|
Network Segmentation
Network segmentation in computer networking is the act or practice of splitting a computer network into subnetworks, each being a network segment. Advantages of such splitting are primarily for boosting performance and improving security. Advantages * Reduced congestion: On a segmented network, there are fewer hosts per subnetwork and the traffic and thus congestion per segment is reduced * Improved security: ** Broadcasts will be contained to local network. Internal network structure will not be visible from outside. ** There is a reduced attack surface available to pivot in if one of the hosts on the network segment is compromised. Common attack vectors such as LLMNR and NetBIOS poisoning can be partially alleviated by proper network segmentation as they only work on the local network. For this reason it is recommended to segment the various areas of a network by usage. A basic example would be to split up web servers, databases servers and standard user machines each into th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Networking
A computer network is a collection of communicating computers and other devices, such as printers and smart phones. In order to communicate, the computers and devices must be connected by wired media like copper cables, optical fibers, or by wireless communication. The devices may be connected in a variety of network topologies. In order to communicate over the network, computers use agreed-on rules, called communication protocols, over whatever medium is used. The computer network can include personal computers, Server (computing), servers, networking hardware, or other specialized or general-purpose Host (network), hosts. They are identified by network addresses and may have hostnames. Hostnames serve as memorable labels for the nodes and are rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
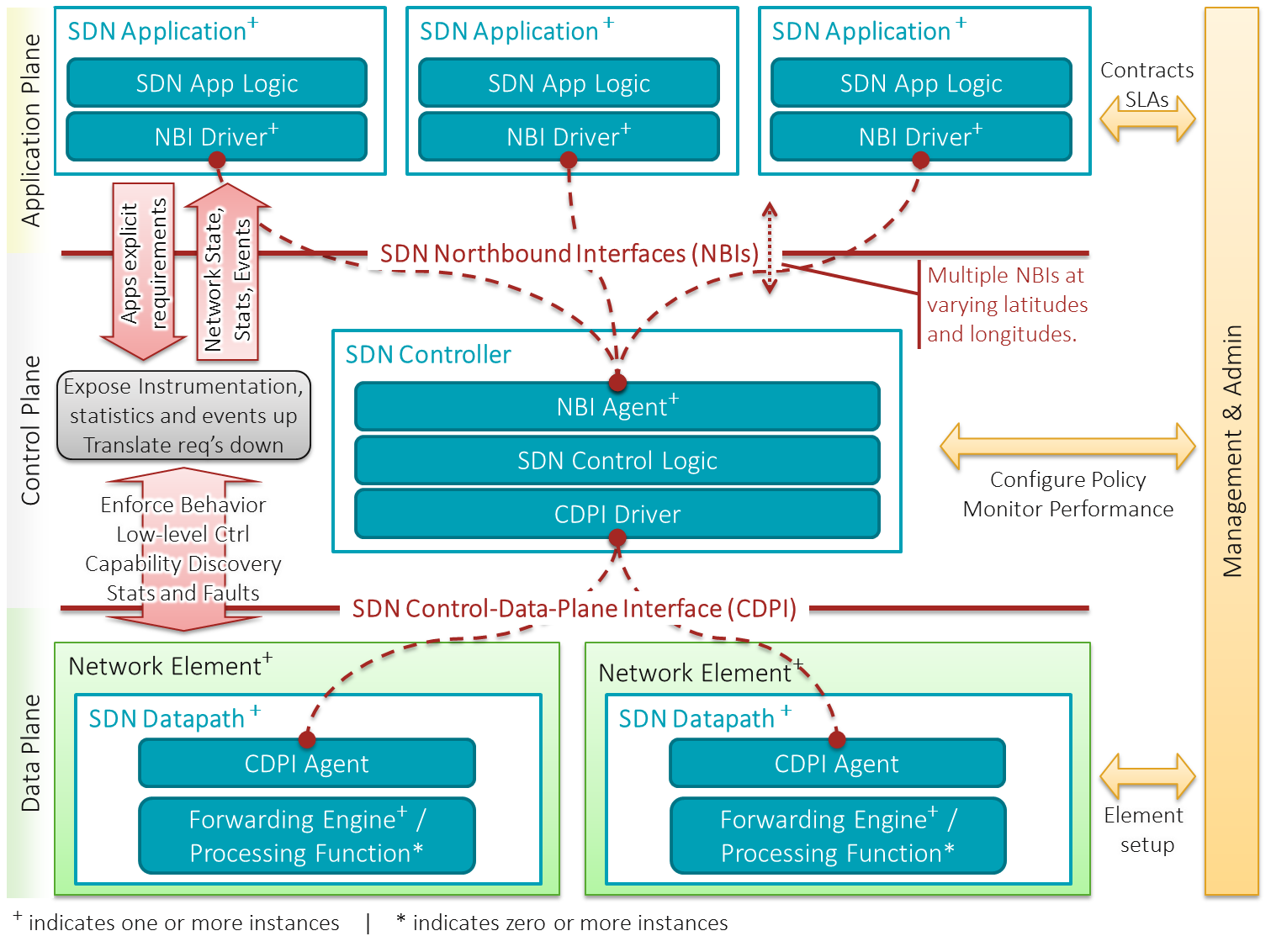
Software-defined Networking
Software-defined networking (SDN) is an approach to network management that uses abstraction to enable dynamic and programmatically efficient network configuration to create grouping and segmentation while improving network performance and monitoring in a manner more akin to cloud computing than to traditional network management. SDN is meant to improve the static architecture of traditional networks and may be employed to centralize network intelligence in one network component by disassociating the forwarding process of network packets ( data plane) from the routing process ( control plane). The control plane consists of one or more controllers, which are considered the brains of the SDN network, where the whole intelligence is incorporated. However, centralization has certain drawbacks related to security, scalability and elasticity. SDN was commonly associated with the OpenFlow protocol for remote communication with network plane elements to determine the path of network pac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Router (computing)
A router is a computer and networking device that Packet forwarding, forwards data packets between computer networks, including internetworks such as the global Internet. Routers perform the "traffic directing" functions on the Internet. A router is connected to two or more data lines from different IP networks. When a data packet comes in on a line, the router reads the network address information in the packet header to determine the ultimate destination. Then, using information in its routing table or routing policy, it directs the packet to the next network on its journey. Data packets are forwarded from one router to another through an internetwork until it reaches its destination Node (networking), node. The most familiar type of Internet Protocol, IP routers are Residential gateway, home and small office routers that forward IP packet (other), IP packets between the home computers and the Internet. More sophisticated routers, such as enterprise routers, conne ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Switch
A network switch (also called switching hub, bridging hub, Ethernet switch, and, by the IEEE, MAC bridge) is networking hardware that connects devices on a computer network by using packet switching to receive and forward data to the destination device. A network switch is a multiport network bridge that uses MAC addresses to forward data at the data link layer (layer 2) of the OSI model. Some switches can also forward data at the network layer (layer 3) by additionally incorporating routing functionality. Such switches are commonly known as layer-3 switches or multilayer switches. Switches for Ethernet are the most common form of network switch. The first MAC Bridge was invented in 1983 by Mark Kempf, an engineer in the Networking Advanced Development group of Digital Equipment Corporation. The first 2 port Bridge product (LANBridge 100) was introduced by that company shortly after. The company subsequently produced multi-port switches for both Ethernet and FDDI such as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Bridge
A network bridge is a computer networking device that creates a single, aggregate network from multiple communication networks or network segments. This function is called network bridging. Bridging is distinct from routing. Routing allows multiple networks to communicate independently and yet remain separate, whereas bridging connects two separate networks as if they were a single network. In the OSI model, bridging is performed in the data link layer (layer 2). If one or more segments of the bridged network are Wireless network, wireless, the device is known as a wireless bridge. The main types of network bridging technologies are simple bridging, multiport bridging, and learning or transparent bridging. Transparent bridging Transparent bridging uses a table called the ''forwarding information base'' to control the forwarding of frames between network segments. The table starts empty and entries are added as the bridge receives frames. If a destination address entry is no ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Flat Network
A flat network is a computer network design approach that aims to reduce cost, maintenance and administration. Flat networks are designed to reduce the number of routers and switches on a computer network by connecting the devices to a single switch instead of separate switches. Unlike a hierarchical network design, the network is not physically separated using different switches. The topology of a flat network is not segmented or separated into different broadcast areas by using routers. Some such networks may use network hubs or a mixture of hubs and switches, rather than switches and routers, to connect devices to each other. Generally, all devices on the network are a part of the same broadcast area. Uses Flat networks are typically used in homes or small businesses where network requirements are low. Home networks usually do not require intensive security, or separation, because the network is often used to provide multiple computers access to the Internet. In such case ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cross-domain Solution
A cross-domain solution (CDS) is an integrated information assurance system composed of specialized software or hardware that provides a controlled interface to manually or automatically enable and/or restrict the access or transfer of information between two or more security domains based on a predetermined security policy. CDSs are designed to enforce domain separation and typically include some form of content filtering, which is used to designate information that is unauthorized for transfer between security domains or levels of classification, such as between different military divisions, intelligence agencies, or other operations which depend on the timely sharing of potentially sensitive information. The goal of a CDS is to allow a trusted network domain to exchange information with other domains, either one-way or bi-directionally, without introducing the potential for security threats. CDS development, assessment, and deployment are based on comprehensive risk management ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Collision Domain
A collision domain is a network segment (connected by a shared medium or through repeaters) where simultaneous data transmissions collide with one another as a result of more than one device attempting to send a packet on the network segment at the same time. The collision domain applies particularly in wireless networks, but also affected early versions of Ethernet. Members of a collision domain may be involved in collisions with one another. Devices outside the collision domain do not have collisions with those inside. A channel access method dictates that only one device in the collision domain may transmit at any one time, and the other devices in the domain listen to the network and refrain from transmitting while others are already transmitting in order to avoid collisions. Because only one device may be transmitting at any one time, total network bandwidth is shared among all devices on the collision domain. Collisions also decrease network efficiency in a collision domain ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
VLAN
A virtual local area network (VLAN) is any broadcast domain that is partitioned and isolated in a computer network at the data link layer ( OSI layer 2).IEEE 802.1Q-2011, ''1.4 VLAN aims and benefits'' In this context, virtual refers to a physical object recreated and altered by additional logic, within the local area network. Basically, a VLAN behaves like a virtual switch or network link that can share the same physical structure with other VLANs while staying logically separate from them. VLANs work by applying tags to network frames and handling these tags in networking systems, in effect creating the appearance and functionality of network traffic that, while on a single physical network, behaves as if it were split between separate networks. In this way, VLANs can keep network applications separate despite being connected to the same physical network, and without requiring multiple sets of cabling and networking devices to be deployed. VLANs allow network administra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Subnetwork
A subnet, or subnetwork, is a logical subdivision of an IP network. Updated by RFC 6918. The practice of dividing a network into two or more networks is called subnetting. Computers that belong to the same subnet are addressed with an identical group of its most-significant bits of their IP addresses. This results in the logical division of an IP address into two fields: the ''network number'' or ''routing prefix'', and the ''rest field'' or ''host identifier''. The ''rest field'' is an identifier for a specific host or network interface. The ''routing prefix'' may be expressed as the first address of a network, written in Classless Inter-Domain Routing (CIDR) notation, followed by a slash character (''/''), and ending with the bit-length of the prefix. For example, is the prefix of the Internet Protocol version 4 network starting at the given address, having 24 bits allocated for the network prefix, and the remaining 8 bits reserved for host addressing. Addresses in the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Firewall (computing)
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on configurable security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet or between several VLANs. Firewalls can be categorized as network-based or host-based. History The term '' firewall'' originally referred to a wall to confine a fire within a line of adjacent buildings. Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The term was applied in the 1980s to network technology that emerged when the Internet was fairly new in terms of its global use and connectivity. The predecessors to firewalls for network security were routers used in the 1980s. Because they already segregated networks, routers could filter packets crossing them. Before it was used in real-life comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network World
International Data Group (IDG, Inc.) is an American market intelligence and demand generation company focused on the technology industry. IDG, Inc.'s mission is centered around supporting the technology industry through research, data, marketing technology, and insights that help create and sustain relationships between businesses. IDG, Inc. is wholly owned by Blackstone and is led by Genevieve Juillard, who was appointed CEO of the company in 2023. Juillard serves on IDG, Inc.'s leadership team along with IDC President Crawford Del Prete and IDG, Inc.'s Chief Financial Officer Tiziana Figliolia. IDG, Inc. is headquartered in Needham, Massachusetts and is the parent company of both International Data Corporation (IDC) and Foundry (formerly IDG Communications). History International Data Group was initially founded as International Data Corporation (IDC) in 1964 by Patrick Joseph McGovern, shortly after he had graduated from the Massachusetts Institute of Technology (MIT) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |