|
Network Chemistry
Network Chemistry was a Wi-Fi security startup based in Redwood City, California. The firm was founded in 2002 by several co-founders including Gary Ramah, Rob Markovich and Dr. Christopher Waters and is backed by venture capital firms such as San Francisco-based Geneva Venture Partners, Innovacom and In-Q-Tel, the investment arm of the CIA. The company sold products such as RFprotect Distributed, a wireless intrusion detection system; RFprotect Endpoint, a laptop security product; and RFprotect Mobile, a portable tool for analyzing network security. The final product was RFprotect Scanner, a wired-side rogue access point A rogue access point is a wireless access point that has been installed on a secure network without explicit authorization from a local network administrator, whether added by a well-meaning employee or by a malicious attacker. Dangers Although i ... detection and mitigation system utilizing patent-pending device fingerprinting technology. Network Chemi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wi-Fi
Wi-Fi () is a family of wireless network protocols, based on the IEEE 802.11 family of standards, which are commonly used for local area networking of devices and Internet access, allowing nearby digital devices to exchange data by radio waves. These are the most widely used computer networks in the world, used globally in home and small office networks to link desktop and laptop computers, tablet computers, smartphones, smart TVs, printers, and smart speakers together and to a wireless router to connect them to the Internet, and in wireless access points in public places like coffee shops, hotels, libraries and airports to provide visitors with Internet access for their mobile devices. ''Wi-Fi'' is a trademark of the non-profit Wi-Fi Alliance, which restricts the use of the term ''Wi-Fi Certified'' to products that successfully complete interoperability certification testing. the Wi-Fi Alliance consisted of more than 800 companies from around the world. over 3.05 billion ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
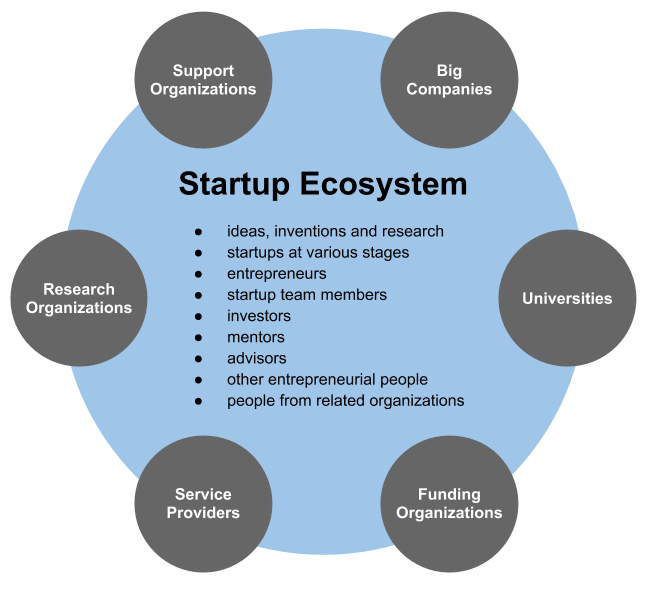
Startup Company
A startup or start-up is a company or project undertaken by an entrepreneur to seek, develop, and validate a scalable business model. While entrepreneurship refers to all new businesses, including self-employment and businesses that never intend to become registered, startups refer to new businesses that intend to grow large beyond the solo founder. At the beginning, startups face high uncertainty and have high rates of failure, but a minority of them do go on to be successful and influential.Erin Griffith (2014)Why startups fail, according to their founders Fortune.com, 25 September 2014; accessed 27 October 2017 Actions Startups typically begin by a founder (solo-founder) or co-founders who have a way to solve a problem. The founder of a startup will begin market validation by problem interview, solution interview, and building a minimum viable product (MVP), i.e. a prototype, to develop and validate their business models. The startup process can take a long period of time (by so ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Redwood City, California
Redwood City is a city on the San Francisco Peninsula in Northern California's Bay Area, approximately south of San Francisco, and northwest of San Jose. Redwood City's history spans its earliest inhabitation by the Ohlone people to being a port for lumber and other goods. The county seat of San Mateo County in the heart of Silicon Valley, Redwood City is home to several global technology companies including Oracle, Electronic Arts, Evernote, Box, and Informatica. The city's population was 84,292 according to the 2020 census. The Port of Redwood City is the only deepwater port on San Francisco Bay south of San Francisco. According to the United States Census Bureau, the city has an area of , of which is land and (44.34%) is water. A major watercourse draining much of Redwood City is Redwood Creek, to which several significant river deltas connect, the largest of which is Westpoint Slough. History The earliest known inhabitants of the area which was to become Redwoo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Venture Capital
Venture capital (often abbreviated as VC) is a form of private equity financing that is provided by venture capital firms or funds to startups, early-stage, and emerging companies that have been deemed to have high growth potential or which have demonstrated high growth (in terms of number of employees, annual revenue, scale of operations, etc). Venture capital firms or funds invest in these early-stage companies in exchange for equity, or an ownership stake. Venture capitalists take on the risk of financing risky start-ups in the hopes that some of the firms they support will become successful. Because startups face high uncertainty, VC investments have high rates of failure. The start-ups are usually based on an innovative technology or business model and they are usually from high technology industries, such as information technology (IT), clean technology or biotechnology. The typical venture capital investment occurs after an initial "seed funding" round. The first ro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
In-Q-Tel
In-Q-Tel (IQT), formerly Peleus and In-Q-It, is an American not-for-profit venture capital firm based in Arlington, Virginia. It invests in high-tech companies to keep the Central Intelligence Agency, and other intelligence agencies, equipped with the latest in information technology in support of United States intelligence capability. The name "In-Q-Tel" is an intentional reference to Q, the fictional inventor who supplies technology to James Bond. In-Q-Tel has stated that the average dollar invested by In-Q-Tel in 2016 attracts fifteen dollars from other investors. History Originally named Peleus and known as In-Q-It, In-Q-Tel was founded by Norm Augustine, a former CEO of Lockheed Martin, and by Gilman Louie, who was In-Q-Tel's first CEO. In-Q-Tel's mission is to identify and invest in companies developing cutting-edge technologies that serve United States national security interests. According to the Washington post, In-Q-Tel started as the idea of then CIA director George ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless Intrusion Detection System
In computing, a wireless intrusion prevention system (WIPS) is a network device that monitors the radio spectrum for the presence of unauthorized access points ''(intrusion detection)'', and can automatically take countermeasures ''(intrusion prevention)''. Purpose The primary purpose of a WIPS is to prevent unauthorized network access to local area networks and other information assets by wireless devices. These systems are typically implemented as an overlay to an existing Wireless LAN infrastructure, although they may be deployed standalone to enforce no-wireless policies within an organization. Some advanced wireless infrastructure has integrated WIPS capabilities. Large organizations with many employees are particularly vulnerable to security breaches caused by rogue access points. If an employee (trusted entity) in a location brings in an easily available wireless router, the entire network can be exposed to anyone within range of the signals. In July 2009, thPCI Secu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Laptop
A laptop, laptop computer, or notebook computer is a small, portable personal computer (PC) with a screen and alphanumeric keyboard. Laptops typically have a clam shell form factor with the screen mounted on the inside of the upper lid and the keyboard on the inside of the lower lid, although 2-in-1 PCs with a detachable keyboard are often marketed as laptops or as having a "laptop mode". Laptops are folded shut for transportation, and thus are suitable for mobile use. They are so named because they can be practically placed on a person's lap when being used. Today, laptops are used in a variety of settings, such as at work, in education, for playing games, web browsing, for personal multimedia, and for general home computer use. As of 2022, in American English, the terms ''laptop computer'' and ''notebook computer'' are used interchangeably; in other dialects of English, one or the other may be preferred. Although the terms ''notebook computers'' or ''notebooks'' or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Security
Network security consists of the policies, policies, processes and practices adopted to prevent, detect and monitor unauthorized access, Abuse, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs: conducting transactions and communications among businesses, Government agency, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: it secures the network, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rogue Access Point
A rogue access point is a wireless access point that has been installed on a secure network without explicit authorization from a local network administrator, whether added by a well-meaning employee or by a malicious attacker. Dangers Although it is technically easy for a well-meaning employee to install a " soft access point" or an inexpensive wireless router—perhaps to make access from mobile devices easier—it is likely that they will configure this as "open", or with poor security, and potentially allow access to unauthorized parties. If an attacker installs an access point they are able to run various types of vulnerability scanners, and rather than having to be physically inside the organization, can attack remotely—perhaps from a reception area, adjacent building, car park, or with a high gain antenna, even from several miles away. Prevention and detection To prevent the installation of rogue access points, organizations can install wireless intrusion prevention sys ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Aruba Networks
Aruba Networks, formerly known as Aruba Wireless Networks, is a Santa Clara, California-based wireless networking subsidiary of Hewlett Packard Enterprise company. The company was founded in Sunnyvale, California in 2002 by Keerti Melkote and Pankaj Manglik. On March 2, 2015, Hewlett-Packard announced it would acquire Aruba Networks for approximately $3 billion USD. On May 19, 2015, HP completed the acquisition. As of November 1, 2015, the company operates as a subsidiary of Hewlett Packard Enterprise company. Acquisitions See also * HP Networking Products * ProCurve * ProCurve Products HP ProCurve was the name of the networking division of Hewlett-Packard from 1998 to 2010 and associated with the products that it sold. The name of the division was changed to HP Networking in September 2010. Please use HP Networking Products fo ... References External links * Aruba Instant OnHPE Networking {{authority control Networking companies of the United States Networking h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |