|
Negative Database
In database security, a negative database is a database that saves attributes that cannot be associated with a certain entry. A negative database is a kind of database that contains huge amount of data consisting of simulating data. When anyone tries to get access to such databases both the actual and the negative data sets will be retrieved even if they steal the entire database. For example, instead of storing just the personal details you store personal details that members don't have. Negative databases can avoid inappropriate queries and inferences. They also support allowable operations. Under this scenario, it is desirable that the database support only the allowable queries while protecting the privacy of individual records, say from inspection by an insider. Collection of negative data has been referred to as "negative sousveillance": Reynolds, C. (2011). Negative sousveillance., in Proc. IACAP2011, pp. 306–308 References Database security {{databa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database Security
Database security concerns the use of a broad range of information security controls to protect databases (potentially including the data, the database applications or stored functions, the database systems, the database servers and the associated network links) against compromises of their confidentiality, integrity and availability. It involves various types or categories of controls, such as technical, procedural/administrative and physical. Security risks to database systems include, for example: * Unauthorized or unintended activity or misuse by authorized database users, database administrators, or network/systems managers, or by unauthorized users or hackers (e.g. inappropriate access to sensitive data, metadata or functions within databases, or inappropriate changes to the database programs, structures or security configurations); * Malware infections causing incidents such as unauthorized access, leakage or disclosure of personal or proprietary data, deletion of or damage ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Instruction (computer Science)
In computer science, an instruction set architecture (ISA), also called computer architecture, is an abstract model of a computer. A device that executes instructions described by that ISA, such as a central processing unit (CPU), is called an ''implementation''. In general, an ISA defines the supported instructions, data types, registers, the hardware support for managing main memory, fundamental features (such as the memory consistency, addressing modes, virtual memory), and the input/output model of a family of implementations of the ISA. An ISA specifies the behavior of machine code running on implementations of that ISA in a fashion that does not depend on the characteristics of that implementation, providing binary compatibility between implementations. This enables multiple implementations of an ISA that differ in characteristics such as performance, physical size, and monetary cost (among other things), but that are capable of running the same machine code, so that a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
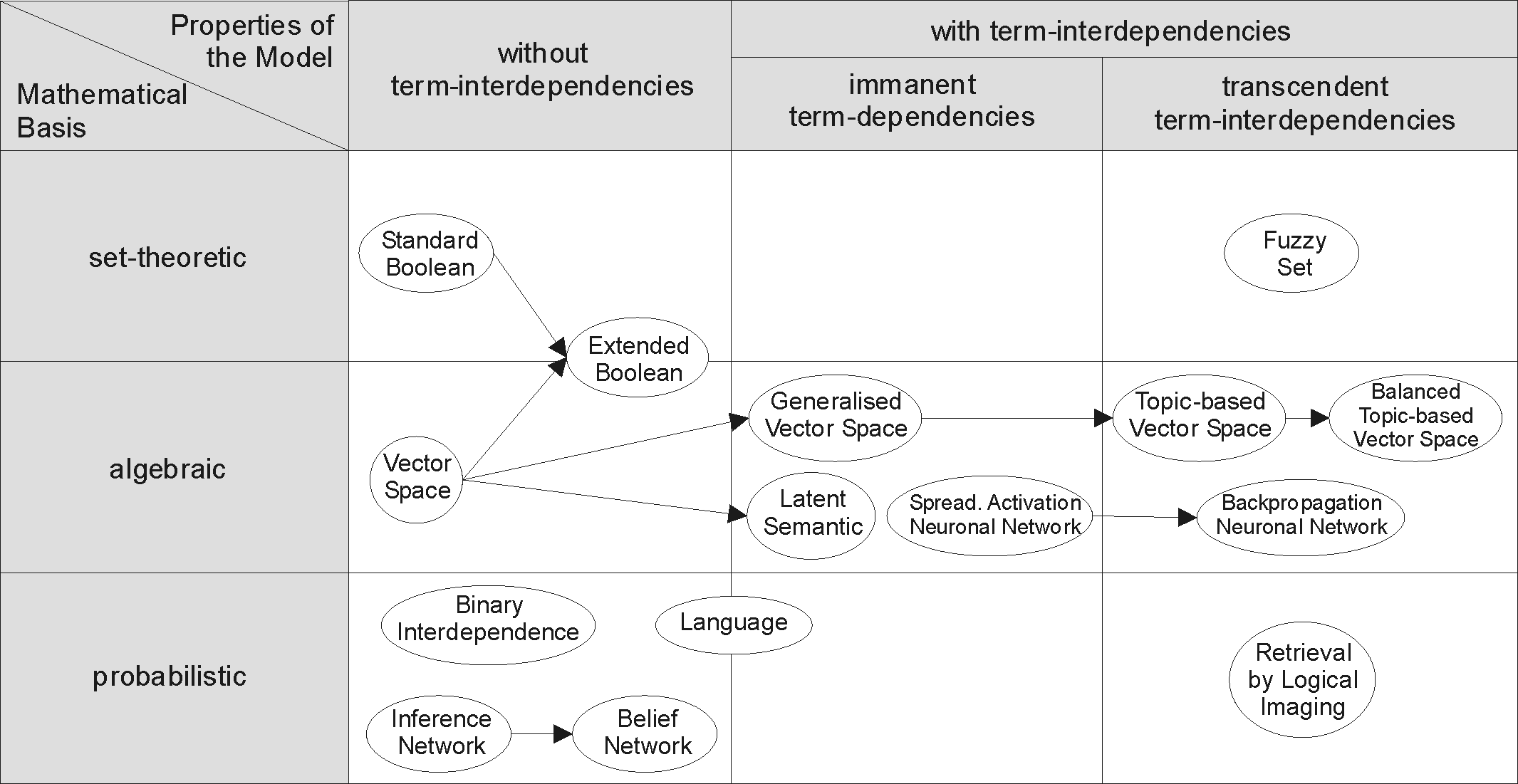
Information Retrieval
Information retrieval (IR) in computing and information science is the process of obtaining information system resources that are relevant to an information need from a collection of those resources. Searches can be based on full-text or other content-based indexing. Information retrieval is the science of searching for information in a document, searching for documents themselves, and also searching for the metadata that describes data, and for databases of texts, images or sounds. Automated information retrieval systems are used to reduce what has been called information overload. An IR system is a software system that provides access to books, journals and other documents; stores and manages those documents. Web search engines are the most visible IR applications. Overview An information retrieval process begins when a user or searcher enters a query into the system. Queries are formal statements of information needs, for example search strings in web search engines. In inf ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Record (computer Science)
In computer science, a record (also called a structure, struct, or compound data) is a basic data structure. Records in a database or spreadsheet are usually called "rows". A record is a collection of ''fields'', possibly of different data types, typically in a fixed number and sequence. The fields of a record may also be called ''members'', particularly in object-oriented programming; fields may also be called ''elements'', though this risks confusion with the elements of a collection. For example, a date could be stored as a record containing a numeric year field, a month field represented as a string, and a numeric day-of-month field. A personnel record might contain a name, a salary, and a rank. A Circle record might contain a center and a radius—in this instance, the center itself might be represented as a point record containing x and y coordinates. Records are distinguished from arrays by the fact that their number of fields is determined in the definition of the rec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sousveillance
Sousveillance ( ) is the recording of an activity by a member of the public, rather than a person or organisation in authority, typically by way of small wearable or portable personal technologies. The term, coined by Steve Mann, stems from the contrasting French words ''sur'', meaning "above", and ''sous'', meaning "below", i.e. "surveillance" denotes the " eye-in-the-sky" watching from above, whereas "sousveillance" denotes bring the means of observation down to human level, either physically (mounting cameras on people rather than on buildings) or hierarchically (ordinary people doing the watching, rather than higher authorities or architectures). While surveillance and sousveillance both usually refer to visual monitoring, they can denote other forms of monitoring such as audio surveillance or sousveillance. With audio (e.g. recording of phone conversations), sousveillance is sometimes referred to as "one party consent". Undersight (inverse oversight) is sousveillance at h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |