Internet backbone may be defined by the principal data routes between large, strategically interconnected computer networks and core routers of the Internet. These data routes are hosted by commercial, government, academic and other high-capacity network centers, as well as the Internet exchange points and network access points, that exchange Internet traffic between the countries, continents, and across the oceans. Internet service providers, often Tier 1 networks, participate in Internet backbone traffic by privately negotiated interconnection agreements, primarily governed by the principle of settlement-free peering. The Internet, and consequently its backbone networks, do not rely on central control or coordinating facilities, nor do they implement any global network policies. The resilience of the Internet results from its principal architectural features, most notably the idea of placing as few network state and control functions as possible in the network elements a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Botnet
A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and "network". The term is usually used with a negative or malicious connotation. Overview A botnet is a logical collection of Internet-connected devices, such as computers, smartphones or Internet of things (IoT) devices whose security have been breached and control ceded to a third party. Each compromised device, known as a "bot," is created when a device is penetrated by software from a '' malware'' (malicious software) distribution. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols, su ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Denial-of-service Attack
In computing, a denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a network. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. In a distributed denial-of-service attack (DDoS attack), the incoming traffic flooding the victim originates from many different sources. More sophisticated strategies are required to mitigate this type of attack, as simply attempting to block a single source is insufficient because there are multiple sources. A DoS or DDoS attack is analogous to a group of people crowding the entry door of a shop, making it hard for legitimate customers to enter, thus disrupting trade. Criminal perpetrators of DoS attacks oft ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backbone Network
A backbone or core network is a part of a computer network which interconnects networks, providing a path for the exchange of information between different LANs or subnetworks. A backbone can tie together diverse networks in the same building, in different buildings in a campus environment, or over wide areas. Normally, the backbone's capacity is greater than the networks connected to it. A large corporation that has many locations may have a backbone network that ties all of the locations together, for example, if a server cluster needs to be accessed by different departments of a company that are located at different geographical locations. The pieces of the network connections (for example: ethernet, wireless) that bring these departments together is often mentioned as network backbone. Network congestion is often taken into consideration while designing backbones. One example of a backbone network is the Internet backbone. History The theory, design principles, and first ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless LAN
A wireless LAN (WLAN) is a wireless computer network A wireless network is a computer network that uses wireless data connections between network nodes. Wireless networking is a method by which homes, telecommunications networks and business installations avoid the costly process of introducing c ... that links two or more devices using wireless communication to form a local area network (LAN) within a limited area such as a home, school, computer laboratory, campus, or office building. This gives users the ability to move around within the area and remain connected to the network. Through a Gateway (telecommunications), gateway, a WLAN can also provide a connection to the wider Internet. Wireless LANs based on the IEEE 802.11 standards are the most widely used computer networks in the world. These are commonly called Wi-Fi, which is a trademark belonging to the Wi-Fi Alliance. They are used for home and small office networks that link together laptop computers, printer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |